Embed presentation
Download as PDF, PPTX




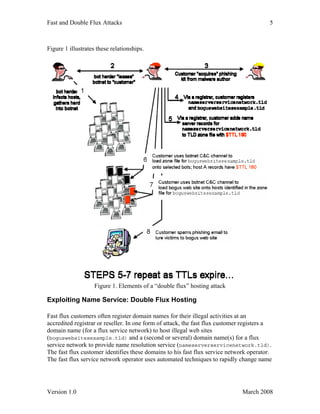








This document provides an overview of fast flux hosting and double flux attacks. It describes how these techniques: 1) Exploit botnets and compromised systems to rapidly change the IP addresses and domains associated with illegal websites and DNS servers, frustrating efforts to take down these systems. 2) Involve underground business relationships where malware authors, bot herders, and fast flux service operators work together to facilitate criminal activities like phishing through these techniques. 3) Recommends education and securing vulnerable systems as ways to reduce the number of compromised systems that can be used in these botnets and fast flux attacks.












