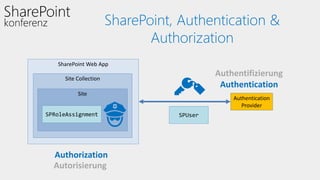
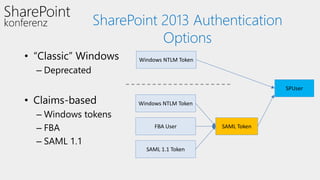
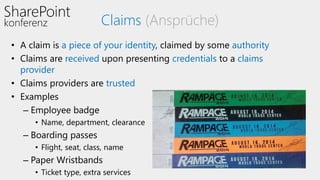
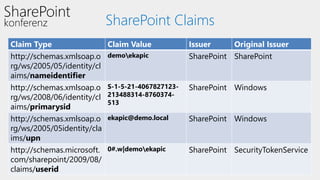
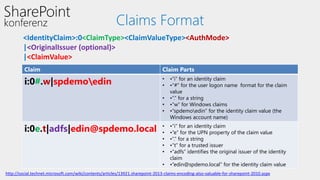
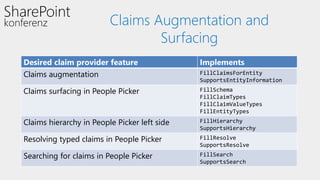
This document discusses authentication and authorization in SharePoint. It covers claims-based authentication and authorization, including claims providers and federated authentication. Claims are pieces of a user's identity that can be used to authenticate and authorize users. SharePoint uses claims-based authentication, allowing it to integrate with different identity providers that provide claims. Claims providers can augment and surface claims to SharePoint. Federated authentication allows authenticating users from an external identity provider using security tokens with claims. The document demonstrates configuring federated authentication with Active Directory Federation Services.