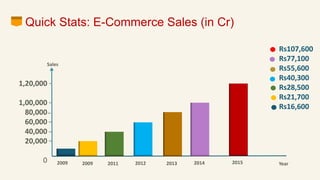
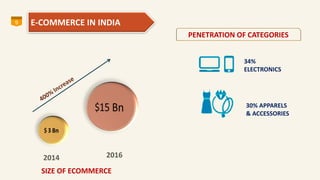
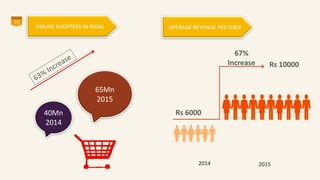
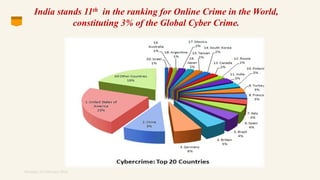
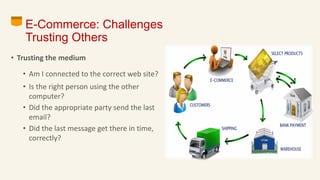
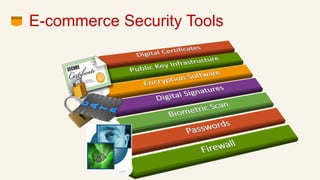
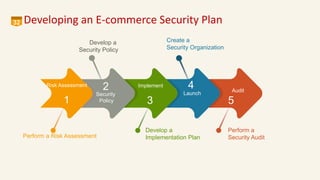
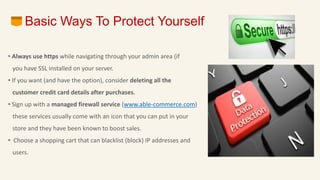
This document discusses eCommerce security challenges and plans. It outlines trends impacting security like increased digital activity and networked value chains. Major security threats to eCommerce include malware, hacking, and credit card fraud. Authentication, integrity, access control and non-repudiation are key security concerns. Developing an eCommerce security plan involves performing a risk assessment, developing security policies and procedures, implementing security tools, and conducting security audits. Government regulations for eCommerce in India are also discussed. Basic security measures for eCommerce sites include using HTTPS, deleting credit card data, and blacklisting suspicious IP addresses.