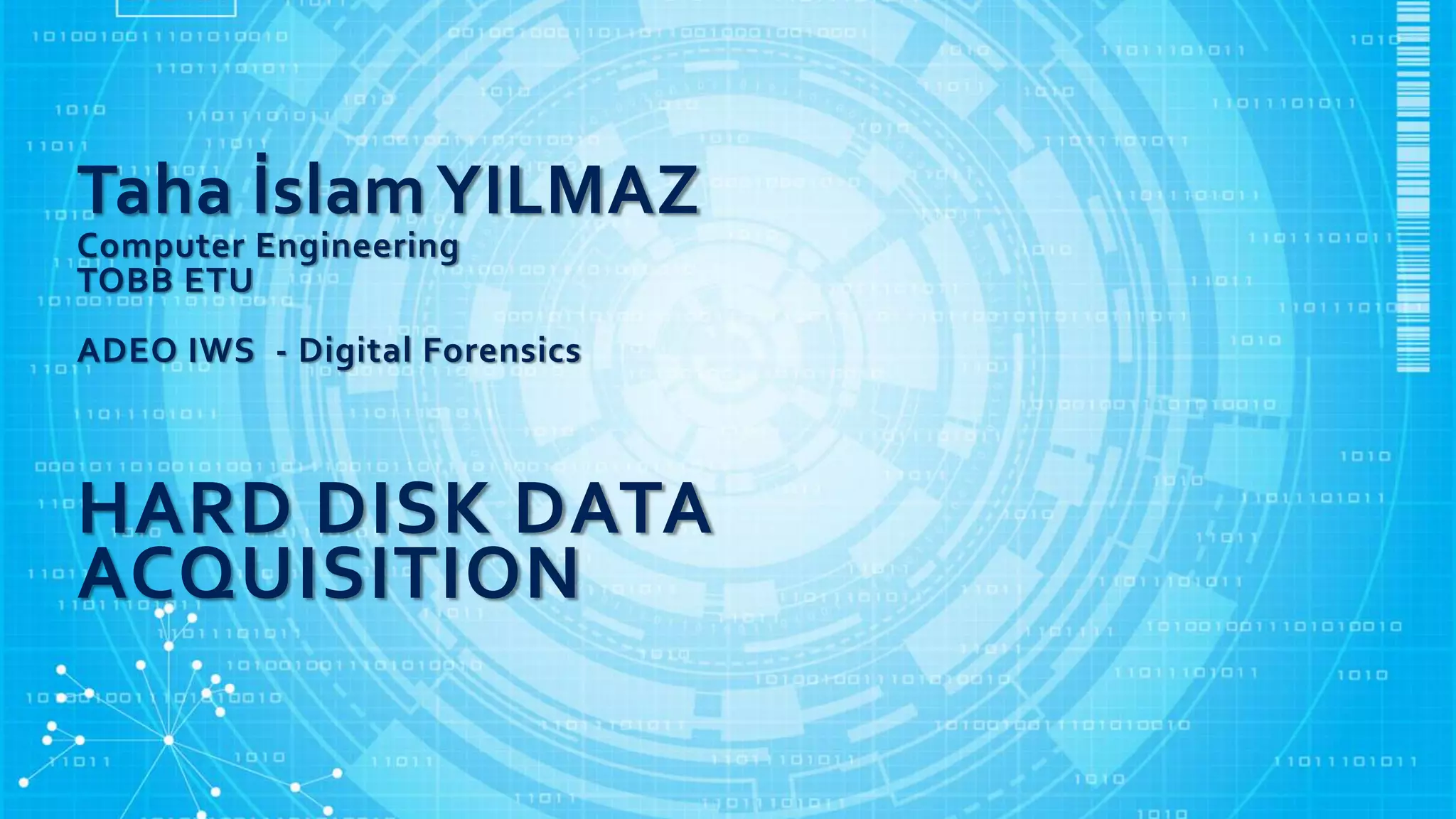
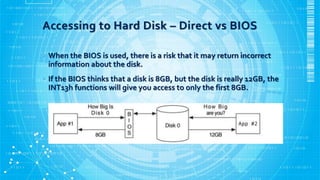
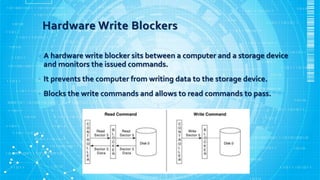
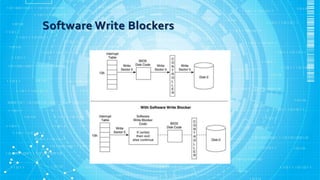
The document discusses various aspects of hard disk data acquisition for digital forensics purposes. It covers the general acquisition procedure, data acquisition layers, requirements for acquisition tools and hardware/software write blockers, and considerations around accessing disks directly versus through BIOS, dead versus live acquisitions, hidden areas like HPA and DCO, and writing output data and image file formats.