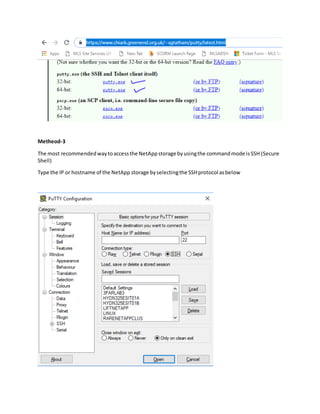
This document provides 3 methods for accessing a NetApp cluster mode storage system through the command line interface (CLI).
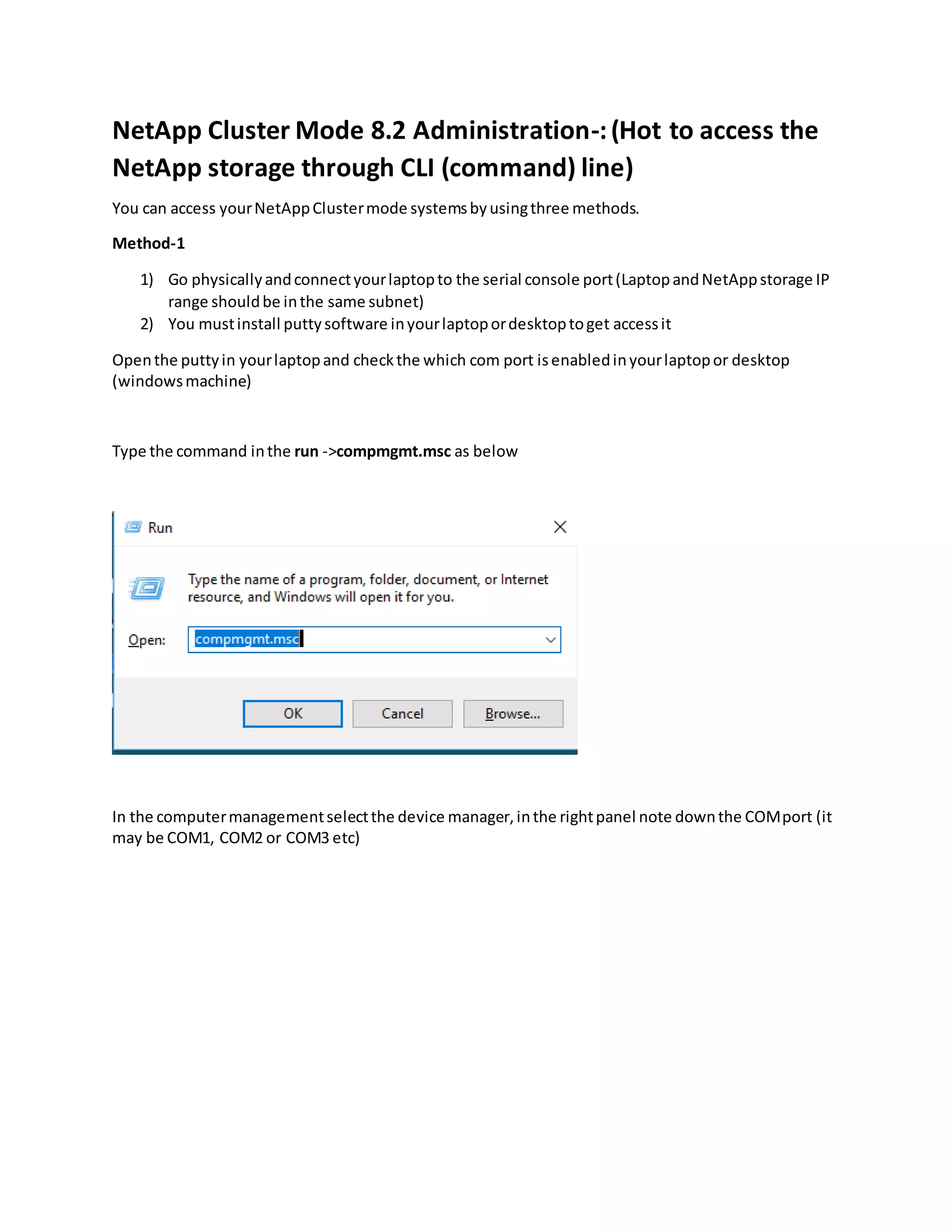
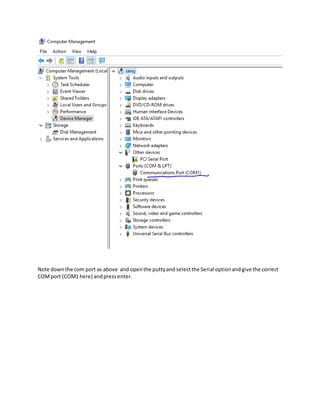
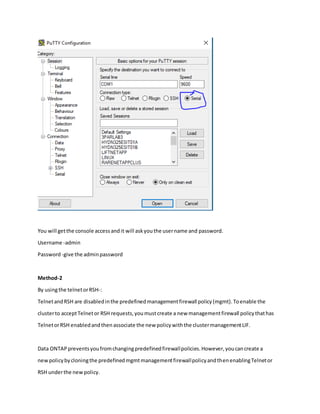
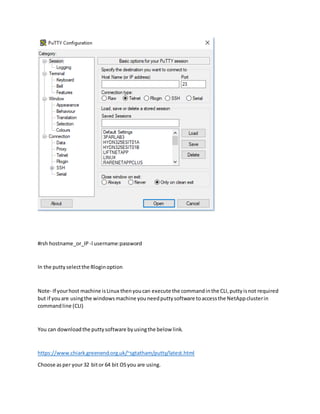
Method 1 involves connecting a laptop directly to the storage system's serial port using PuTTY software and logging in with username "admin". Method 2 allows using telnet or RSH by first cloning the firewall policy and enabling those services, but they are insecure. Method 3, which is recommended, uses SSH to securely access the storage system by hostname or IP and log in as "admin". The document provides instructions for downloading PuTTY and checking which CLI services are enabled or disabled.