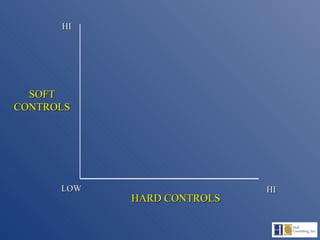
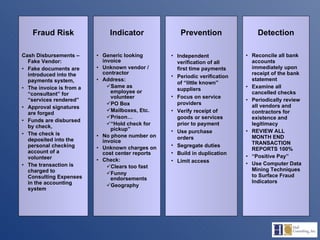
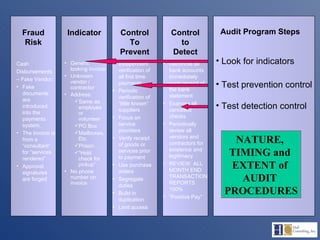
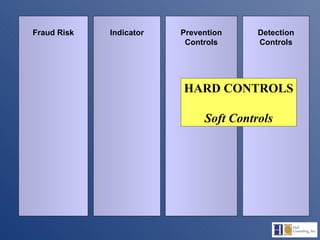
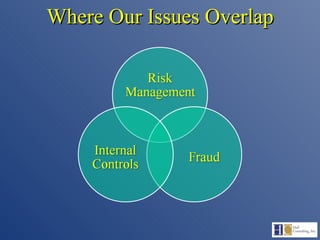
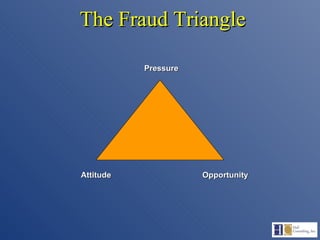
The document discusses the complexities of fraud management, highlighting the vulnerabilities in organizational controls and the significance of fraud risk assessment, prevention, and detection mechanisms. It emphasizes the importance of governance, internal controls, and employee awareness in mitigating fraud risks, while detailing common fraud scenarios and prevention strategies. Key areas include the role of management, employee attitudes, and the need for comprehensive fraud risk management programs to safeguard organizational resources.
![Fraud and Internal Controls: Fraud Prevention, Detection and Incident Handling John J. Hall, CPA Hall Consulting, Inc. [email_address]](https://image.slidesharecdn.com/fraudandinternalcontrolslinkedinapril2011-13012338591302-phpapp01/75/Fraud-And-Internal-Controls-Linked-In-April-2011-1-2048.jpg)





































![SAS 99: Consideration of Fraud in a Financial Statement Audit Auditor Responsibilities: “ This statement [SAS 99] established standards and provides guidance to auditors in fulfilling that responsibility, as it related to fraud, in an audit of financial statements conducted in accordance with generally accepted auditing standards (GAAS).”](https://image.slidesharecdn.com/fraudandinternalcontrolslinkedinapril2011-13012338591302-phpapp01/85/Fraud-And-Internal-Controls-Linked-In-April-2011-42-320.jpg)