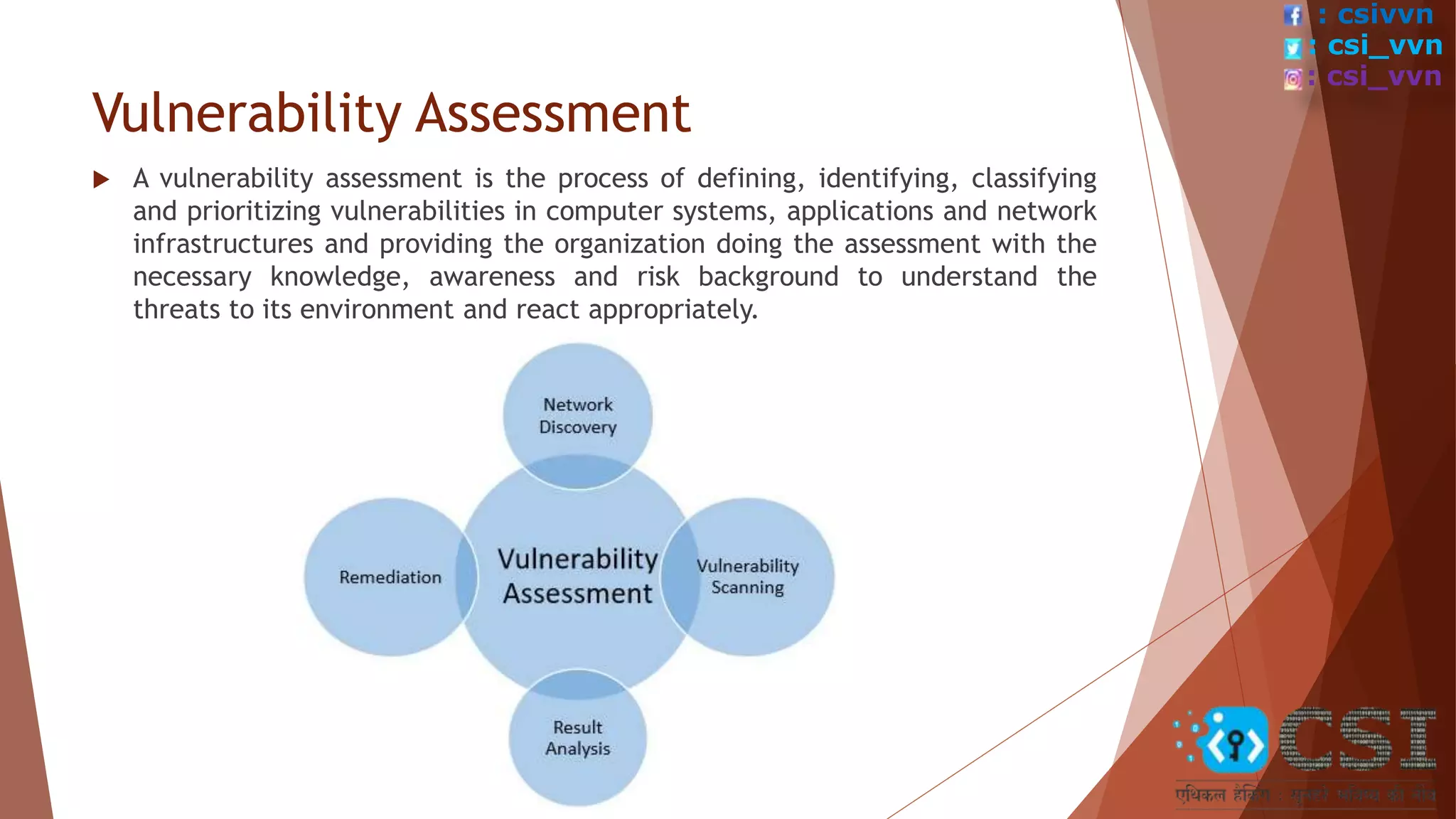
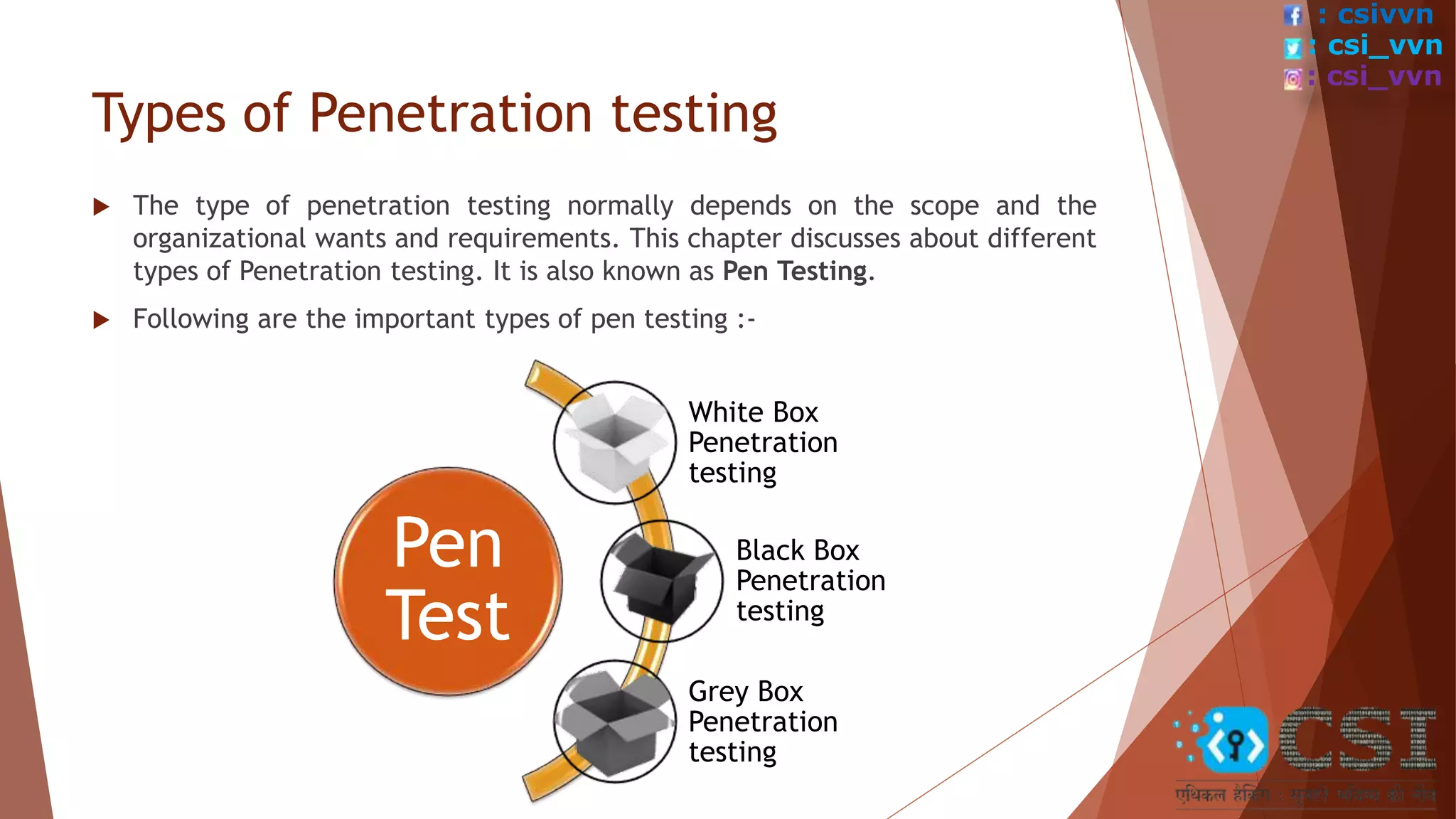
The document provides an overview of penetration testing, describing its importance in identifying security vulnerabilities in systems and applications. It covers types of penetration testing, such as white box, black box, and grey box testing, as well as the phases and steps involved in conducting a pen test. Additionally, it highlights the benefits of pen testing, which include enhancing security measures, preventing financial losses, and ensuring regulatory compliance.