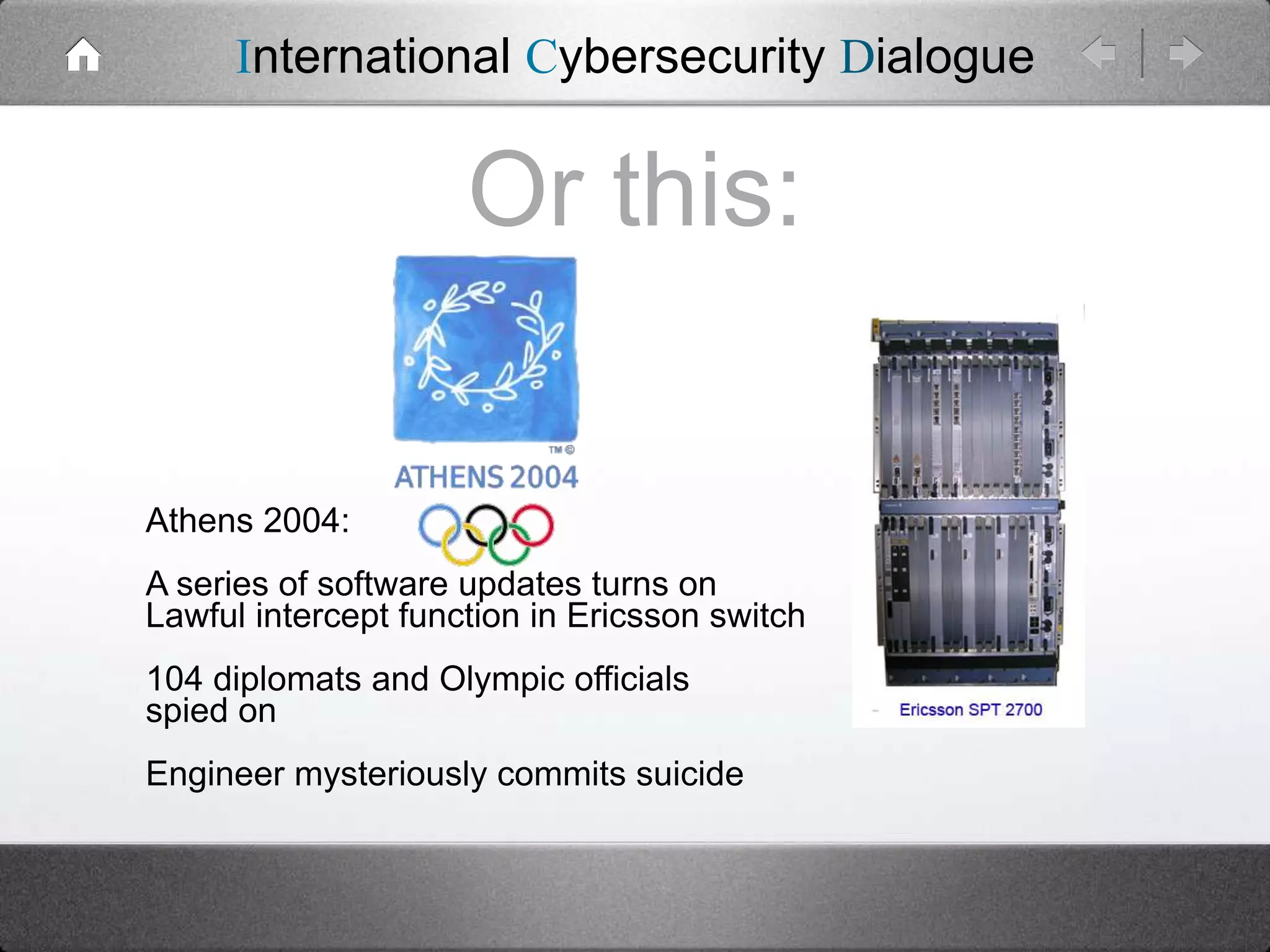
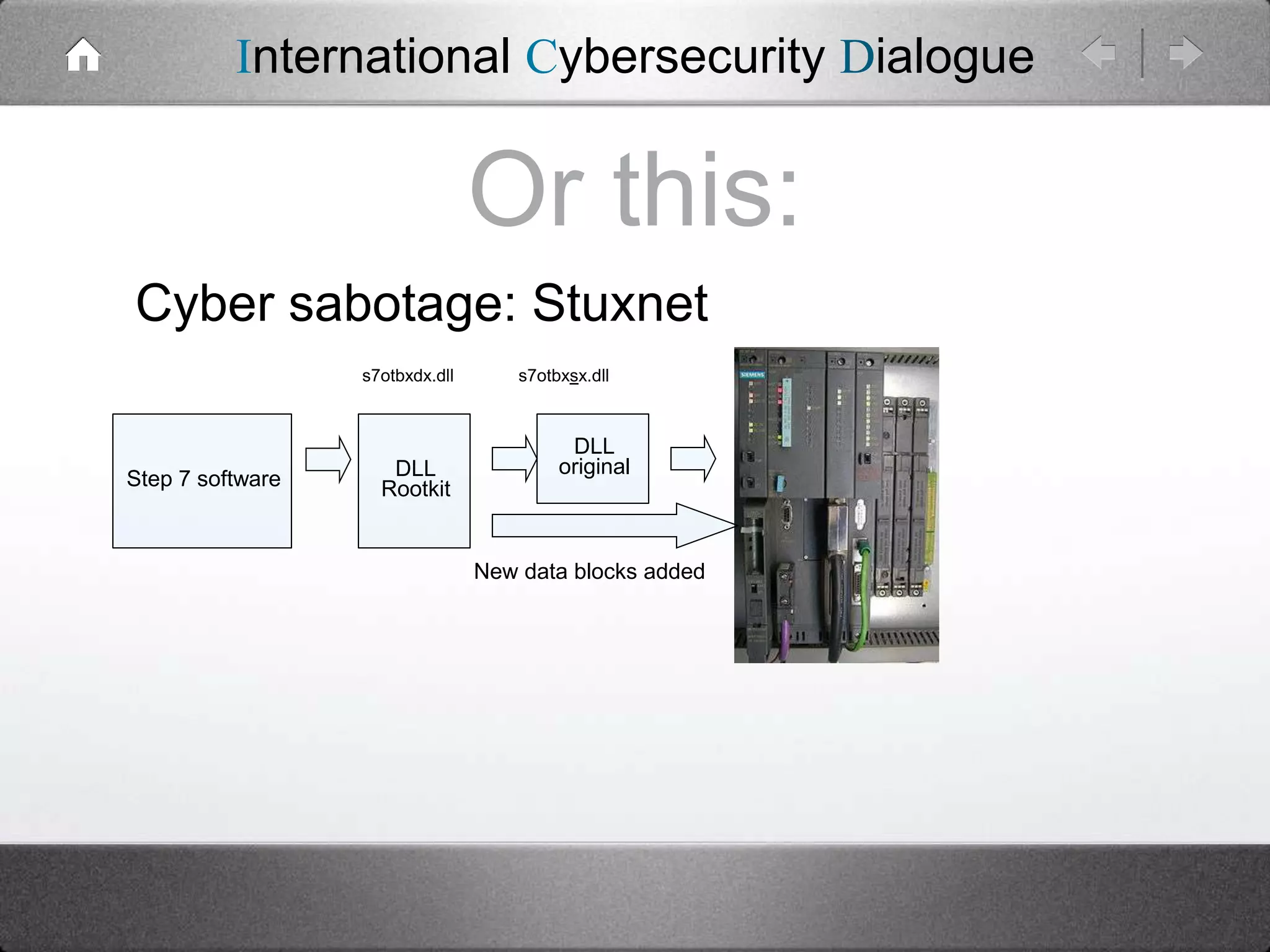
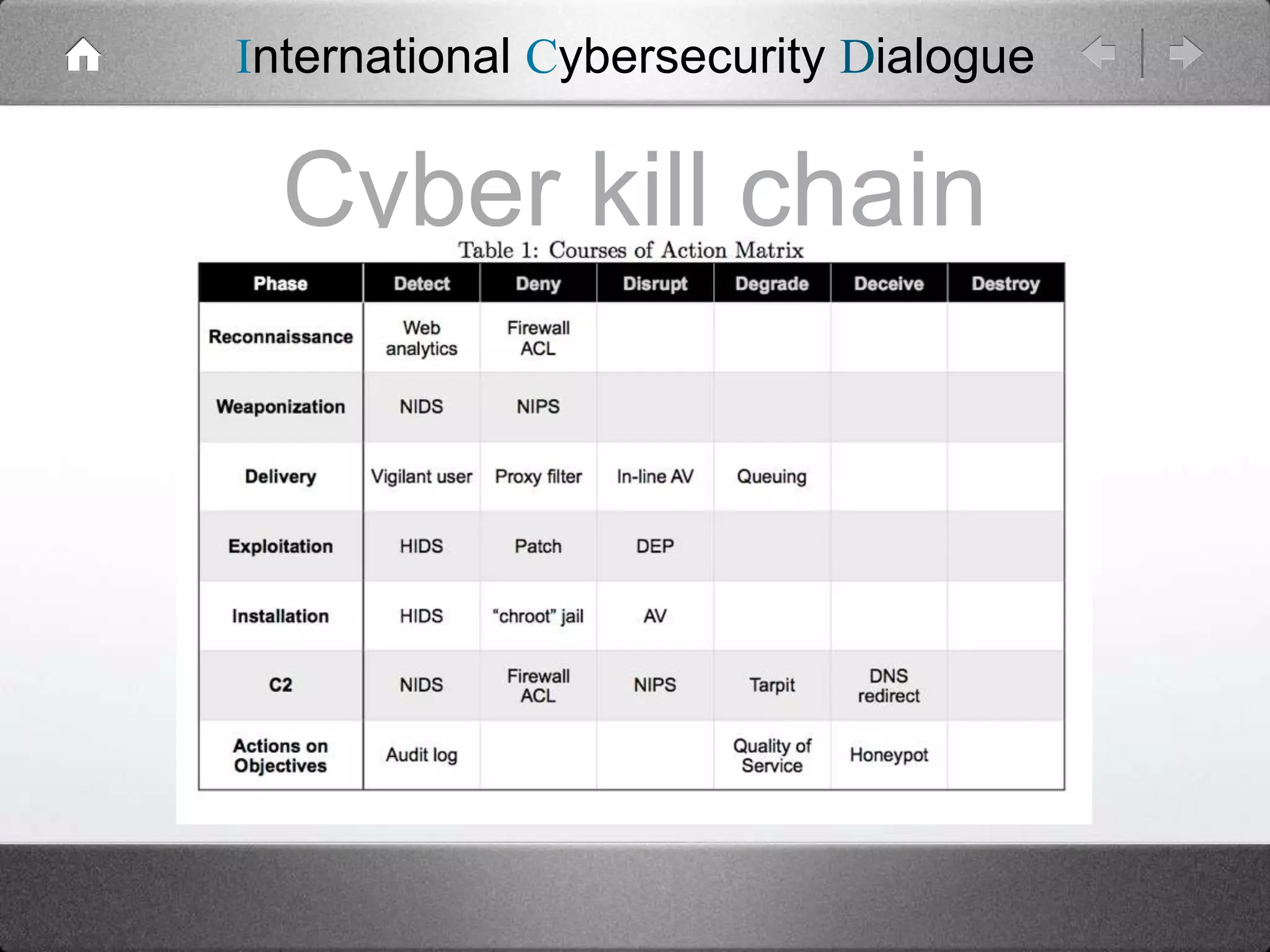
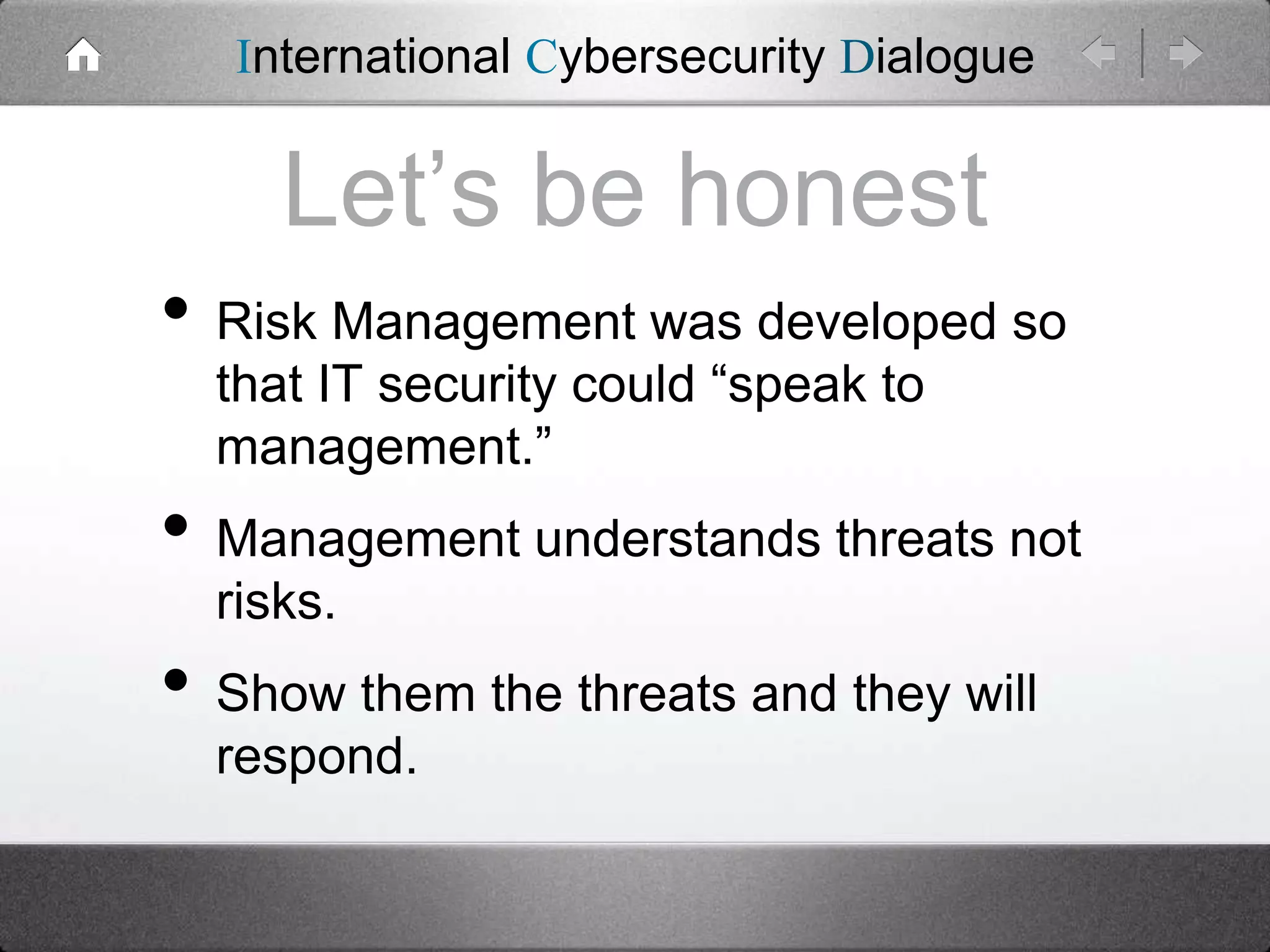
The document critiques traditional risk management strategies in cybersecurity, arguing that they often have unachievable goals and focus on random events rather than targeted attacks. It suggests a shift towards threat-based security, emphasizing the need for understanding specific threats and employing intelligence for effective threat management. Additionally, it highlights the inadequacies of assessing IT assets, vulnerabilities, and their potential value accurately.