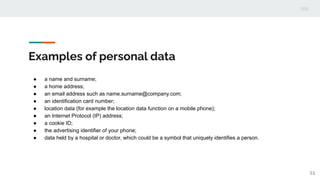
This document outlines the ethical principles and considerations for computing professionals regarding their responsibilities and the impact of their work on society. It highlights the importance of respecting personal data, privacy, and adhering to the General Data Protection Regulation (GDPR) when conducting research involving human subjects or personal data. Additionally, it provides an ethical issues checklist for the research process and emphasizes the need for responsible research and innovation practices.