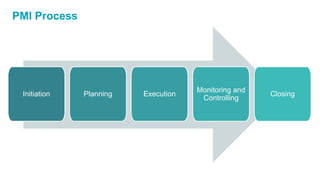
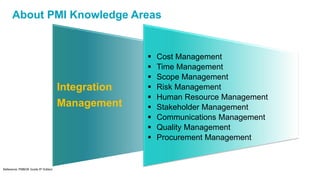
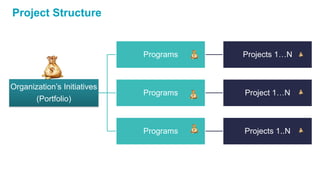
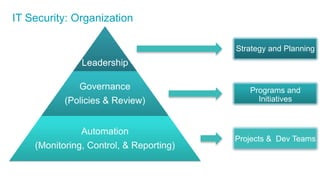
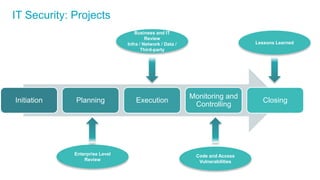
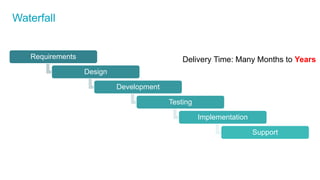
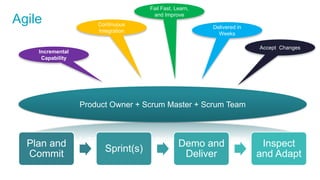
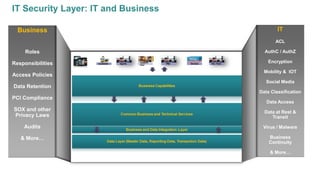
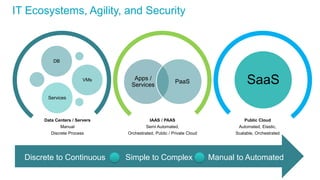
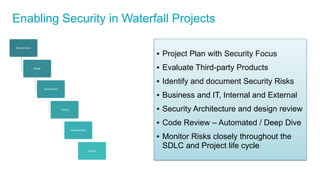
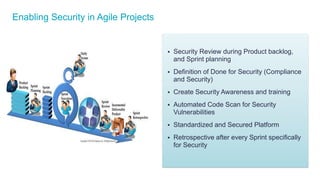
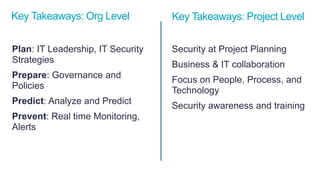
The document discusses the importance of integrating security into IT projects, highlighting the complexities and risks associated with large-scale enterprise projects. It emphasizes the need for collaboration between business and IT, security training, and the application of security throughout the project lifecycle in both waterfall and agile methodologies. Key takeaways include the development of organizational security strategies and the need for real-time monitoring and awareness to mitigate risks.