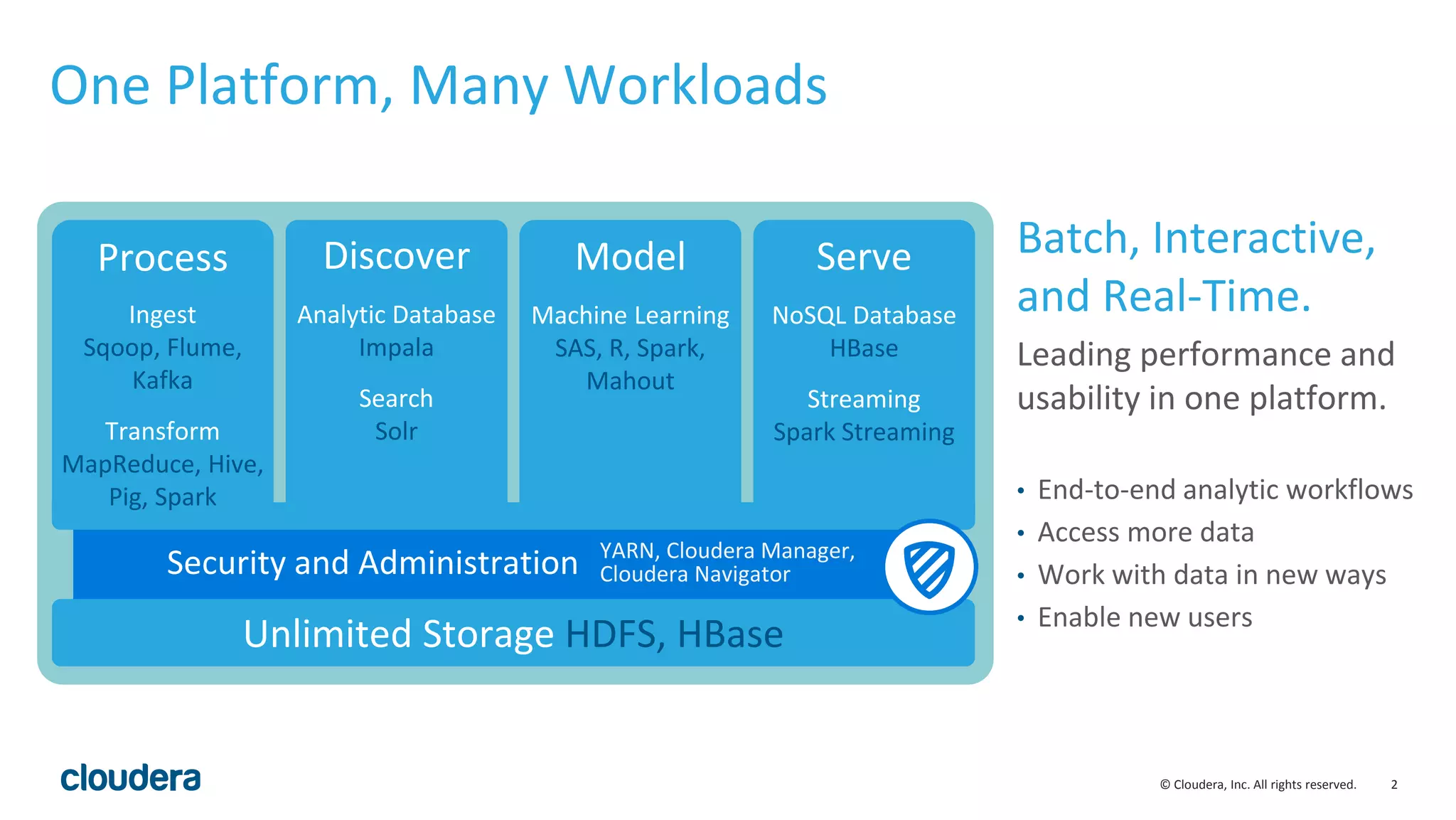
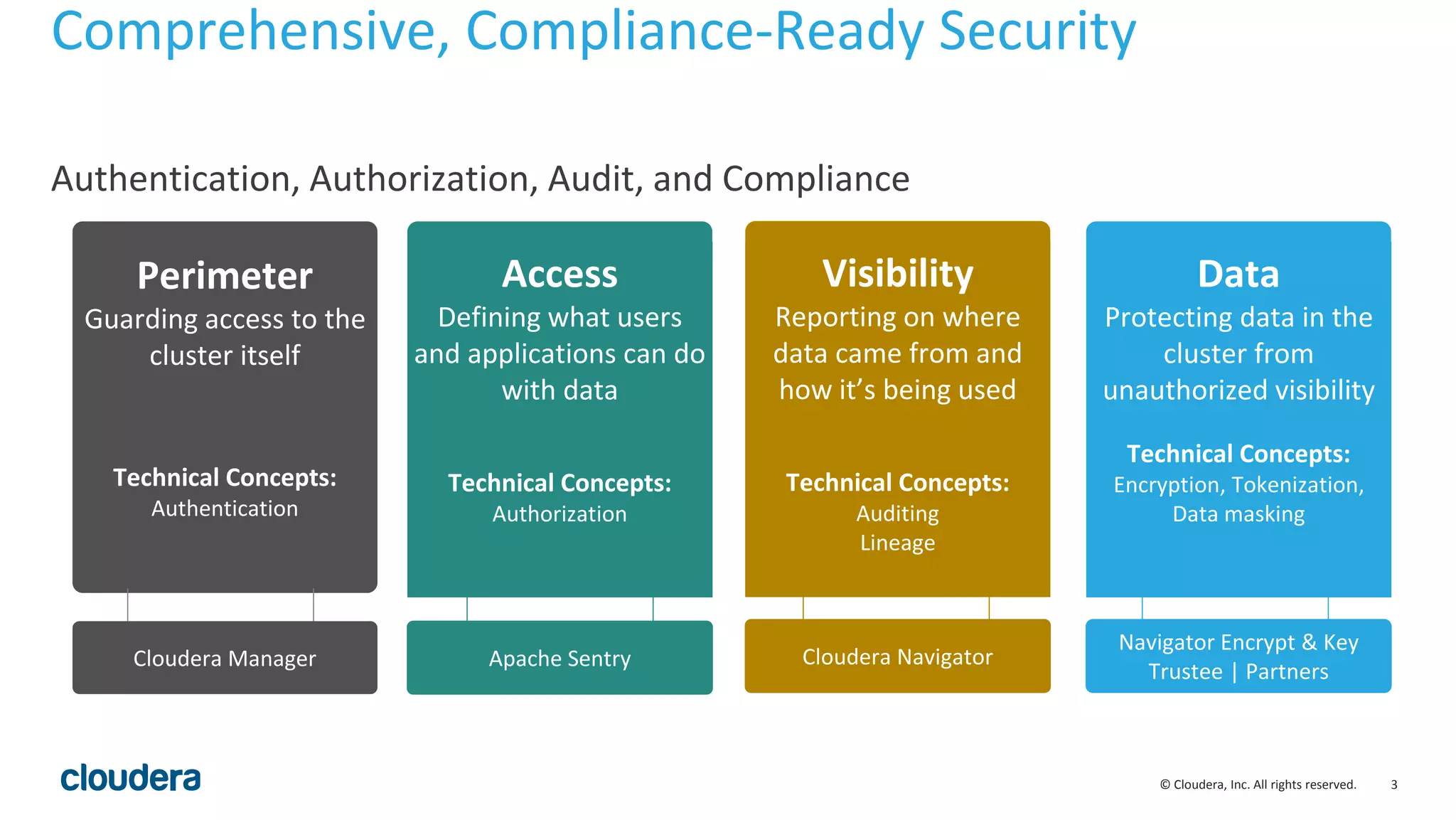
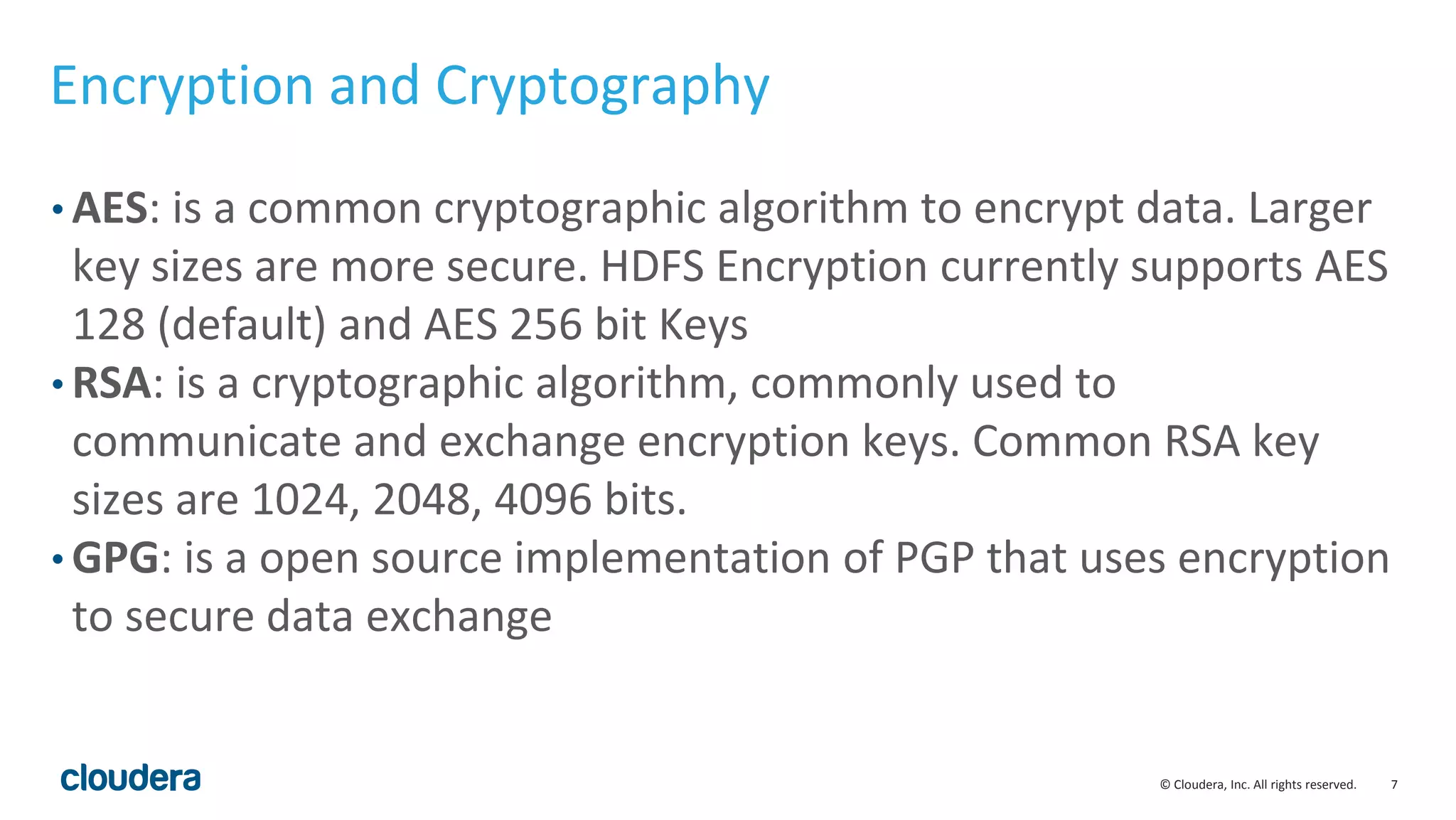
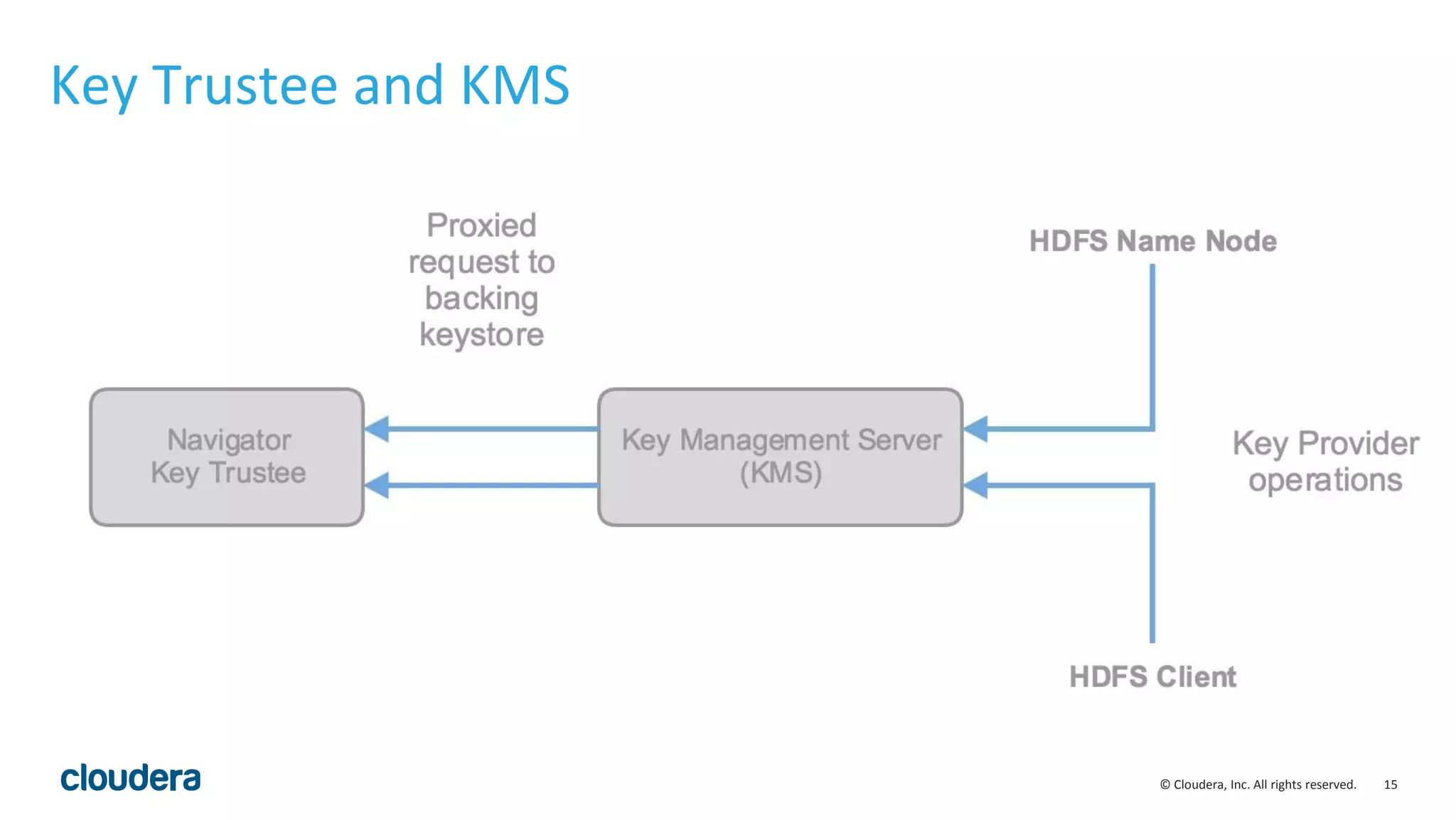
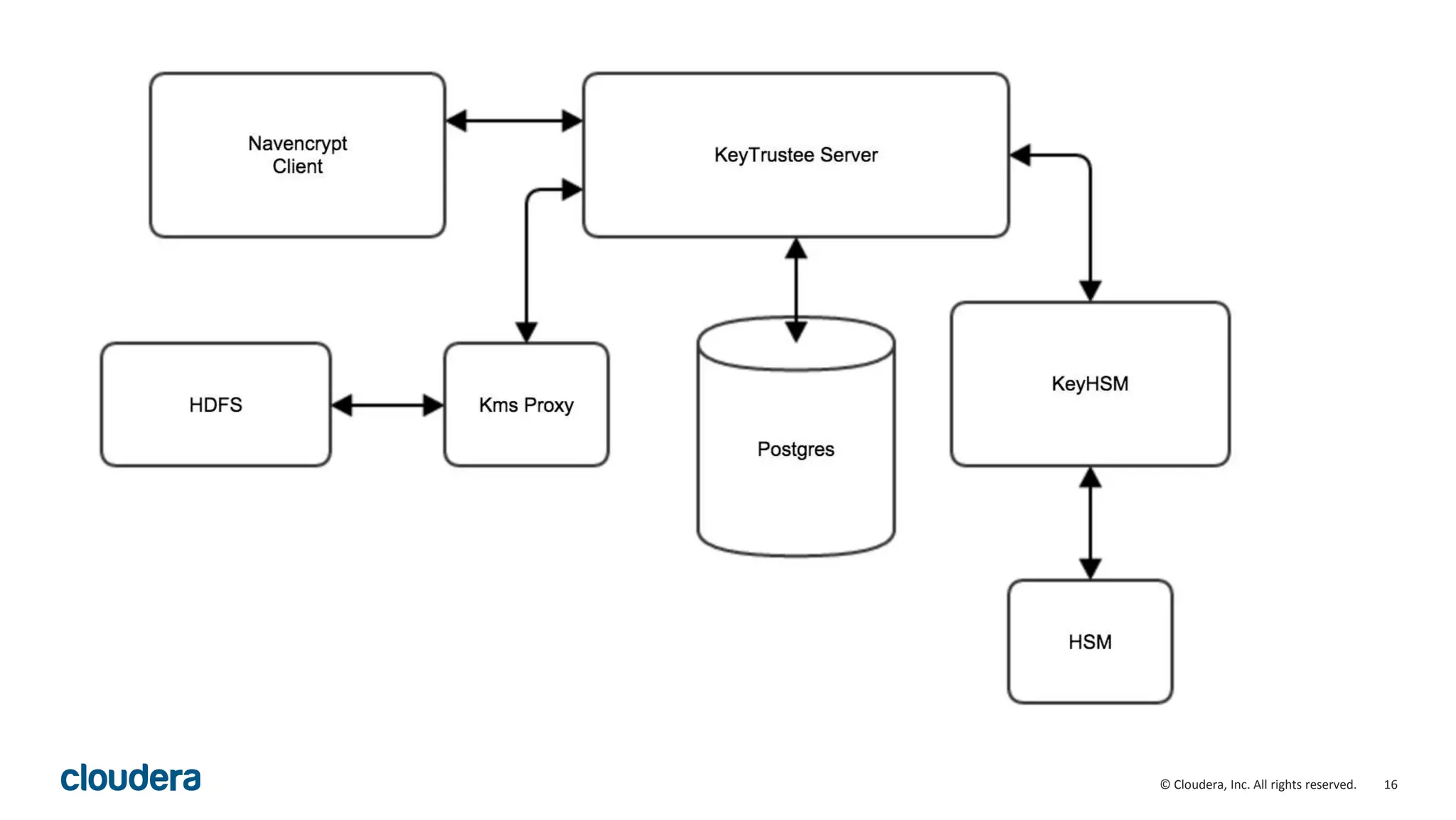
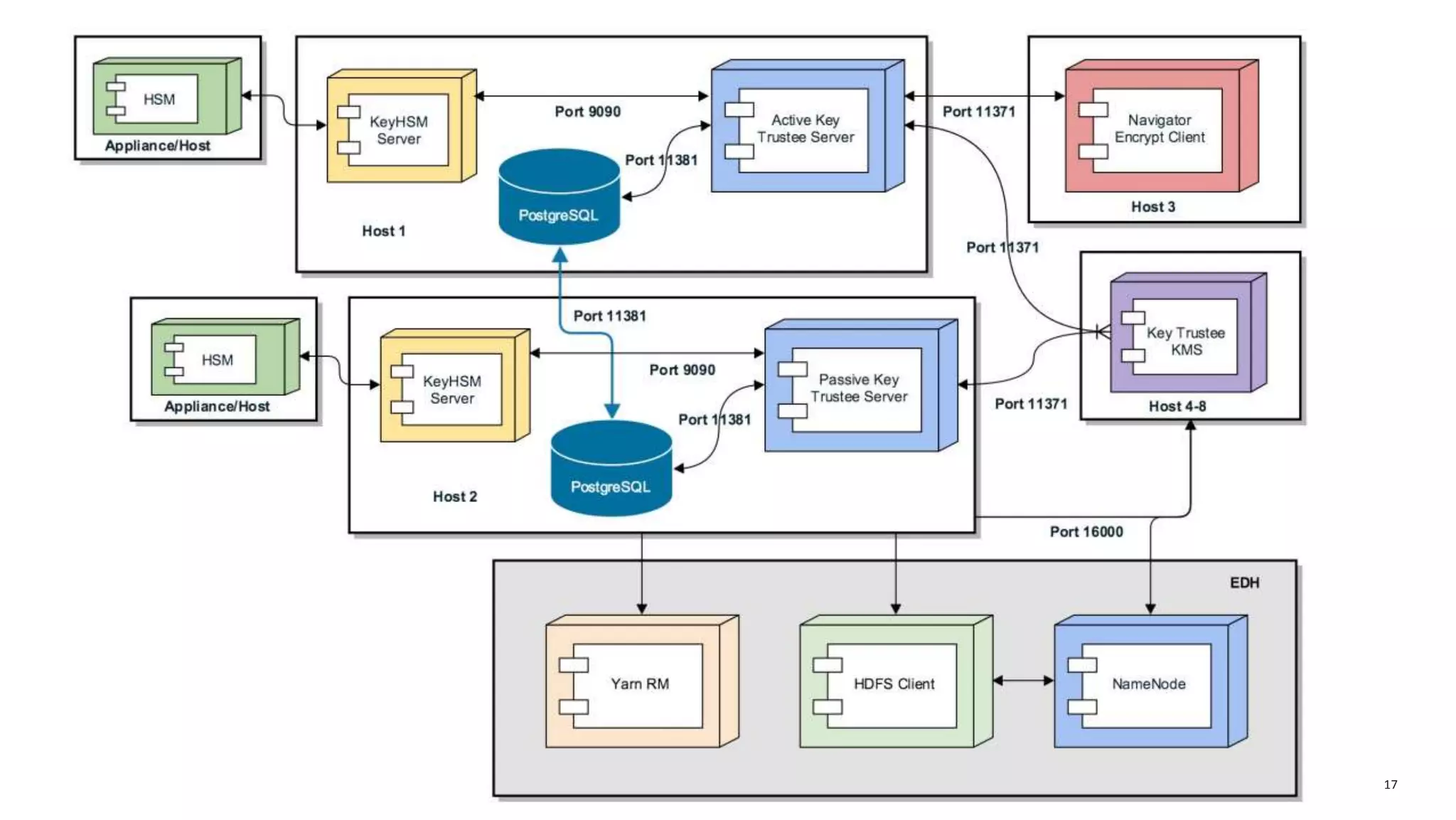
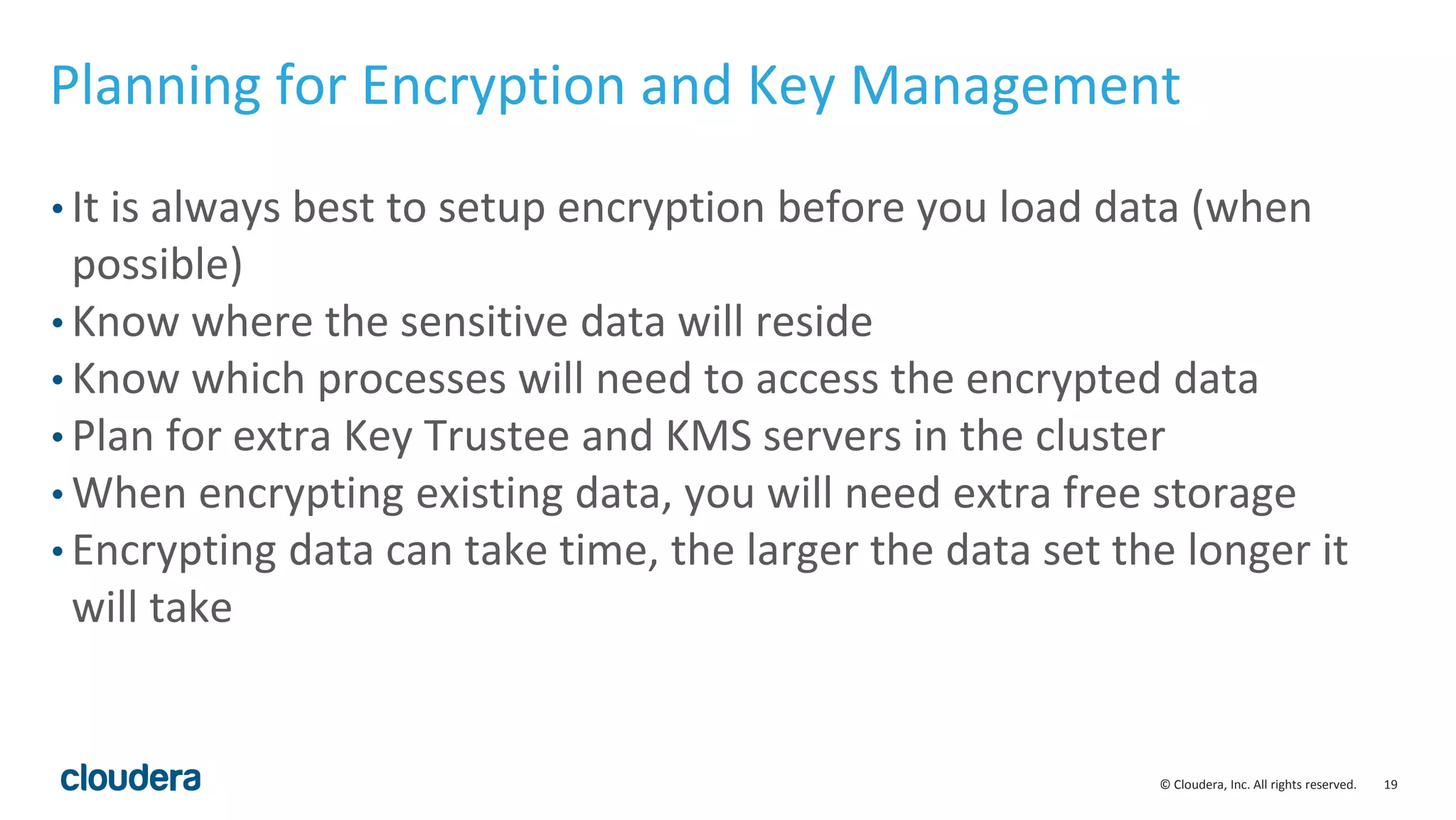
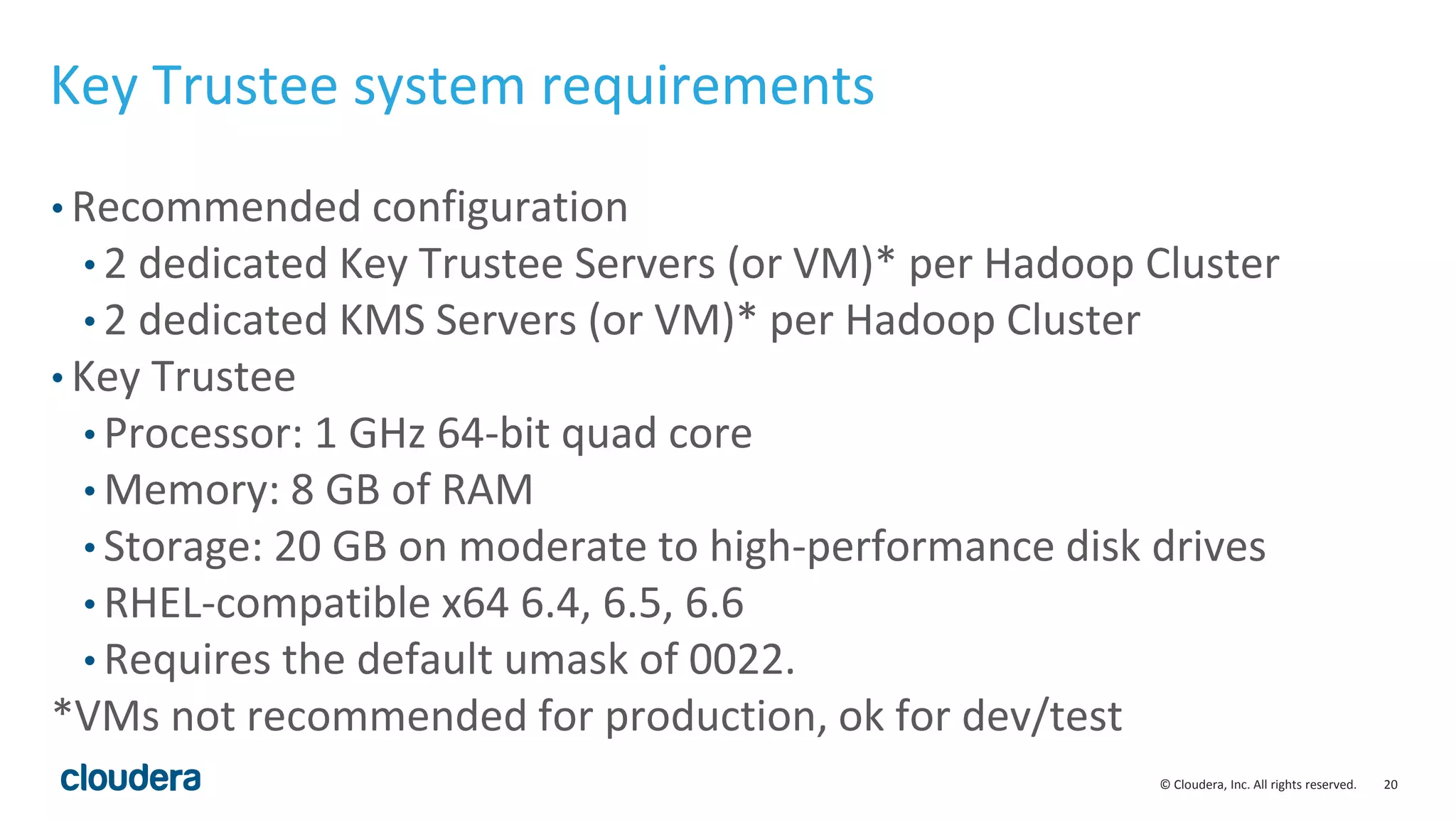
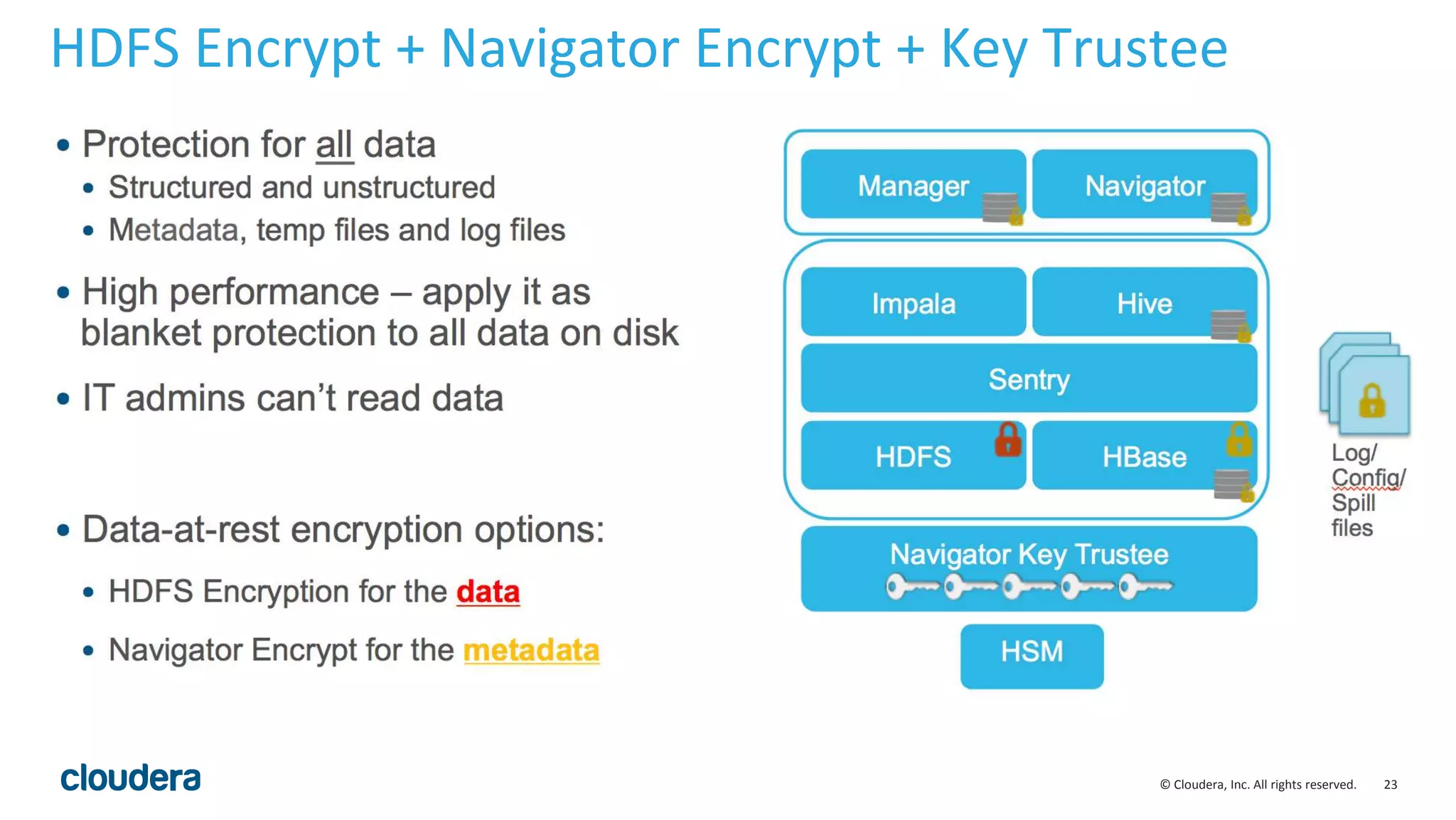
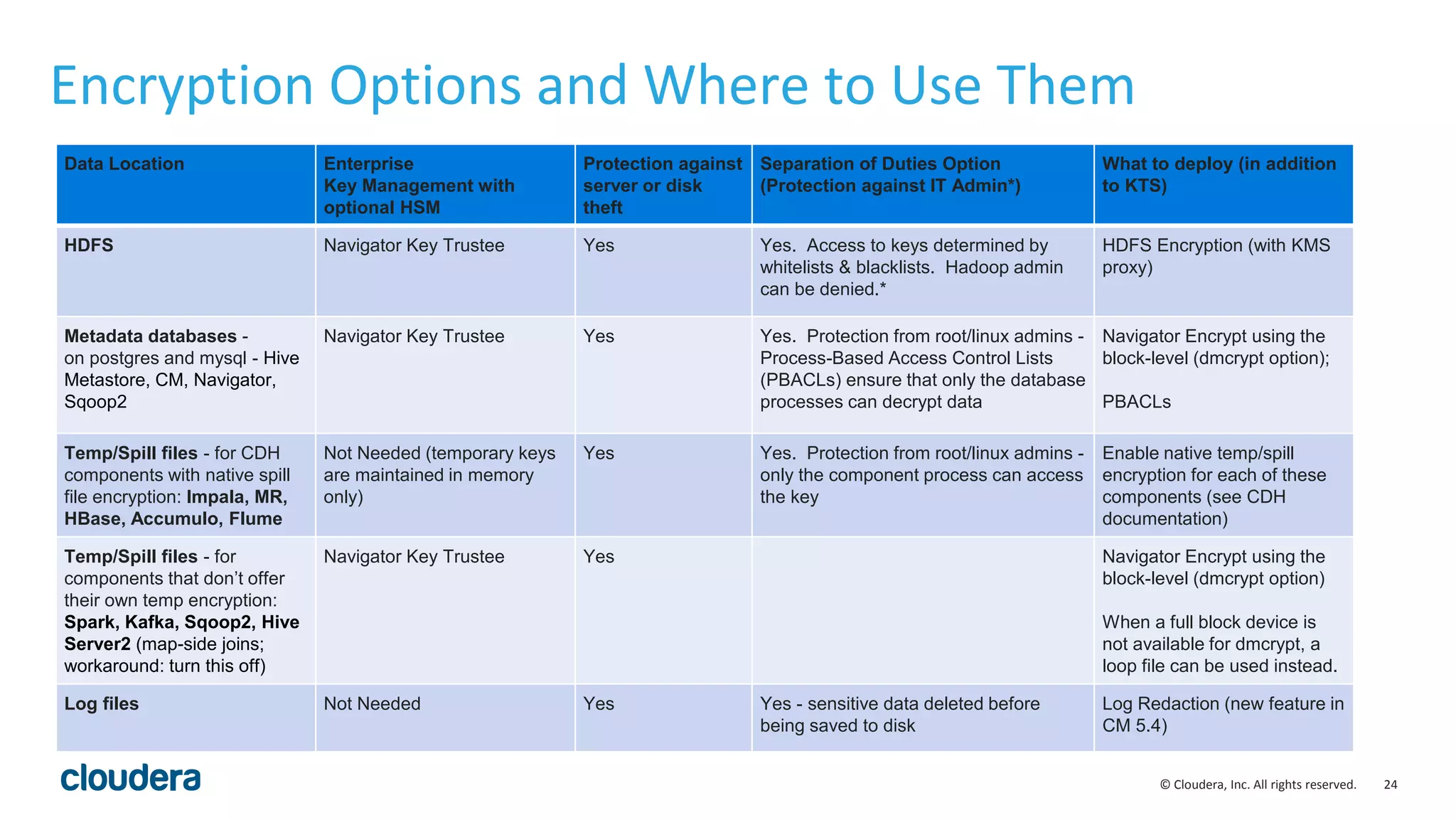
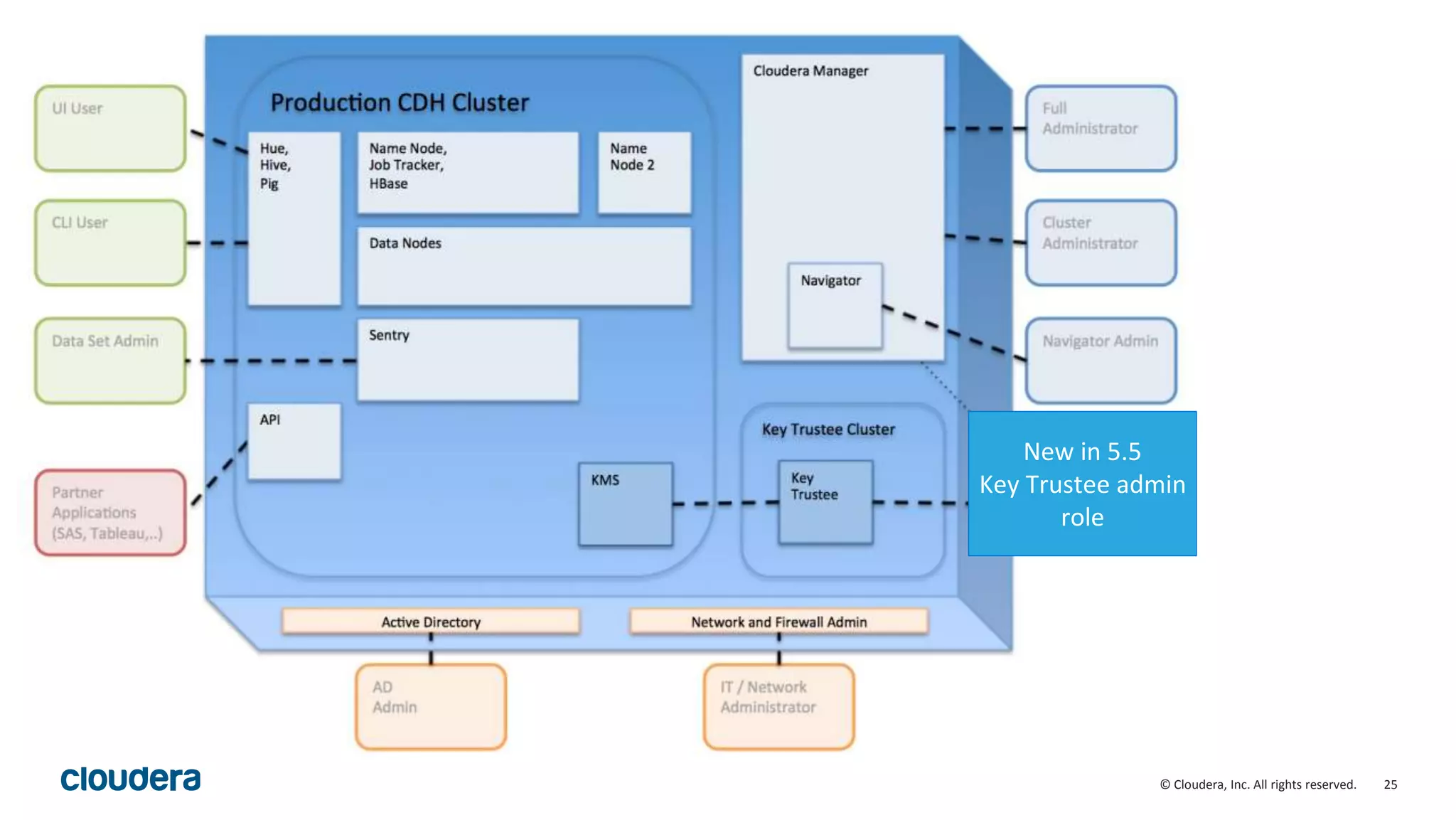
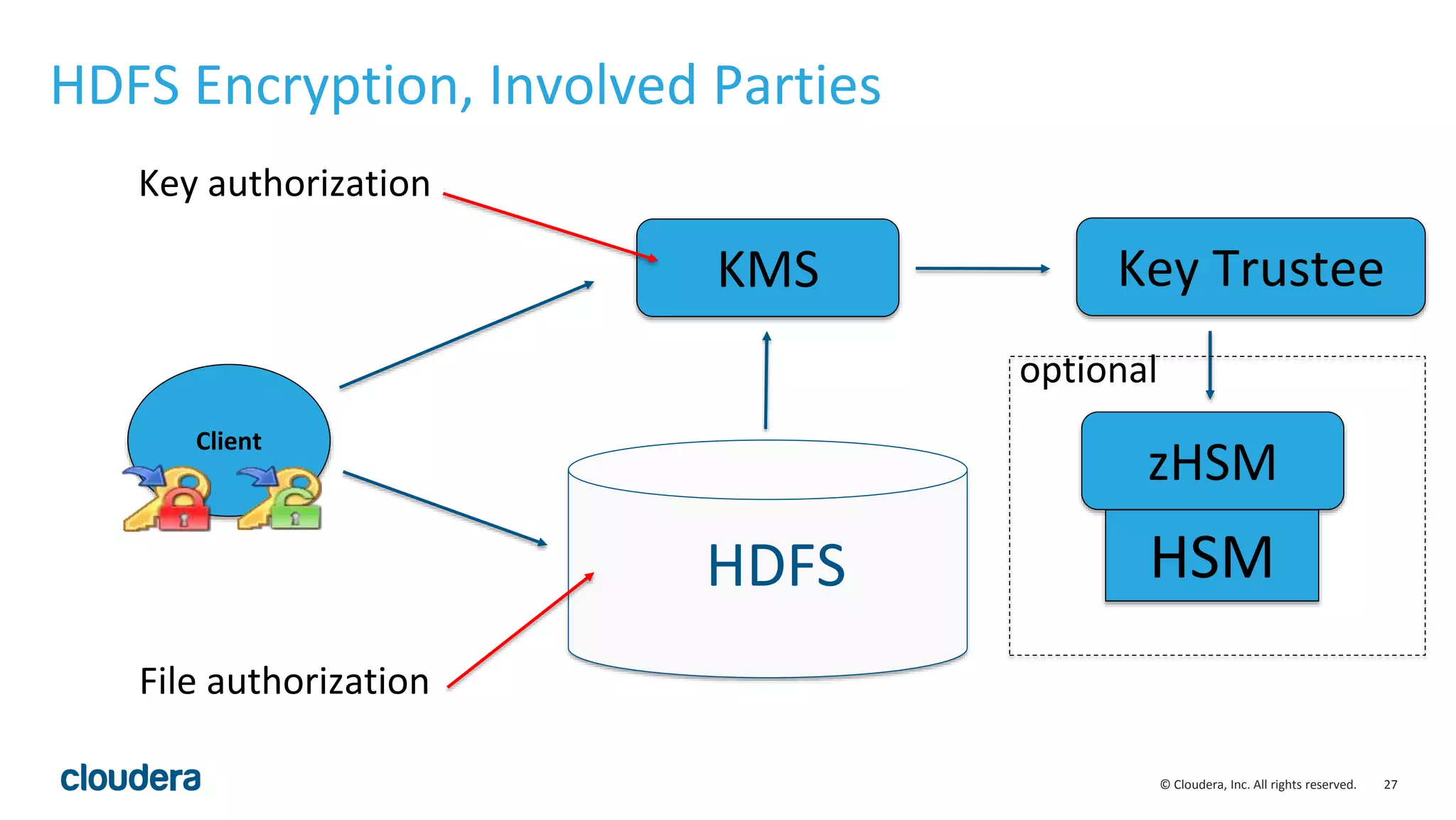
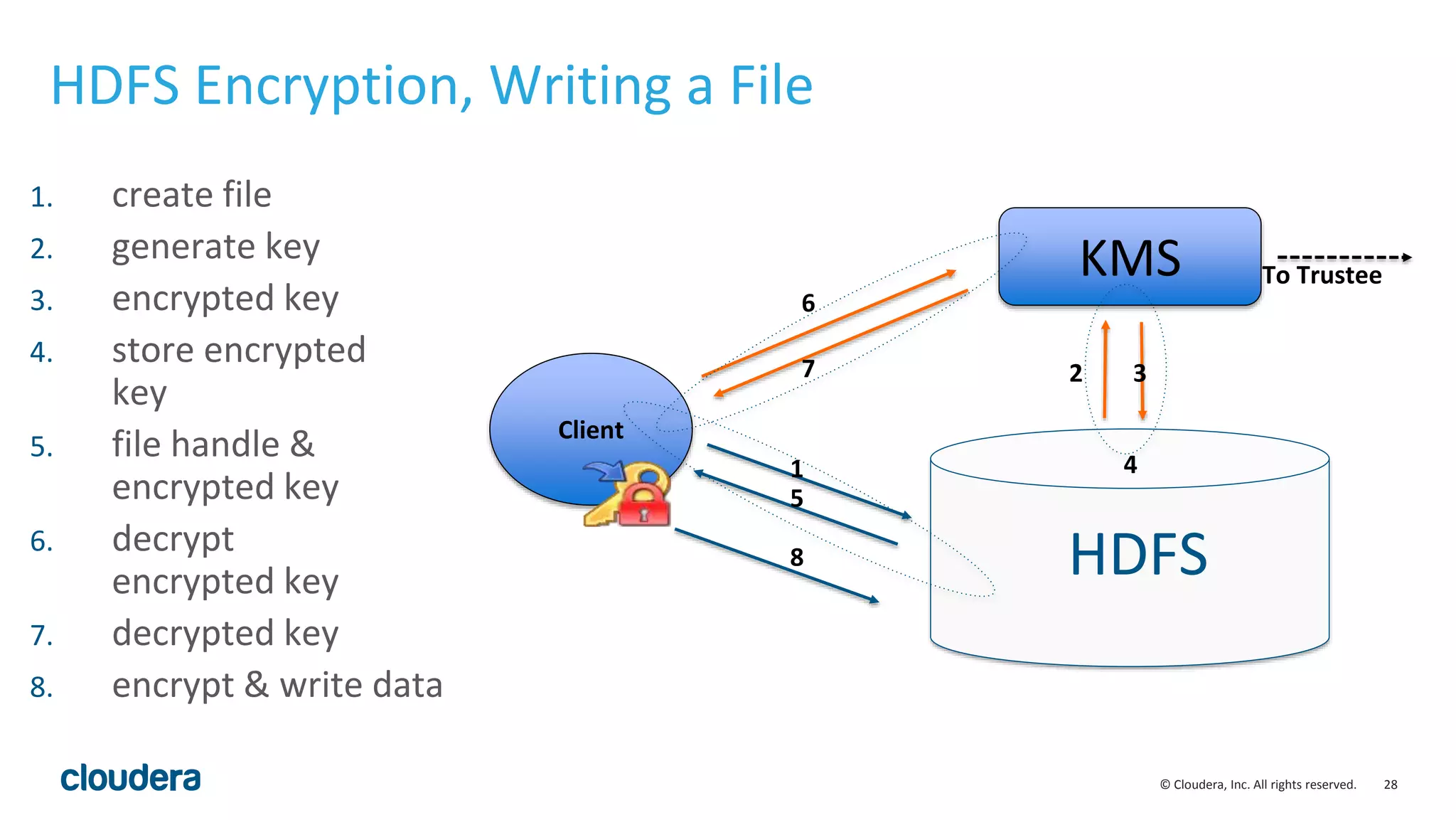
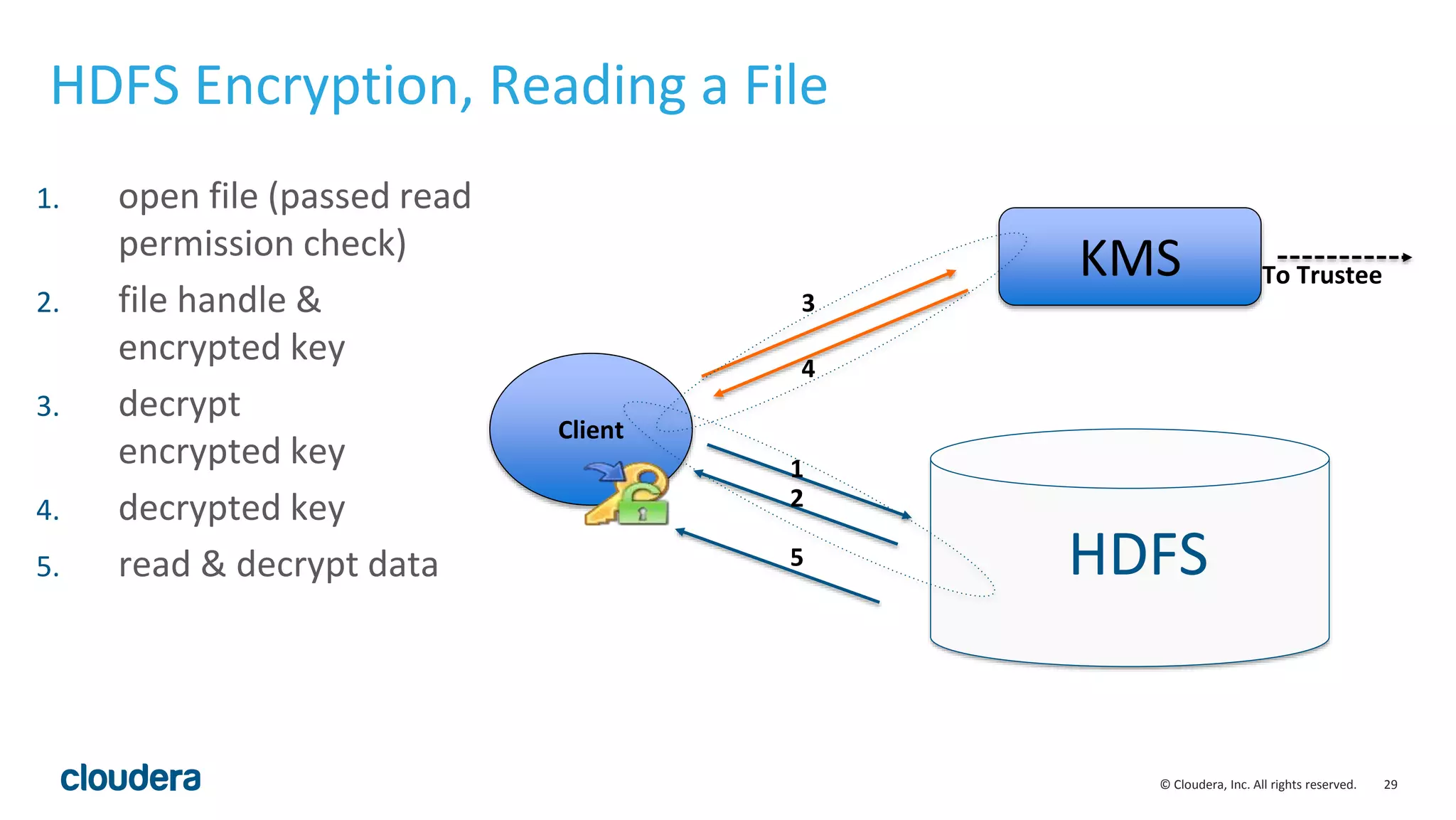
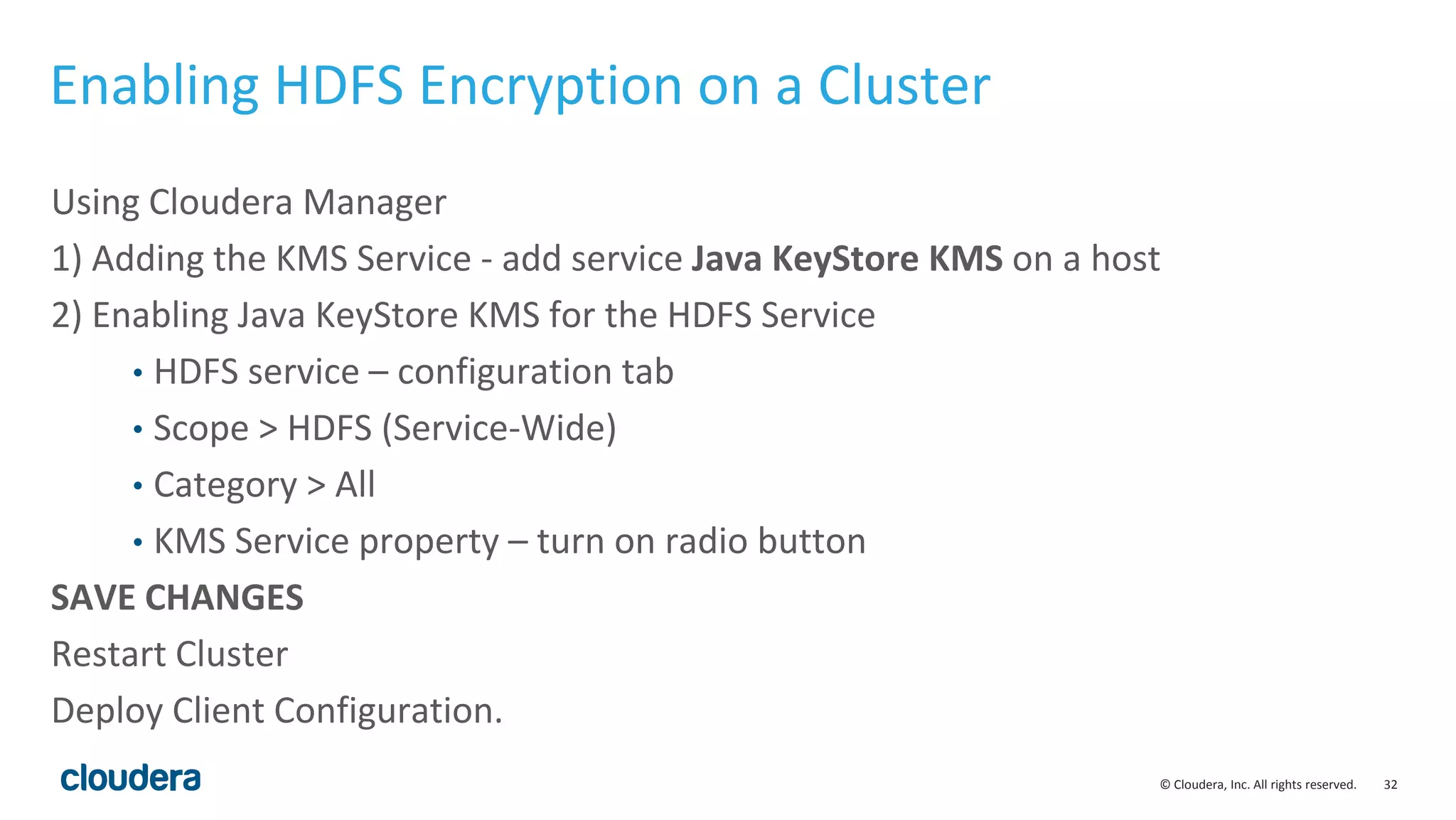
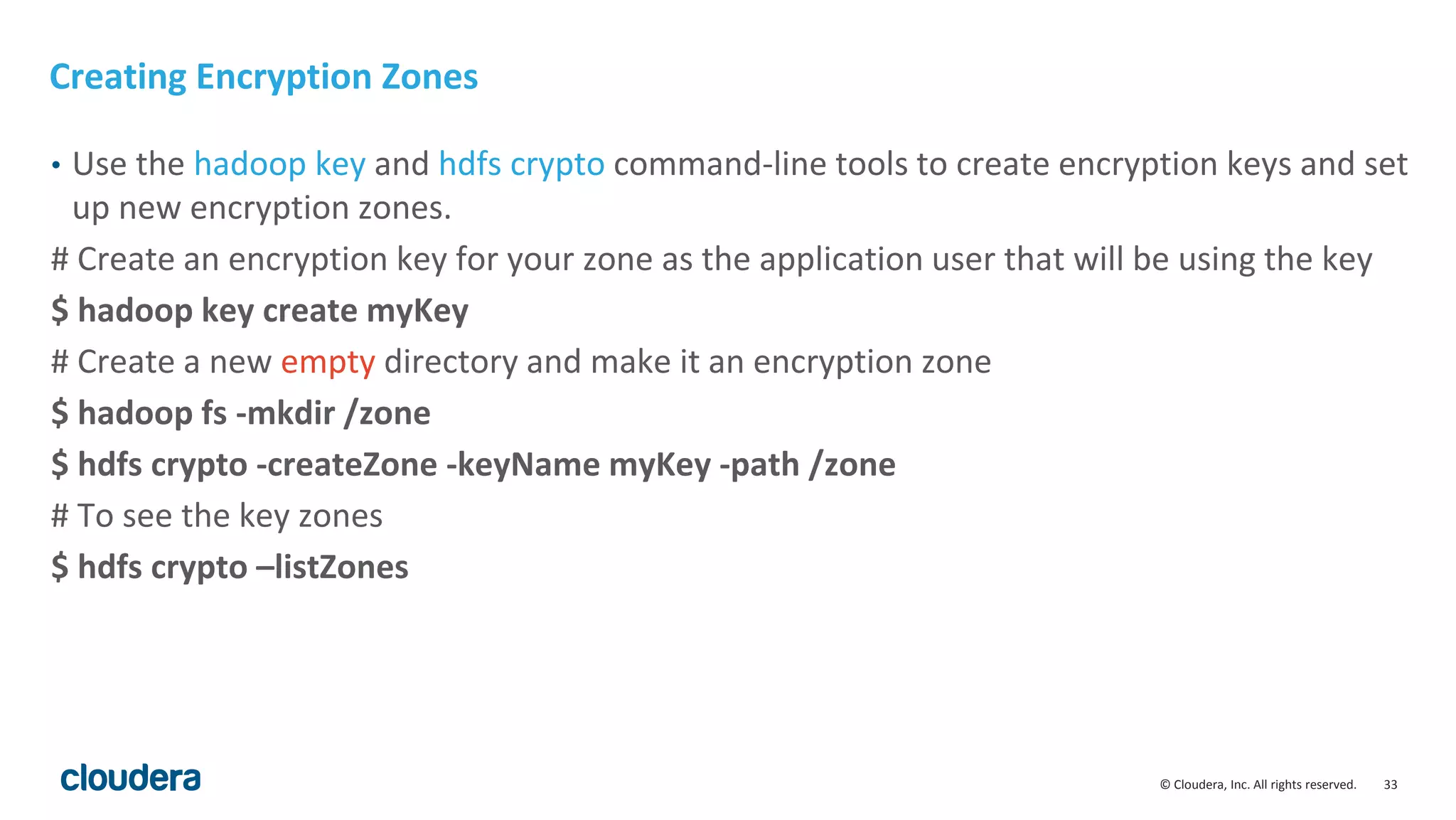
The document provides an overview of risk management for data within Cloudera's platform, focusing on HDFS encryption and key management. It outlines security requirements for storing sensitive data, key management concepts, and the implementation of encryption using various techniques such as AES and RSA. Additionally, it details the planning, prerequisites, and best practices for deploying encryption in Hadoop environments.