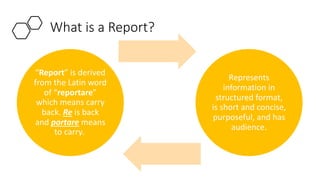
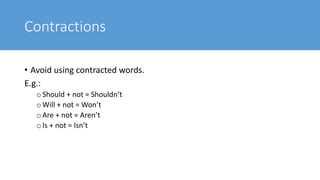
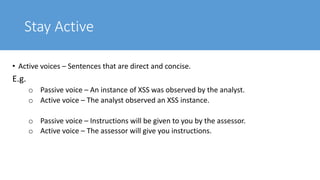
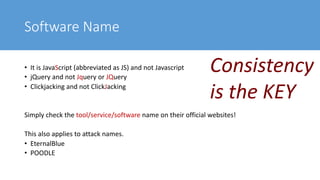
The document provides guidance on effective report writing for cyber security. It defines a report and explains that reports in cyber security are used in security operations centers, assessments, digital forensics and incident response, and governance, risk, and compliance. Common mistakes in reporting include communicating someone else's output, using vague sentences, and having image related issues. Effective reports are structured, concise, purposeful, use proper grammar and writing conventions like avoiding contractions and writing in the active voice. Capitalization, software names, highlights and emphasis, and images should be handled consistently within a report.