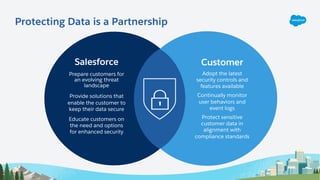
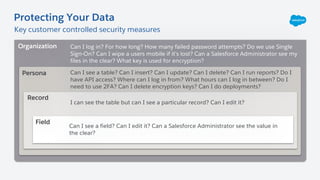
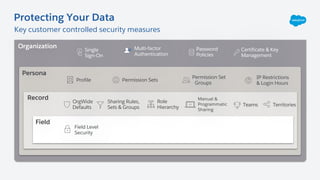
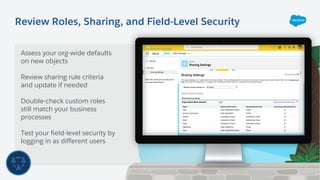
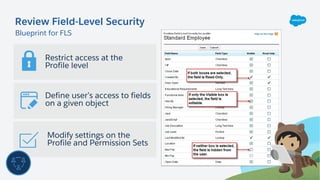
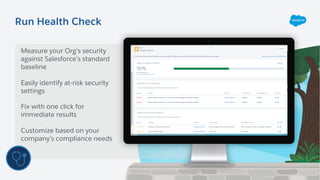
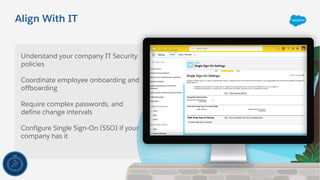
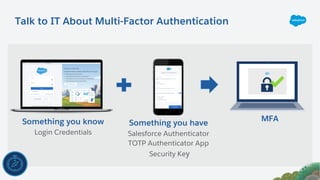
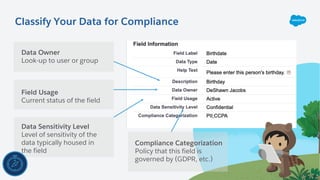
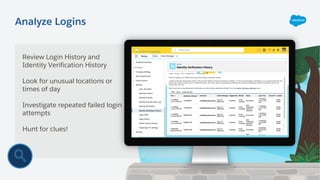
The document outlines essential security habits for Salesforce administrators, emphasizing the importance of managing user access, data protection, and compliance with security policies. It provides practical advice on maintaining secure systems, including regular security reviews and the implementation of multi-factor authentication. Additionally, it highlights the need for ongoing education and alignment with company IT policies to mitigate risks associated with data security.