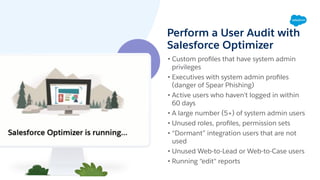
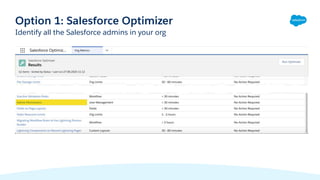
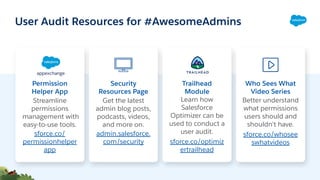
The document discusses performing a user audit to boost security in a Salesforce org. It recommends reviewing the user list and last login dates, deactivating unused users, removing unused profiles and permission sets, aligning access levels with job functions, and using tools like Salesforce Optimizer to identify security issues. The document also provides tips for preparing, communicating, and managing security changes after a user audit is completed.