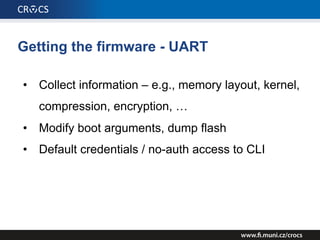
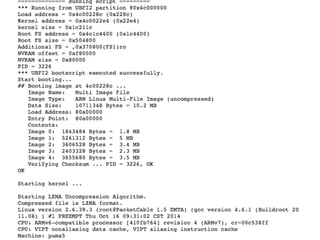
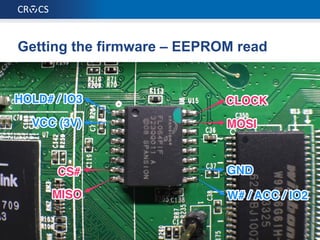
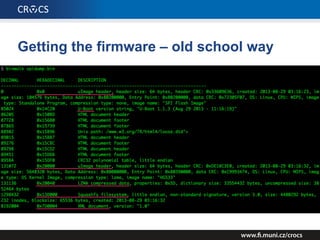
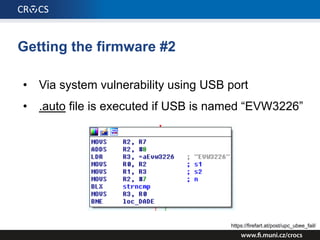
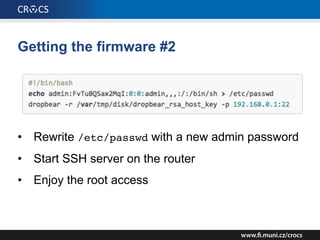
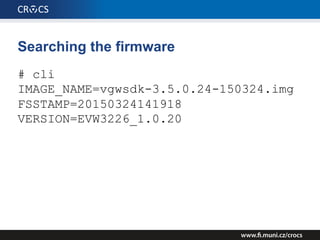
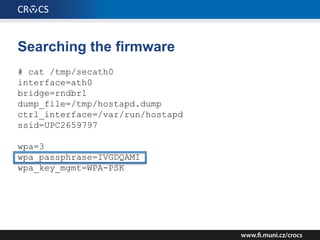
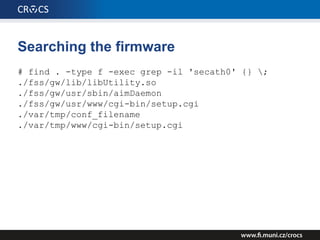
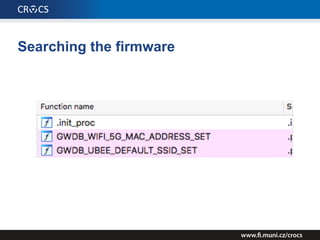
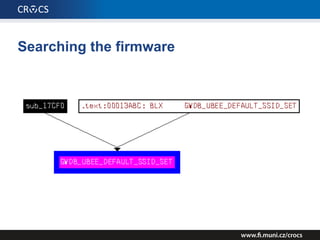
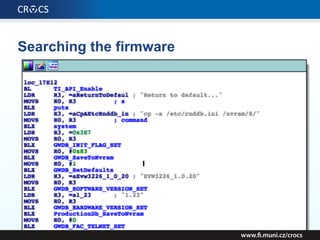
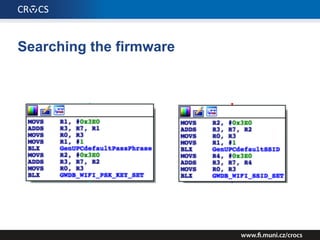
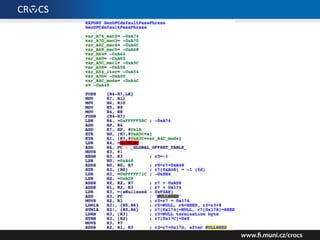
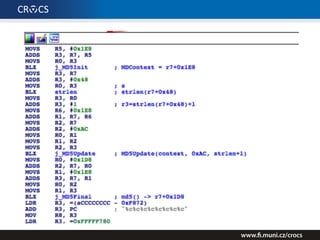
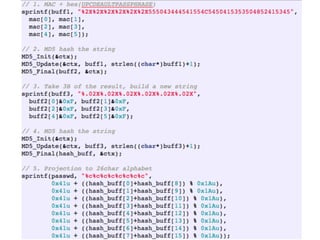
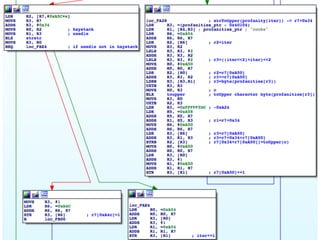
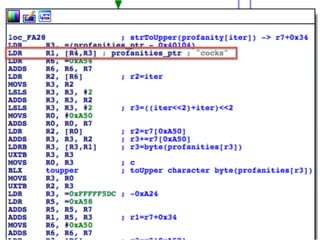
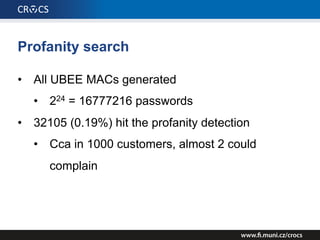
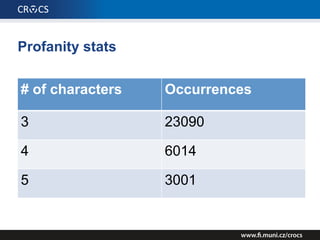
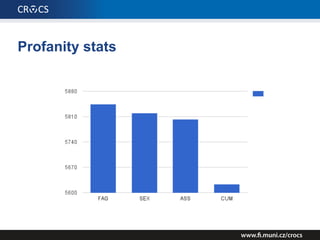
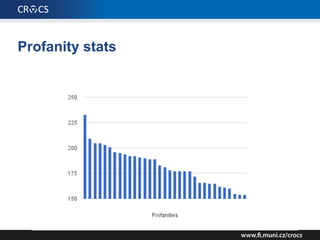
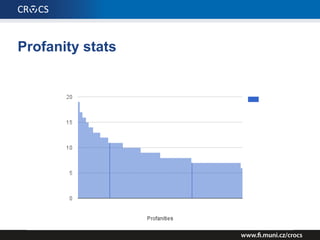
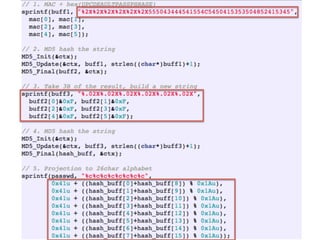
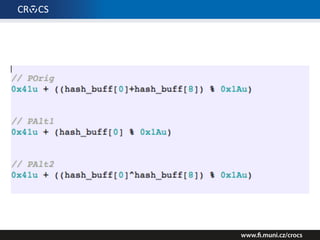
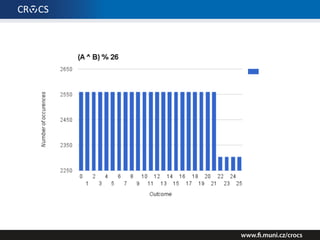
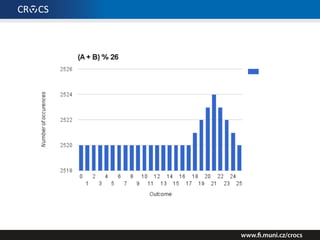
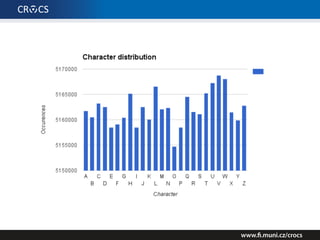
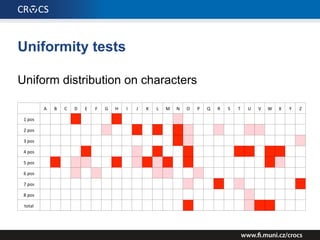
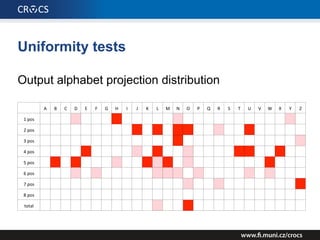
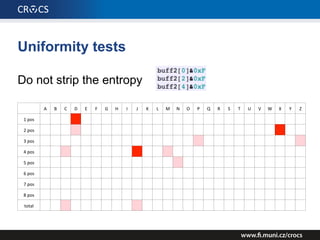
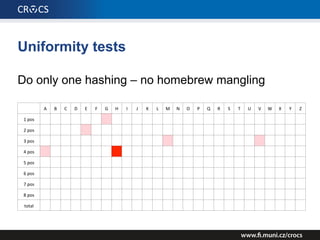
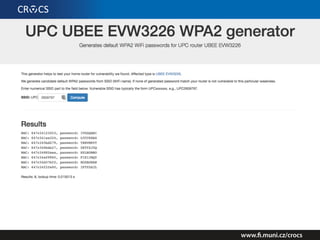
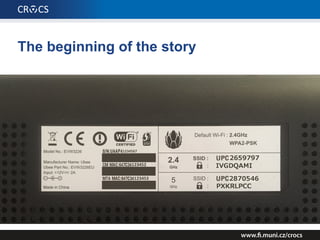
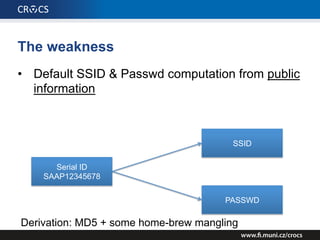
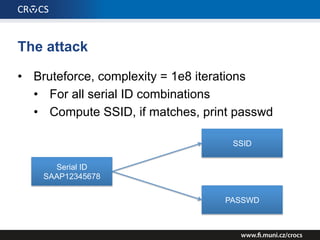
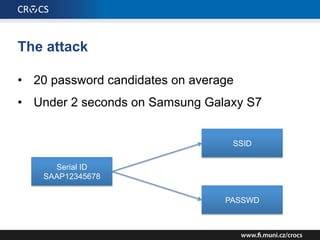
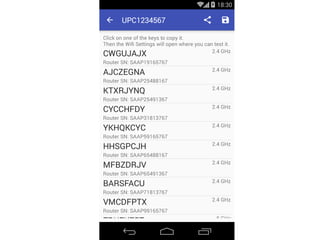
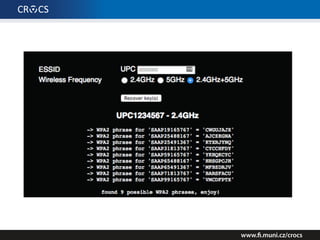
The document details a comprehensive analysis of vulnerabilities found in UPC router firmware, particularly focusing on the process of reverse engineering to extract WPA2 password generation methods. It highlights the ease of accessing sensitive firmware data, various attack methods including brute force and command injection, and outlines the discovery of numerous security flaws across different router models with statistical analyses of affected networks. The timeline of the research project and its disclosure to Liberty Global are also documented.


![Technicolor TC 7200
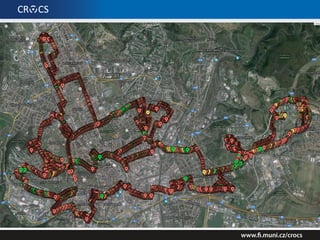
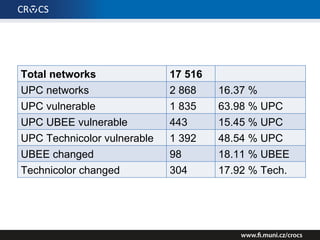
48.53 % of all UPC[0-9]{7} networks in Brno 02/2016
Vulnerable modem
* 2868 UPC samples collected / 17516 total](https://image.slidesharecdn.com/upceuropen-161012164156/85/UPC-router-reverse-engineering-case-study-9-320.jpg)
![UBEE EVW 3226
15.44 % of all UPC[0-9]{7} networks in Brno 02/2016
Not-yet-vulnerable modem
* 2868 UPC samples collected / 17516 total](https://image.slidesharecdn.com/upceuropen-161012164156/85/UPC-router-reverse-engineering-case-study-10-320.jpg)