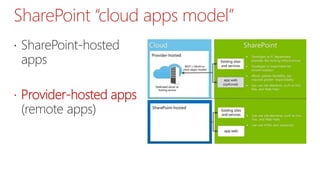
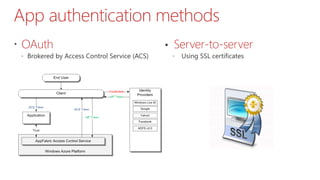
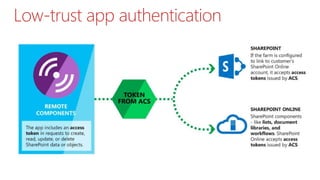
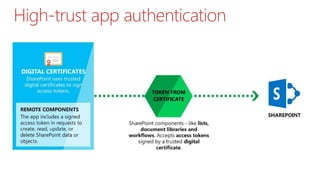
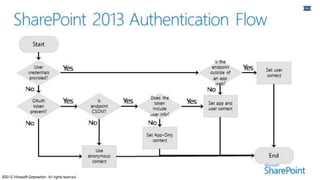
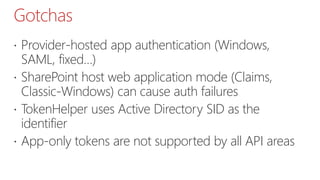
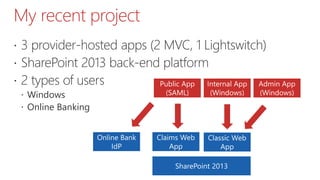
This document summarizes the high-trust app model for on-premises SharePoint development. It discusses the differences between low-trust and high-trust app authentication, how high-trust apps use certificates instead of OAuth, and the prerequisites and mechanism for high-trust app authentication. It also covers some gotchas, using other authentication methods, technology stacks, extending the TokenHelper code, and provides examples of high-trust app projects and information sources.