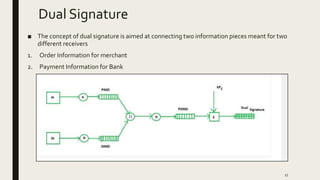
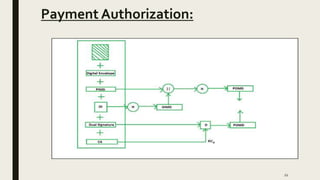
The document discusses electronic payment protocols. It describes the requirements of an e-payment protocol including anonymity, divisibility, transference, and overspending detection. It then summarizes the Kim and Lee protocol which uses certificate issuing, payment, and redemption schemes involving a user, bank, and merchant. Limitations are discussed along with a proposed protocol using a blind signature scheme involving registration, blind, transaction, and redemption schemes. Finally, it explains the Secure Electronic Transaction (SET) protocol involving participants, features, requirements, and dual signature implementation through purchase request, payment authorization, and payment capture events.


![Kim and Lee Protocol:
■ An E-Payment protocol that supports multiple merchants.
■ Protocol is divided into three schemes : (i) Certificate issuing scheme (ii) Payment Scheme (iii)
Redemption Scheme
(1) Certificate Issuing Scheme:
3
User(U) requests a
certificate to a bank B by
sending his secret
information
The bank B passes
CU[User Certificate] and
SU will be employed for
the root value in payment
scheme later
User creates his/her public
and secret key pair (PKU
,SKU) & passes PKU with IU
that contains max no: of
merchants(N) ,size of
hash (n) with his credit
info to the bank
The bank generates
special infoTU which acts
as a key factor of the root
value. Only the bank can
generate the new hash
values](https://image.slidesharecdn.com/epaymentprotocol-200517061630/85/Electronic-Payment-Protocol-3-320.jpg)