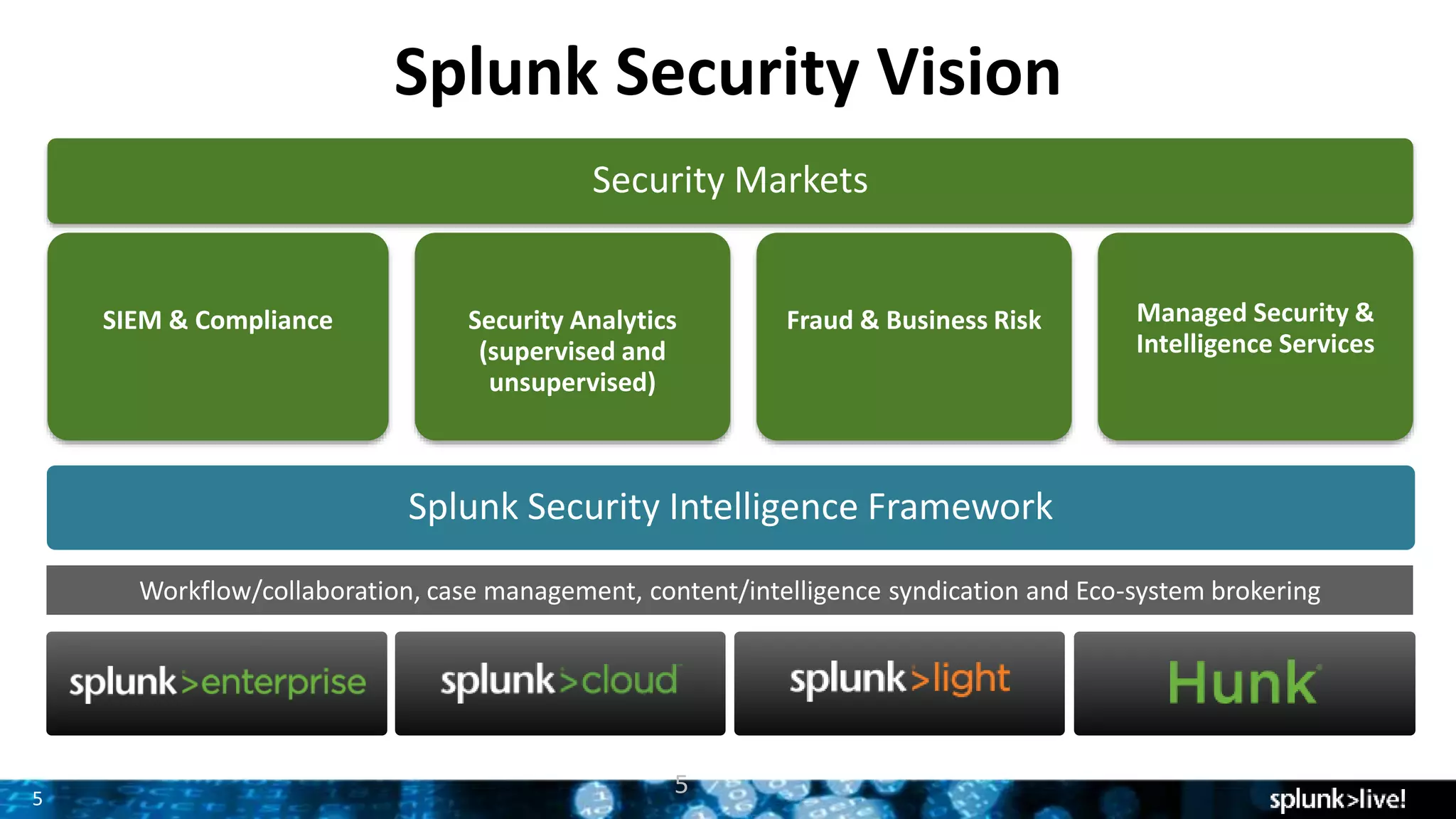
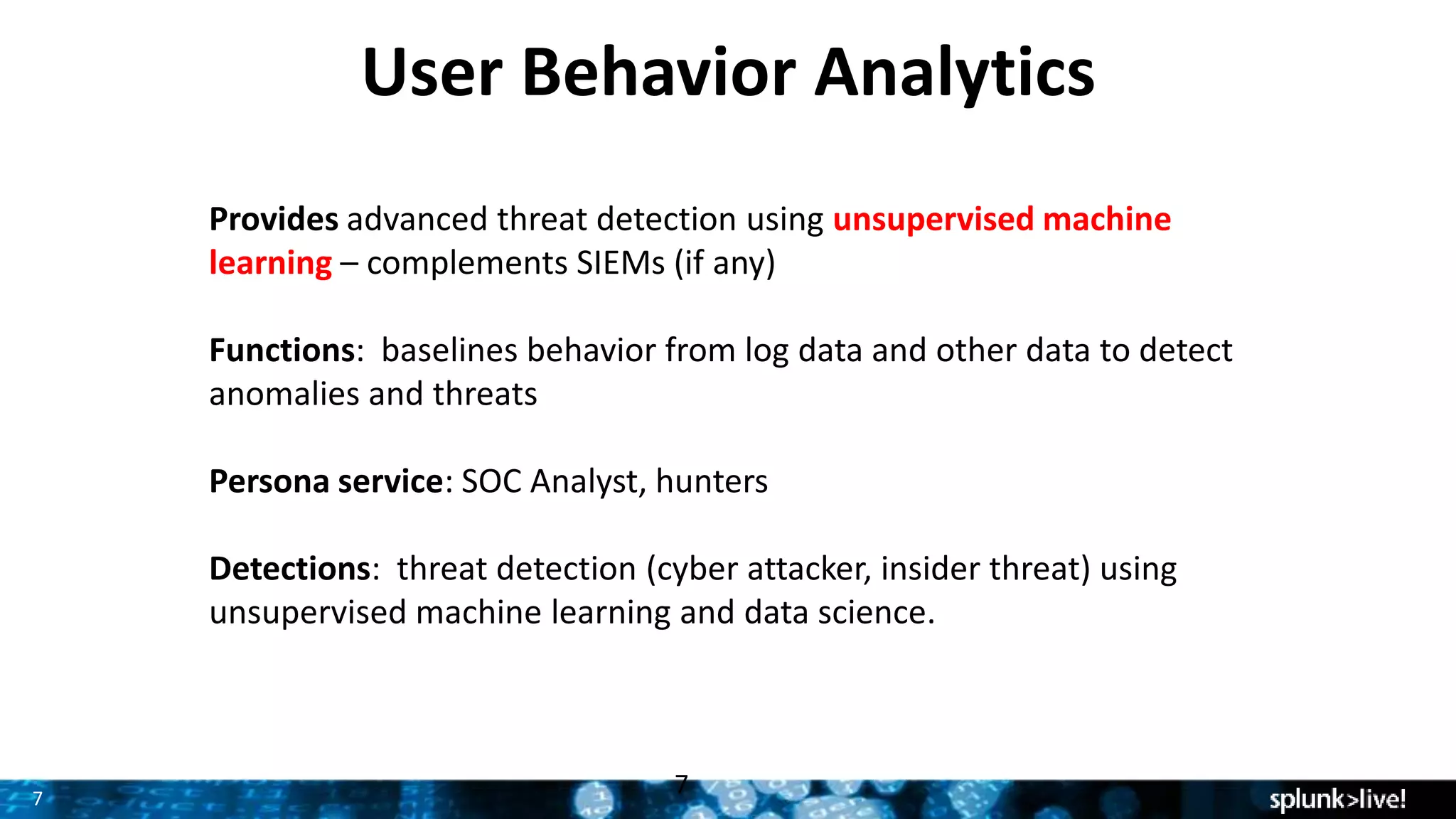
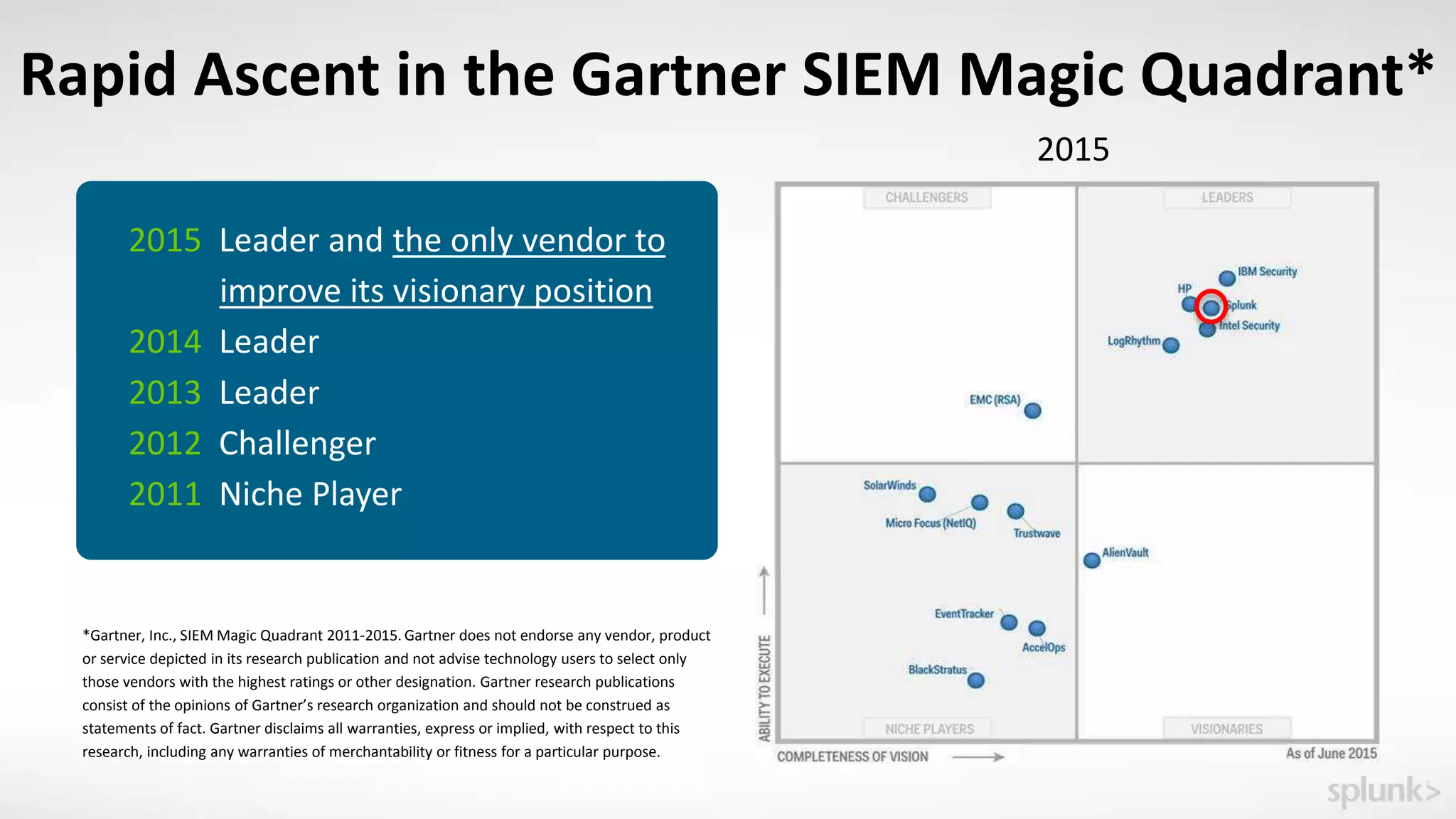
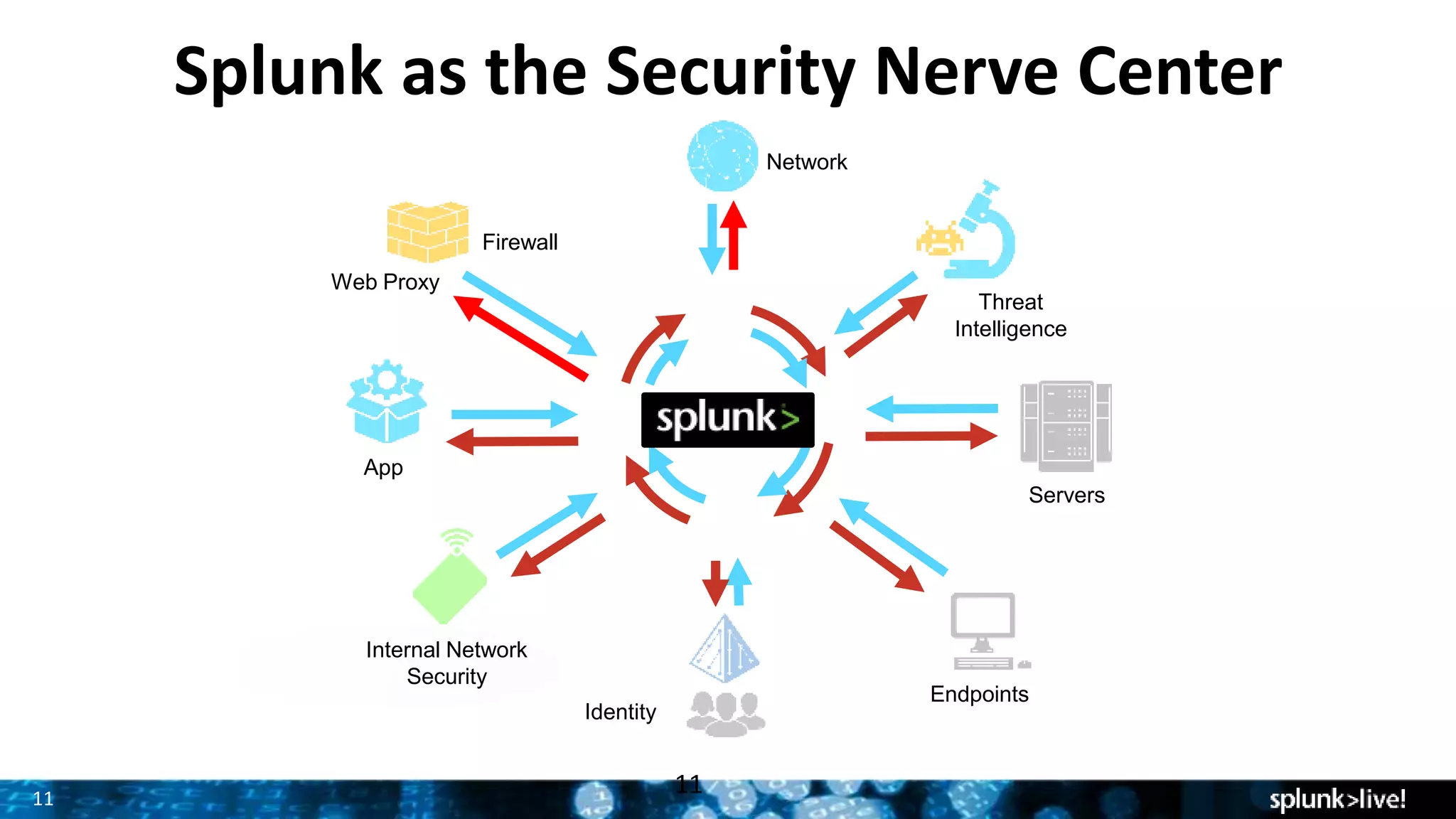
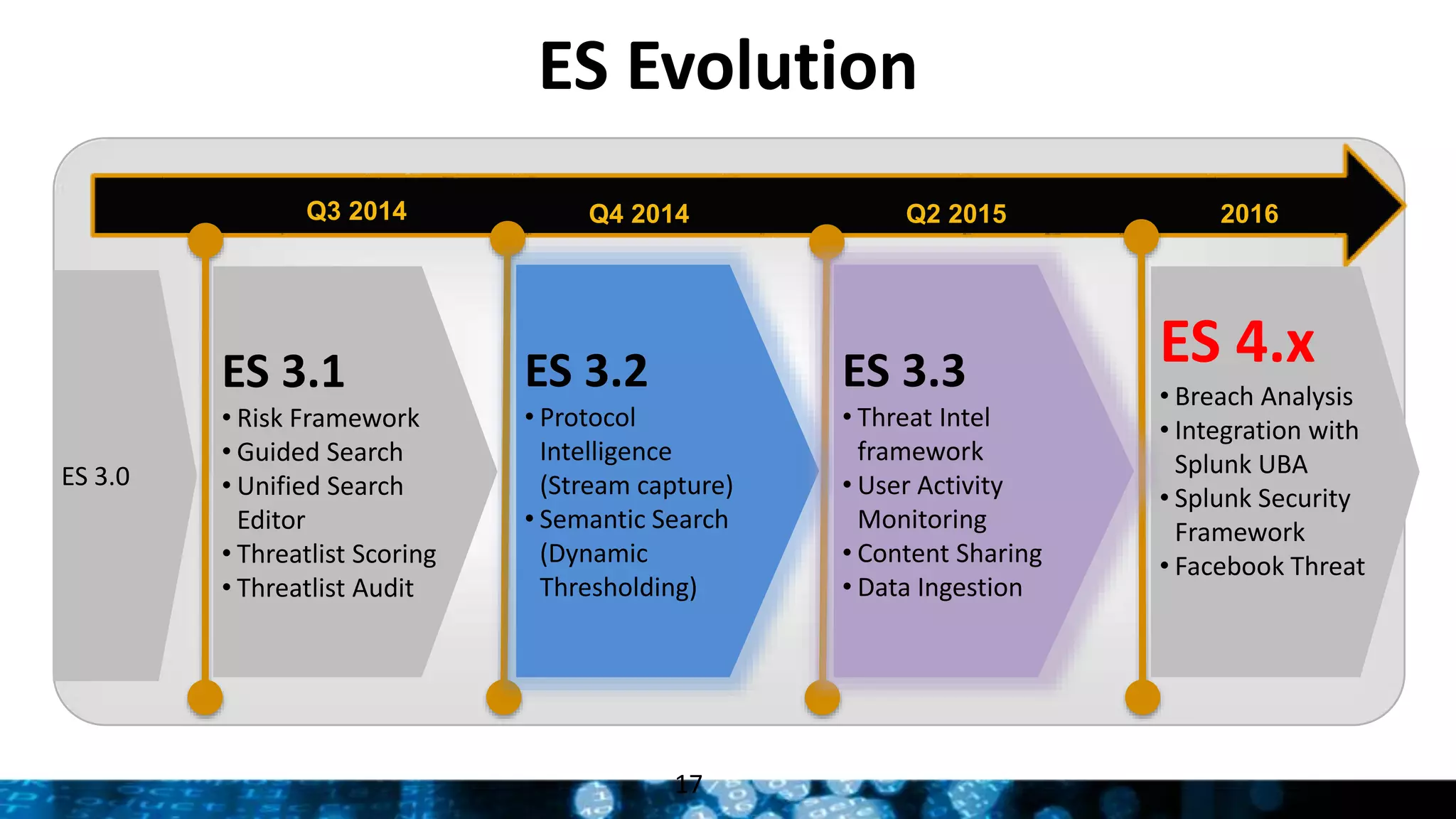
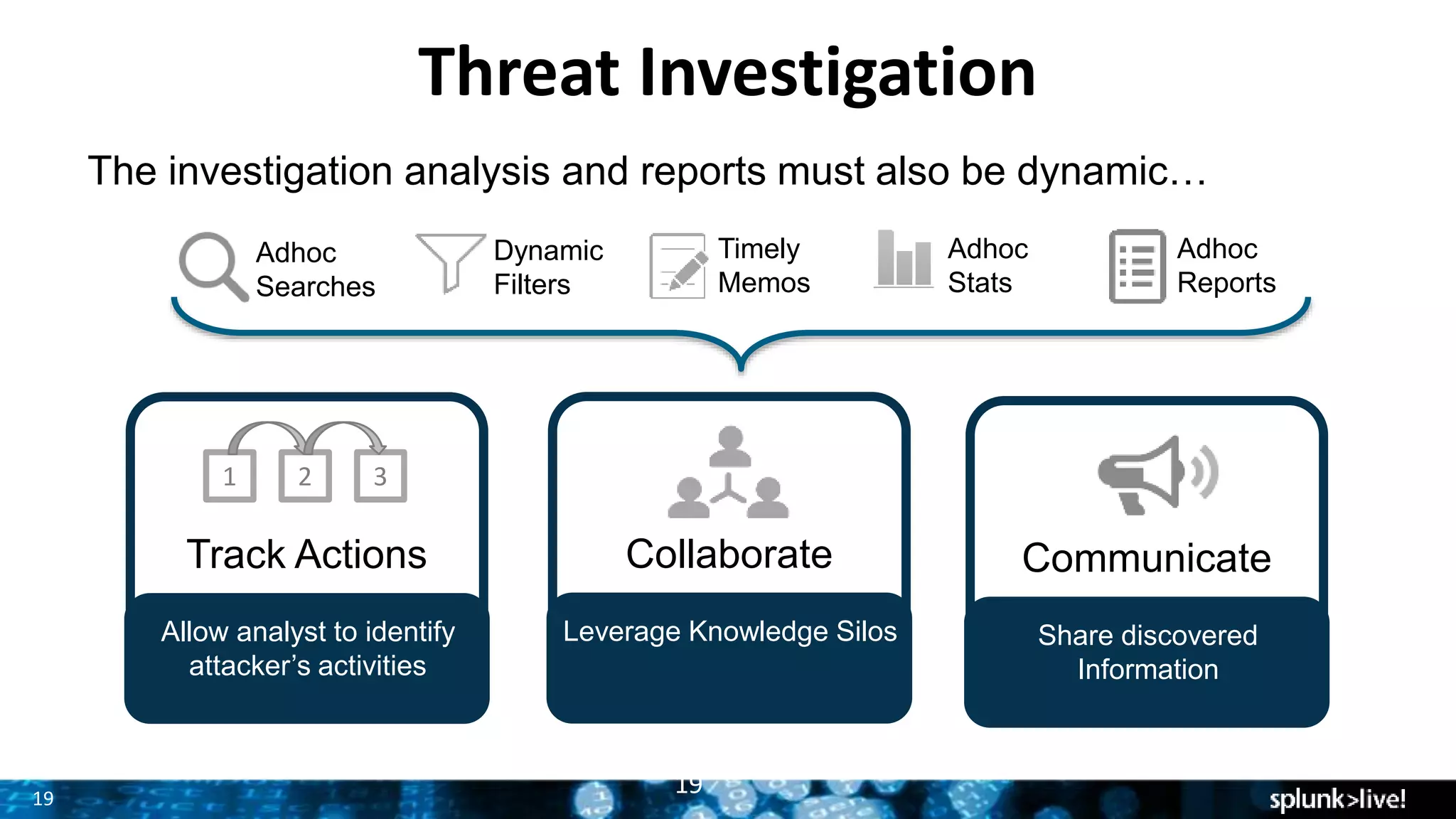
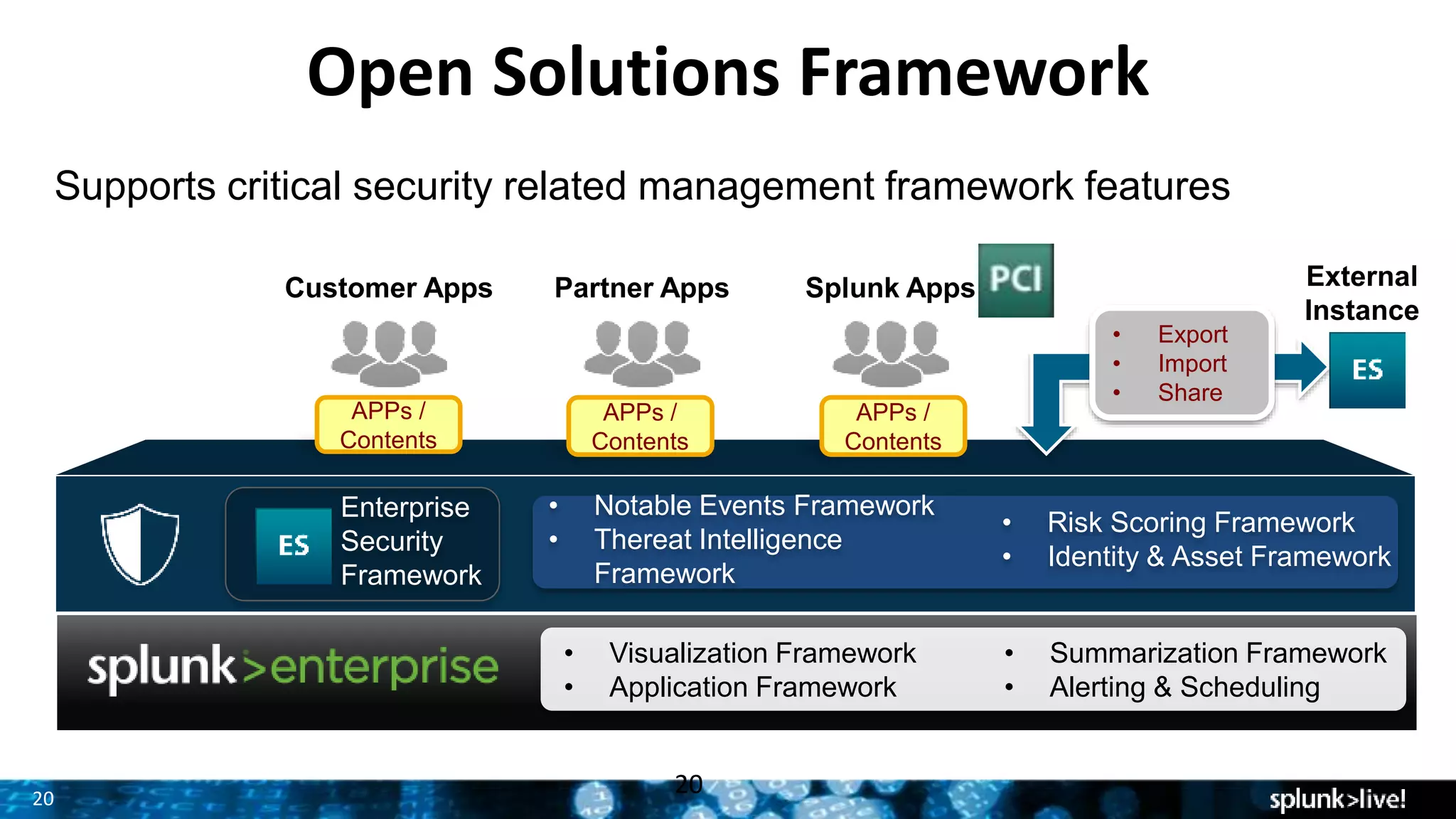
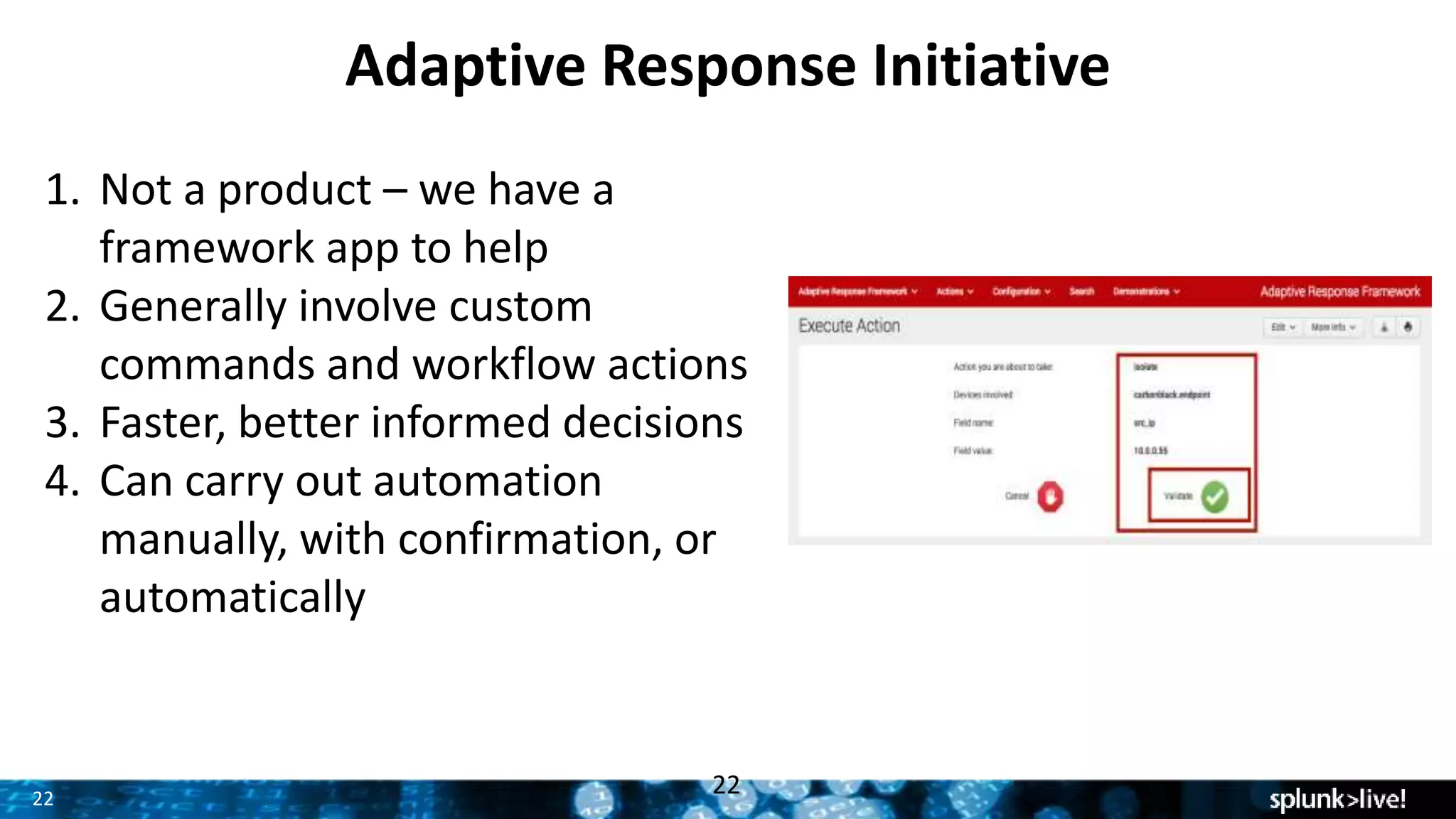
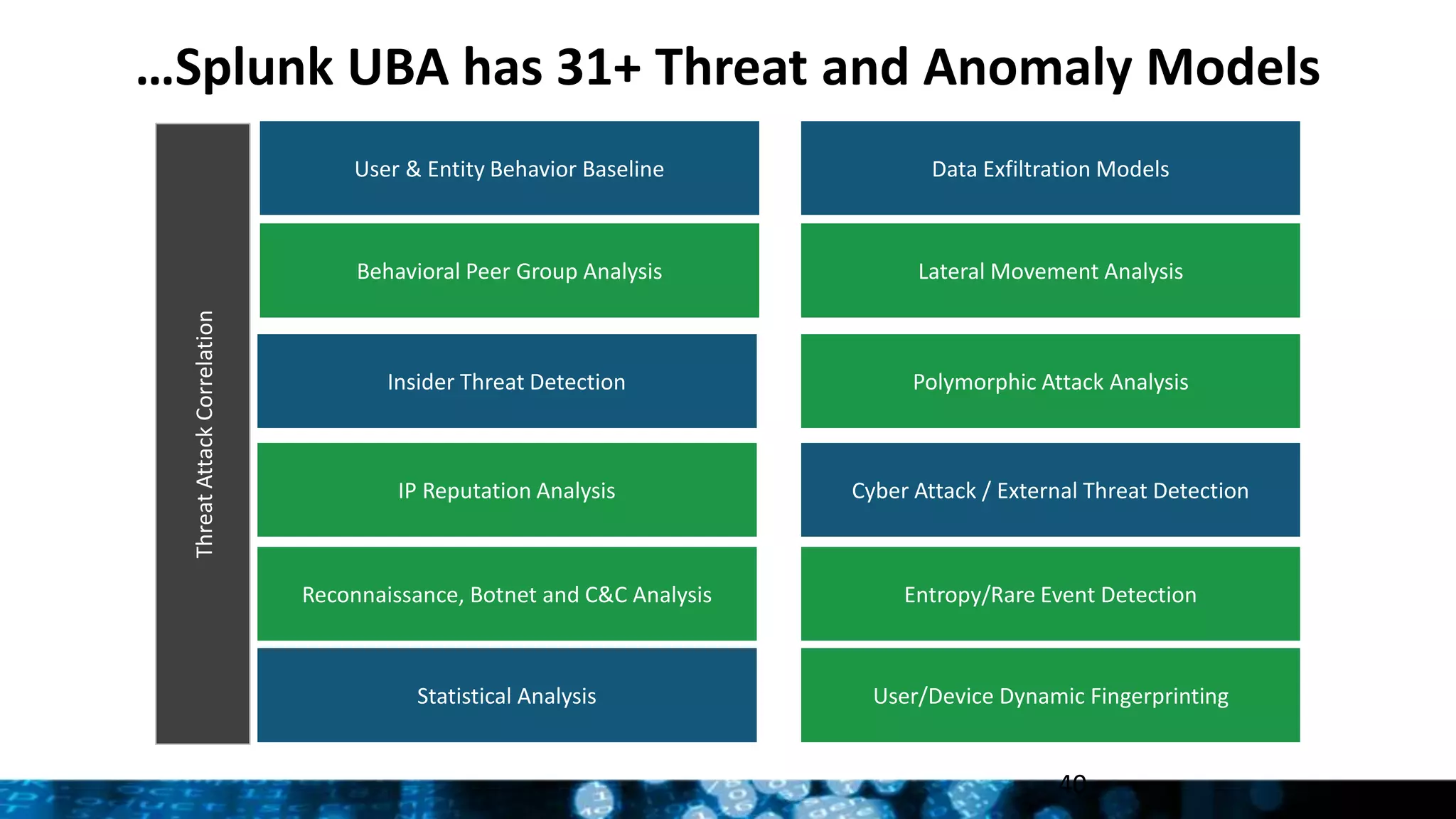
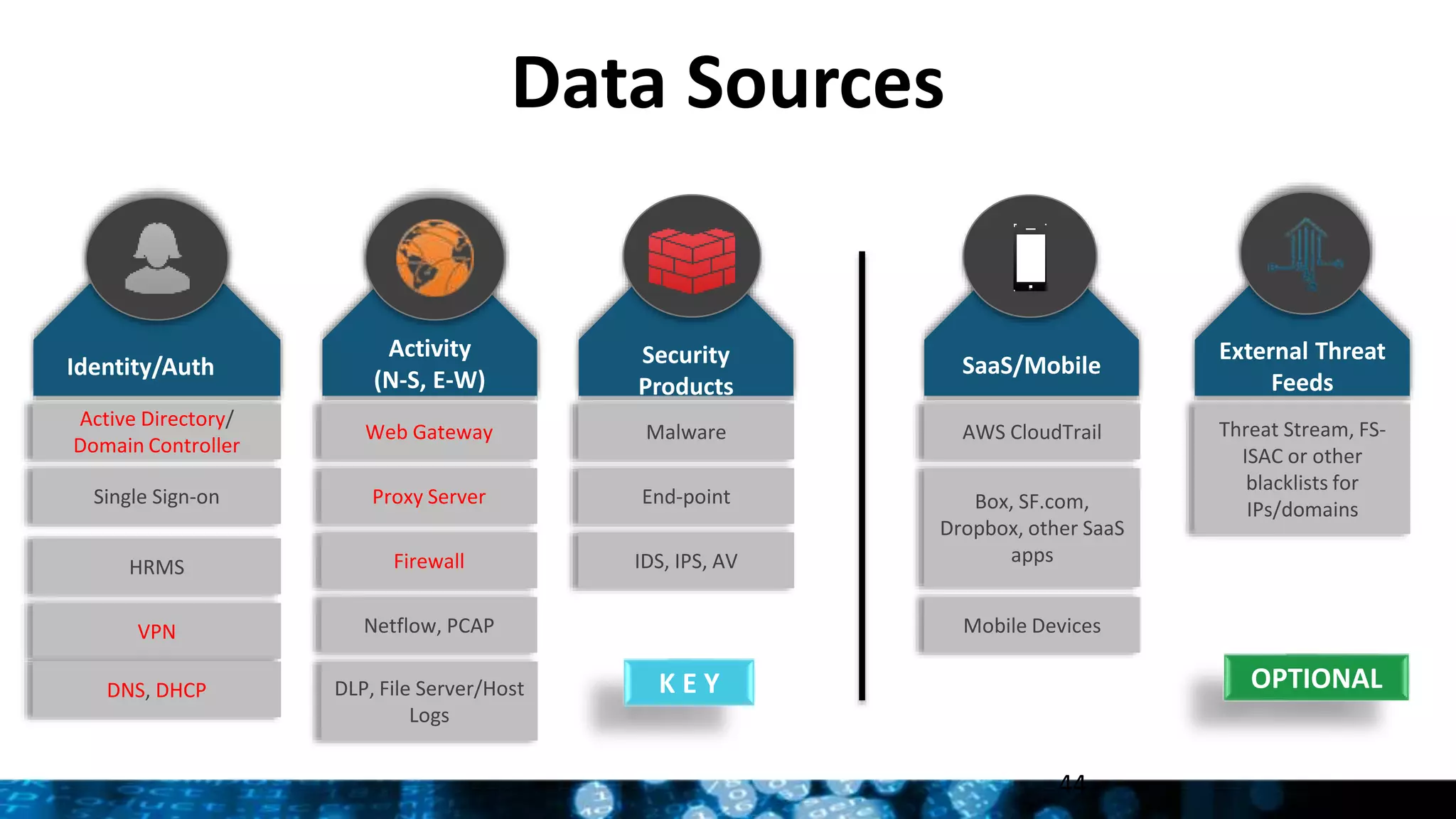
This document provides an overview and update on Splunk's Enterprise Security and User Behavior Analytics solutions. It discusses the latest releases of Splunk Enterprise, Enterprise Security, and User Behavior Analytics. It describes the key functions and use cases of Enterprise Security, which provides security monitoring, alert management, and incident response capabilities. It also outlines the main functions and use cases of User Behavior Analytics, which uses unsupervised machine learning to detect anomalies and advanced threats. The document promotes Splunk as an effective security intelligence platform to collect, analyze, and investigate machine data from various sources.