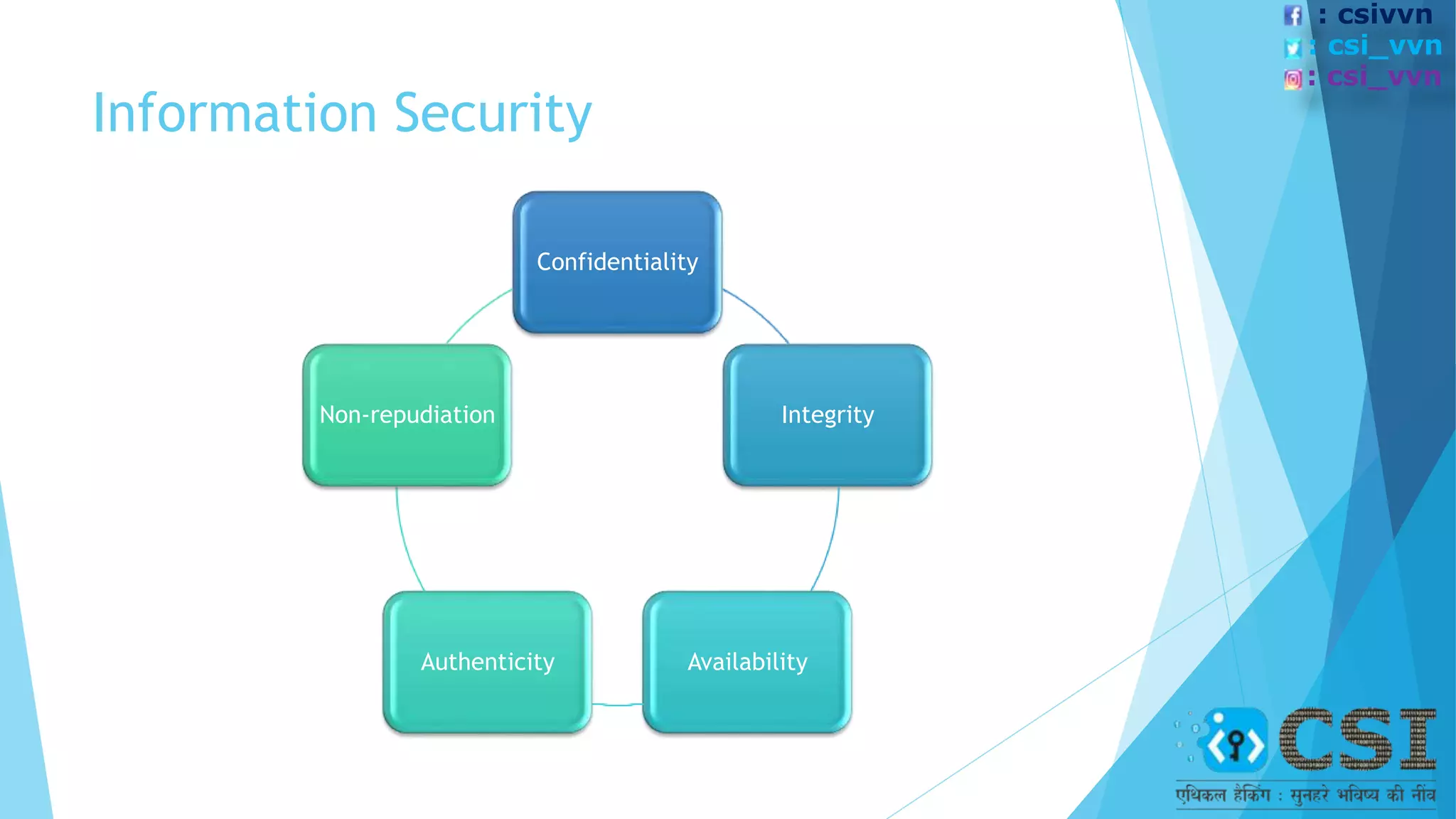
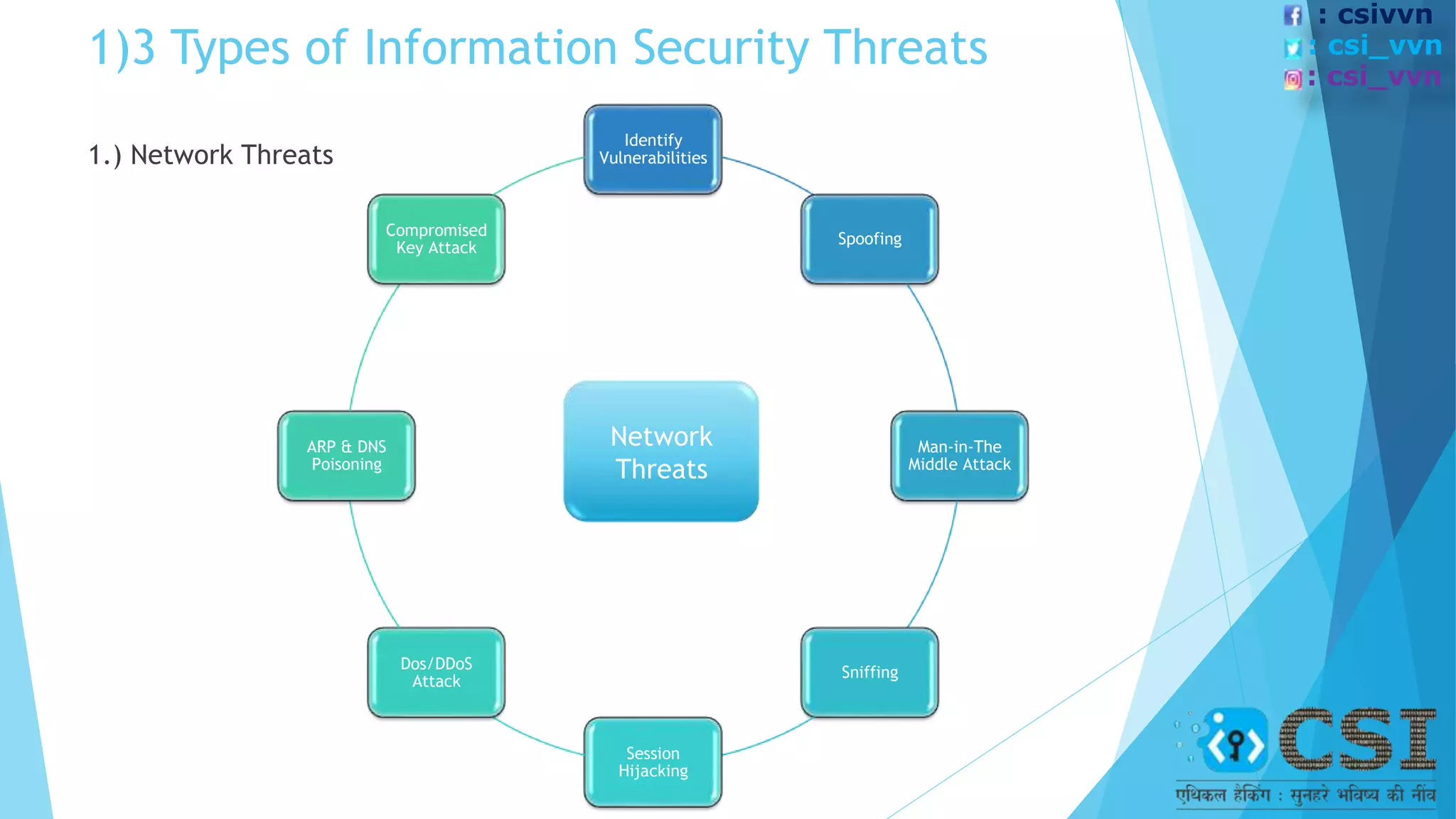
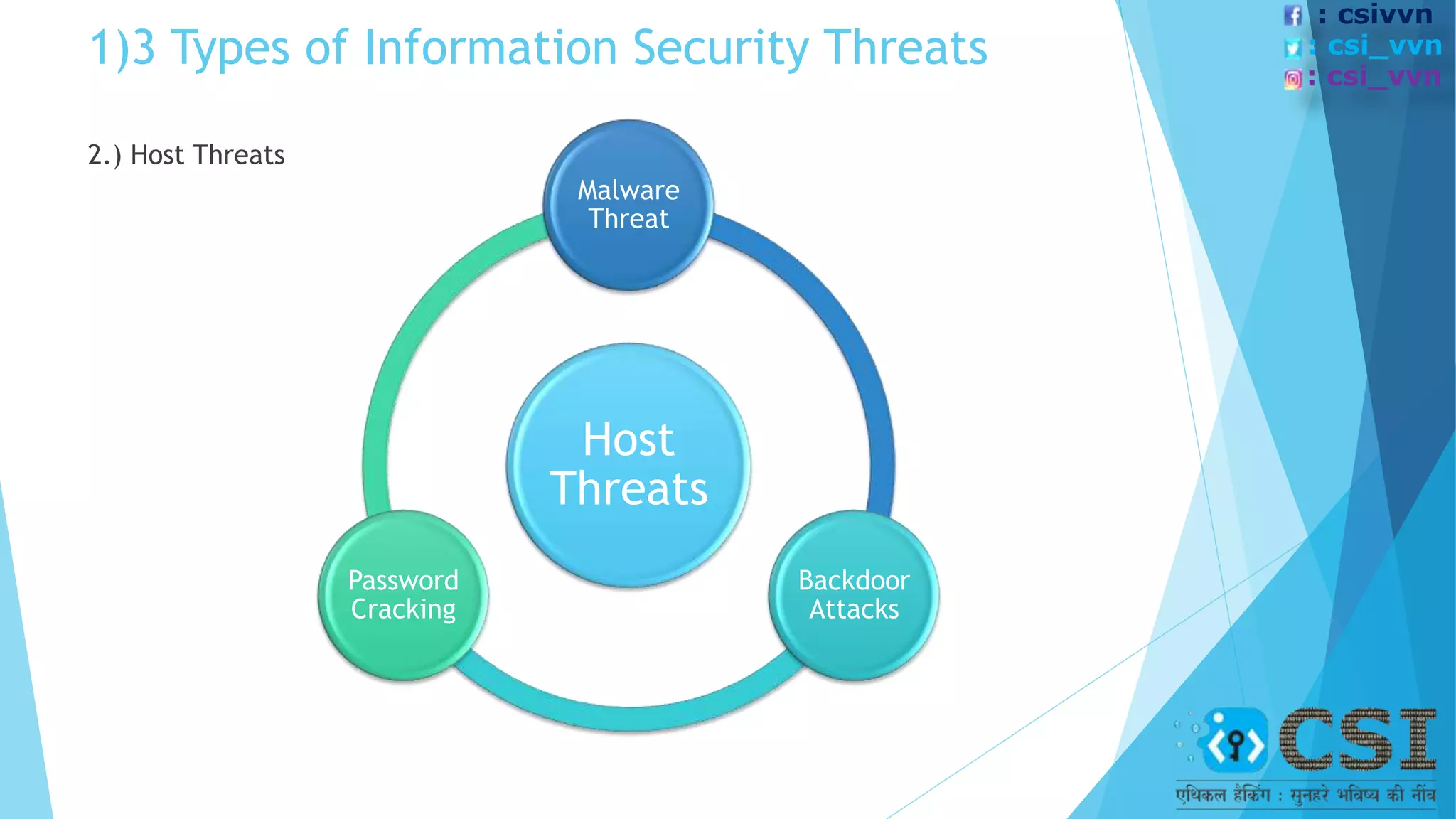
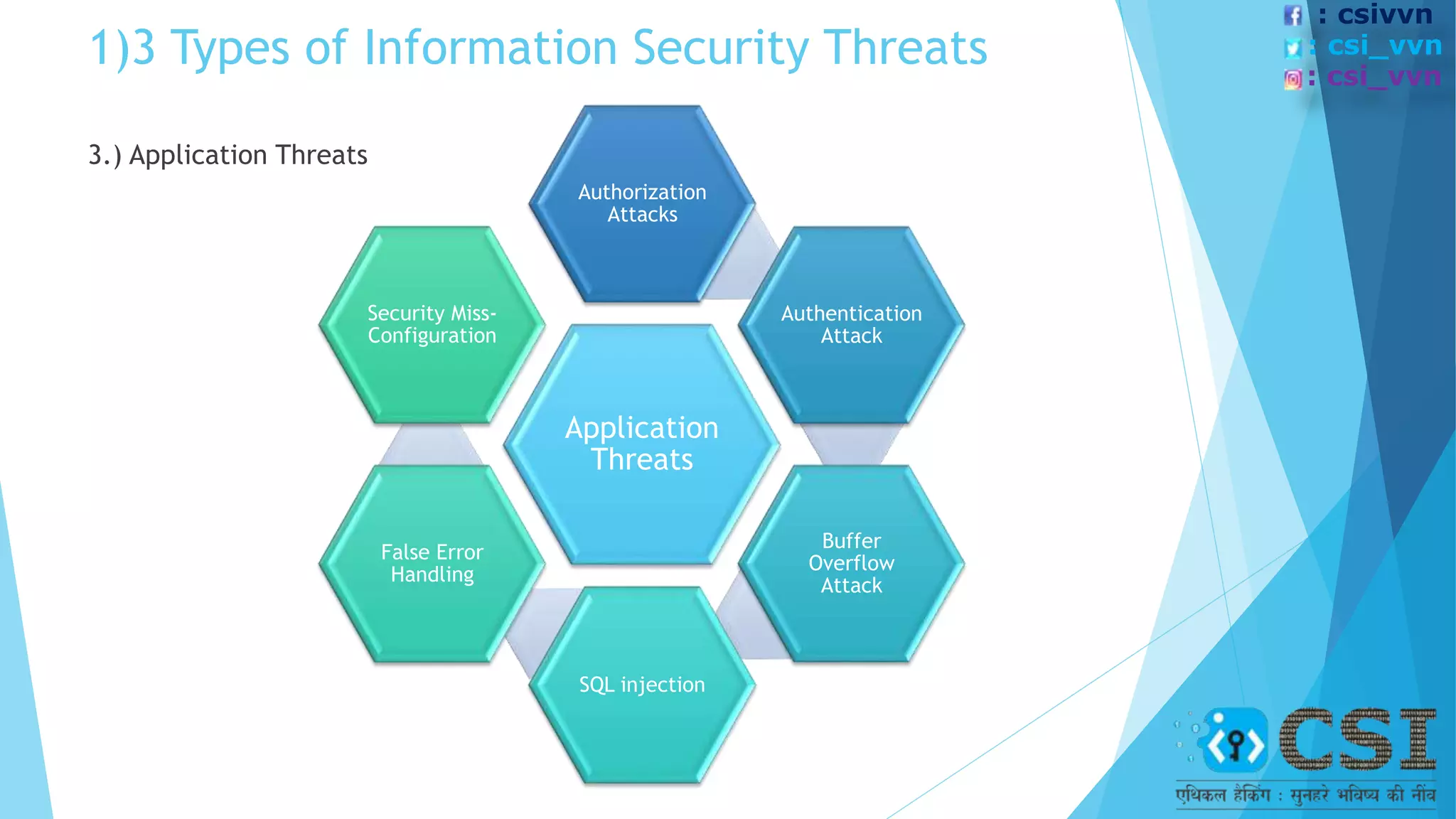
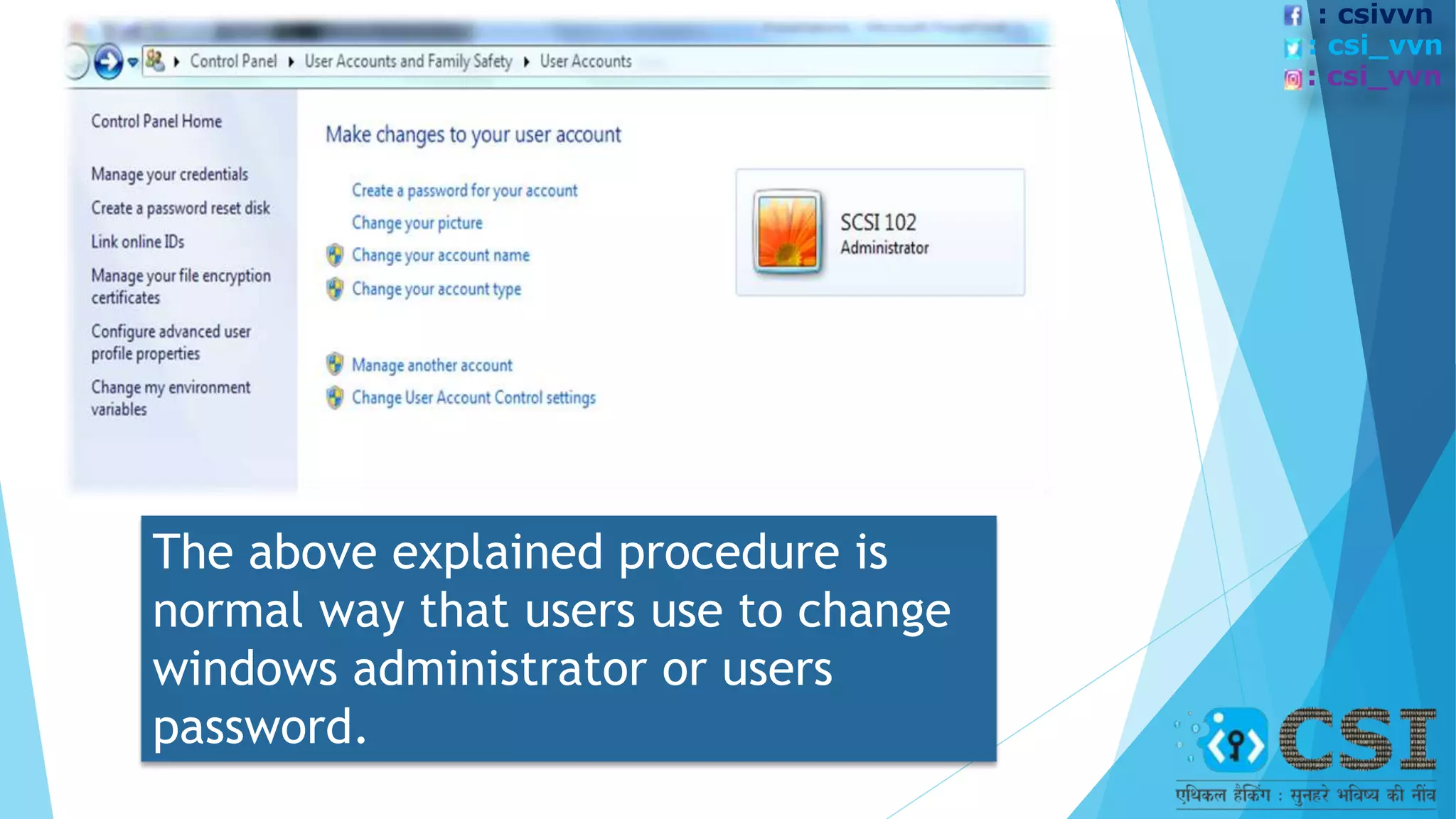
The document discusses the concept of ethical hacking, outlining information security principles including confidentiality, integrity, and availability. It covers various security threats, types of hackers, and the phases of a hacking attempt, from information gathering to maintaining access. Ethical hacking is framed as a legitimate method for companies to test their security by allowing hackers to penetrate their systems under authorized conditions.