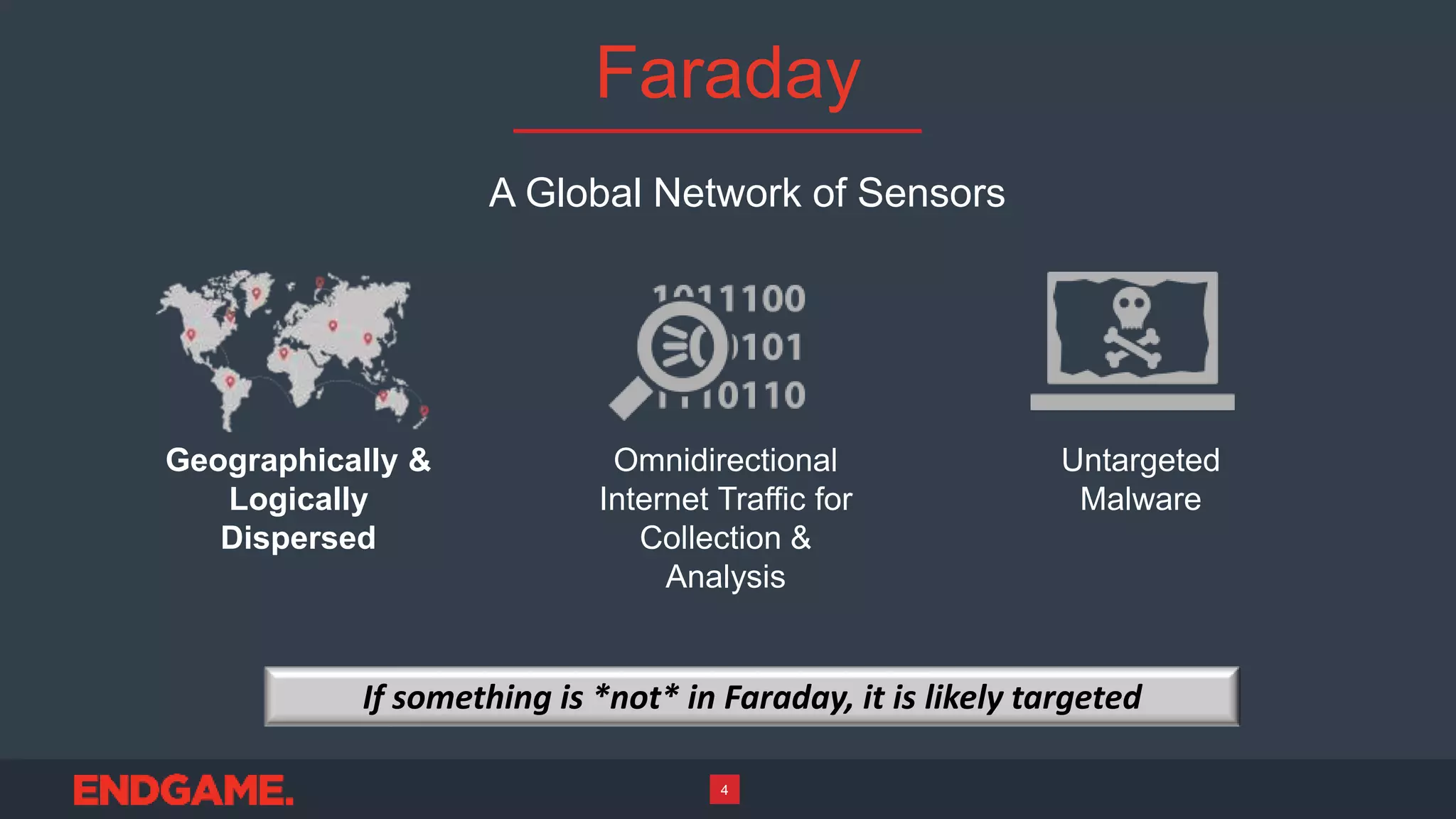
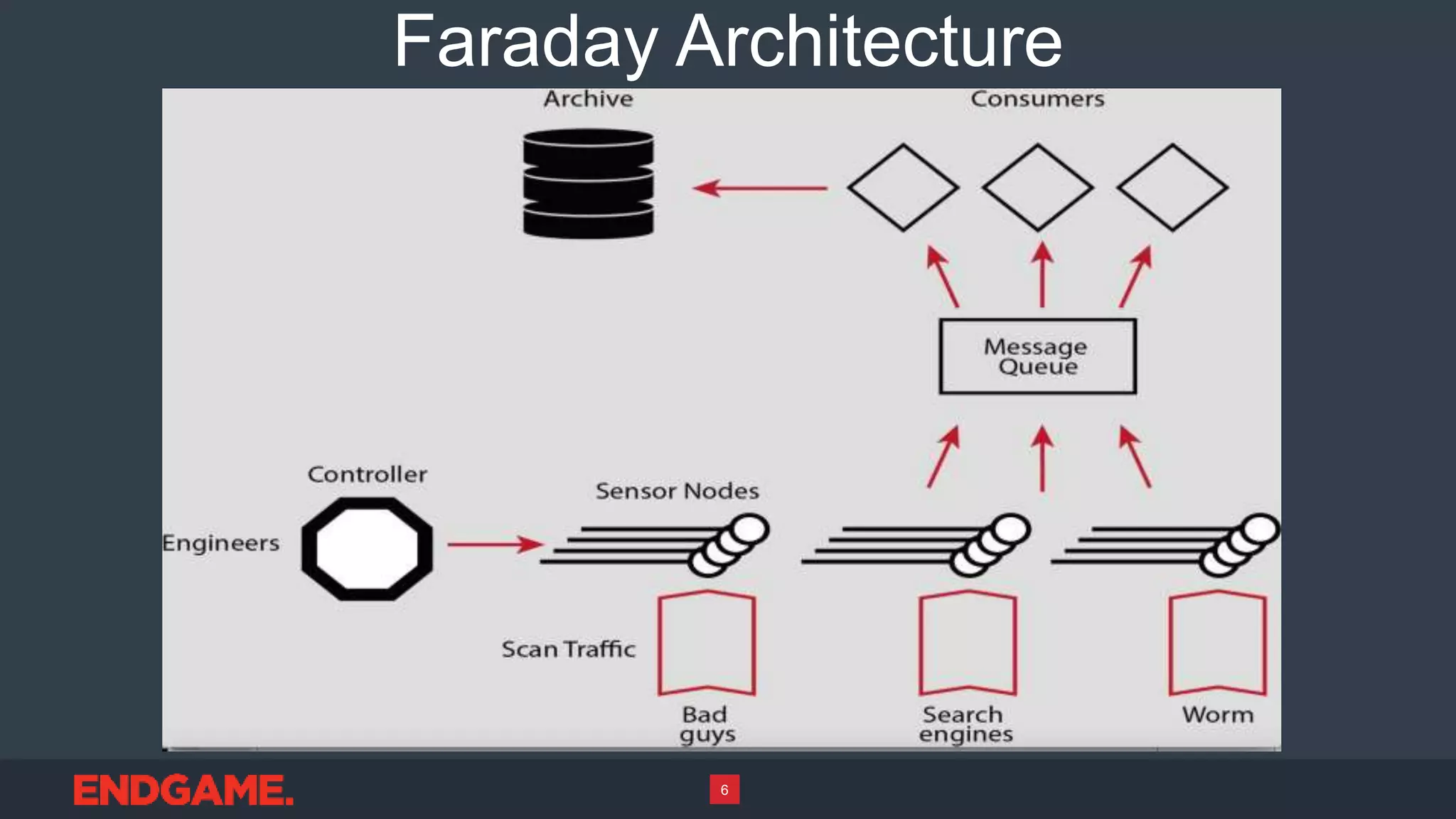
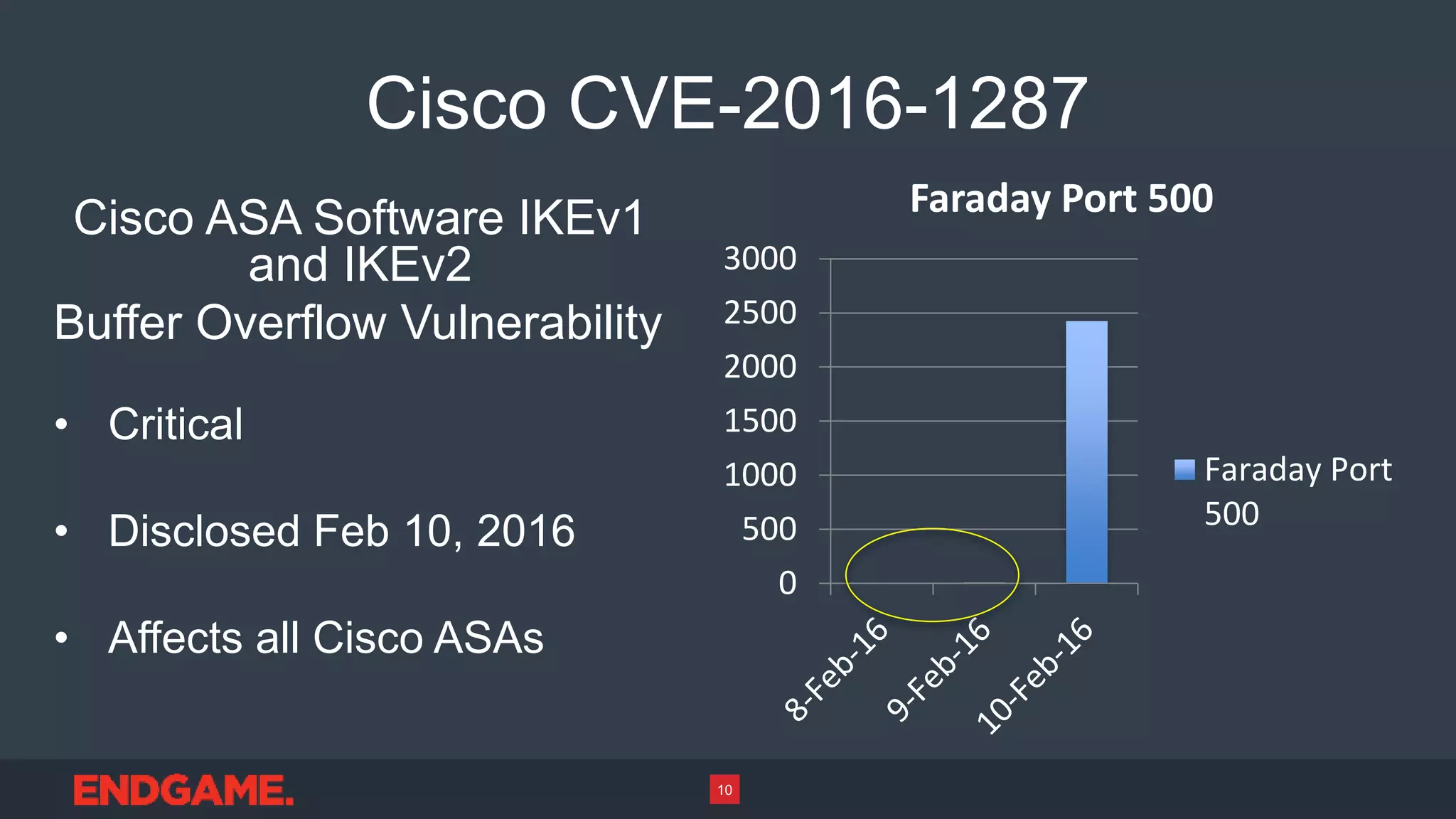
1) Faraday is a global network of sensors that collects untargeted malware and internet traffic geographically and logically dispersed to extract the malware signal from internet noise.
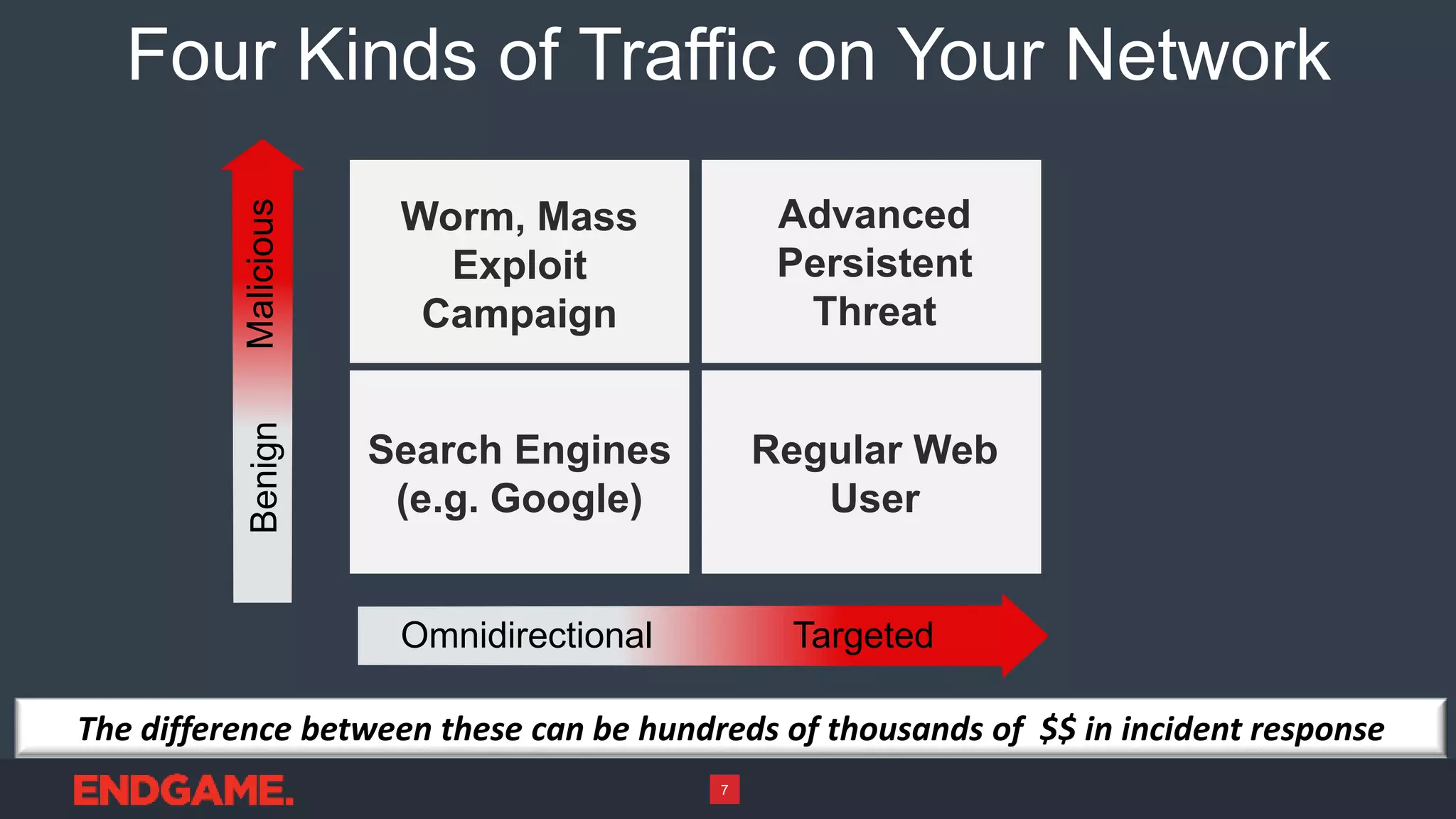
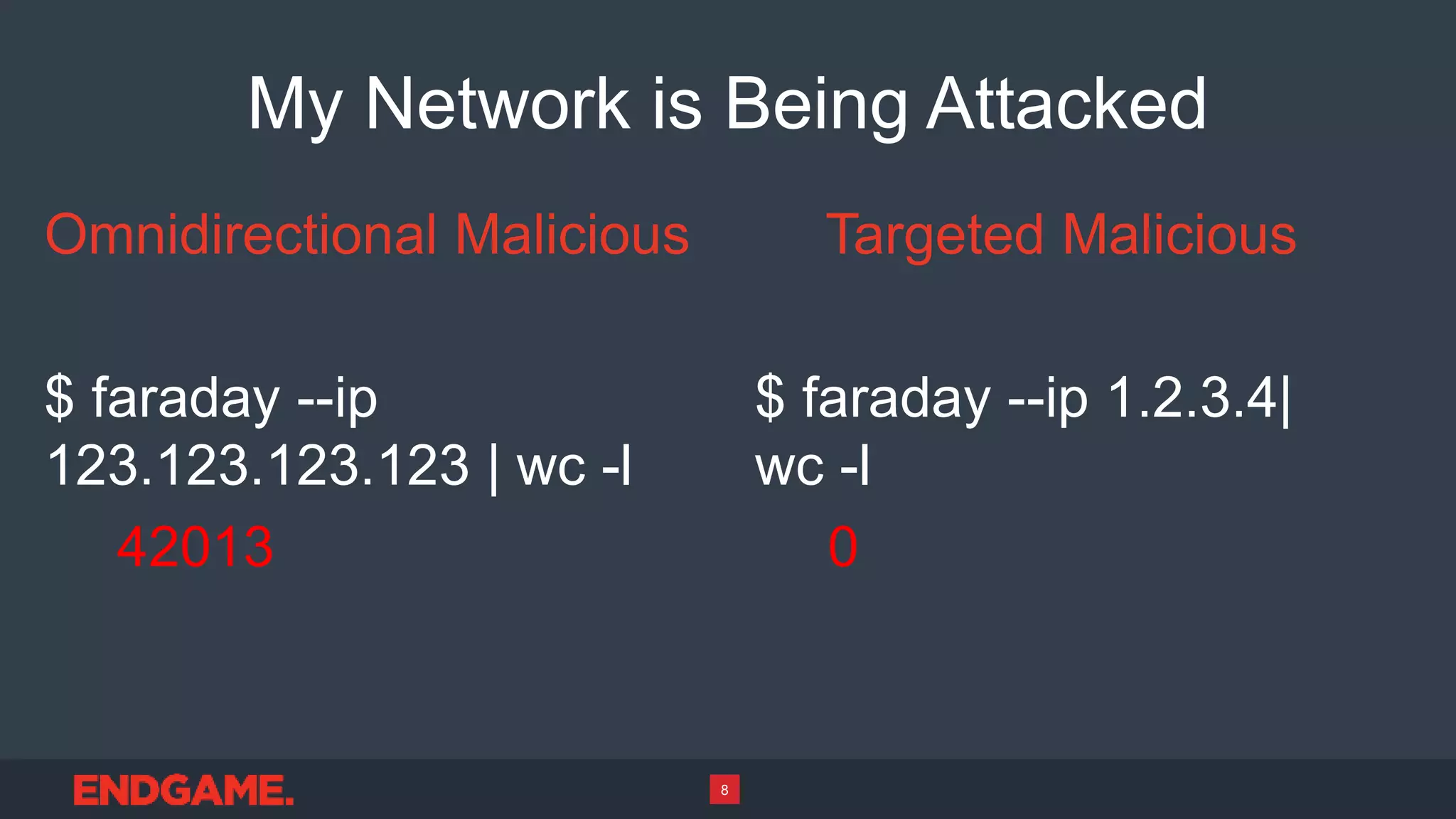
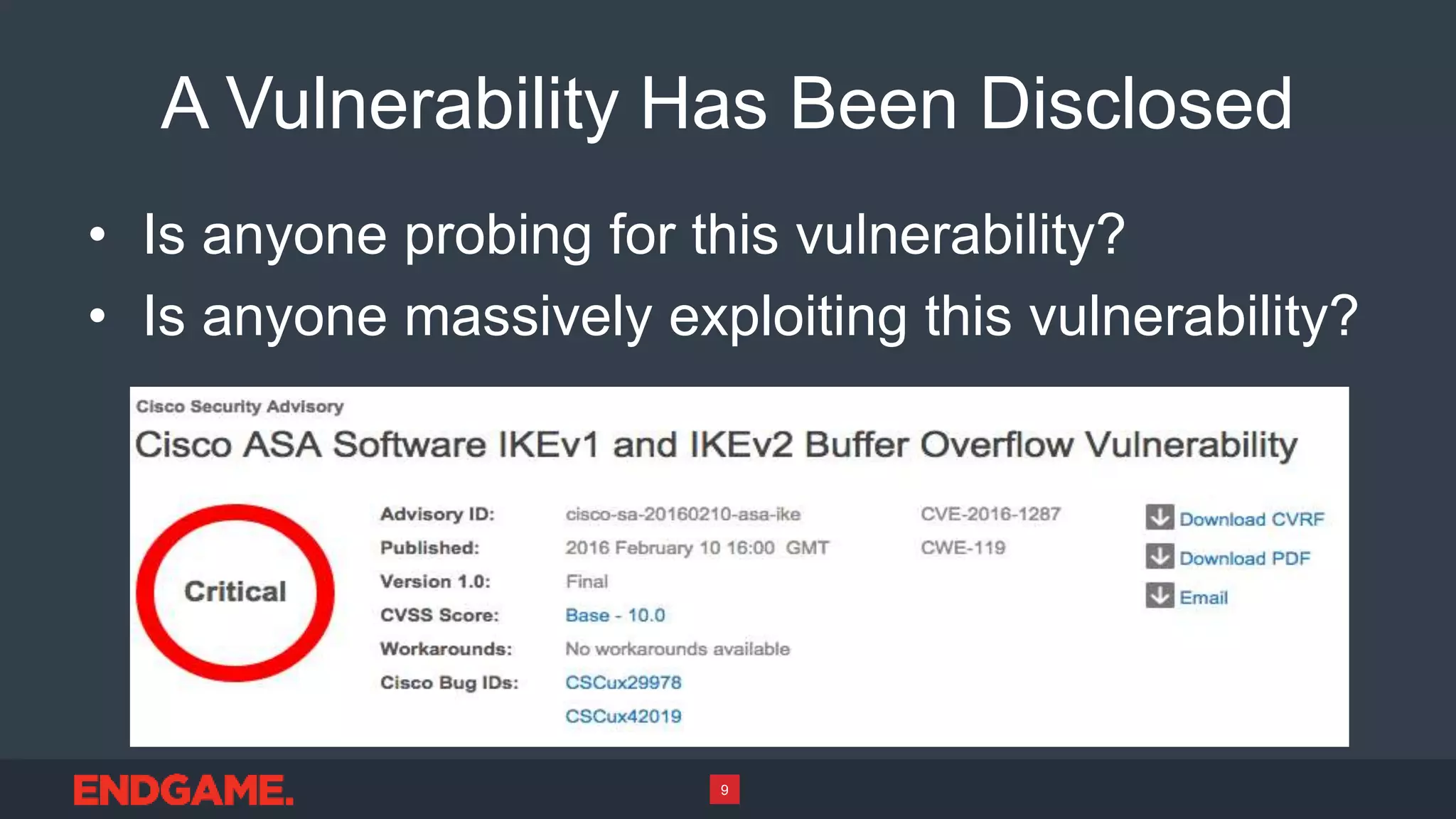
2) The sensors can provide insights into whether attacks on a network are targeted or omnidirectional mass exploits, and monitor for probing and exploitation of newly disclosed vulnerabilities.
3) The data collected by Faraday can be used for early warning applications, tracking worms and attackers, and integrating with cyber operations platforms to gain visibility into novel techniques and collect new malware samples.