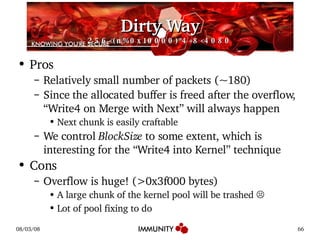
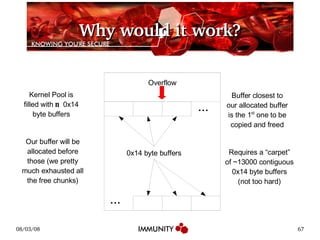
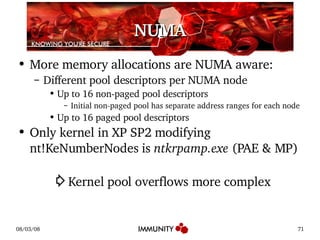
The document discusses the Windows kernel pool and how it can be exploited. It provides an overview of the kernel pool structures like pool descriptors and lookaside lists. It describes the allocation and freeing algorithms, including splitting and merging of chunks. It then gives an example of exploiting a kernel pool overflow bug, MS08-001, by overwriting structures in the pool to achieve code execution.












![nt!_POOL_DESCRIPTOR kd> dt nt!_POOL_DESCRIPTOR +0x000 PoolType : _POOL_TYPE +0x004 PoolIndex : Uint4B +0x008 RunningAllocs : Uint4B +0x00c RunningDeAllocs : Uint4B +0x010 TotalPages : Uint4B +0x014 TotalBigPages : Uint4B +0x018 Threshold : Uint4B +0x01c LockAddress : Ptr32 Void +0x020 PendingFrees : Ptr32 Void +0x024 PendingFreeDepth : Int4B +0x028 ListHeads : [512] _LIST_ENTRY](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-16-320.jpg)





![nt!_GENERAL_LOOKASIDE kd> dt nt!_GENERAL_LOOKASIDE +0x000 ListHead : _SLIST_HEADER +0x008 Depth : Uint2B +0x00a MaximumDepth : Uint2B +0x00c TotalAllocates : Uint4B +0x010 AllocateMisses : Uint4B +0x010 AllocateHits : Uint4B +0x014 TotalFrees : Uint4B +0x018 FreeMisses : Uint4B +0x018 FreeHits : Uint4B +0x01c Type : _POOL_TYPE +0x020 Tag : Uint4B +0x024 Size : Uint4B +0x028 Allocate : Ptr32 void* +0x02c Free : Ptr32 void +0x030 ListEntry : _LIST_ENTRY +0x038 LastTotalAllocates : Uint4B +0x03c LastAllocateMisses : Uint4B +0x03c LastAllocateHits : Uint4B +0x040 Future : [2] Uint4B](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-23-320.jpg)




![Simplified Allocation Algorithm nt!ExAllocatePoolWithTag (2/2) If failed, try the “system wide” non-paged lookaside list Return on success Try and lock the non-paged pool descriptor Use ListHeads of currently locked pool: Use 1 st non empty ListHeads[n] With BlockSize n<512 Split entry if bigger than needed Return on success If failed, expand the pool by adding a page Try again!](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-28-320.jpg)














![ListHeads Write4 When the chunk we overflowed is allocated: If the chunk was requested through ListHeads list No other constraint on BlockSize , PreviousSize , ... Then the overflowed list entry is removed from the ListHeads list ⇨ Write4 Variations of the write4 exist based on operations done on the neighboring entries We can end up overwriting ListHeads[ BlockSize ] Flink with a pointer we control Next time a chunk of BlockSize is requested, our pointer will be returned](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-48-320.jpg)
![ListHeads Illustrated (1/3) ListHeads[n] Flinks Free Chunk Free Chunk Free Chunk : Overflowed list entry Flink Blink Flink Blink Flink Blink Flink Blink](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-49-320.jpg)
![ListHeads Illustrated (1/3) ListHeads[n] Blinks Free Chunk Free Chunk Free Chunk : Overflowed list entry Flink Blink Flink Blink Flink Blink Flink Blink](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-50-320.jpg)
![ListHeads Illustrated (2/3) ListHeads[n] Free Chunk Free Chunk PLIST_ENTRY b,f; f=ListHeads[n] Flink Flink; b=ListHeads[n] Flink Blink; b Flink=f; f Blink=b; Allocation of size n unlinks ListHeads[n] Flink Flink Blink Flink Blink Flink Blink](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-51-320.jpg)
![ListHeads Illustrated (3/3) ListHeads[n] Free Chunk PLIST_ENTRY b,f; f=ListHeads[n] Flink Flink; b=ListHeads[n] Flink Blink; b Flink=f; f Blink=b; ⇦ might AV Allocation of size n unlinks ListHeads[n] Flink ListHeads[n] Flink is now under our control! Flink Blink Flink Blink](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-52-320.jpg)



![Write4 into the Kernel Before mov eax, [edx+ 8 ] mov ebx, [edx+ 0Ch ] mov [ebx], eax mov [eax+ 4 ], ebx loc_80543F0B: ; CODE XREF: ExFreePoolWithTag(x,x)+518j movzx edx, word ptr [edx+ 2 ] After mov eax, [edx+ 8 ] mov ebx, [edx+ 0Ch ] mov [ebx], eax mov [eax+ 4 ], ebx loc_80543F0B: ; CODE XREF: ExFreePoolWithTag(x,x)+518j jmp edx Edx points to something we control Jmp edx being 2 bytes long, we can pick the upper 2 so that the write4 doesn't trigger an access violation](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-56-320.jpg)
![Fixing the Kernel Pool Check for inconsistencies and fix them: Lookaside lists, both “per processor” and systemwide Zero out Sequence , Depth and Next of ListHead member of the given nt!_GENERAL_LOOKASIDE entry In fact the first 8 bytes ListHeads lists for involved pool descriptor(s) Set ListHeads[ BlockSize ] Flink and ListHeads[ BlockSize ] B link to &ListHeads[ BlockSize ] nt!MmNonPagedPoolFreeListHead array](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-57-320.jpg)


![IGMPv3 Membership Queries RFC 3376 0 1 2 3 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Type = 0x11 | Max Resp Code | Checksum | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Group Address | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Resv |S| QRV | QQIC | Number of Sources (N) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Source Address [1] | +- -+ | Source Address [2] | +- . -+ . . . . . . +- -+ | Source Address [N] | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-60-320.jpg)
![Vulnerability Walk a single linked list to count the number of entries (using a 32 bit counter) Allocate some memory: loc_44197: ; CODE XREF: GetGSIsInRecord(x,x)+18j push 10h ; Priority movzx eax, dx push 'qICT' ; Tag lea eax, ds: 8 [eax*4] push eax ; NumberOfBytes push ebx ; PoolType call ds: __imp__ExAllocatePoolWithTagPriority@16 Copy the list entries in the allocated array by walking the list ⇨ Overflow ⇦ Failed!](https://image.slidesharecdn.com/kernelpool-1217777694161423-8/85/Kernel-Pool-61-320.jpg)