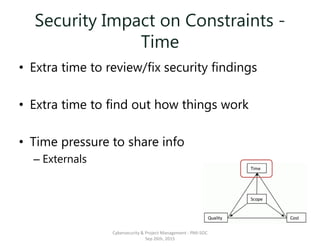
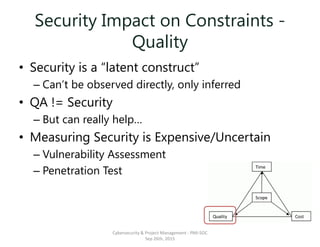
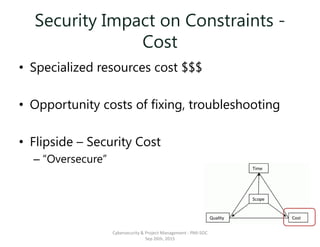
The document discusses the integration of cybersecurity within project management, emphasizing the importance of addressing security early in the project phases to reduce costs and risks. It outlines various project phases including initiation, planning, execution, and closing, highlighting the need for security assessments and compliance considerations. Furthermore, it emphasizes the importance of understanding security constraints affecting scope, time, quality, and cost while advocating for a proactive approach to security practices in project management methodology.





![Human Triggers/Motivation
• “Just get it done…”
– Project Management -> …as planned
– Business -> … to get functionality. [What details?]
– Technical -> .. and move to next task. [What impact?]
– Security -> … so it doesn’t expose us. [What impact?]
– Vendors -> … to keep business going.
• Beware Underlying Economics
• Externalities:
– security imposing controls
– business underscoping actual risks
• Moral hazard:
– Undue assumptions about risk model
Cybersecurity & Project Management - PMI-SOC
Sep 26th, 2015](https://image.slidesharecdn.com/cybersecurityandprojectmanagement-151108041744-lva1-app6892/85/Cybersecurity-Project-Management-7-320.jpg)

![Project Phase: Execution(1)
Building
• Dealing with Externals
– Sharing Information
– User and Access Management
• Security configurations
– Hardening
– Defaults!
• Security [unit] tests
– Other security testing?
• Temporary files
Cybersecurity & Project Management - PMI-SOC
Sep 26th, 2015](https://image.slidesharecdn.com/cybersecurityandprojectmanagement-151108041744-lva1-app6892/85/Cybersecurity-Project-Management-11-320.jpg)