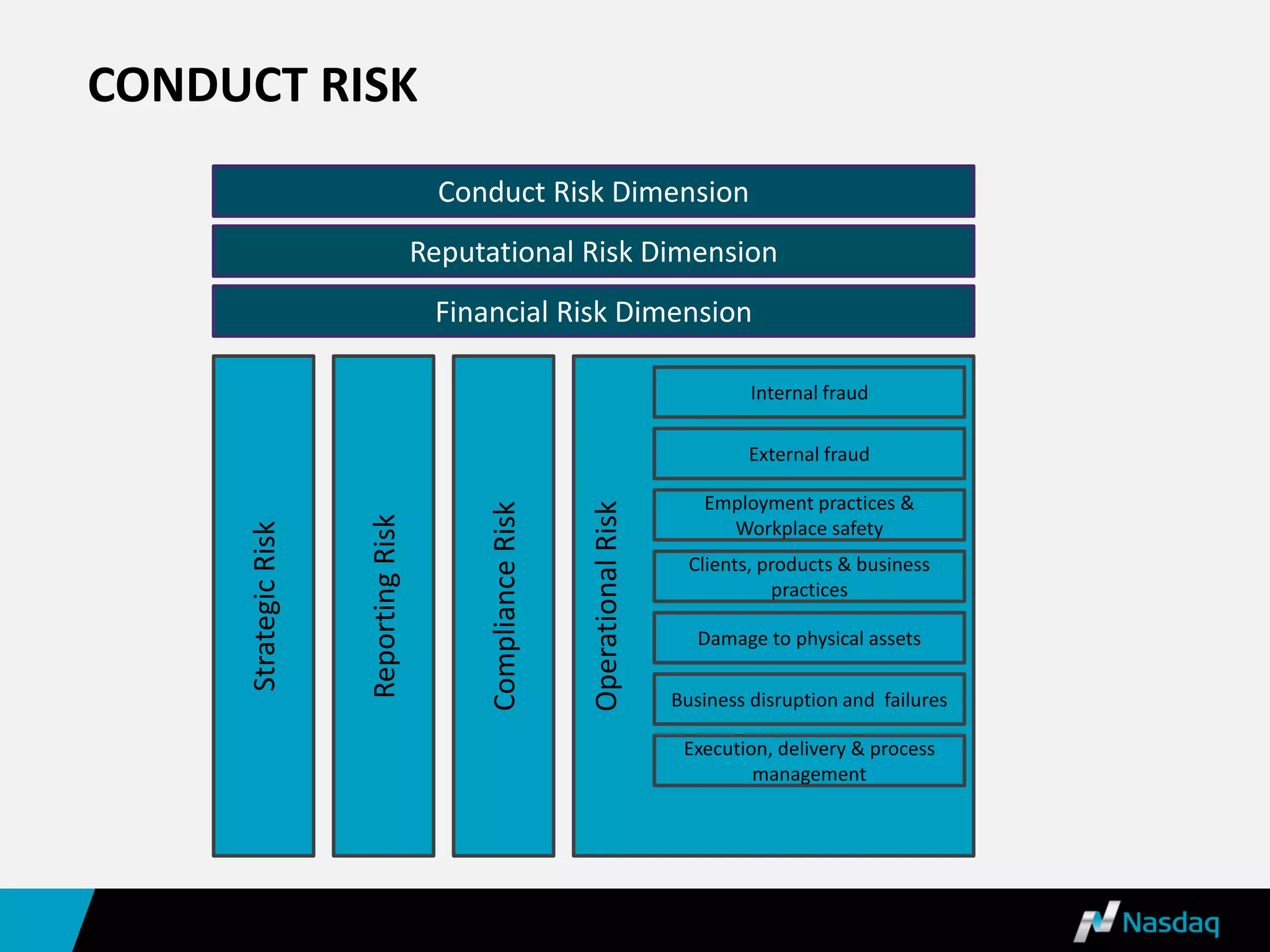
Nasdaq-Bwise is a leading provider of enterprise governance, risk management, and compliance (GRC) software, aimed at helping organizations manage key risks while improving accountability and efficiency. The document outlines various aspects of conduct risk and highlights the main areas of GRC including operational, compliance, and financial risks. It also discusses how technology facilitates risk management processes and emphasizes Nasdaq's long-term commitment to the GRC industry.