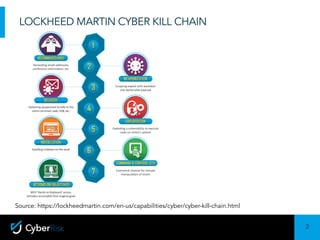
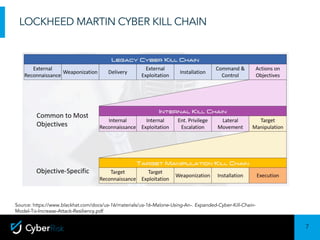
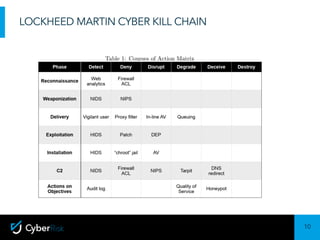
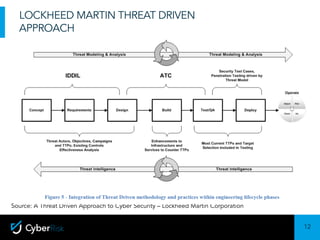
The document discusses the Lockheed Martin Cyber Kill Chain model for describing cyber attacks. It outlines the seven stages of the kill chain: exploitation, installation, command and control, actions on objectives, and others. It also discusses some limitations of only focusing on the kill chain, such as that it is malware-focused and doesn't address internal threats. The document then covers ways the kill chain model can still be useful, such as for explaining attacks to executives. It introduces the concept of an internal kill chain for modeling insider threats. Finally, it discusses how persistent insiders and flight risks can be modeled at different stages of an internal kill chain approach.