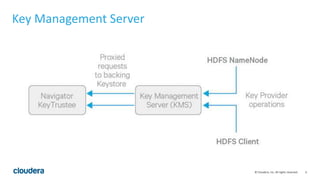
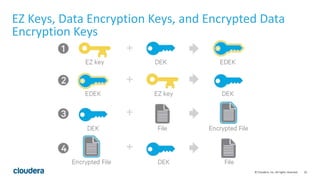
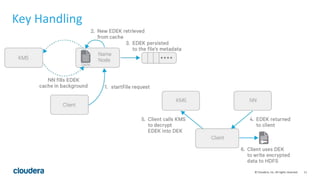
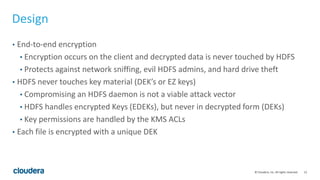
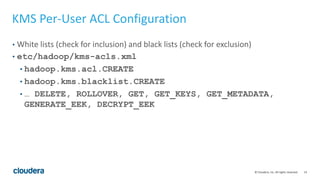
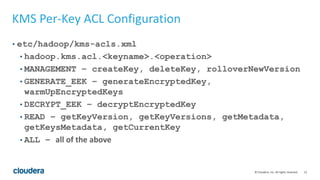
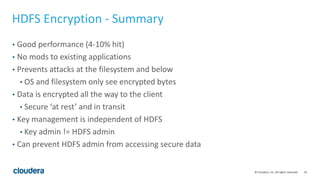
HDFS transparent encryption allows data written to and read from encrypted directories to be encrypted and decrypted transparently without any changes to user code. The encryption is performed by the client and HDFS never handles unencrypted data or keys. A key management server provides a unified API and keys are stored in encryption zones with unique data encryption keys for each file. This provides end-to-end encryption with strong security while maintaining good performance.