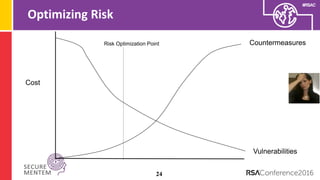
The document discusses the myths surrounding sophisticated cyber attacks, arguing that many high-profile breaches result from poor security practices rather than advanced tactics. It emphasizes the need for adaptive security strategies that anticipate failure, improve detection, and cultivate a strong security culture among personnel. The authors suggest a shift from prevention-focused programs to those that prioritize adaptability and effective response to threats.