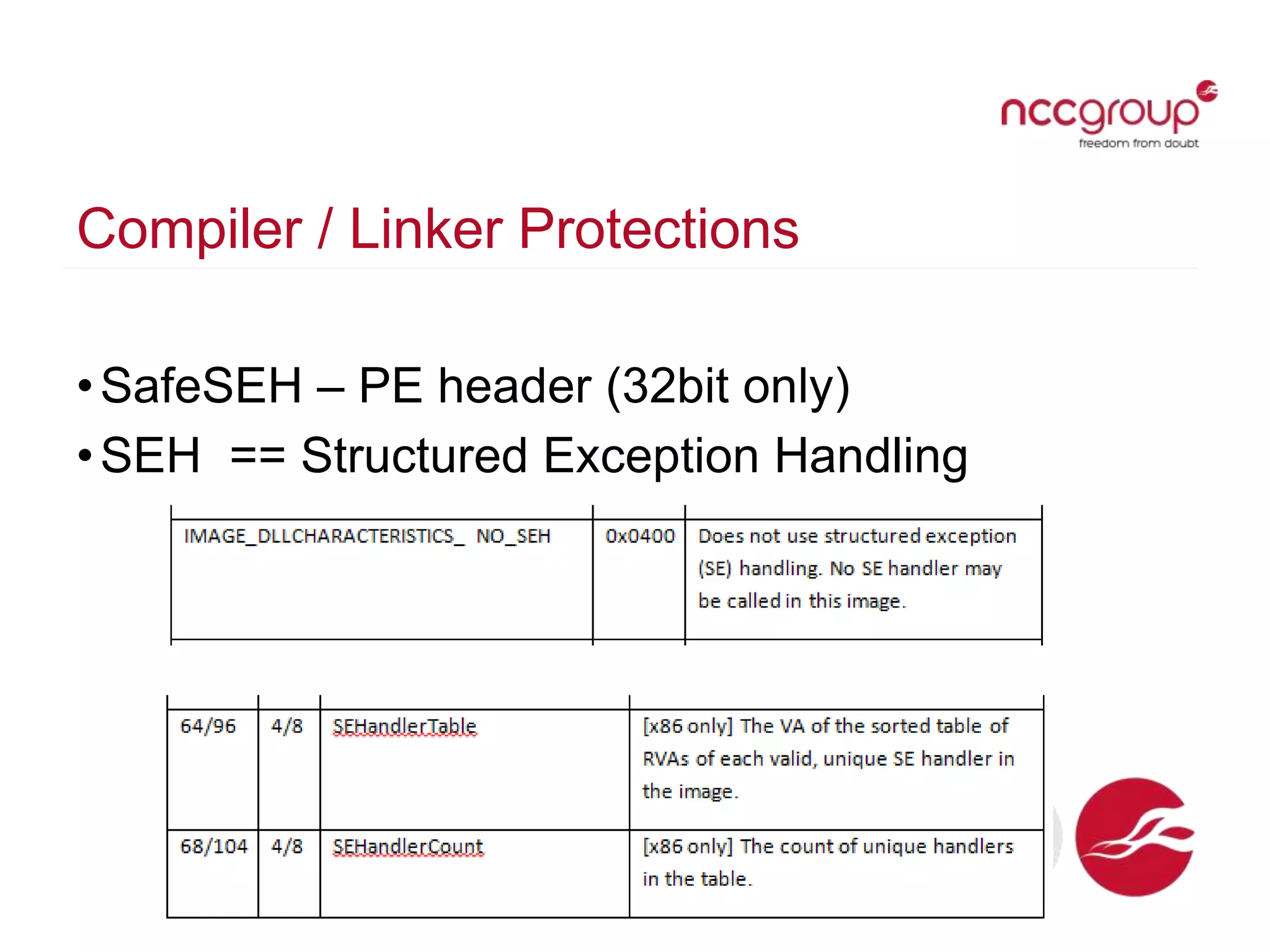
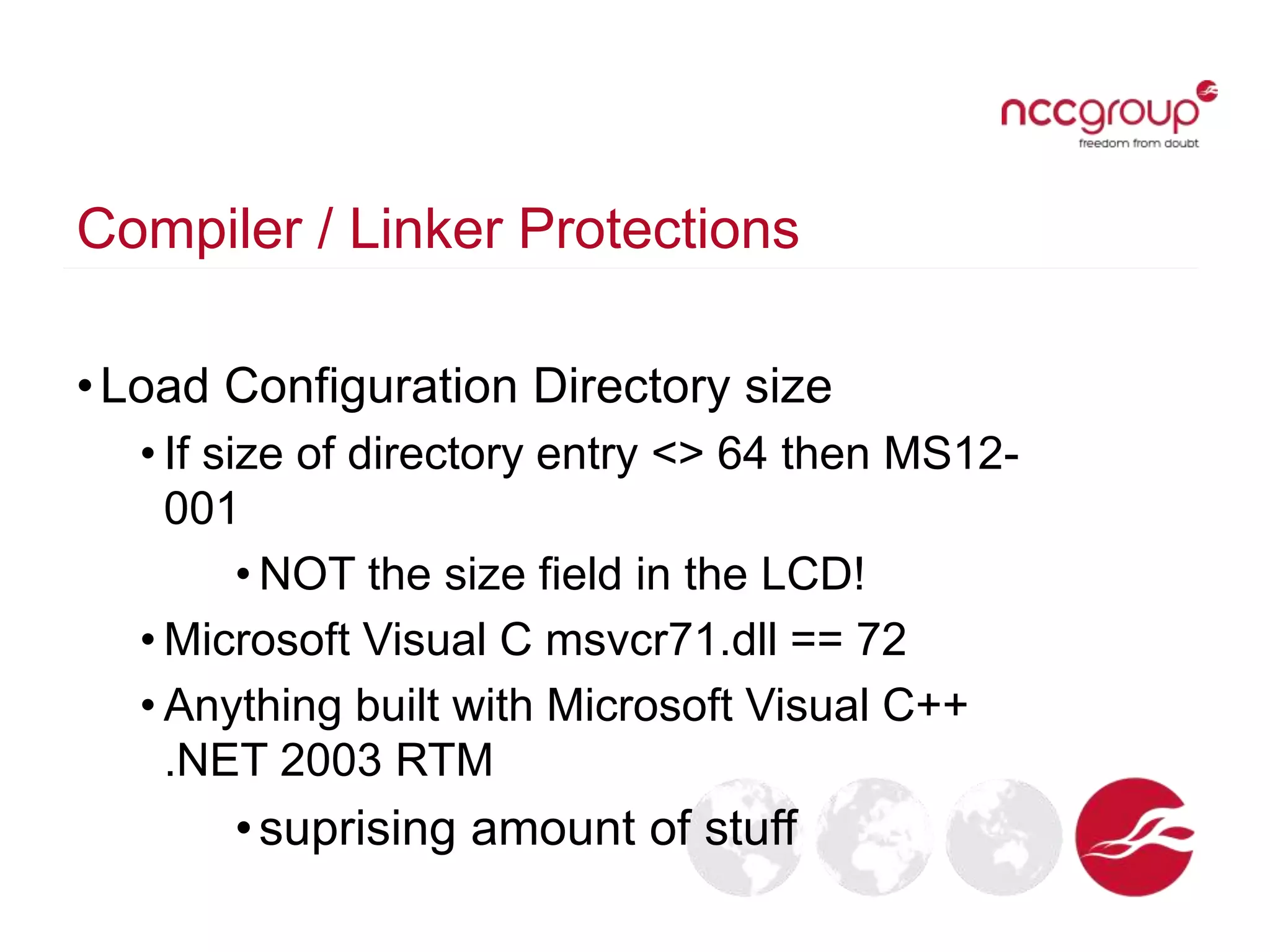
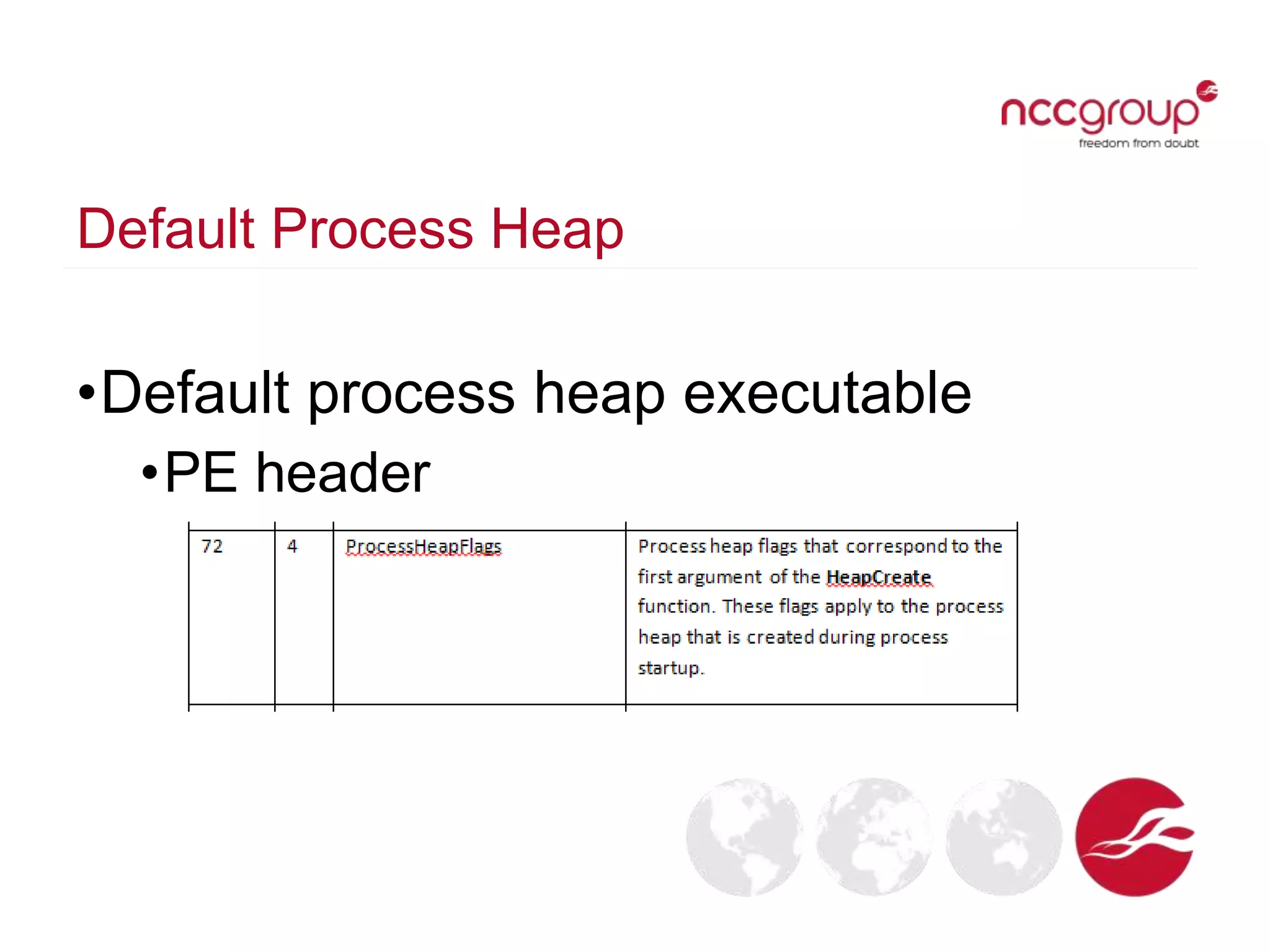
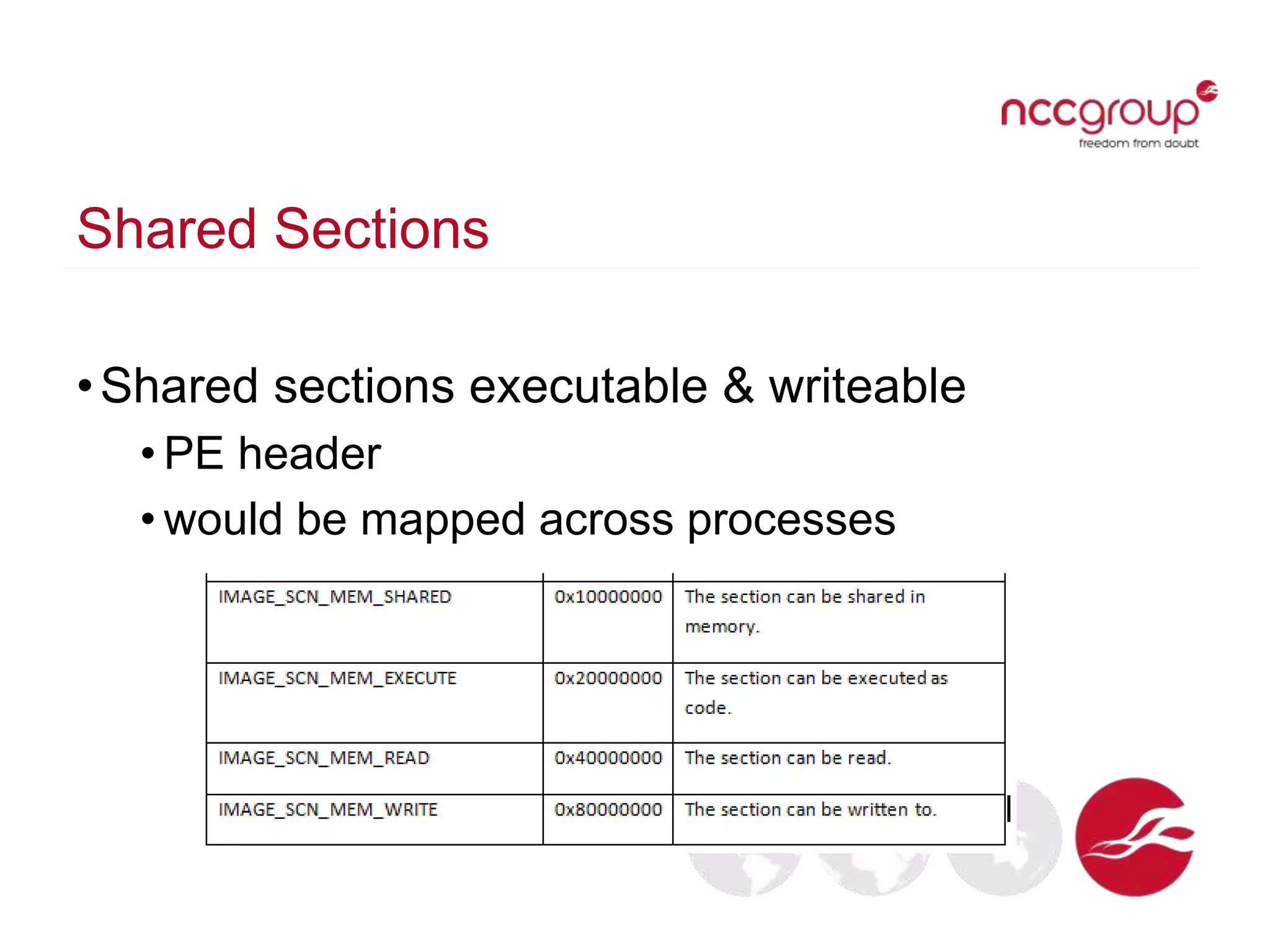
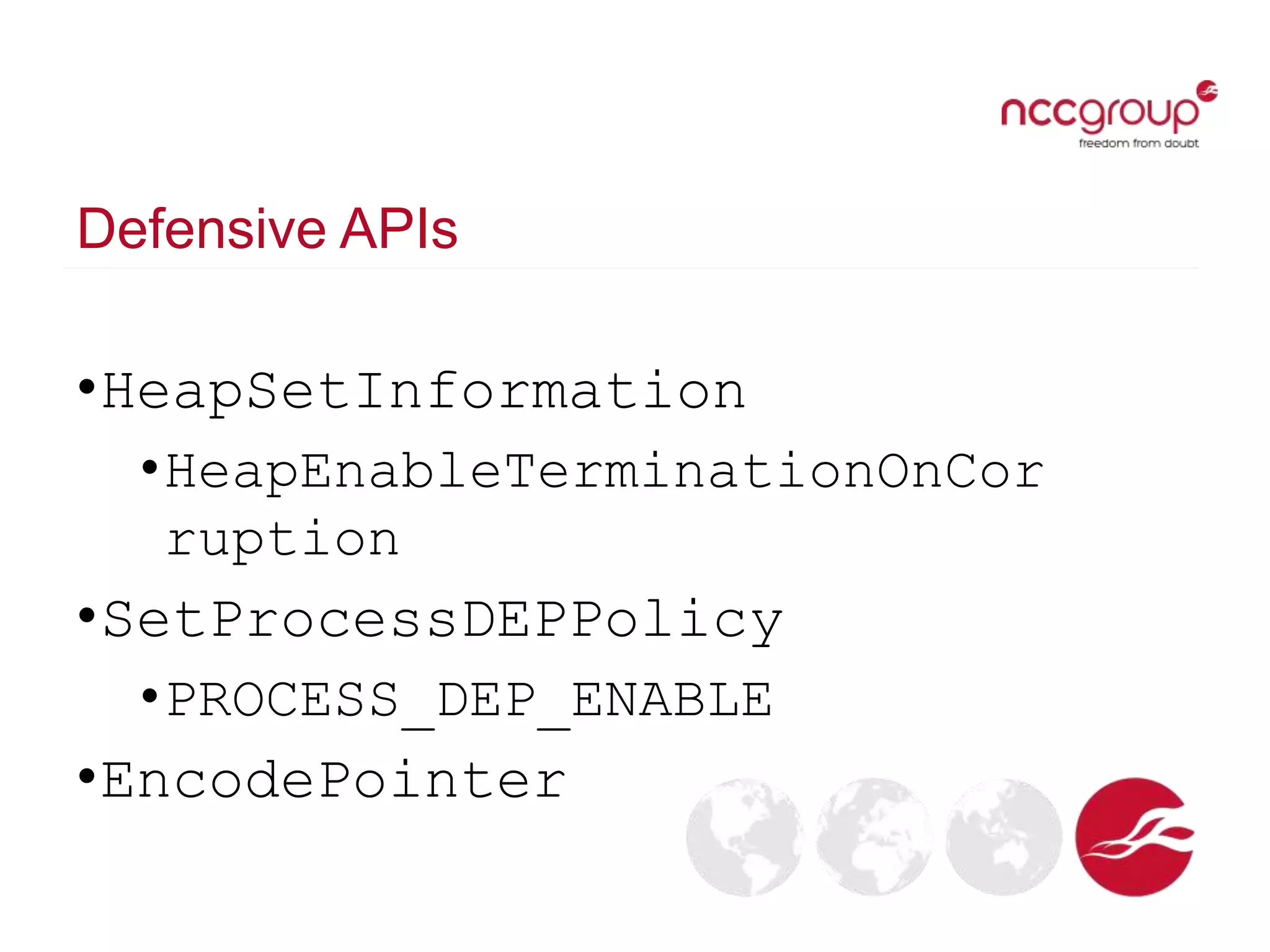
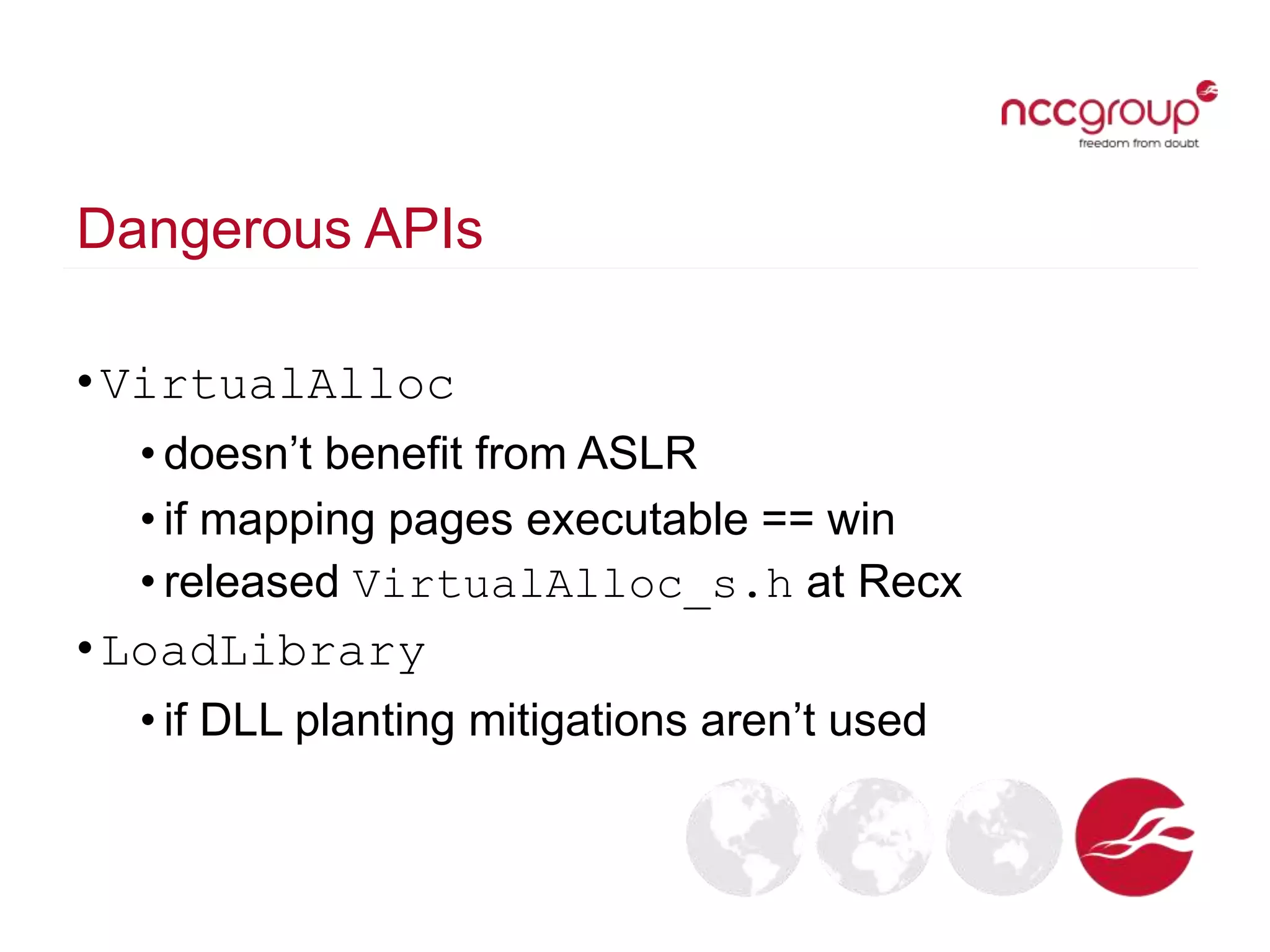
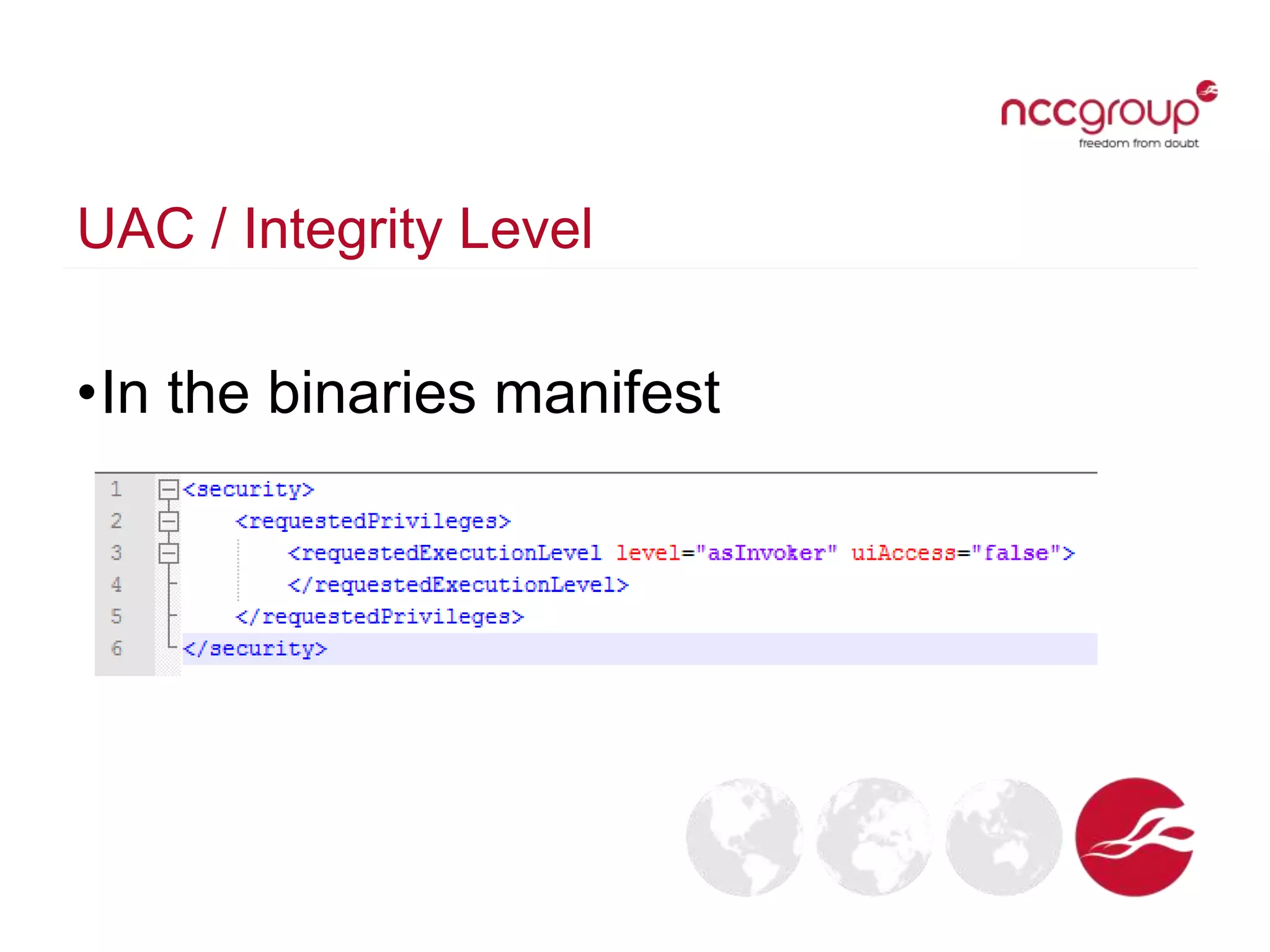
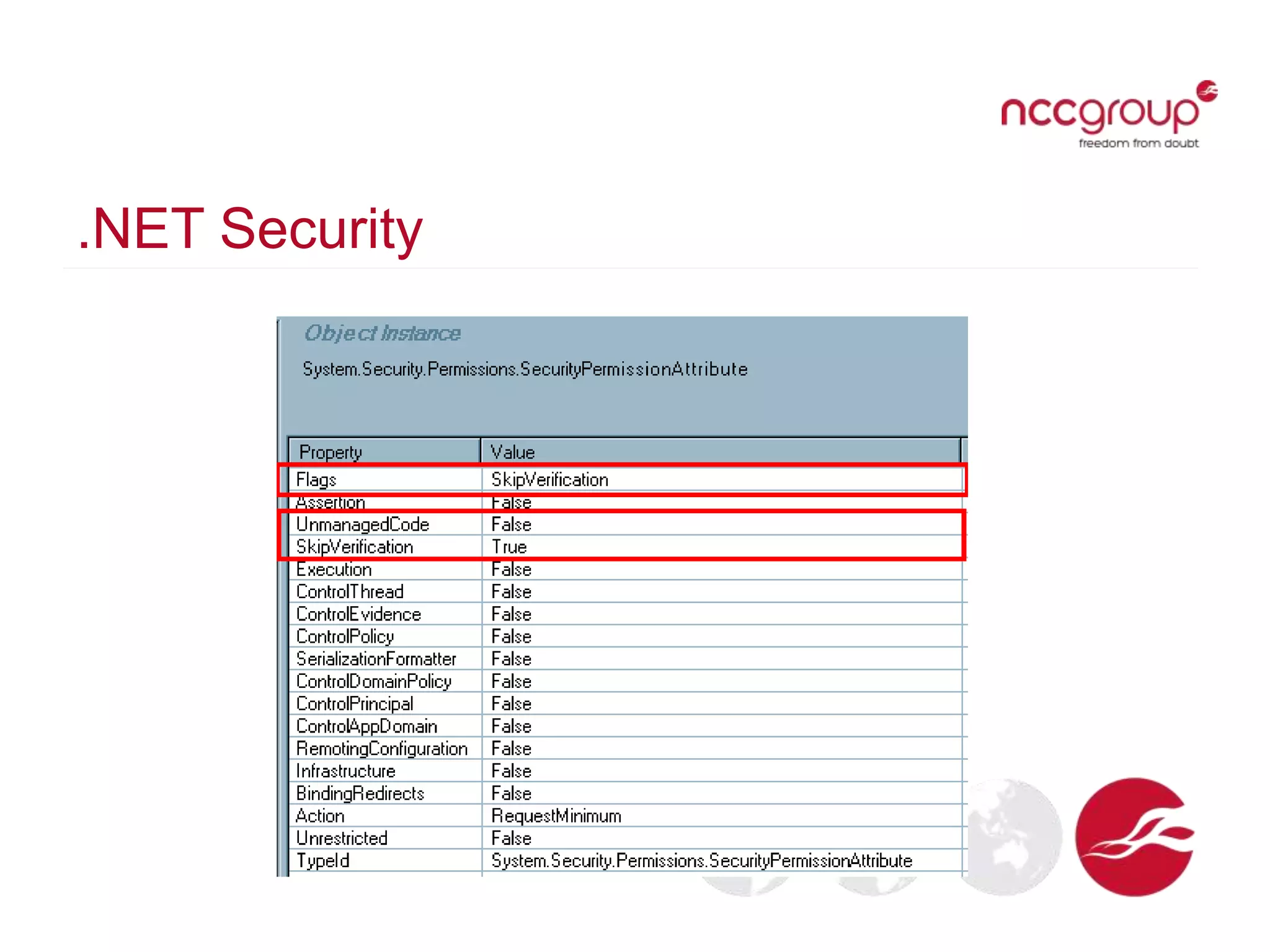
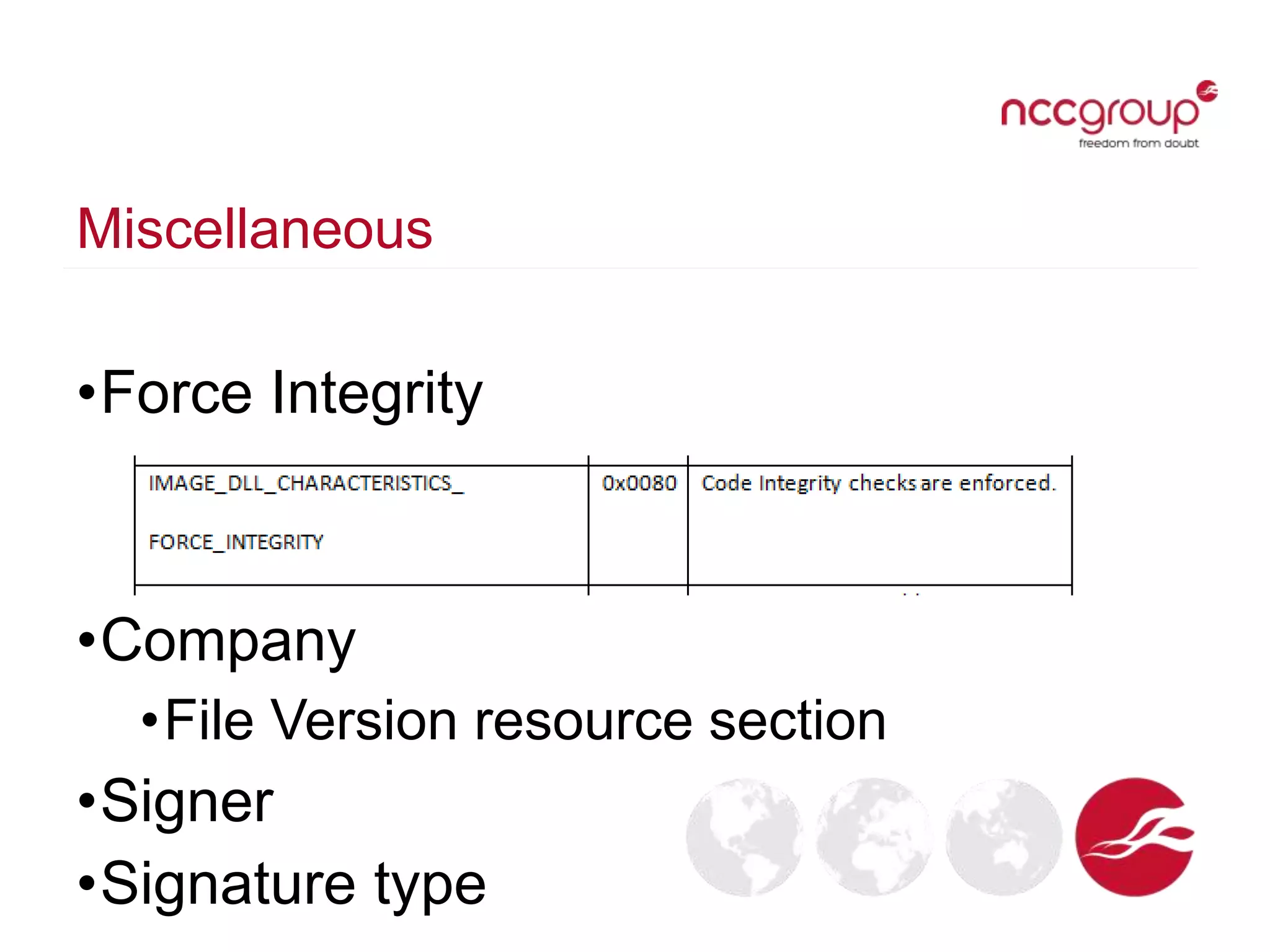
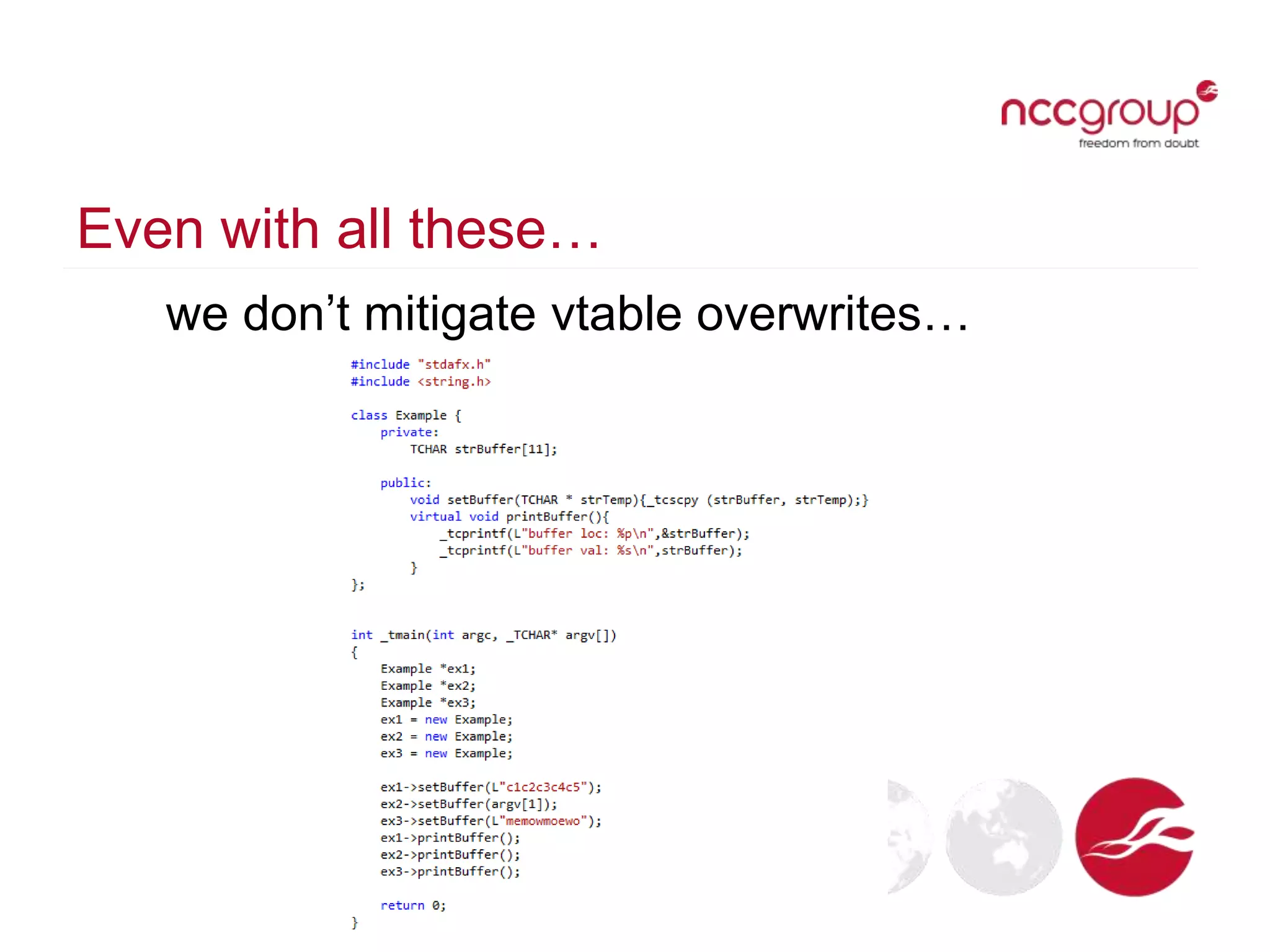
The document discusses analyzing Windows binaries to identify weaknesses without access to debug symbols or source code. It describes checking the binaries for compiler/linker protections like ASLR, DEP, stack cookies; banned and dangerous API usage; .NET security settings; and defensive coding practices. The author then demonstrates their tool for performing this analysis on binaries, noting existing tools' limitations, and concludes some binaries may have lower defenses without symbol information.







![Why? - Defensive
•A product == many vendors
•e.g. Adobe Reader 10.0 == [guess?]
•License != source code
•License != private symbols
•SDL assurance…
• getting the free security features enabled
•End user assurance / threat awareness
• Understanding where you need EMET](https://image.slidesharecdn.com/2012-10-11-findingtheweaklinkinbinaries-150130084321-conversion-gate02/75/Finding-The-Weak-Link-in-Windows-Binaries-9-2048.jpg)