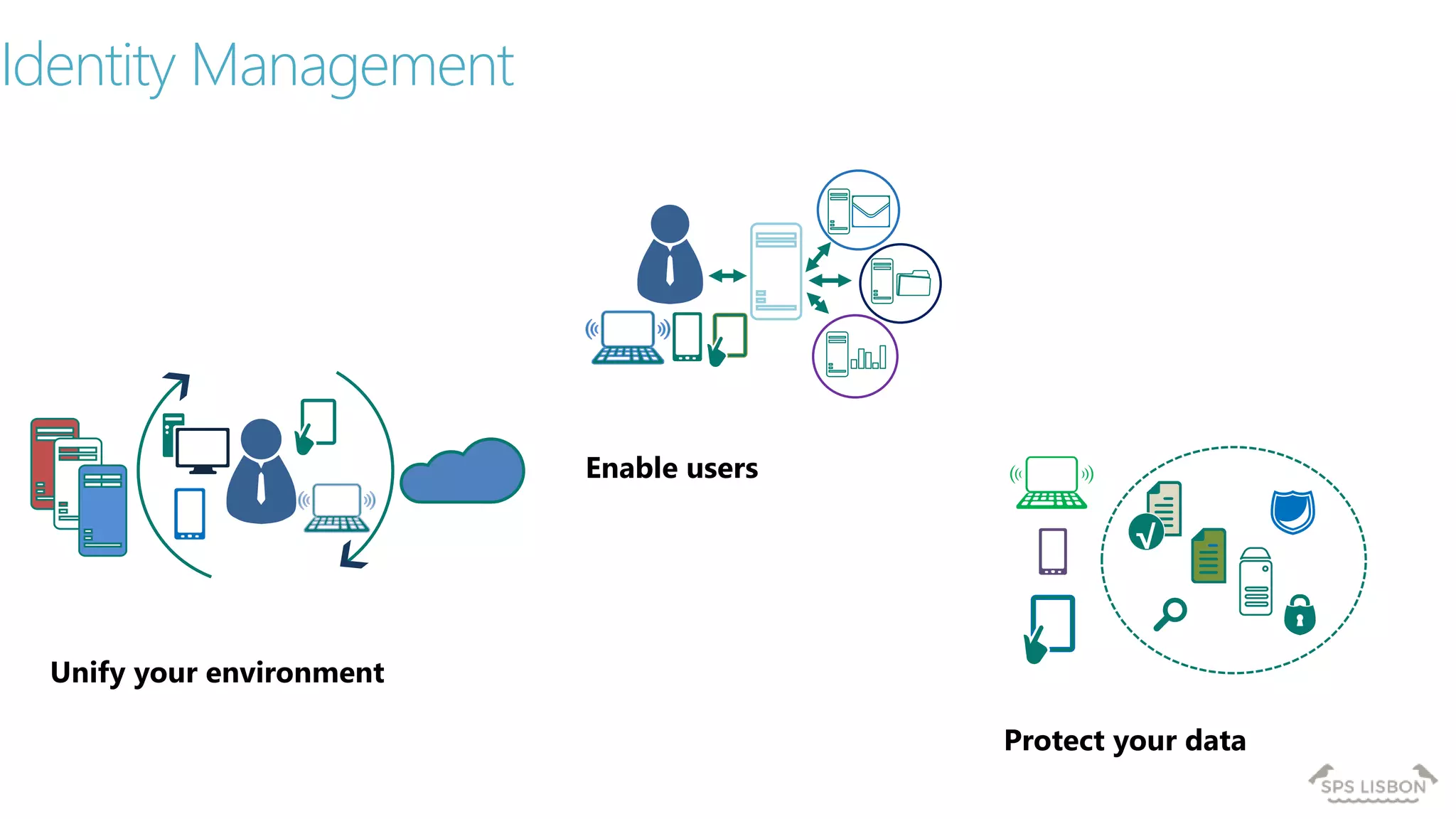
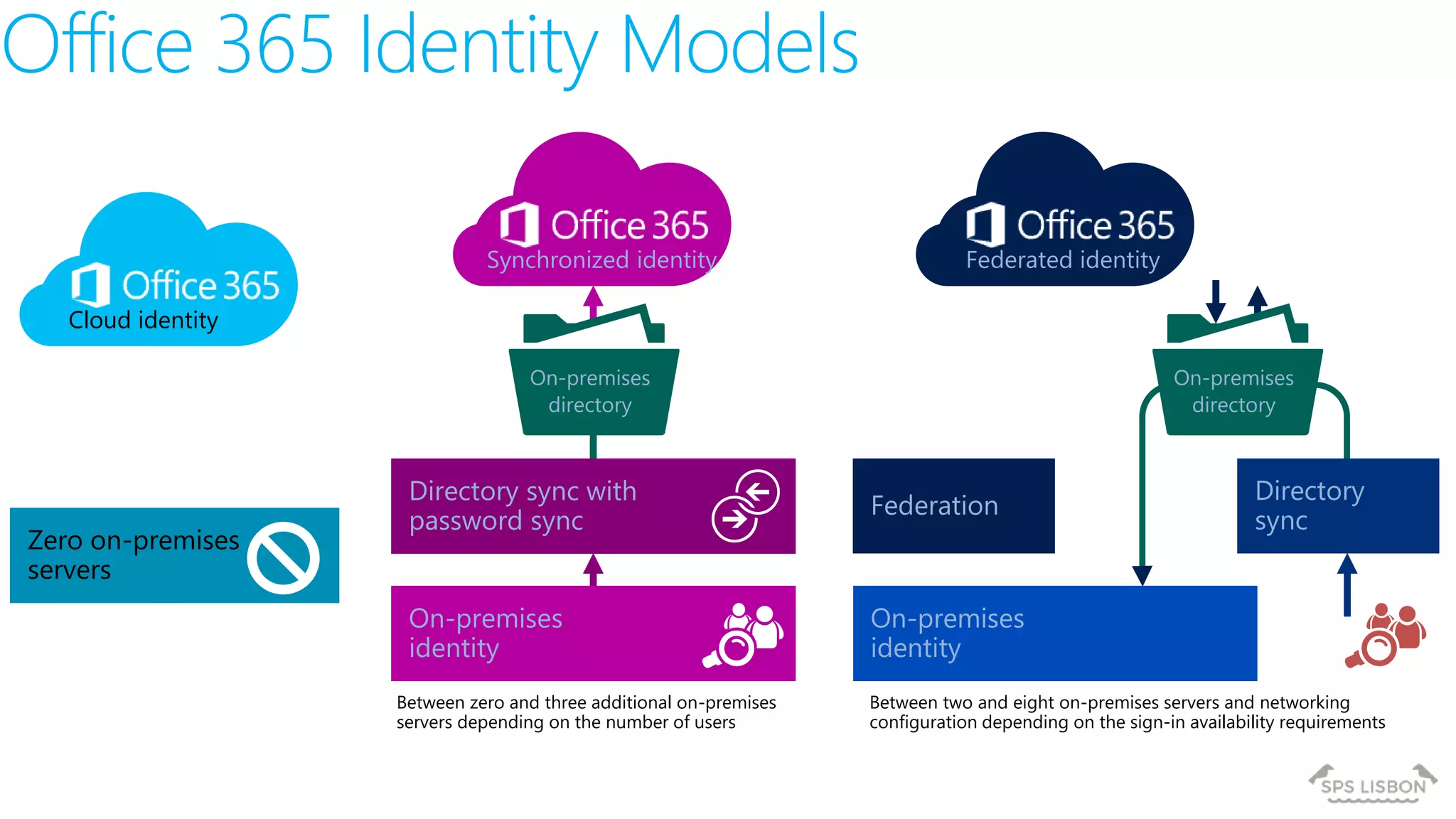
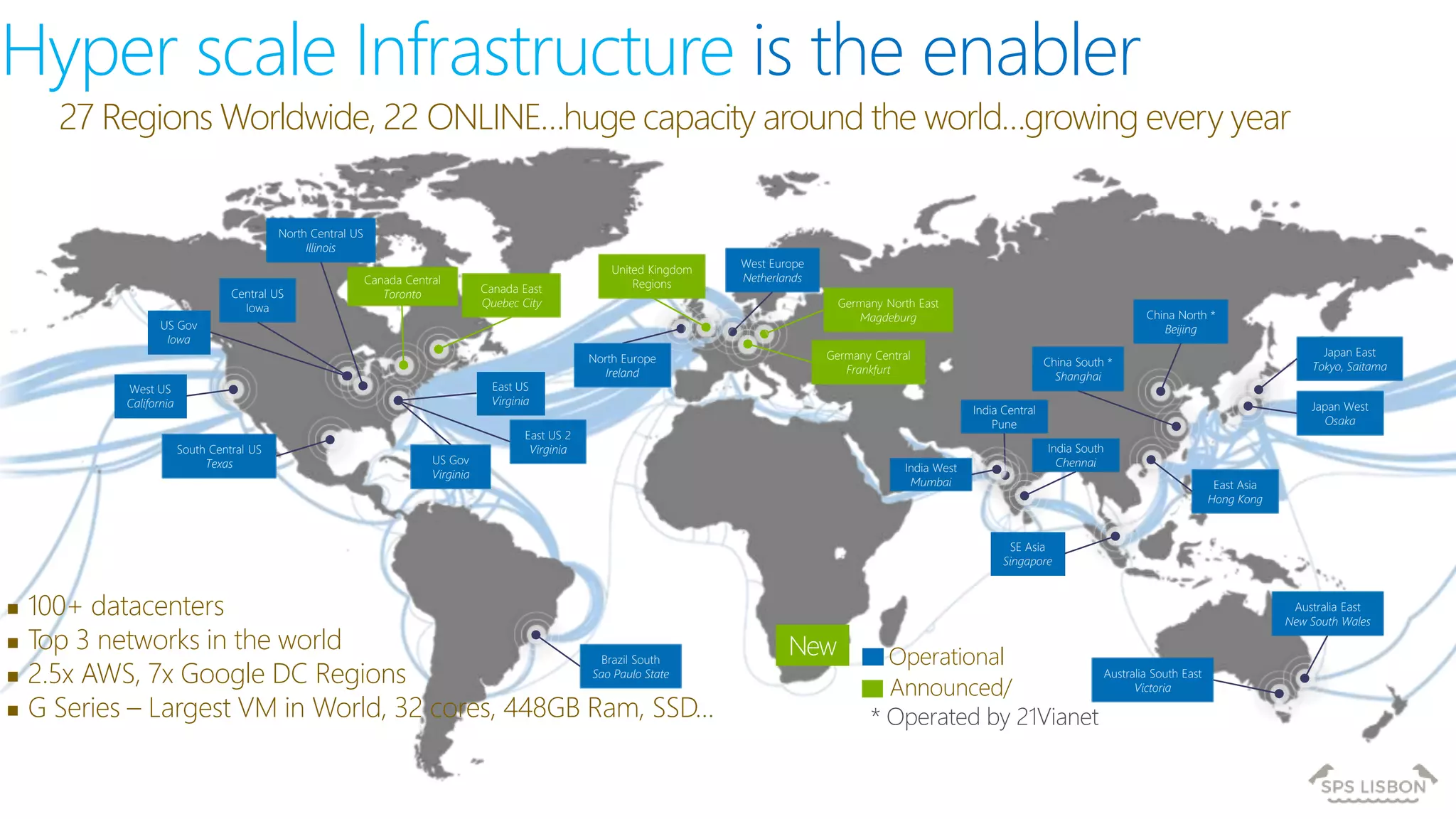
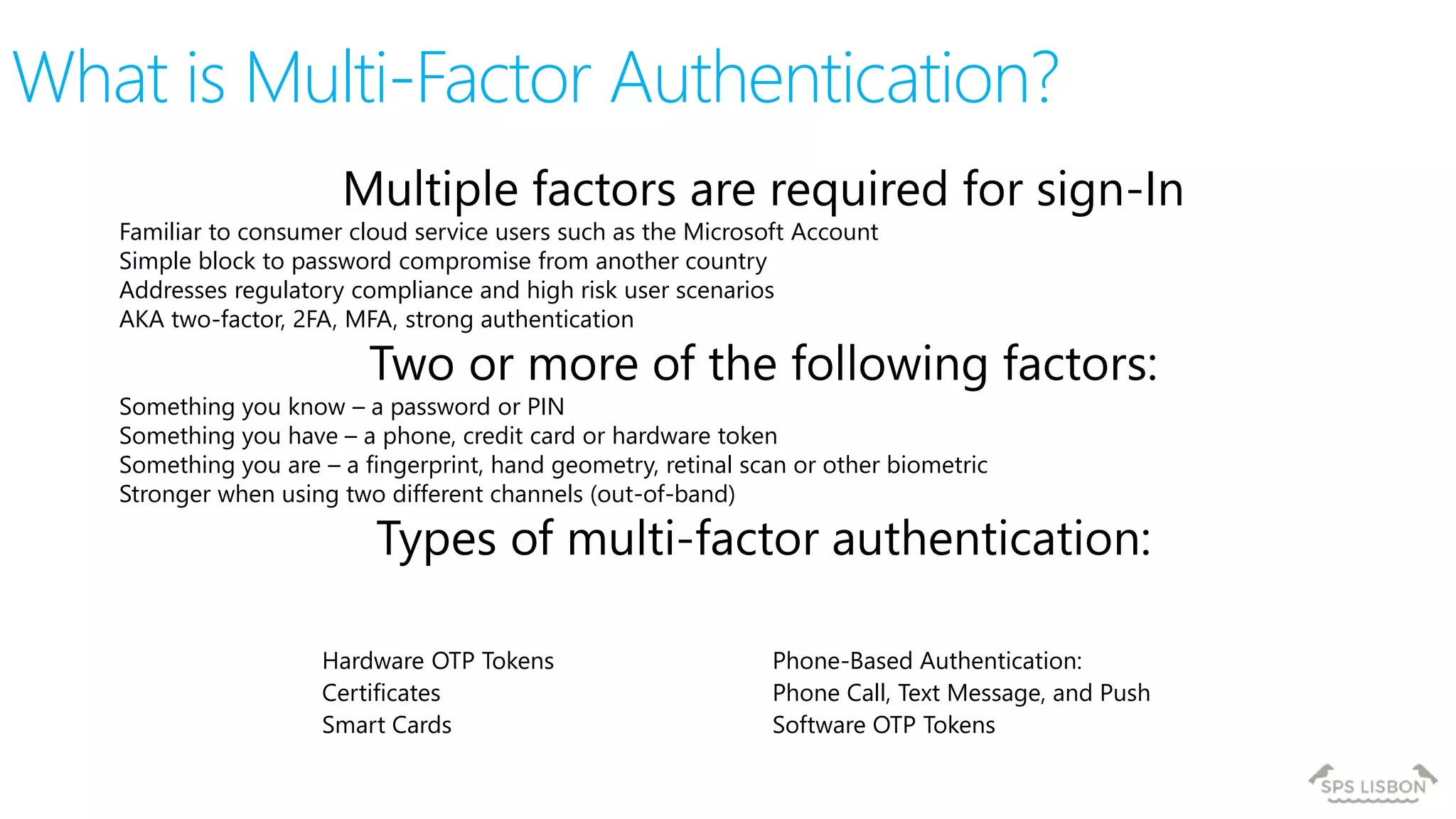
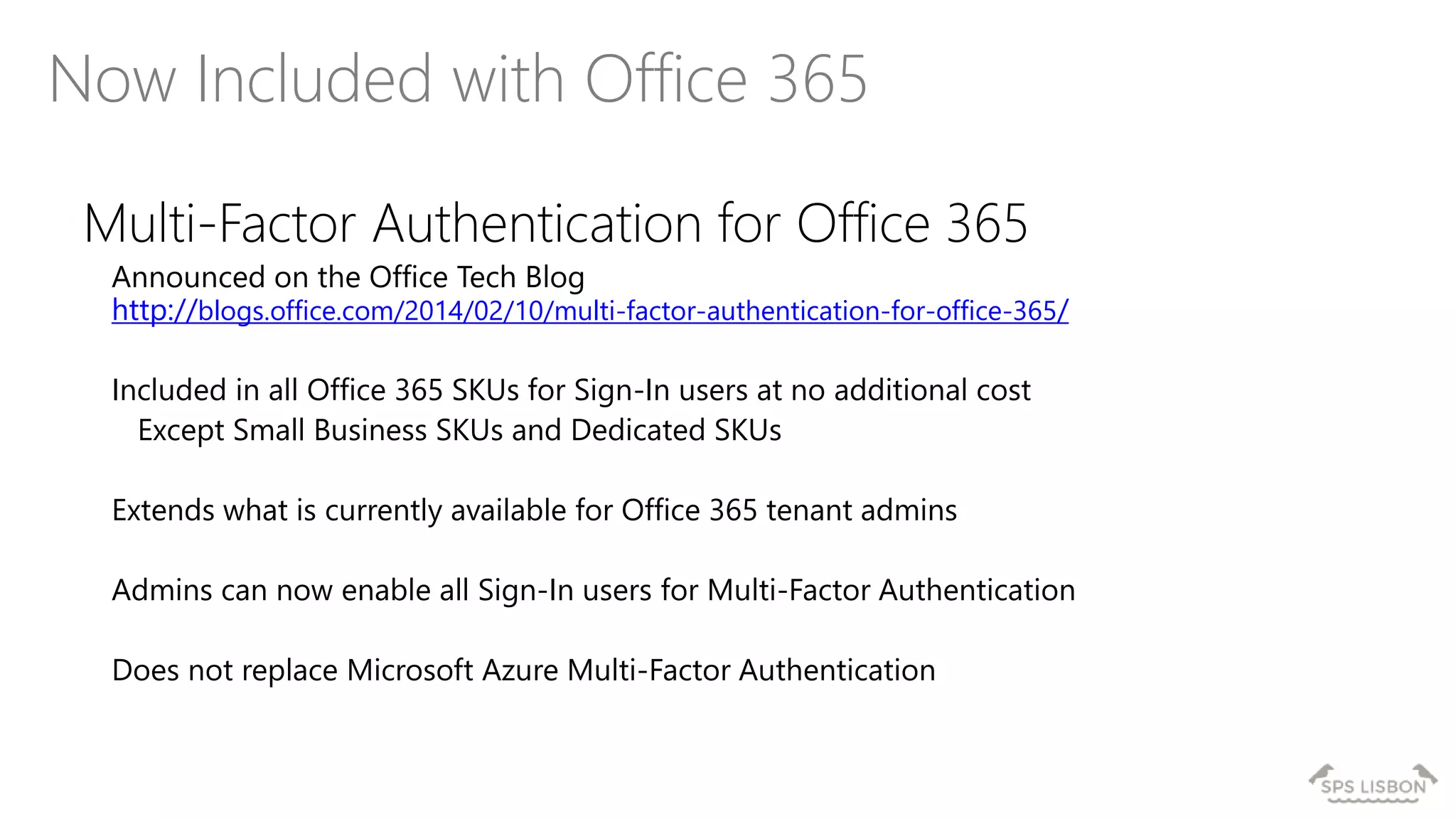
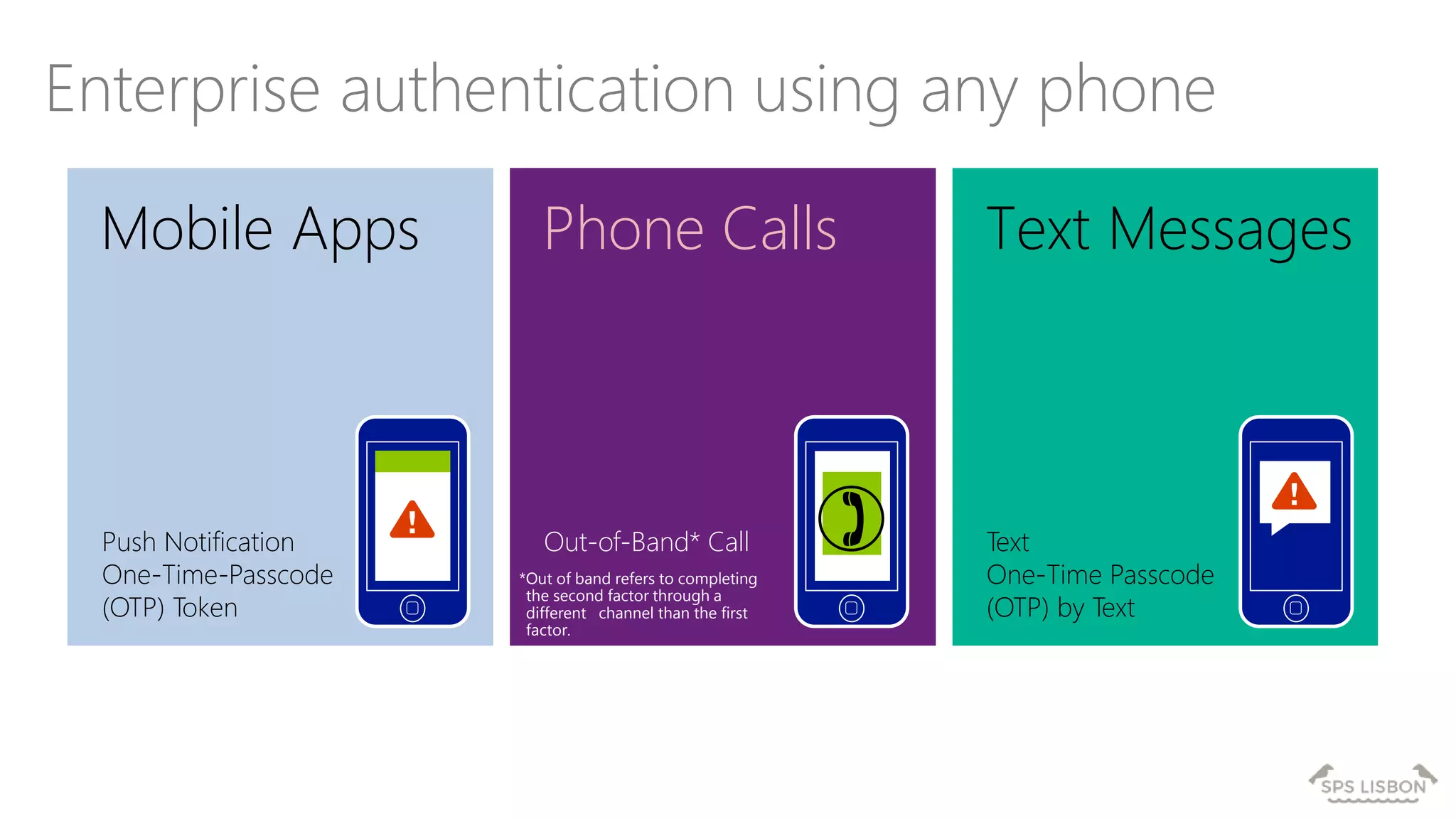
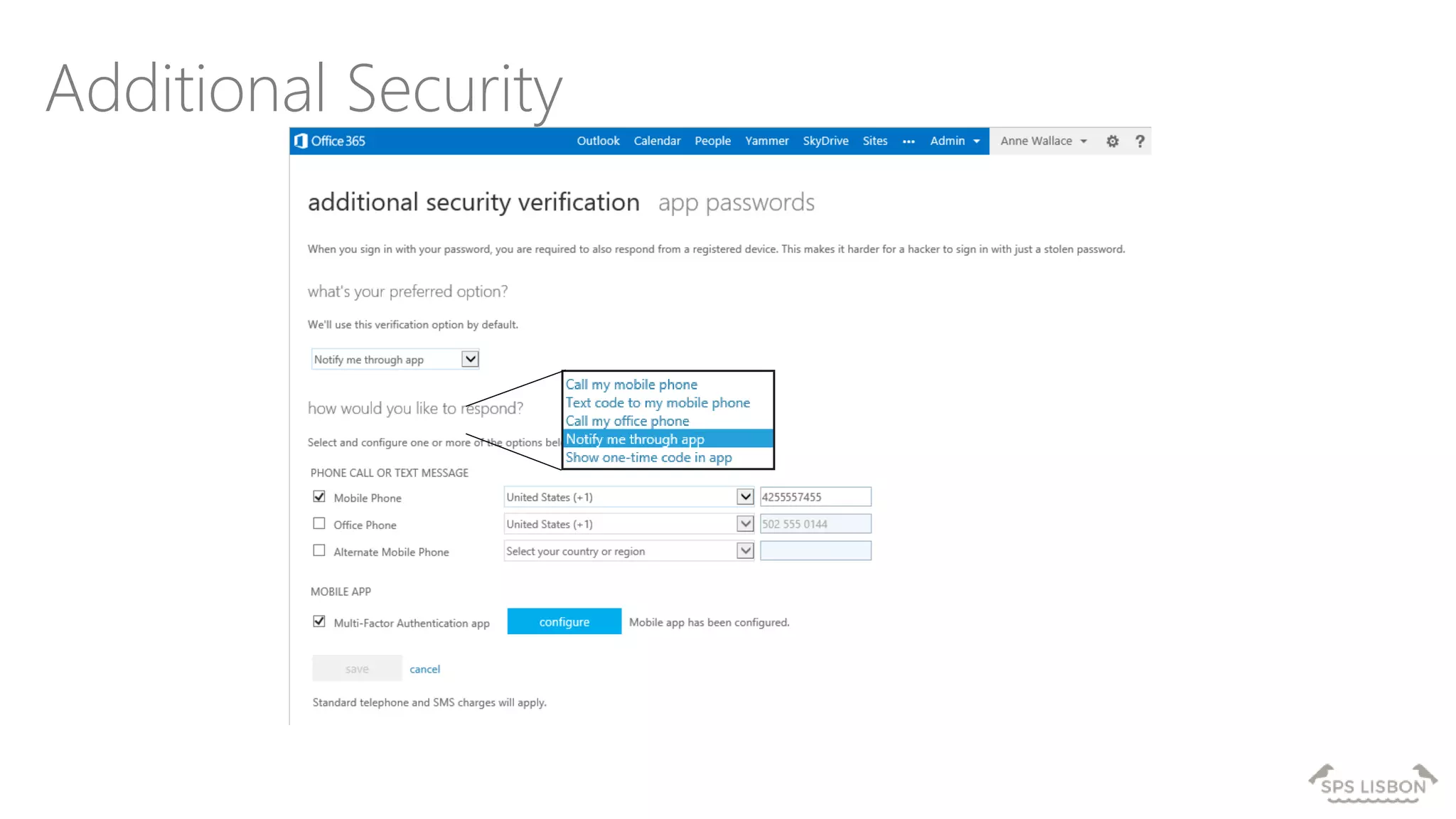
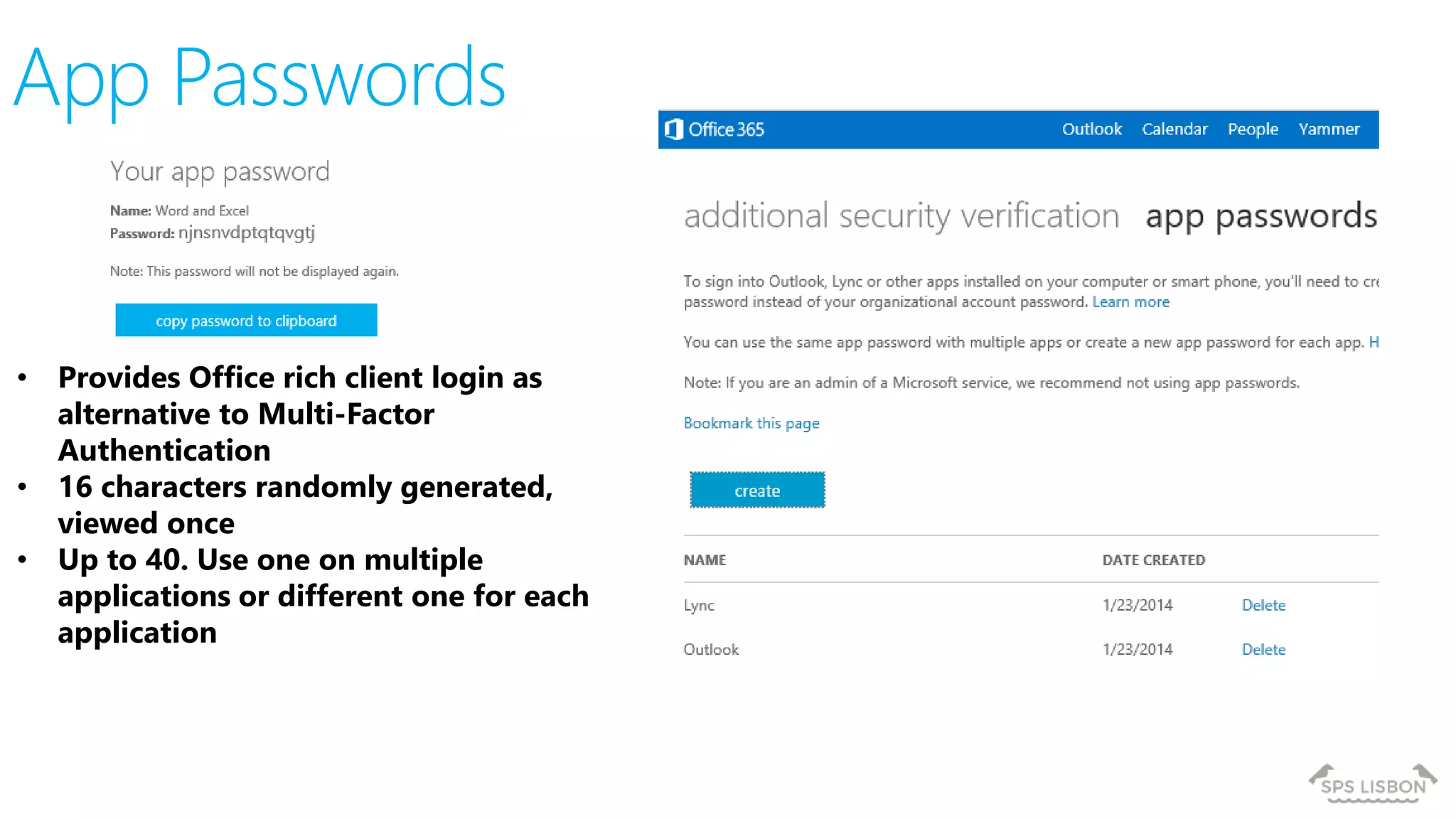
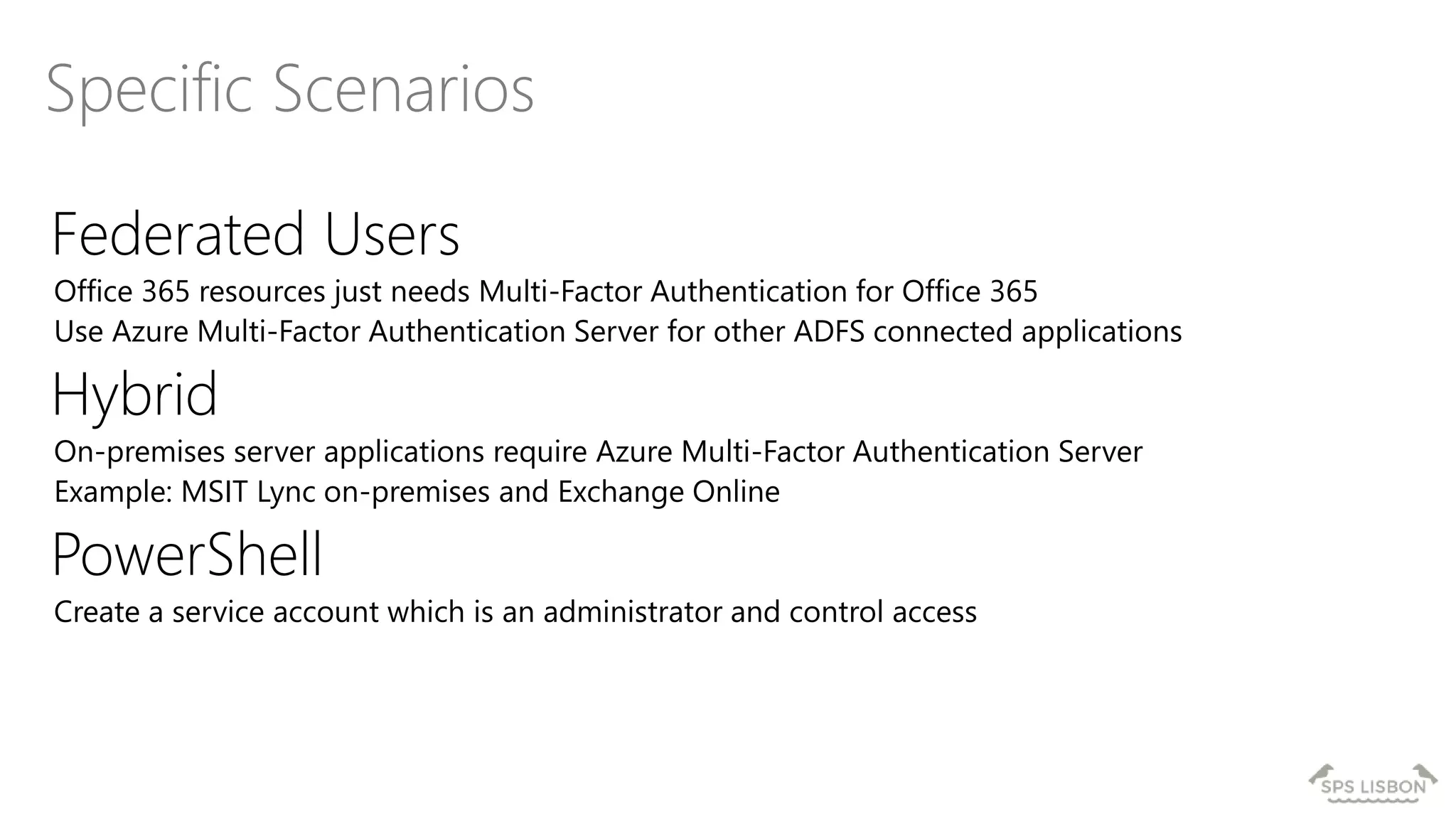
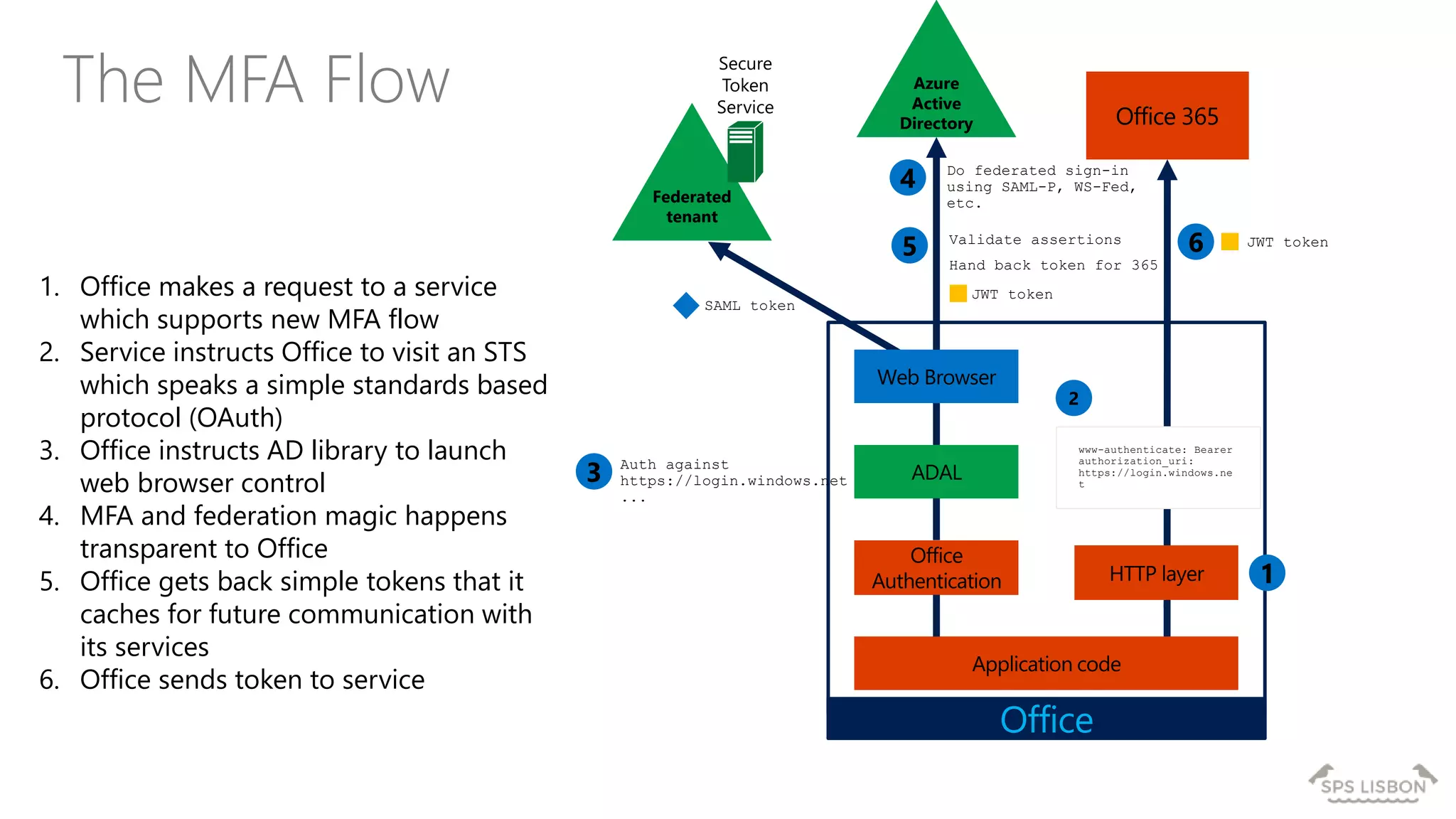
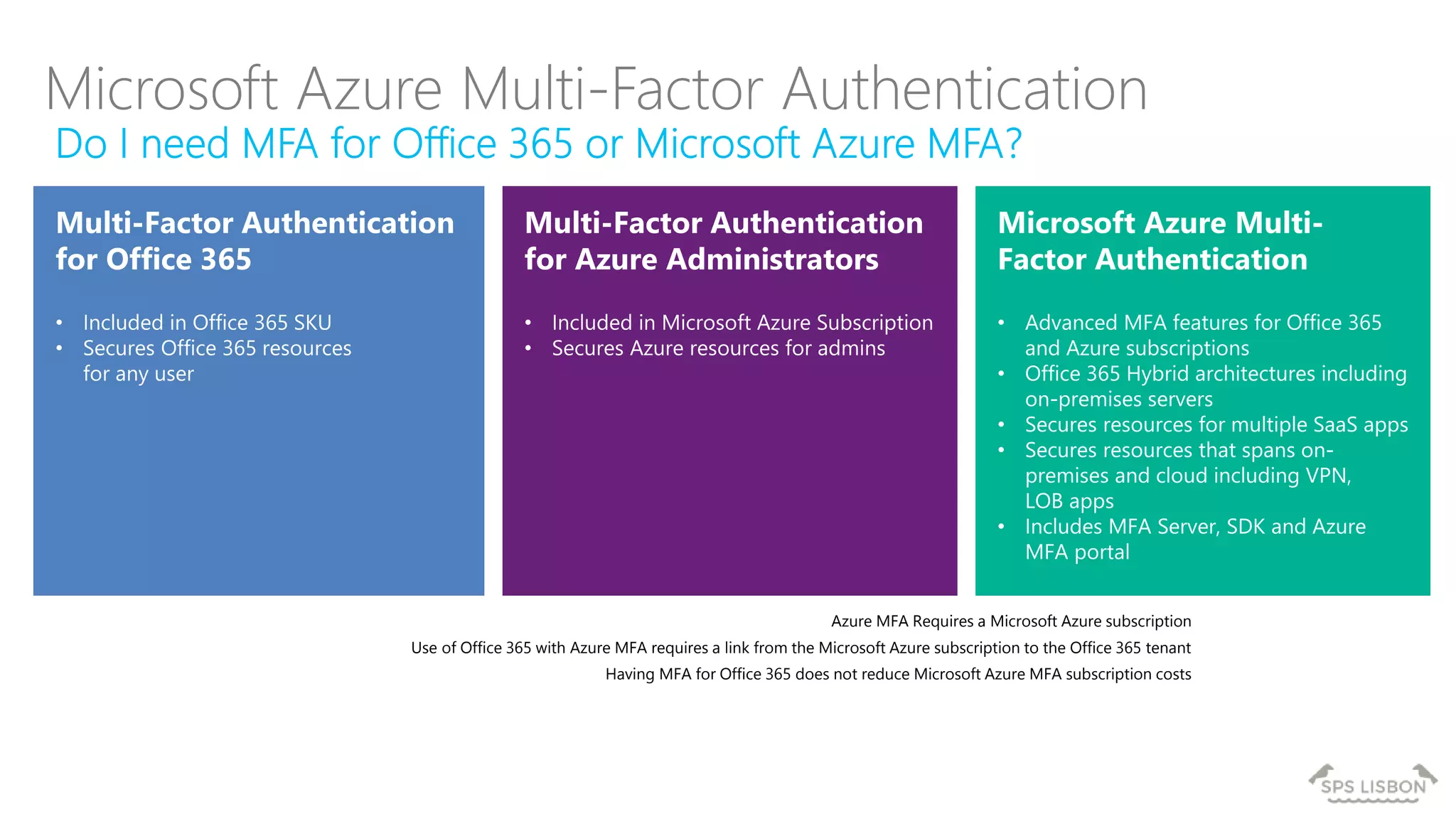
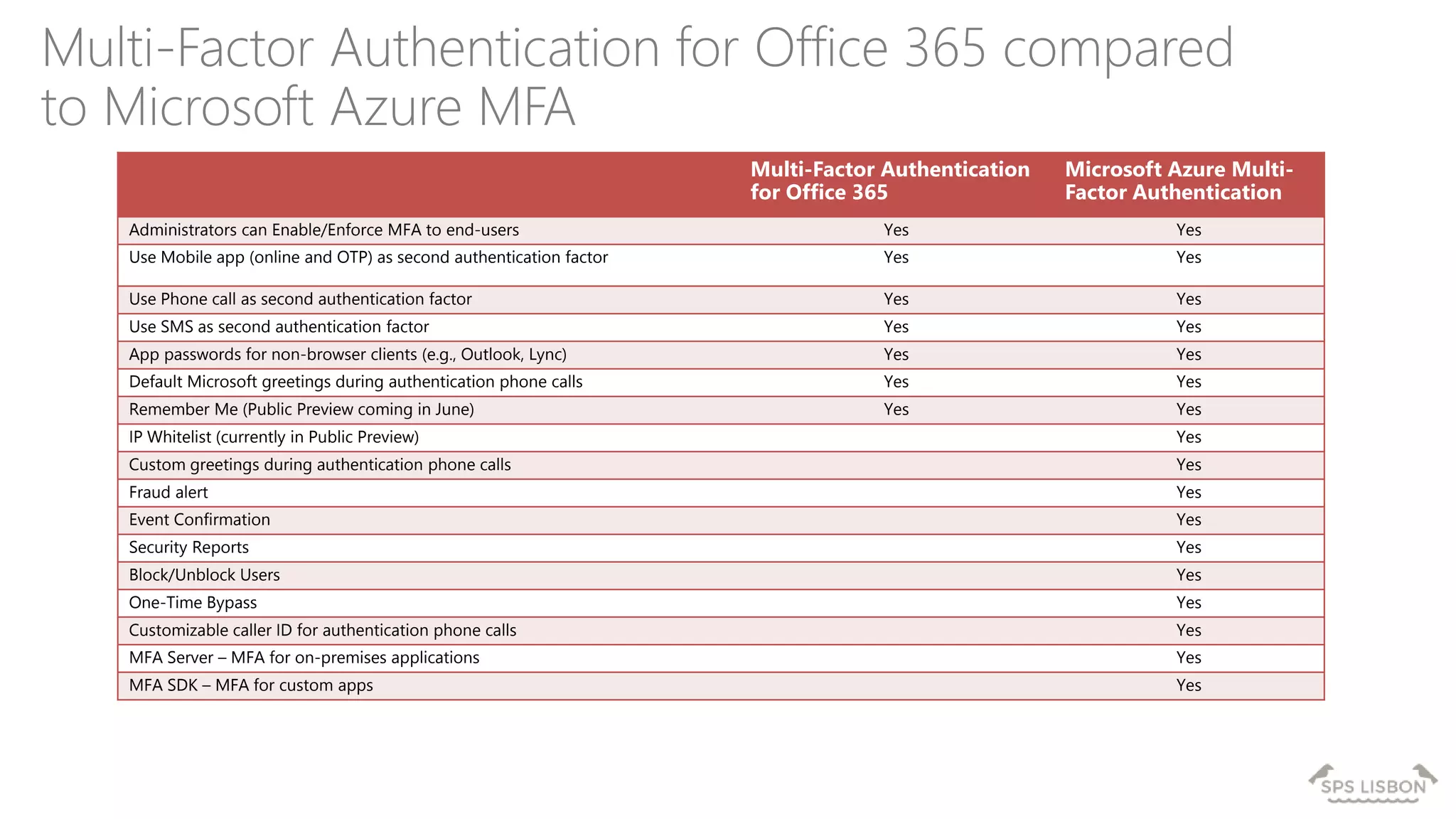
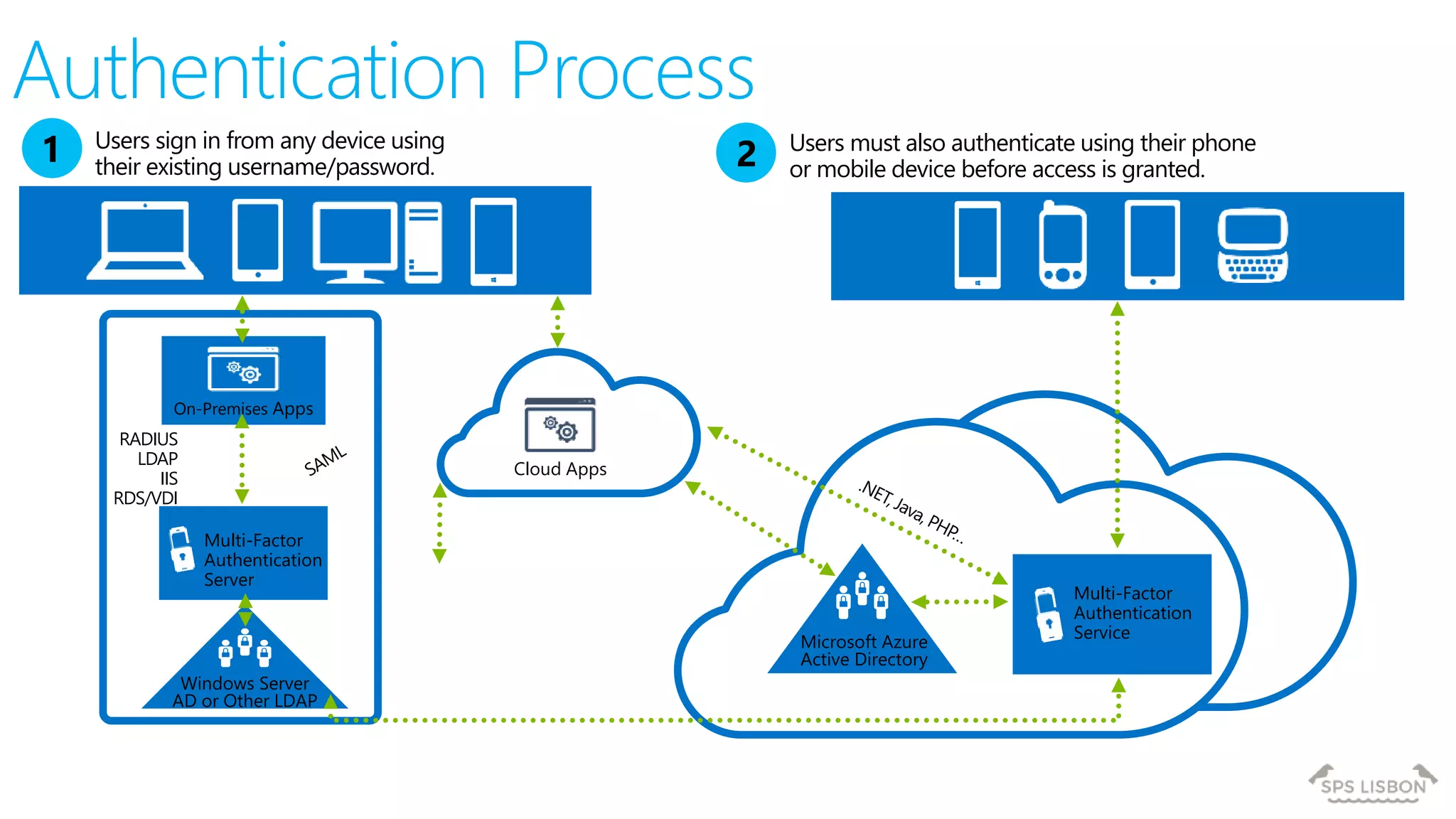
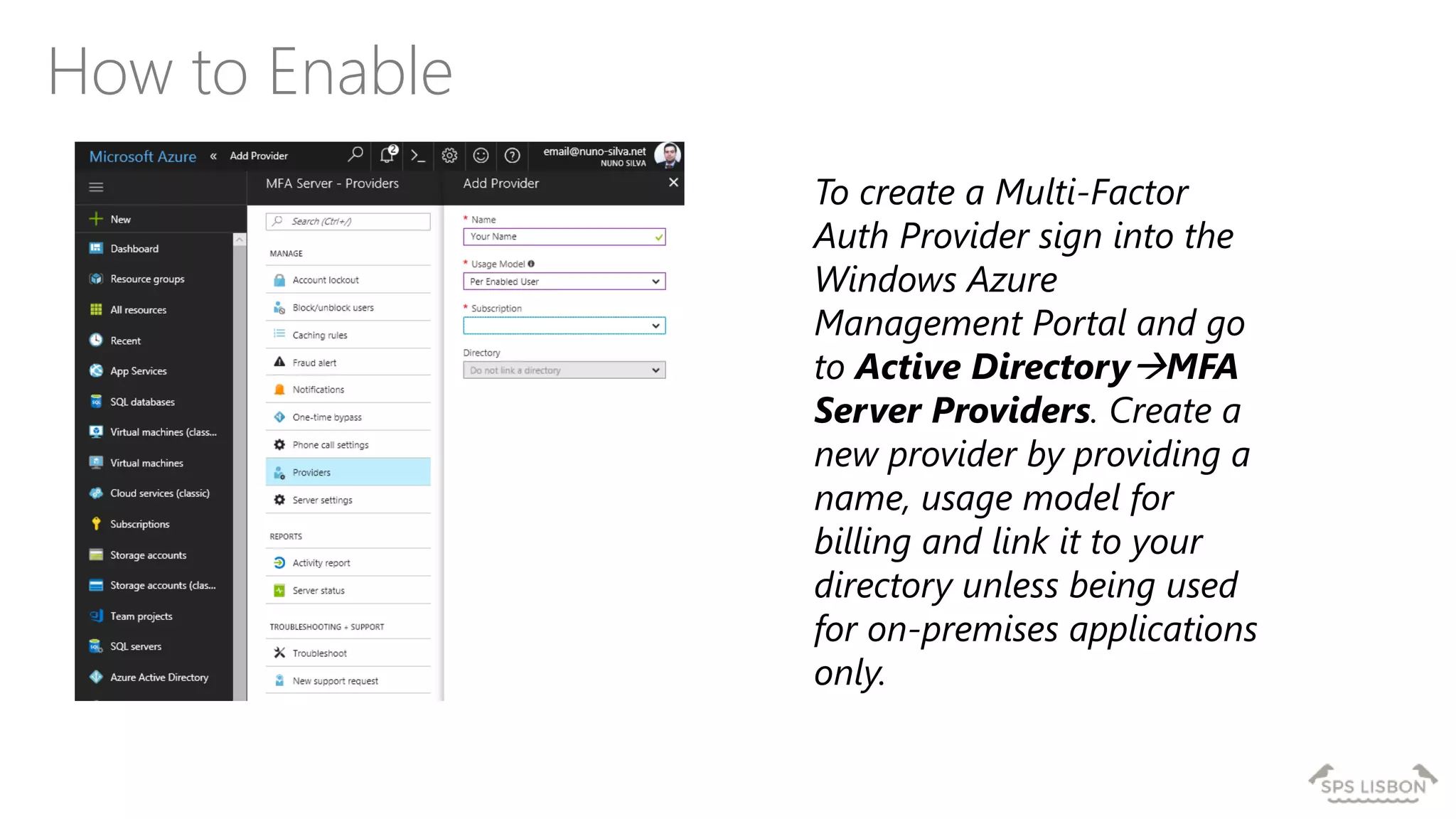
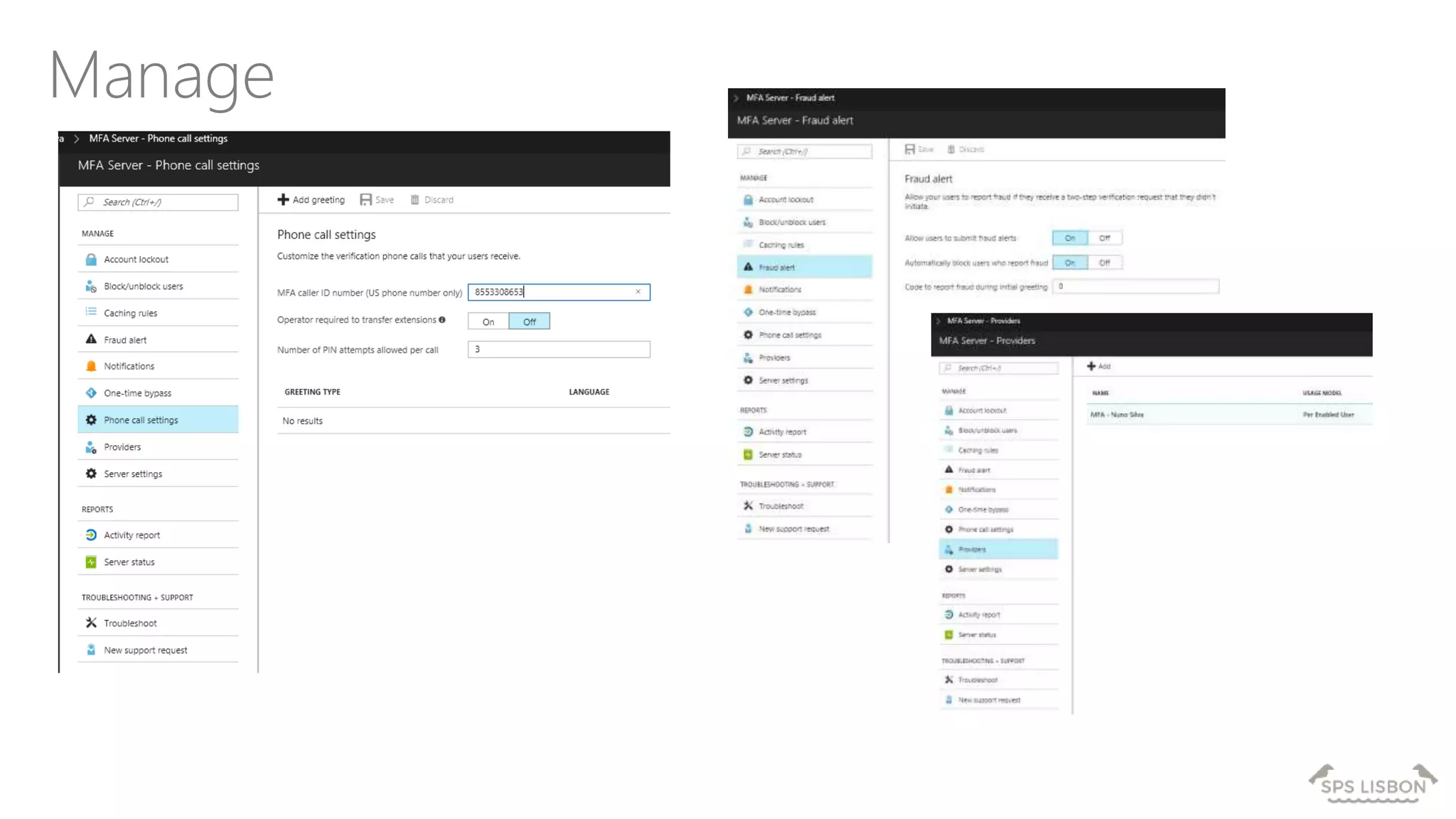
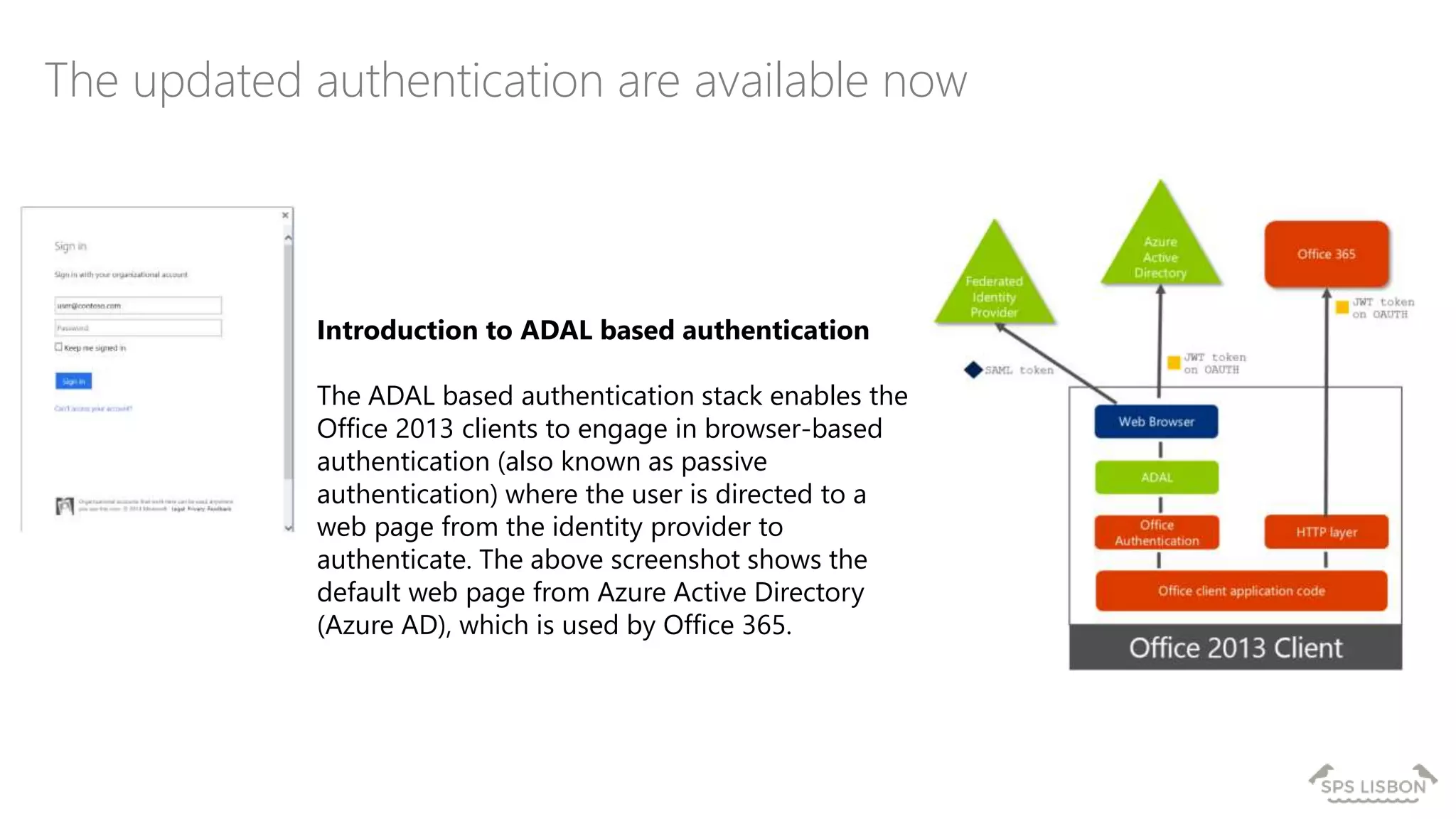
The document discusses multi-factor authentication (MFA) for Office 365 using Microsoft Azure Active Directory, emphasizing its importance in enhancing security and protecting user data. It details various MFA methods, including hardware tokens and phone-based authentication, while highlighting the integration and support for Office 2013 clients. Additionally, it offers insights into identity management options and the benefits of adopting Azure's MFA services for secure access to cloud applications.