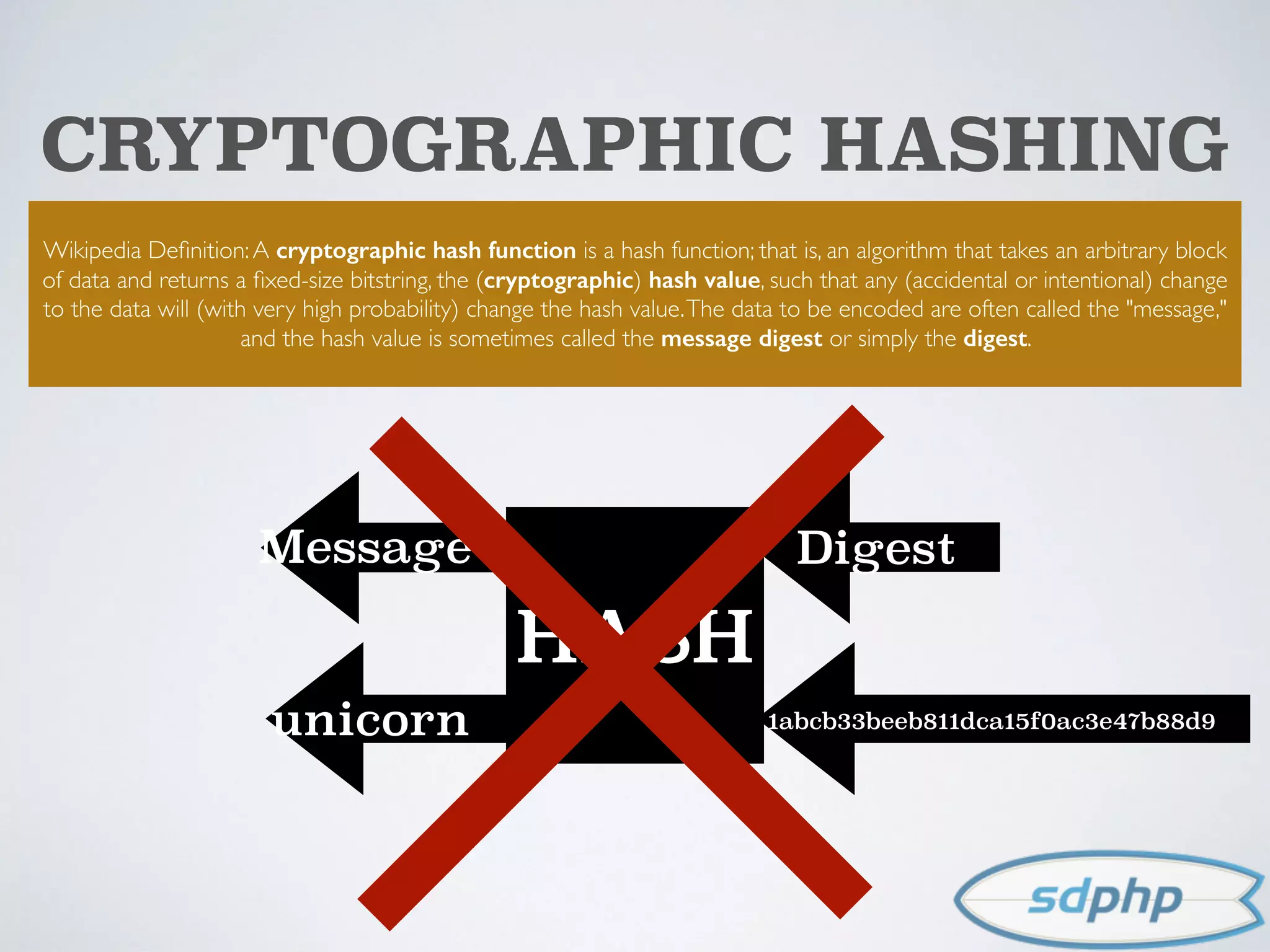
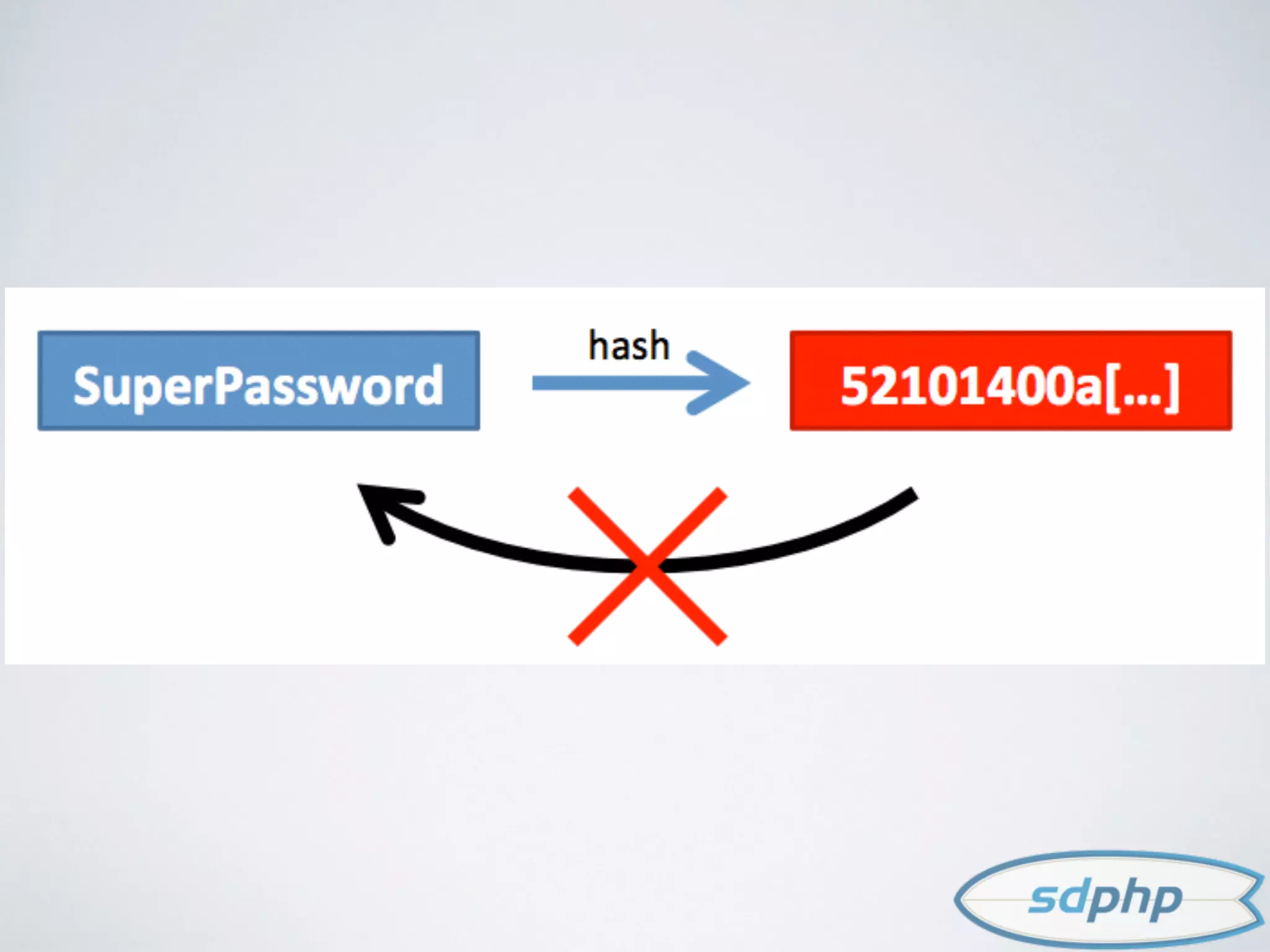
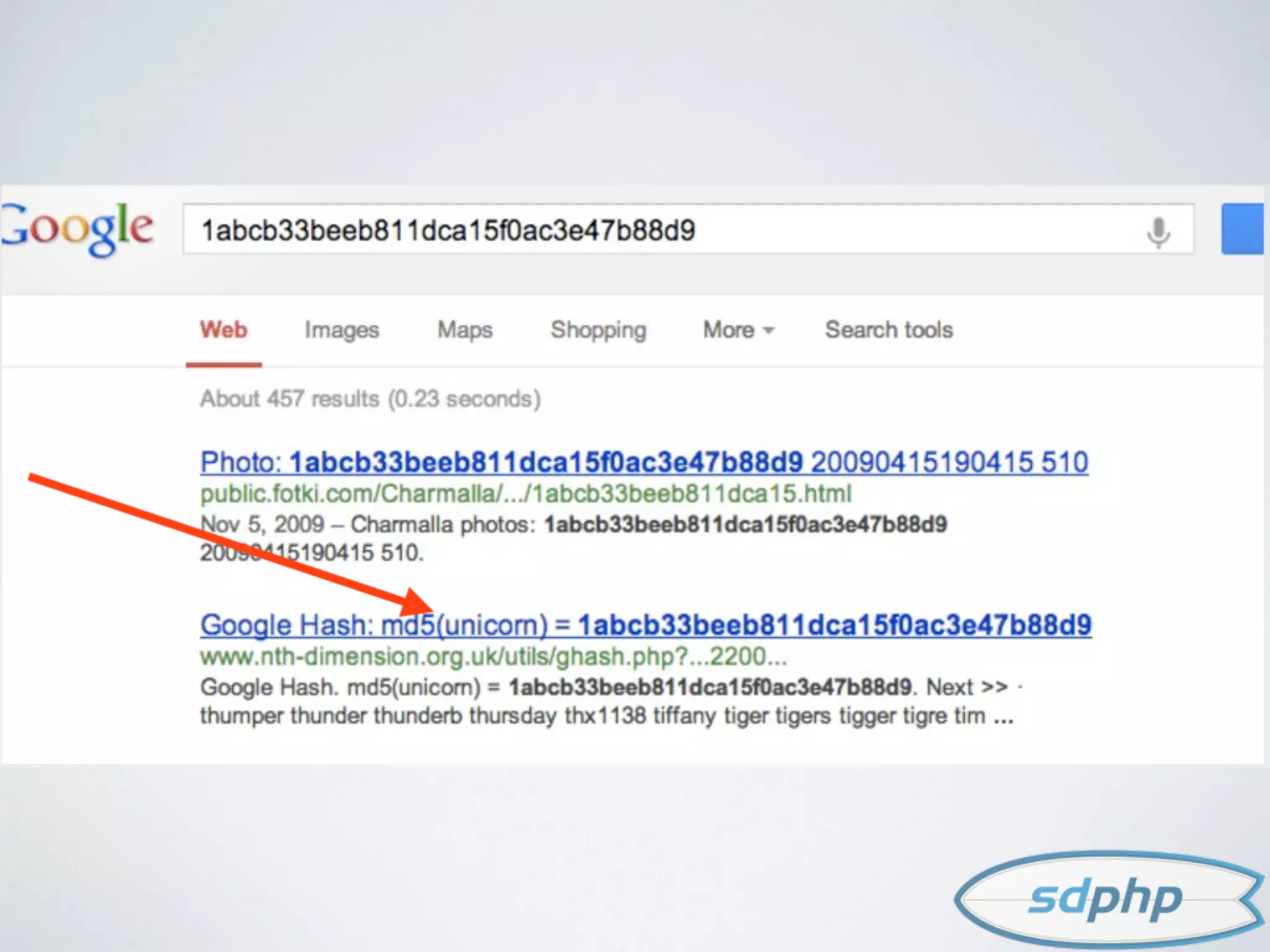
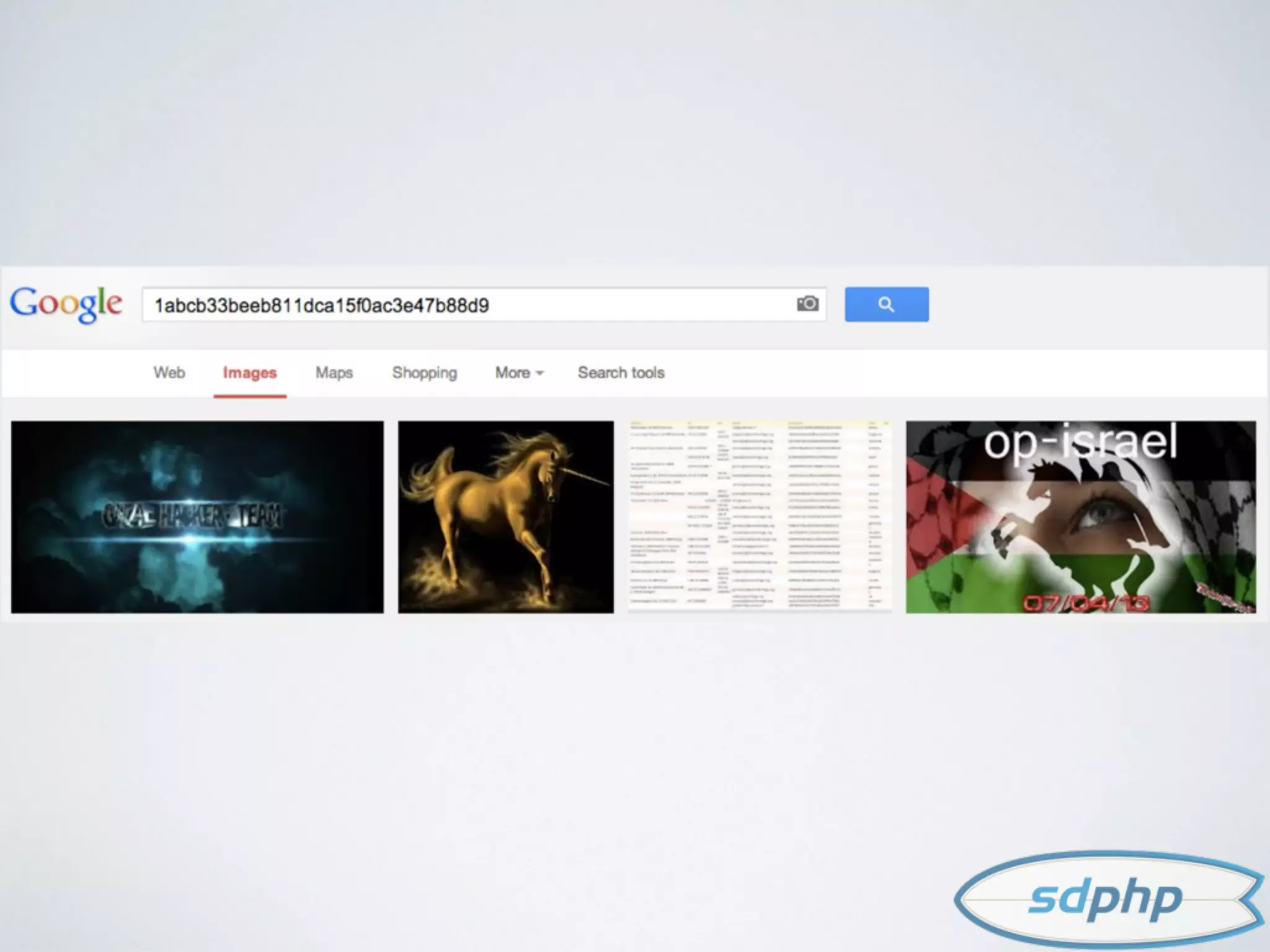
The document discusses various aspects of encryption and password security, emphasizing the importance of hashing and salting passwords to protect against vulnerabilities like SQL injection. It highlights modern practices such as using bcrypt for password hashing and advises against storing sensitive data that requires encryption. The document also explores different cryptographic algorithms and methods, stressing the need for strong techniques to ensure data integrity and security.











![CLEAR TEXT
$username = $_POST['username'];
$password = $_POST['password'];
$user = getUserByUsername($username);
$authenticated = false;
if ($user->password == $password) {
$authenticated = true;
}
*example only: not meant to be used](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-12-2048.jpg)







![MD5 EXAMPLE
$username = $_POST['username'];
$password = $_POST['password'];
$user = getUserByUsername($username);
$authenticated = false;
if ($user->password == md5($password)) {
$authenticated = true;
}
*example only: not meant to be used](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-23-2048.jpg)
![MD5 EXAMPLE
$username = $_POST['username'];
$password = $_POST['password'];
$user = getUserByUsername($username);
$authenticated = false;
if ($user->password == md5($password)) {
$authenticated = true;
}
*example only: not meant to be used](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-24-2048.jpg)
![AVAILABLE ALGORITHMS
<?php
print_r(hash_algos());
Array
(
[0] => md2
[1] => md4
[2] => md5
[3] => sha1
[4] => sha224
[5] => sha256
[6] => sha384
[7] => sha512
[8] => ripemd128
[9] => ripemd160
[10] => ripemd256
[11] => ripemd320
[12] => whirlpool
[13] => tiger128,3
[14] => tiger160,3
[15] => tiger192,3
[16] => tiger128,4
[17] => tiger160,4
[18] => tiger192,4
[19] => snefru
[20] => snefru256
[21] => gost
[22] => gost-crypto
[23] => adler32
[24] => crc32
[25] => crc32b
[26] => fnv132
[27] => fnv1a32
[28] => fnv164
[29] => fnv1a64
[30] => joaat
[31] => haval128,3
[32] => haval160,3
[33] => haval192,3
[34] => haval224,3
[35] => haval256,3
[36] => haval128,4
[37] => haval160,4
[38] => haval192,4
[39] => haval224,4
[40] => haval256,4
[41] => haval128,5
[42] => haval160,5
[43] => haval192,5
[44] => haval224,5
[45] => haval256,5
)](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-25-2048.jpg)



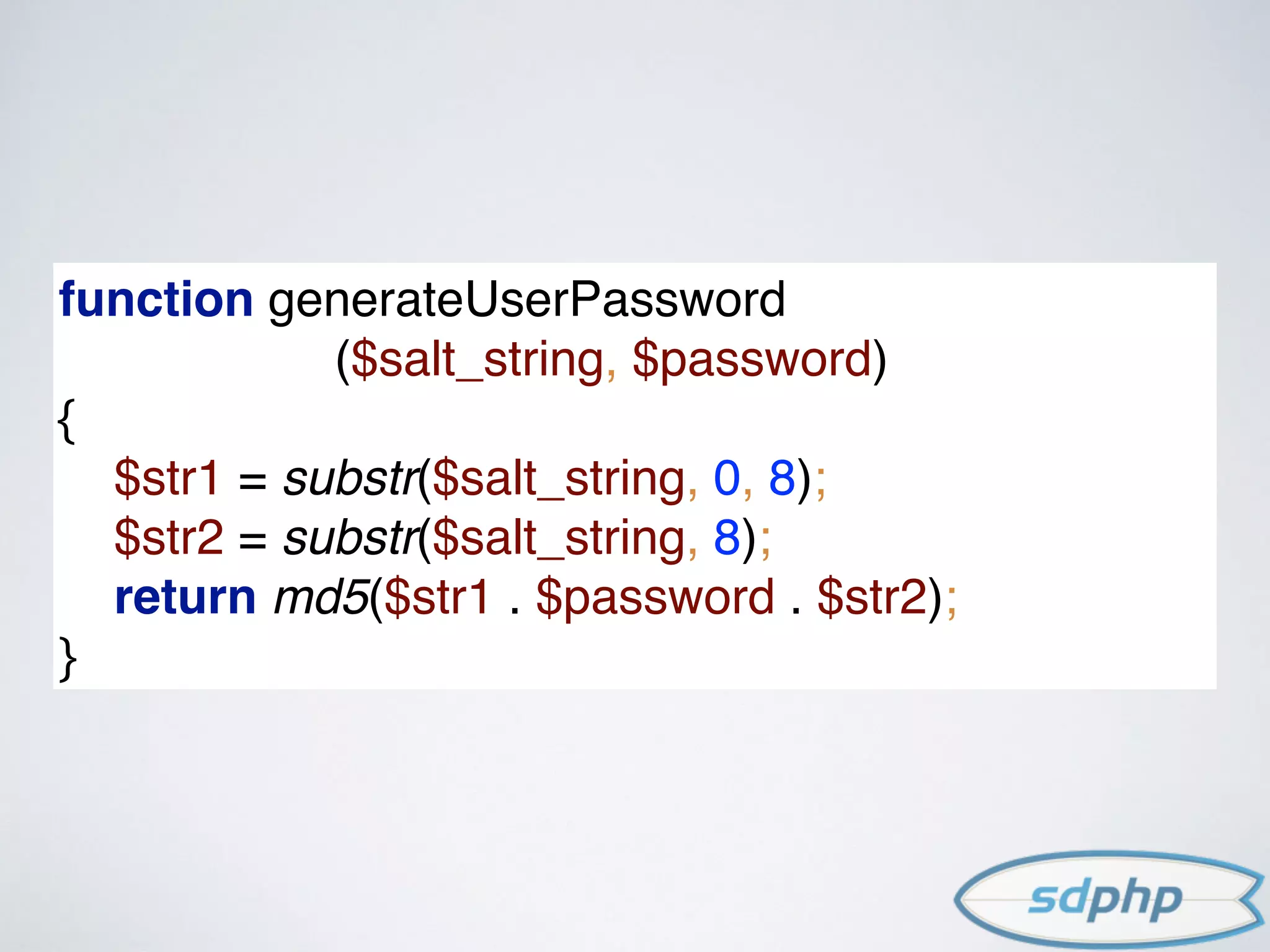
![ADDING SALT
In cryptography, a salt is random data that is used as an additional input to a one-way function that hashes a password or
passphrase.[1]The primary function of salts is to defend against dictionary attacks versus a list of password hashes and
against pre-computed rainbow table attacks.](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-32-2048.jpg)
![ADDING SALT
In cryptography, a salt is random data that is used as an additional input to a one-way function that hashes a password or
passphrase.[1]The primary function of salts is to defend against dictionary attacks versus a list of password hashes and
against pre-computed rainbow table attacks.
$hash = md5('RAND_SALT' . $password);](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-33-2048.jpg)
![ADDING SALT
In cryptography, a salt is random data that is used as an additional input to a one-way function that hashes a password or
passphrase.[1]The primary function of salts is to defend against dictionary attacks versus a list of password hashes and
against pre-computed rainbow table attacks.
$hash = md5('RAND_SALT' . $password);
RAND_SALT must come from a cryptographically secure
source.
Do not use (rand, mt_rand, uniqid)
Do use (/dev/urandom, mcrypt, openssl)](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-34-2048.jpg)
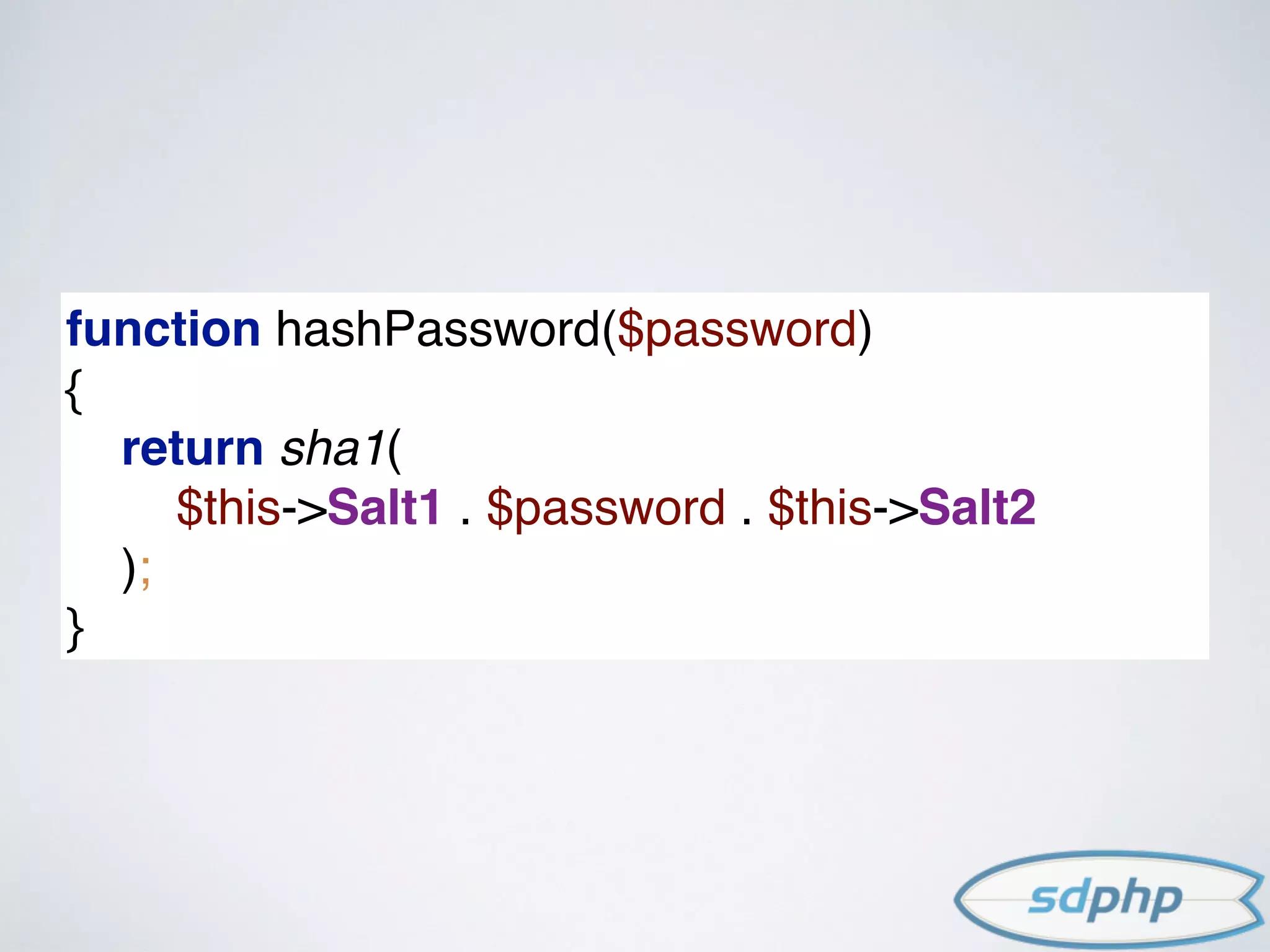
![$username = $_POST['username'];
$password = $_POST['password'];
$user = getUserByUsername($username);
$authenticated = false;
if ($user->password == md5($user->salt . $password))
{
$authenticated = true;
}
*example only: not meant to be used
MD5+SALT EXAMPLE](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-35-2048.jpg)



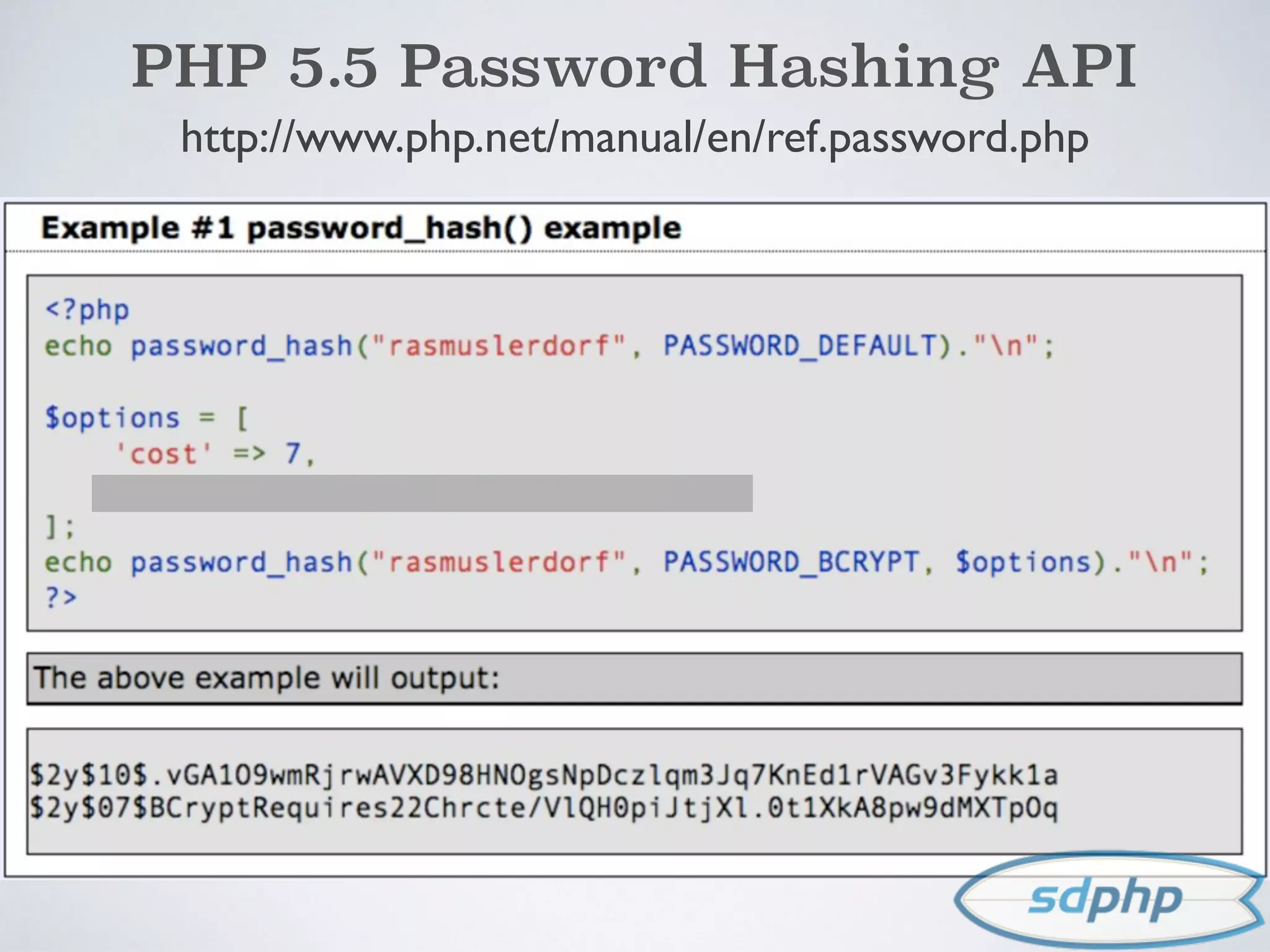
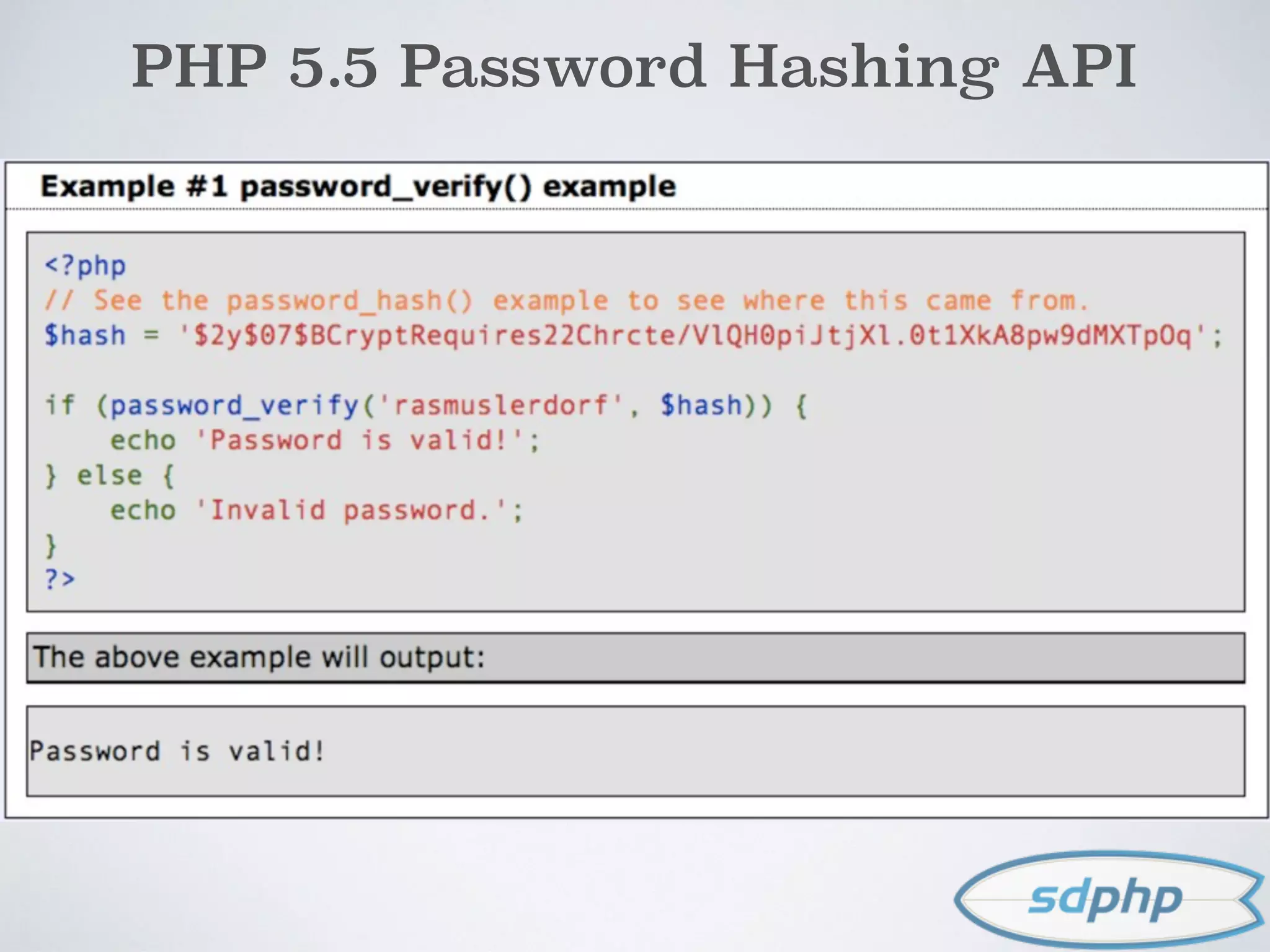

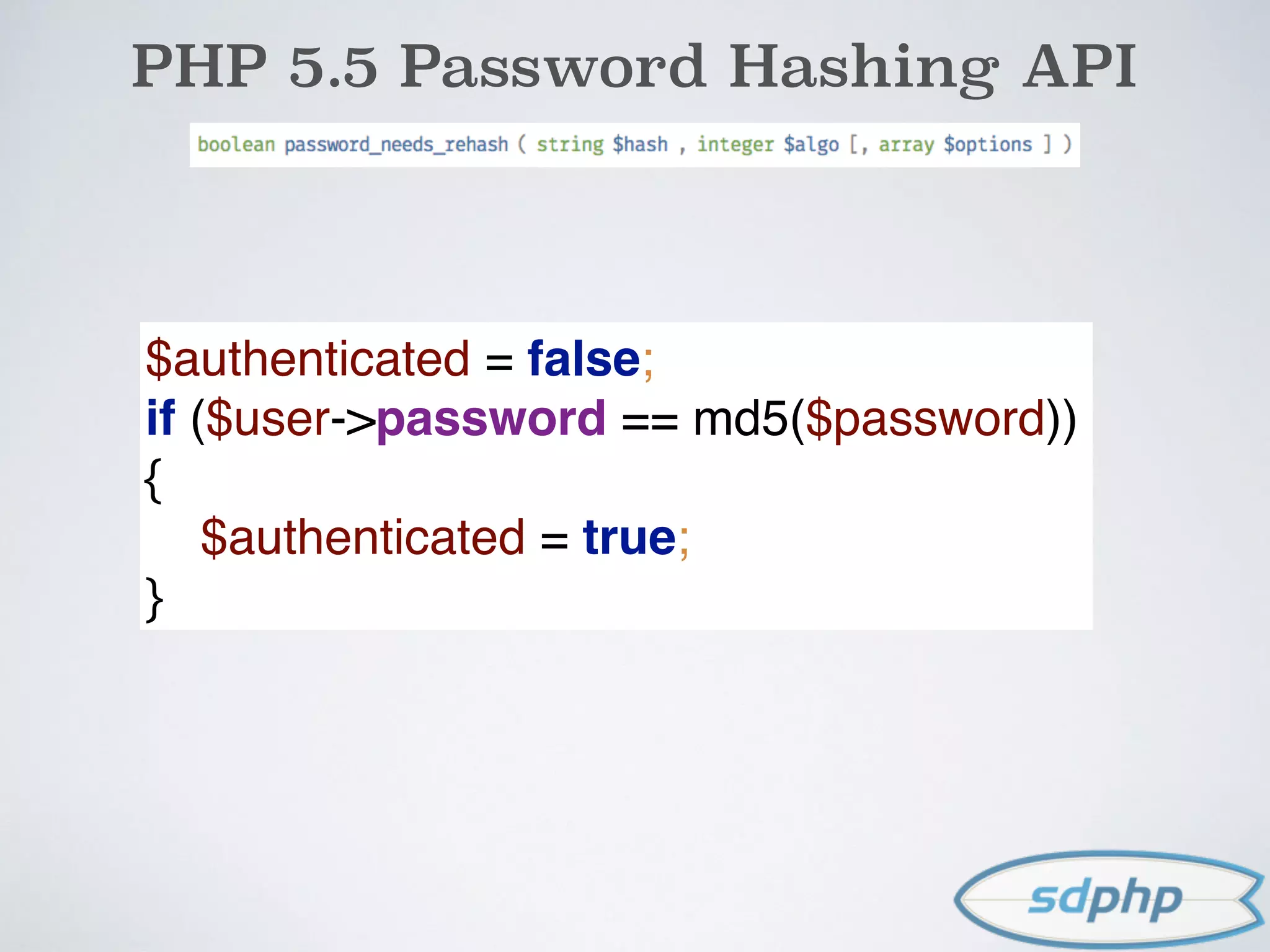
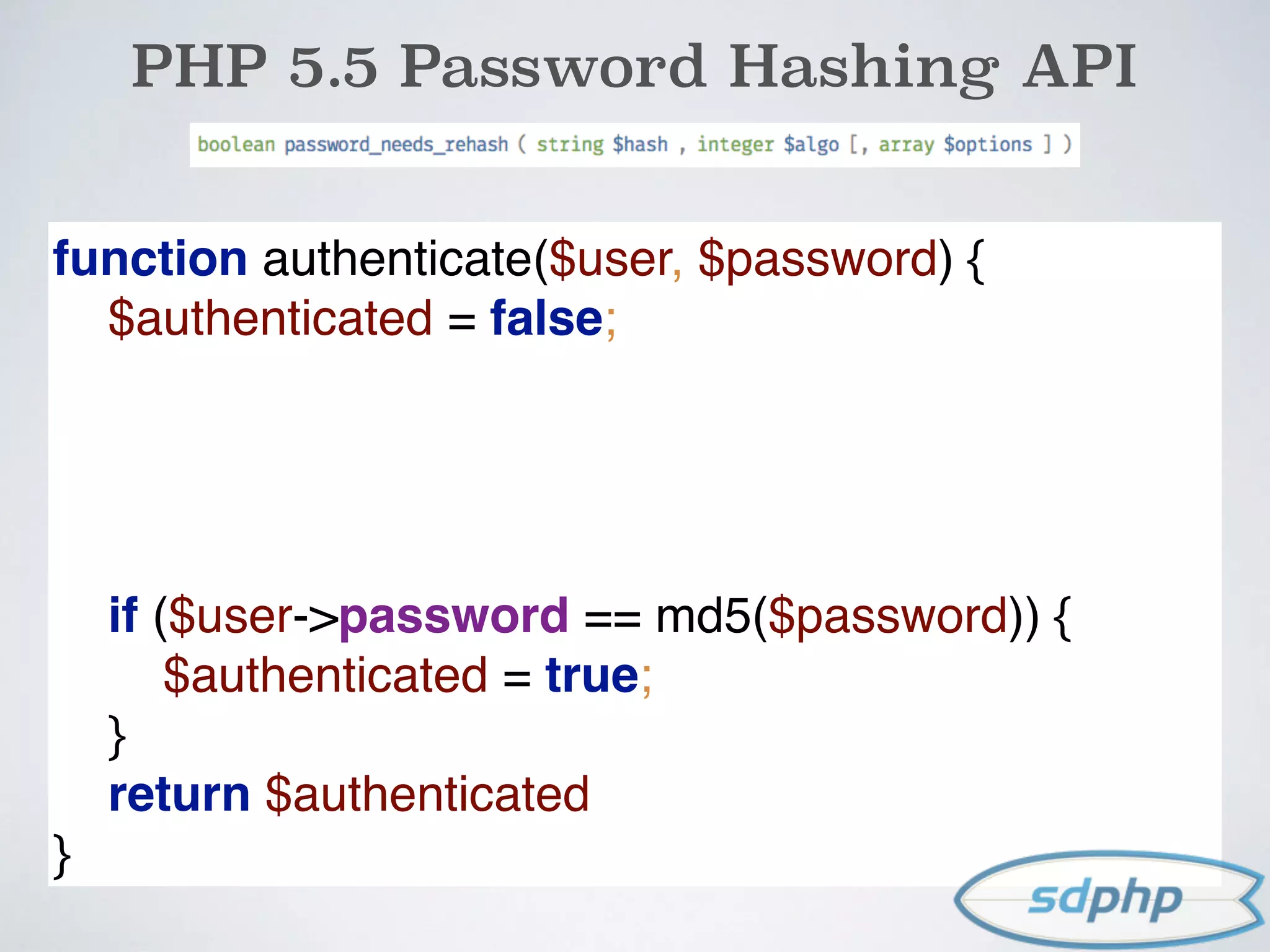
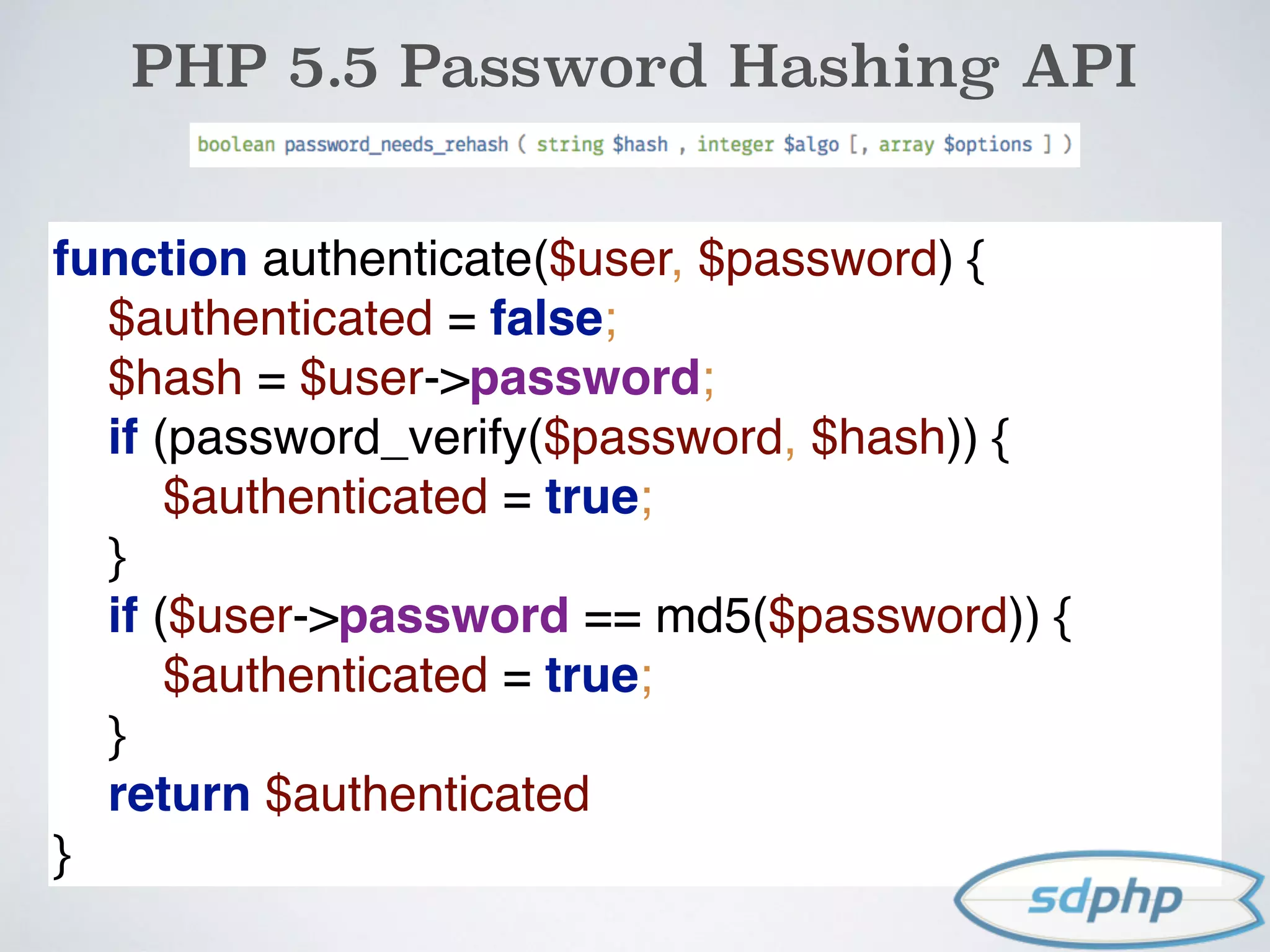
![PHP 5.5 Password Hashing API
$username = $_POST['username'];
$password = $_POST['password'];
$user = getUserByUsername($username);
if (authenticate($user, $password)) {
if (password_needs_rehash
($user->password, PASSWORD_DEFAULT))
{
$user->password =
password_hash($password, PASSWORD_DEFAULT);
$user->save();
}
}](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-47-2048.jpg)


















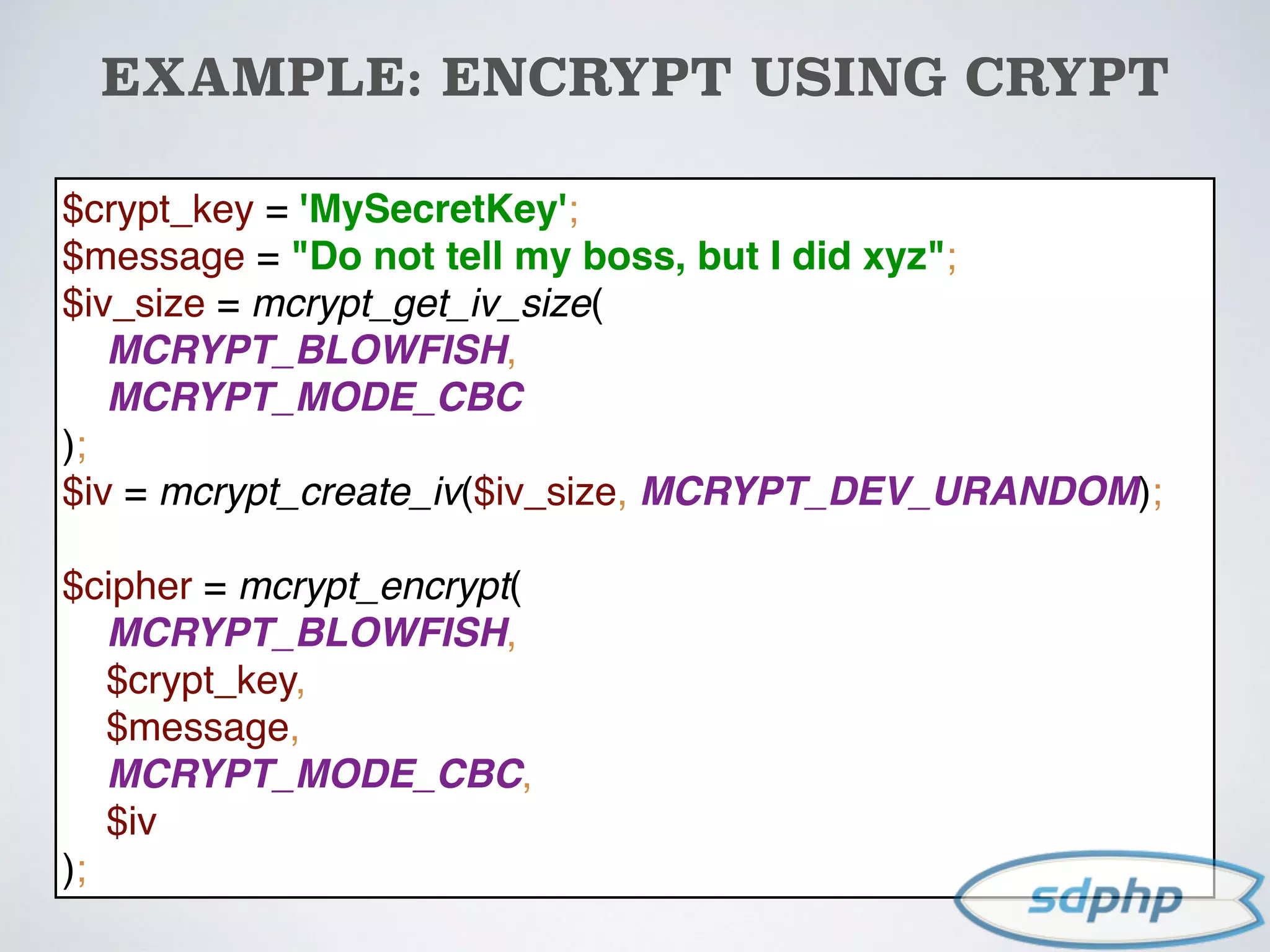








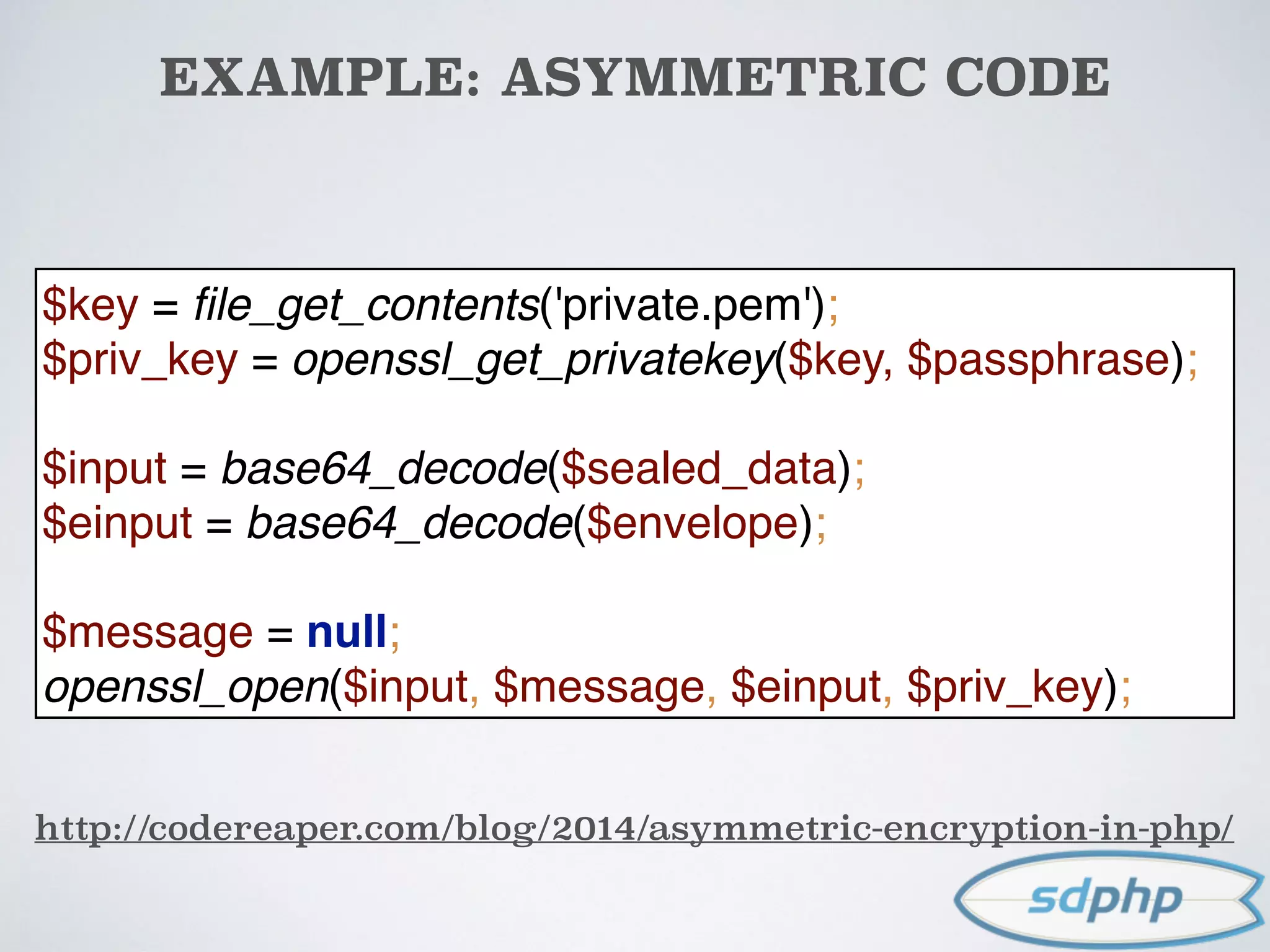
![EXAMPLE: ASYMMETRIC CODE
http://codereaper.com/blog/2014/asymmetric-encryption-in-php/
$key = file_get_contents('public.pem');
$public_key = openssl_get_publickey($key);
$message = "Do not tell my boss, but I did xyz";
$cipher = $e = null;
openssl_seal($message, $cipher, $e, array($public_key));
$sealed_data = base64_encode($cipher);
$envelope = base64_encode($e[0]);
openssl req -x509 -newkey rsa:2048 -keyout private.pem -out
public.pem -days 365](https://image.slidesharecdn.com/encryption-150122203651-conversion-gate02/75/Encryption-It-s-For-More-Than-Just-Passwords-91-2048.jpg)