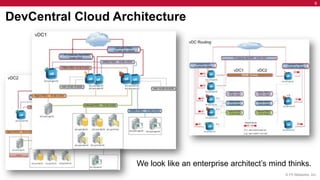
F5's DevCentral technical community website has moved to multiple virtual datacenters hosted by Bluelock in the public cloud. This allows DevCentral to adhere to best practices for scale, control, and security while gaining agility. It also provides an example for partners and the community of how F5 solutions can be run securely and with control in the cloud.



![4
F5 DevCentral
F5’s Global Technical Community
• Over 100,000 members worldwide
• 55% of visits originate outside U.S.
• Over 60,000 Forum Posts All Time
“F5 Networks has set the gold standard for
• iRules, iControl, Advanced all scripting environments combined with a
community site with its TCL based iRules
Design/Config, ISV solutions, and more! and DevCentral community.” - Zeus
Kerravala, ZK Research, 2012
“F5 has developed a large community of committed
• Critical platform for our customers and users [DevCentral] that fuels the use of iRules to
partners to build skills and connect with solve unique data center application
challenges, creating an increasingly loyal and
peers engaged user base.” - Gartner – Magic Quadrant for
“…DevCentral creates2010
ADCs, a modest network effect for
• Members express high product satisfaction F5 and it would be difficult for a competitor to
• Member NPS scores world class; over 2x replicate the large and growing library of custom
configuration and scripting templates available..." -
higher than non-member customers By Grady Burkett, CFA – SeekingAlpha.com
© F5 Networks, Inc.](https://image.slidesharecdn.com/f5dccloudslideshare-120611130203-phpapp02/85/F5-DevCentral-to-the-Cloud-4-320.jpg)