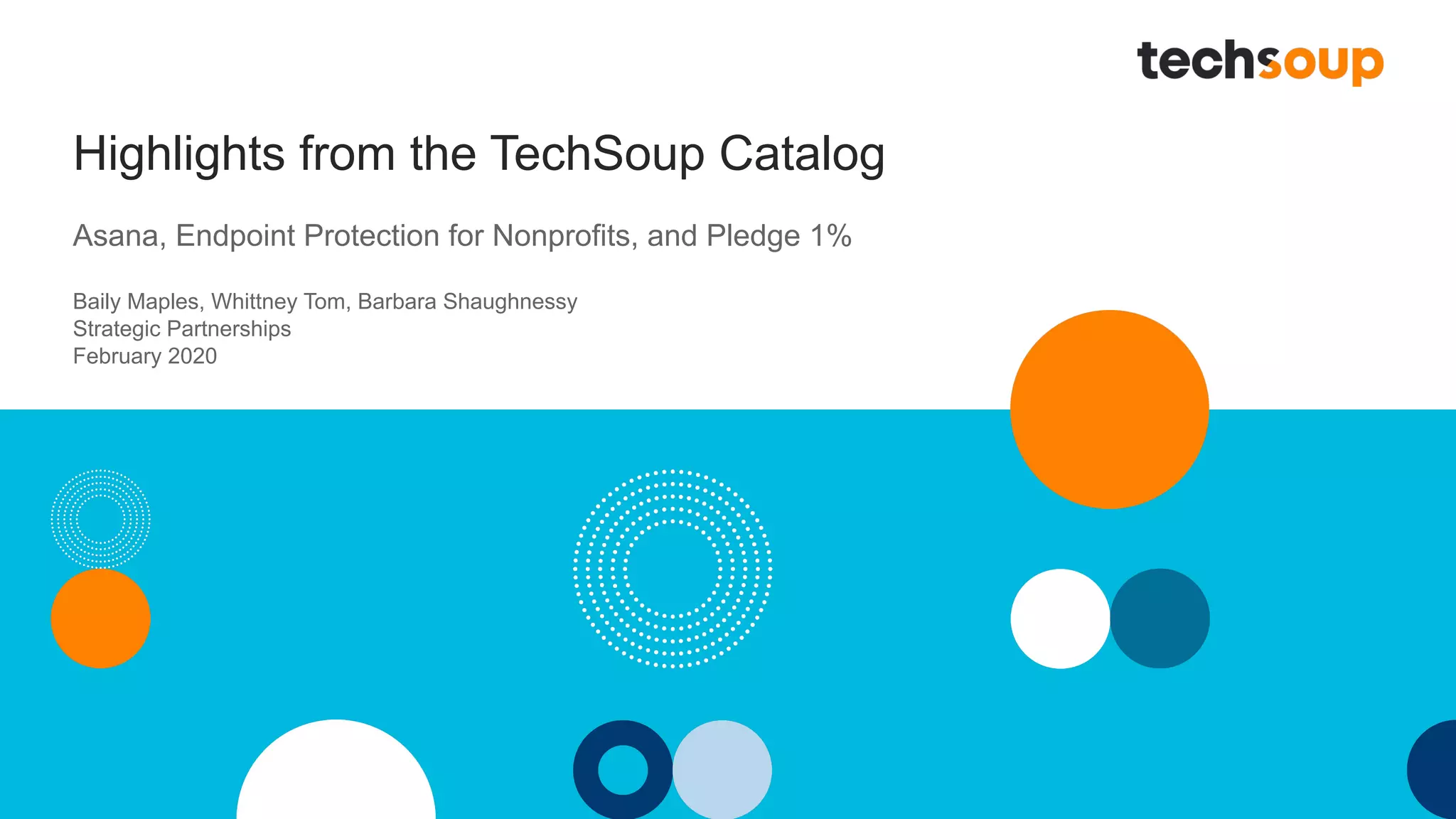
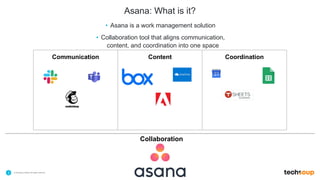
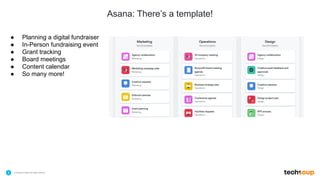
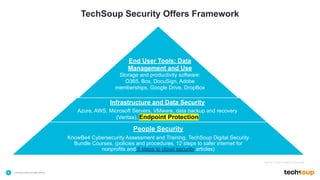
The document outlines TechSoup's offerings including Asana, a work management solution for nonprofits, and endpoint protection products like Norton and Bitdefender designed to enhance data security for small organizations. It emphasizes the importance of cybersecurity training for staff and the availability of various resources to help improve organizational efficiency. Additionally, it introduces the Pledge 1% initiative aimed at fostering corporate philanthropy and community engagement among businesses.