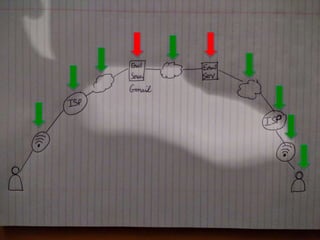
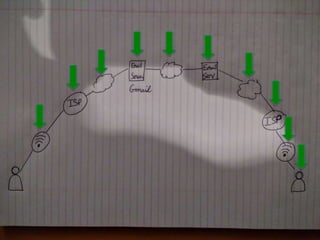
1) End-to-end encryption protects communications by encrypting messages in a way that only the sender and recipient can access, not intermediate servers or other third parties.
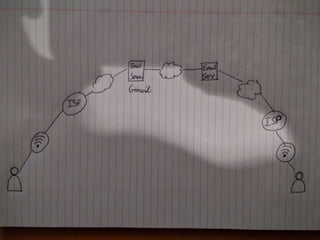
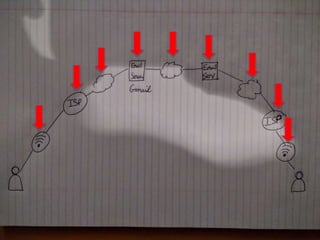
2) Currently, most email services like Gmail can be accessed by system administrators and is sent in clear text, similar to sending a postcard through the mail system.
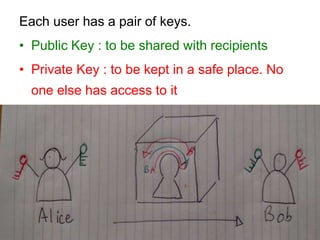
3) With end-to-end encryption, messages are encrypted like placing the message in a locked safe that only the intended recipient can open, providing privacy and security from threats of surveillance, hacking and other attacks.