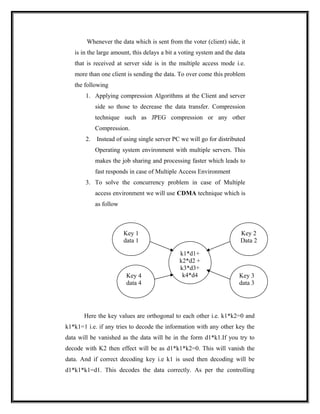
In the proposed "Global Wireless E-Voting" system:
1. Votes would be cast using an electronic voting machine but stored on a remote server through radio waves, preventing tampering with vote counts on individual machines.
2. The machines would be made intelligent to verify voter eligibility by scanning eye patterns, reducing the risk of corruption.
3. Even if a machine is damaged, elections would not be disrupted since votes are stored remotely on a server.



![Here the matrix pattern of this type of picture may be as
R G B R G B R G B
[12 a1 15] [11 21 54] [25 f4 5c]
[2d 1c 5A] [99 85 57] [2c fa b3]
[1b b1 a2] [11 b1 ac] [50 b4 5F]
[CA 1f 3c] [11 2c d4] [03 ca e5]
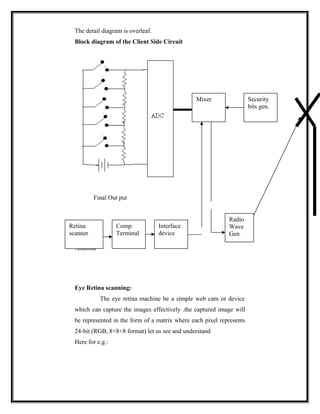
Interface device
This is an electronic kit which converts the input digital signals
such as (retina pattern votes+ secure bits) to radio waves.
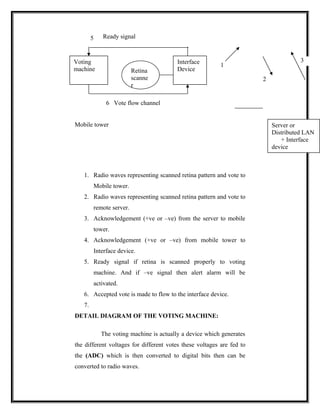
Working of whole system
Whenever voters enter to voting booth then he will be instructed to
directly look at retina scanning machine at this time the machine
scans the retina. once retina scanning properly confirmed then it
sent signal to the voting machine as to accept the vote it will be
powered on .then voter is made to vote. Now the whole data
including the retina pattern is sent to interfacing device which
convert into radio waves of mobile frequency range and these radio
waves are sent to mobile tower and then to the remote server,
where the authentication and voters identification is stored into a
secured database. The received data is first converted into digital
format from the radio waves through the interface device kept at
the server side, and then retina pattern and vote separated. Next the
retina pattern is matched against the existing database .If match is](https://image.slidesharecdn.com/globalwirelesse-voting-130306103239-phpapp02/85/Global-wireless-e-voting-6-320.jpg)