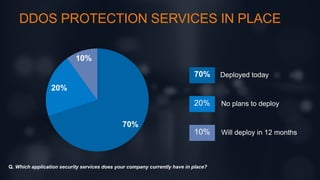
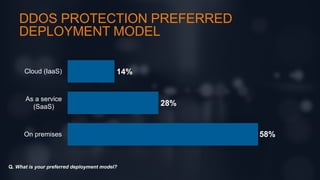
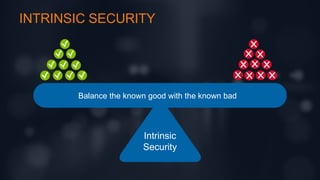
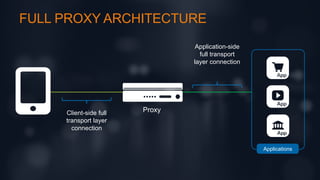
The document discusses intrinsic security as a critical element for effective hybrid DDoS protection, highlighting the increasing complexity and frequency of DDoS threats. It includes survey results on current application security services and preferred deployment models, indicating a shift towards cloud-based solutions. Additionally, it emphasizes the need for a balance of known good and bad elements in security approaches.