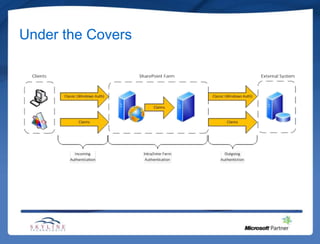
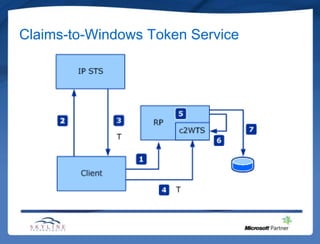
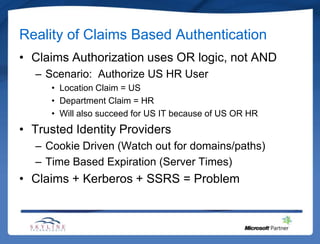
This document provides an overview of claims-based authentication in SharePoint 2010. It defines what claims are and why one would use claims-based authentication. It describes the basic claims-based architecture including security token services, security assertion markup language, and the Windows identity framework. It also covers trusted identity providers, claims development tasks, and some realities of implementing claims-based authentication.