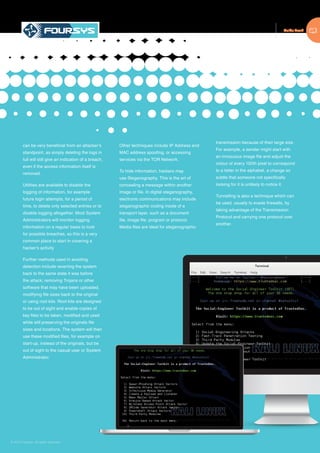
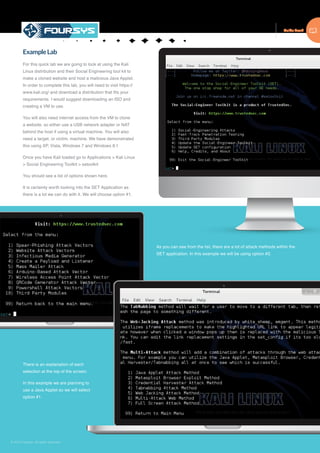
The document provides an overview of ethical hacking, including definitions, goals, and the typical 5 phases of hacking: reconnaissance, scanning, gaining access, maintaining access, and covering tracks. It describes the importance of reconnaissance in gathering target information through passive and active means. Scanning involves using tools to discover technical details about a network like open ports and services. Gaining access focuses on exploiting vulnerabilities to infiltrate systems, while maintaining access ensures continued infiltration even after reboots. Covering tracks aims to remove evidence and logs of the intrusion. The document provides examples of techniques for each phase.