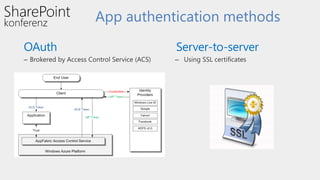
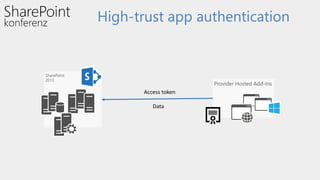
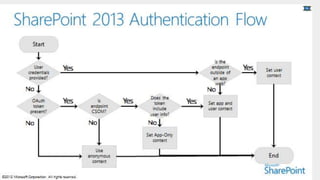
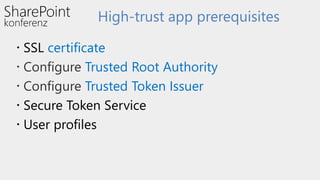
This document discusses high-trust app authentication for on-premises SharePoint development. It begins with an overview of the SharePoint app models and describes how high-trust apps use certificates to authenticate instead of OAuth tokens like low-trust apps. The document then covers prerequisites, the authentication mechanism, considerations, and examples of using other programming languages and extending the TokenHelper code. It concludes with information about resources for learning more about high-trust app authentication in SharePoint 2013.