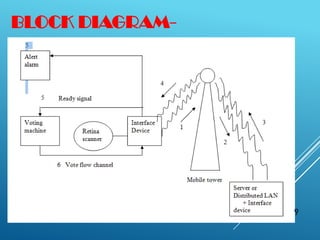
This document proposes a system for global wireless e-voting. It summarizes the current voting system and its disadvantages like need for re-elections and inability to check voter eligibility. The proposed system allows anyone to vote from anywhere via the internet after retina scanning authentication. The voter's choice is encrypted and sent to a remote server for verification and counting. Several security measures like encryption keys are discussed to ensure protection of votes. Technical aspects like use of mobile towers, interfaces and databases are described. Challenges around security, efficiency and geographical reach are also covered along with ideas to enhance the system for SMS voting and use over the internet.


![Is it legally
possible to vote
via the Internet?
[Law]
How can electronic
voting via the Internet
work technically?
[Technology]
Does e-Voting raise
the voter turnout?
[Sociopolitics]
Law Technogy Sociopolitics
Overview
3](https://image.slidesharecdn.com/globalwirelesse-voting-130919110455-phpapp01/85/Global-wireless-e-voting-3-320.jpg)