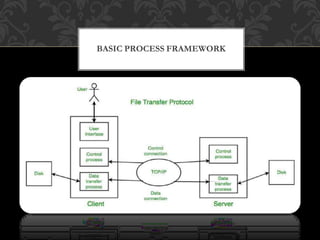
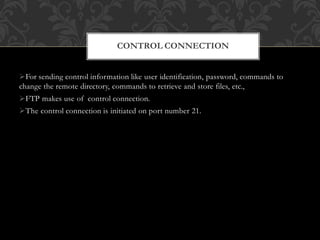
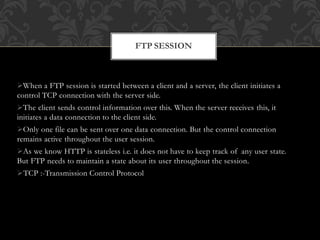
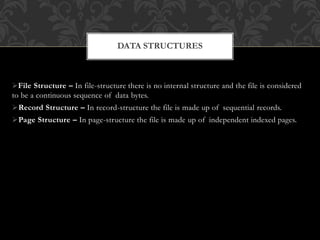
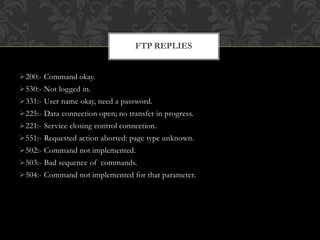
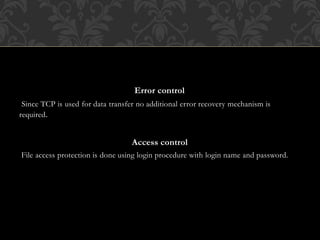
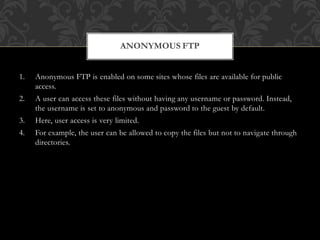
FTP (File Transfer Protocol) is an application layer protocol for transferring files between a client and server over TCP. It uses separate connections for control information (on port 21 by default) and data transfer (on port 20 by default). Common FTP commands allow users to navigate directories, retrieve and store files. FTP supports different data representations like ASCII, EBCDIC and binary. It provides features like error control, access control and transmission modes like stream, block and compressed. Variants include FTPS (FTP over SSL/TLS), FTPES (FTP over explicit SSL/TLS) and TFTP (trivial file transfer without authentication over UDP).