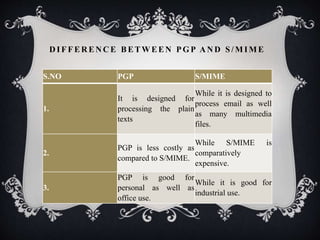
The document discusses email security, emphasizing its importance in protecting communications from cyber threats through encryption and authentication methods. It covers key protocols like Pretty Good Privacy (PGP) and S/MIME, detailing their functionalities, benefits, and differences in security algorithms. Key features include spam filtering, anti-virus protection, and measures to ensure confidentiality and integrity of email messages.