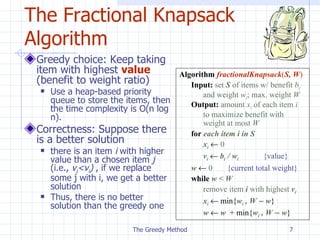
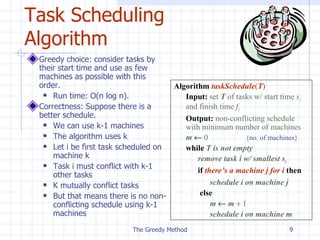
The document discusses the greedy method algorithm design paradigm. It can be used to solve optimization problems with the greedy-choice property, where choosing locally optimal decisions at each step leads to a globally optimal solution. Examples discussed include fractional knapsack problem, task scheduling, and making change problem. The greedy algorithm works by always making the choice that looks best at the moment, without considering future implications of that choice.

![Outline and Reading The Greedy Method Technique ( §5.1 ) Fractional Knapsack Problem ( §5.1.1 ) Task Scheduling ( §5.1.2 ) Minimum Spanning Trees ( §7.3 ) [future lecture] The Greedy Method](https://image.slidesharecdn.com/greedy-110907233019-phpapp02/85/Greedy-2-320.jpg)


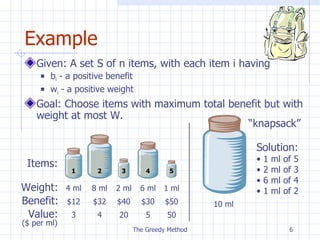
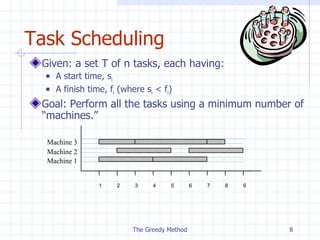
![Example Given: a set T of n tasks, each having: A start time, s i A finish time, f i (where s i < f i ) [1,4], [1,3], [2,5], [3,7], [4,7], [6,9], [7,8] (ordered by start) Goal: Perform all tasks on min. number of machines The Greedy Method 1 9 8 7 6 5 4 3 2 Machine 1 Machine 3 Machine 2](https://image.slidesharecdn.com/greedy-110907233019-phpapp02/85/Greedy-10-320.jpg)