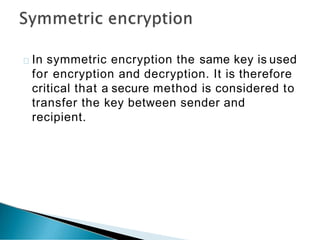
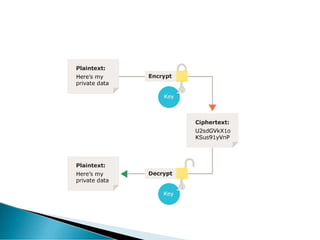
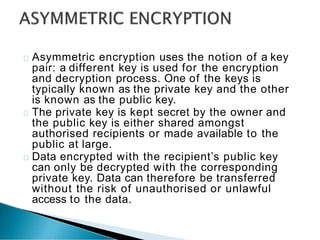
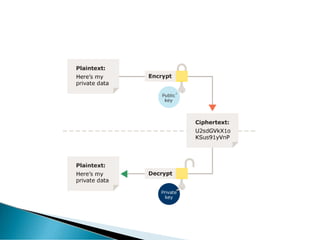
This document provides an overview of e-marketing and e-commerce. It defines e-marketing as marketing done using the internet, email, and wireless media. It discusses different types of e-marketing like article marketing and video marketing. It also defines e-commerce and the different models of e-commerce transactions including business-to-business, business-to-consumer, and consumer-to-consumer. Additional topics covered include infrastructure needs for e-commerce and some of the challenges of conducting international e-commerce.
































































![An online travel agen
[
c
3]
y(OTA) specializes in offering planning sources and
booking capabilities. Major OTAs include:
Voyages-sncf.com – revenue €2.23 billion (2008)
Expedia, Inc., including Expedia.com, Hote
]
ls.com, Hotwire.com, Travelocity and
others – revenue US$2.937 billion (2008), later expanded to
include Orbitz Worldwide, Inc., including
[6]
Orbitz, CheapTickets, ebookers,and
others – revenue US$870 million (2008)
Sabre Holdings, including lastminute.com and others – revenue US$2.9 billion
(2008)
Opodo – revenue €1.3 billion (2008)
The Priceline Group,
including Priceline.com, Booking.com,
]
Agoda.com, Kayak.com, OpenTable and
others – revenue US$1.9 billion (2008)
Travelgenio – revenue €344 million (2014)
Wotif.com – revenue A$145 million (2012)
Webjet – revenue A$59.3 million (2012)](https://image.slidesharecdn.com/emarketing-221021014219-941e0ada/85/Emarketing-pptx-74-320.jpg)


![Online social entertainment blends entertaining interactive
functionality and content including live video streaming, video
chat communications, multi-player gaming, music and videos
streaming, with social networking service such as social graph
management, forums, reviews, ratings, and geo-
location options. It is the foundation for a more immersive,
interactive, enriching and engaging c
[
1
o
]
ntent consumption
experience through social channels. Social entertainment is
distinct from social networking websites in that the former is
based fundamentally on immersive engaging experiences with
functionality, content and people, while the latter is based
primarily on building and maintaining relationships with other
users. Typically, social entertainment is defined by the individual
sites dedicated to a particular type of entertainment experience
incorporating basic social networking services.](https://image.slidesharecdn.com/emarketing-221021014219-941e0ada/85/Emarketing-pptx-77-320.jpg)


![Online social entertainment blends entertaining interactive
functionality and content including live video streaming, video
chat communications, multi-player gaming, music and videos
streaming, with social networking service such as social graph
management, forums, reviews, ratings, and geo-
location options. It is the foundation for a more immersive,
interactive, enriching and engaging c
[
1
o
]
ntent consumption
experience through social channels. Social entertainment is
distinct from social networking websites in that the former is
based fundamentally on immersive engaging experiences with
functionality, content and people, while the latter is based
primarily on building and maintaining relationships with other
users. Typically, social entertainment is defined by the individual
sites dedicated to a particular type of entertainment experience
incorporating basic social networking services.](https://image.slidesharecdn.com/emarketing-221021014219-941e0ada/85/Emarketing-pptx-80-320.jpg)