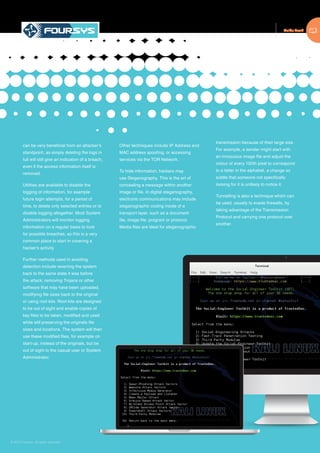
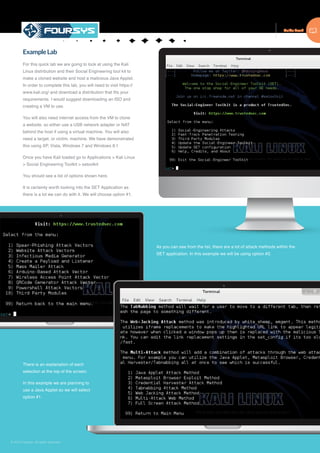
The document is a guide to ethical hacking that defines it as helping organizations strengthen security by simulating attacks while staying within legal limits. It outlines the typical phases of hacking: reconnaissance through passive and active information gathering; scanning networks to identify vulnerabilities; gaining access, often by exploiting vulnerabilities; maintaining access over time; and covering tracks to avoid detection. The guide provides examples of tools and techniques used for each phase to help administrators understand hacker mindsets and better protect their networks.