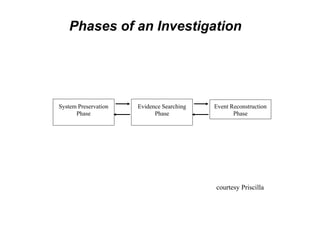
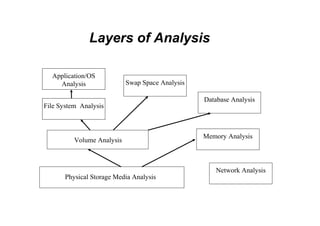
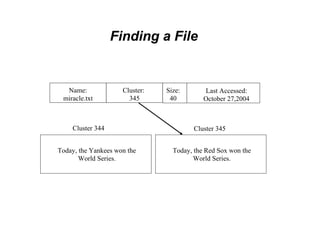
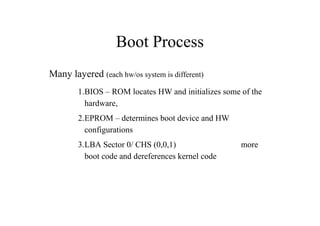
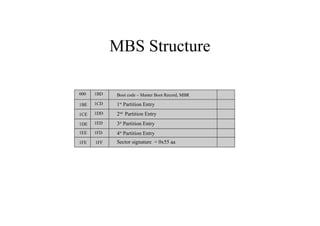
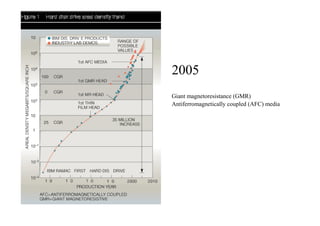
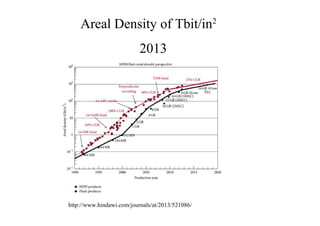
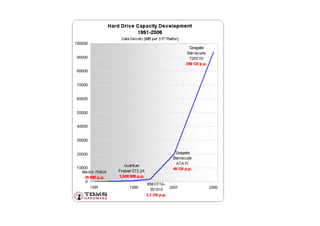
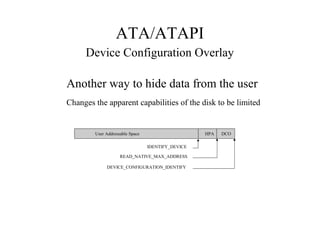
This document discusses the topics of computer/digital forensics including hard drive imaging, volume and file system analysis, tools, and case studies. It describes the acquisition of digital evidence from devices, analyzing the evidence while maintaining integrity, and preparing the evidence for trial. The key aspects covered are hard disk imaging standards, volume layout and partitioning, file system analysis formats like FAT, NTFS, EXT2/3, and UFS, as well as forensic analysis techniques and layers.