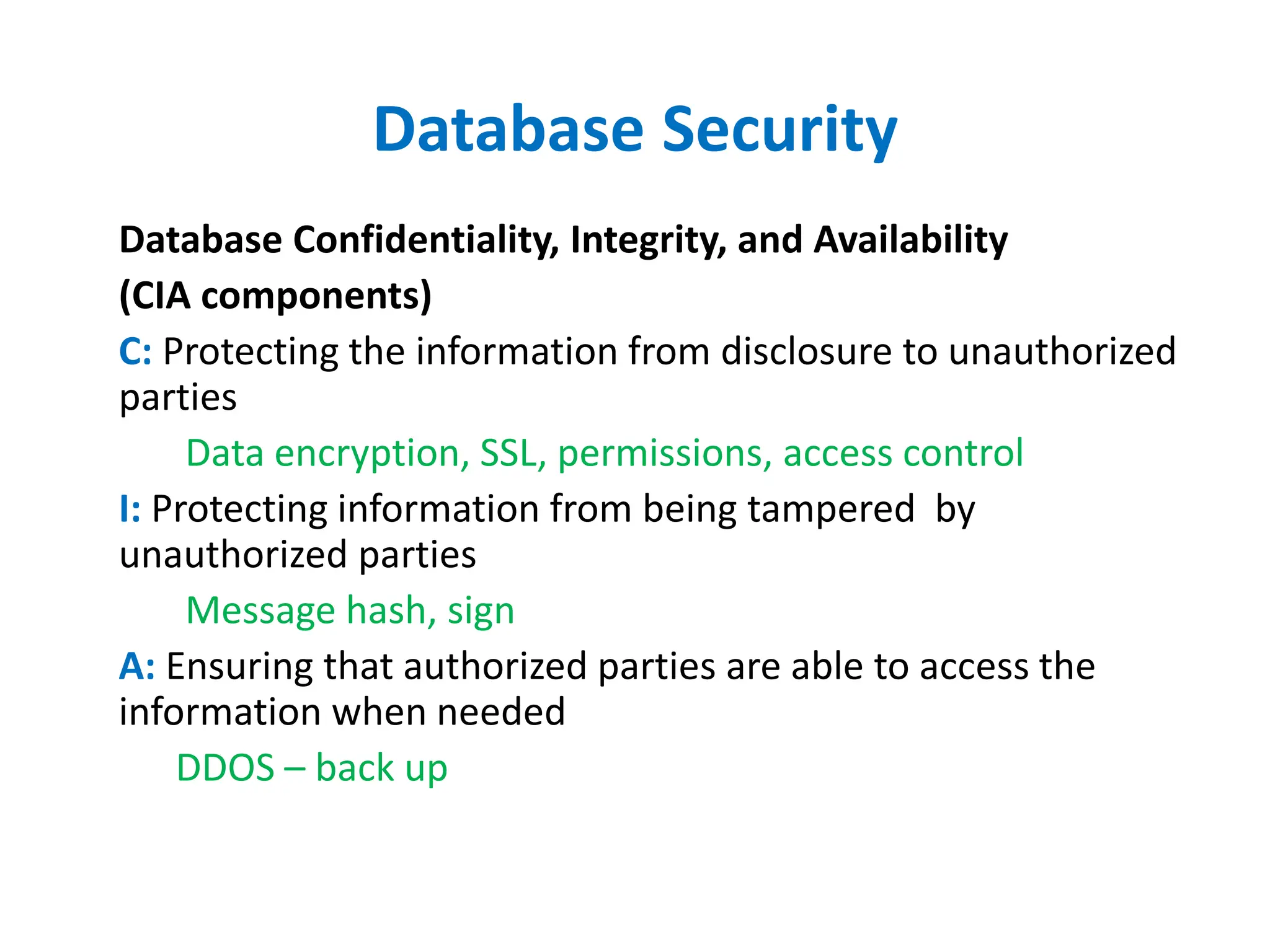
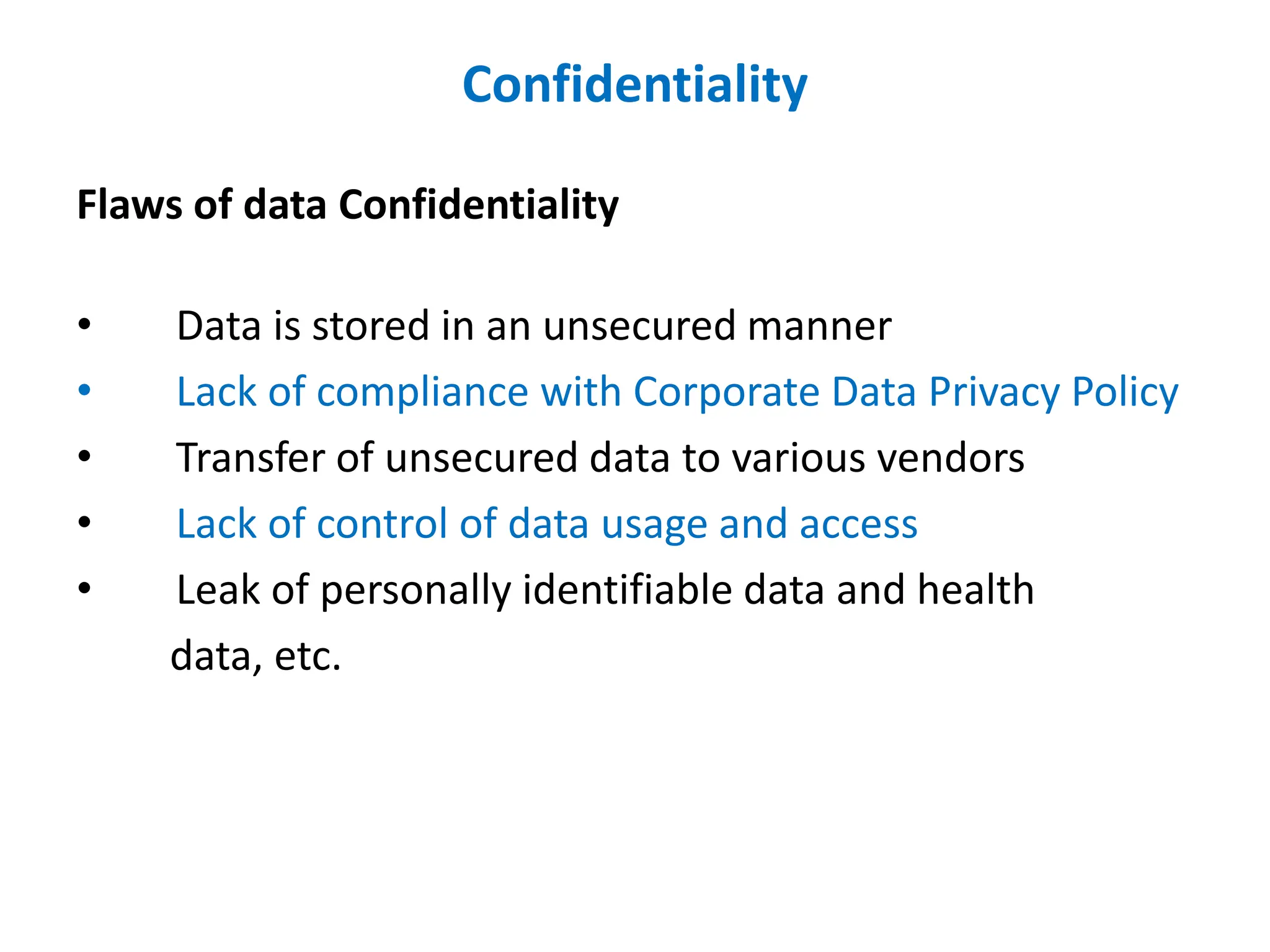
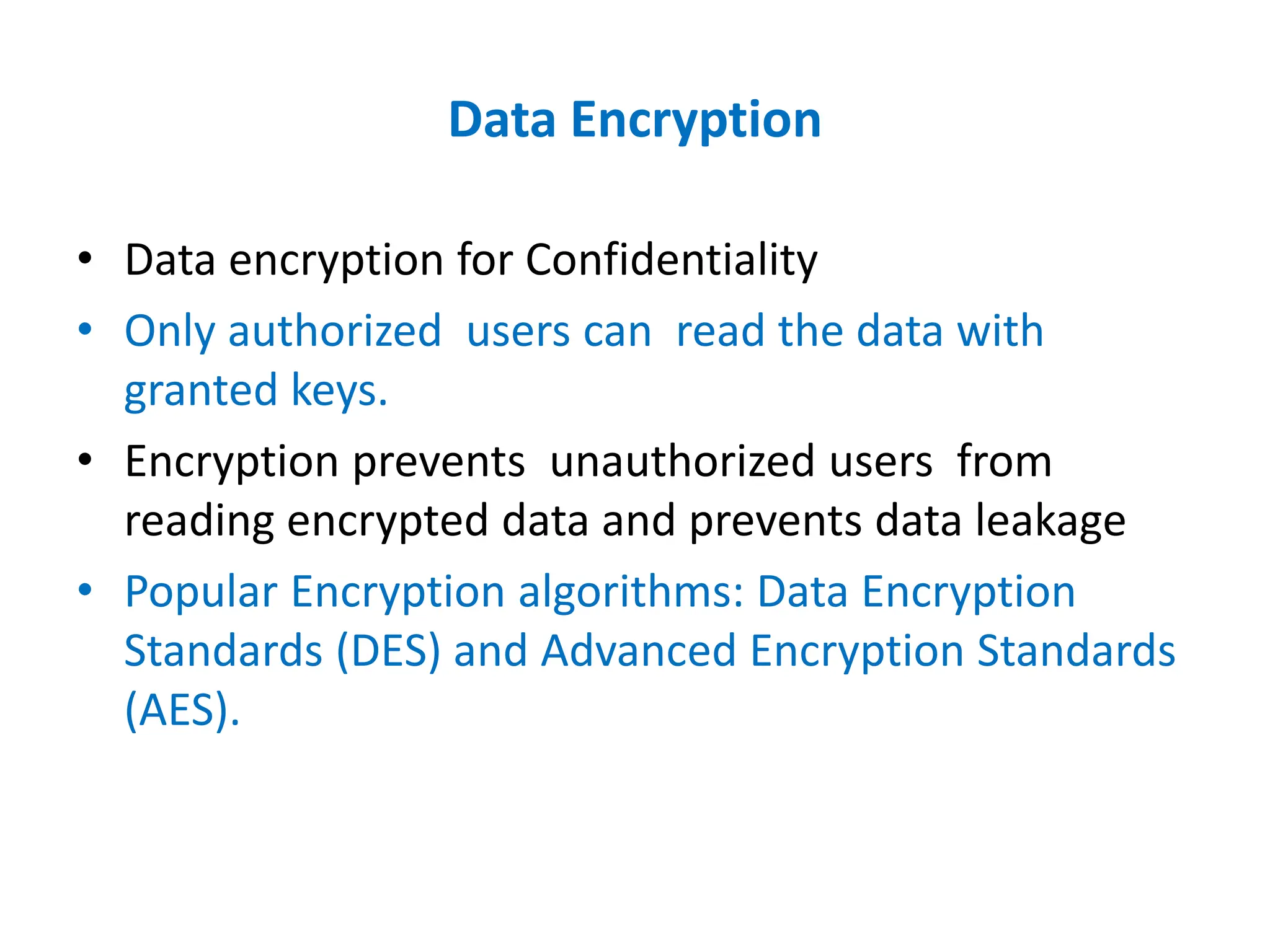
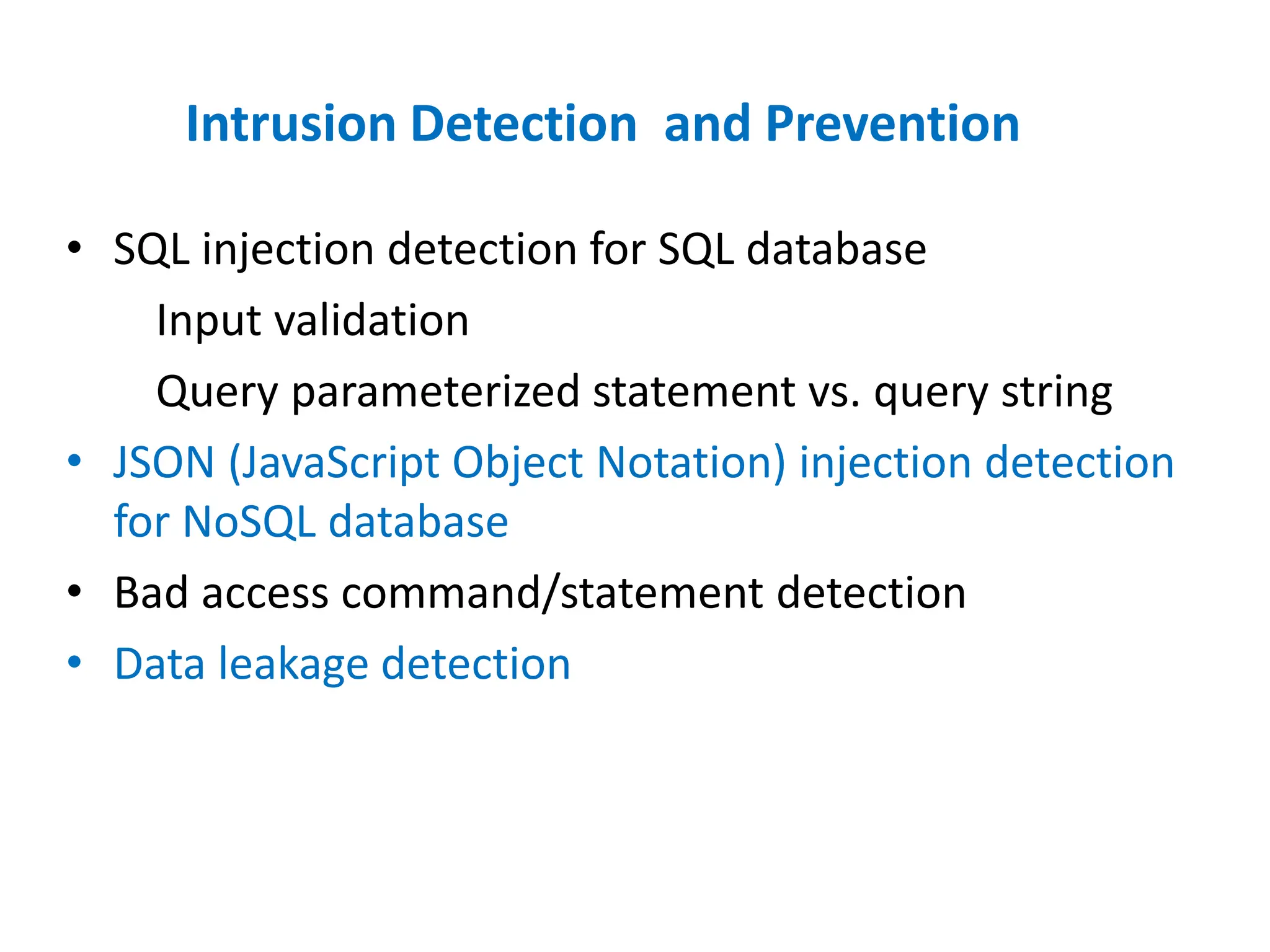
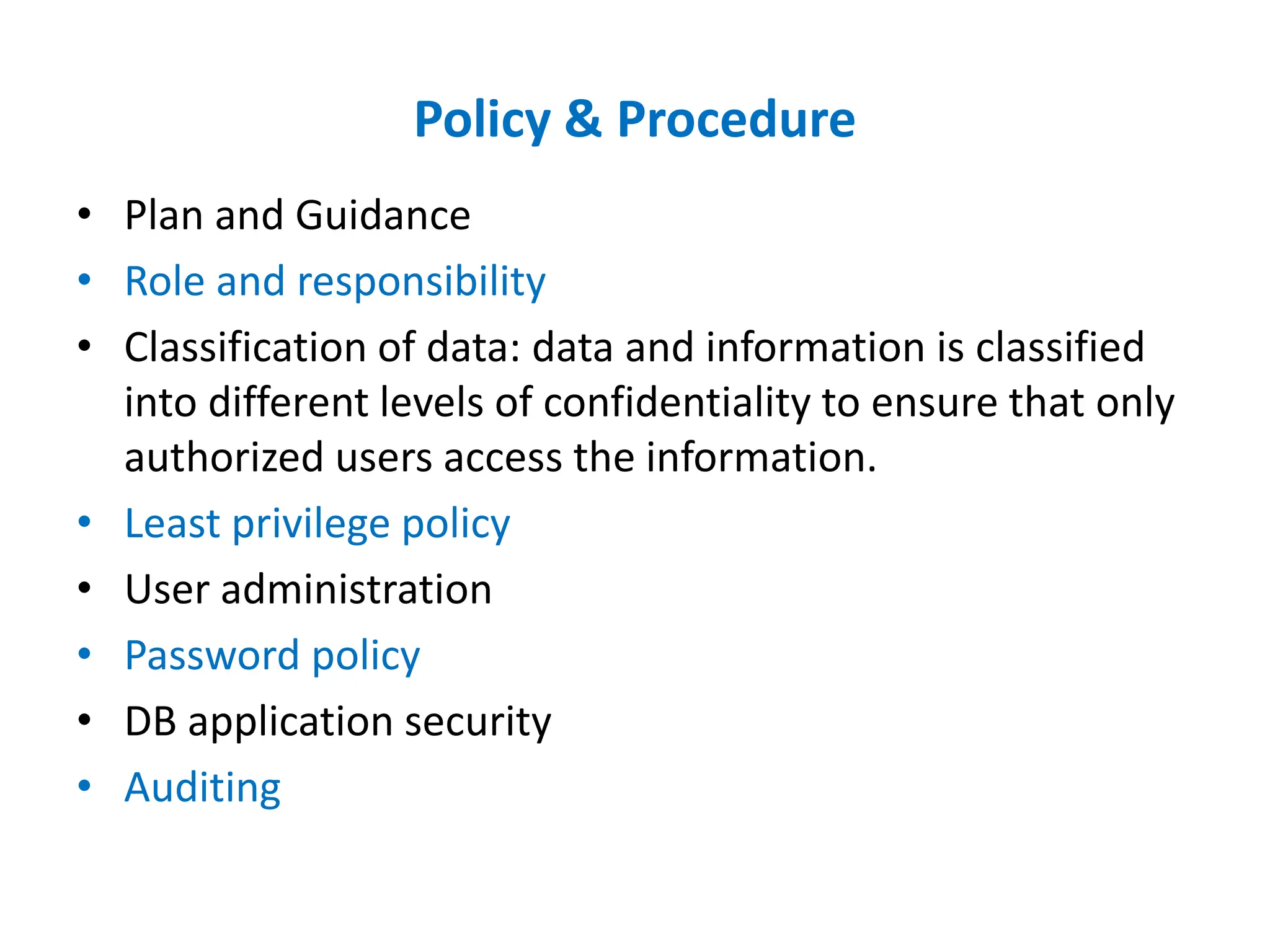
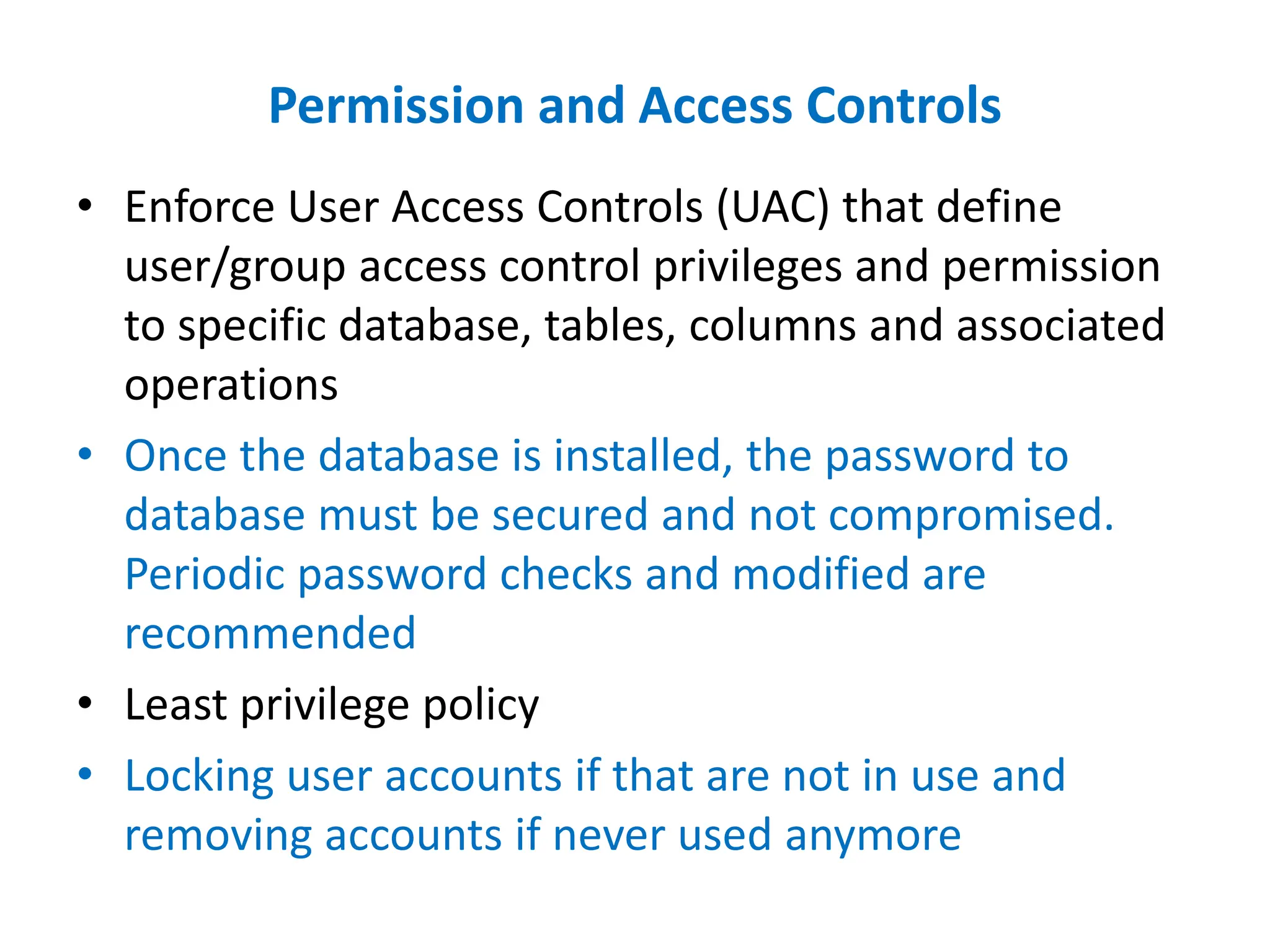
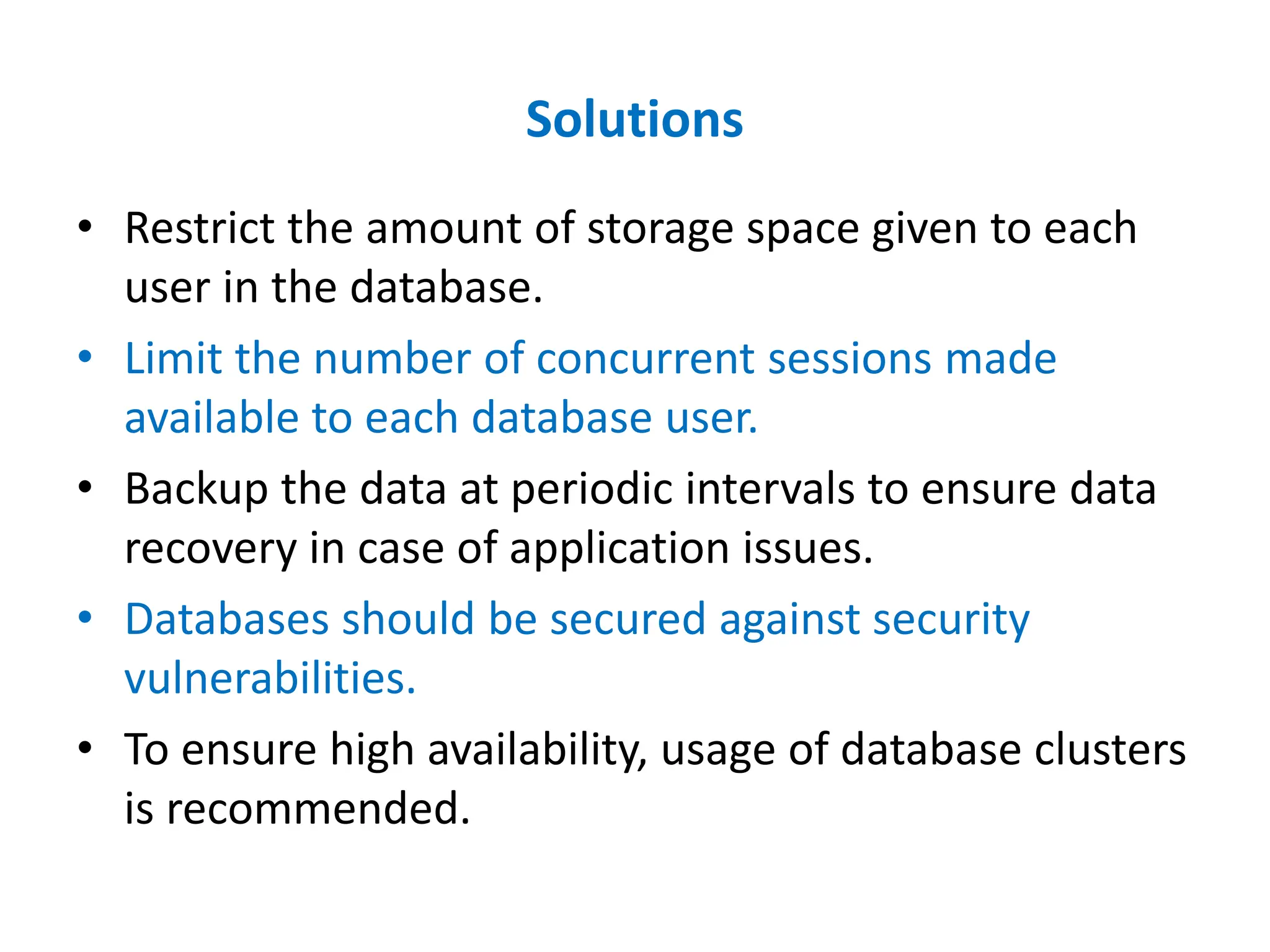
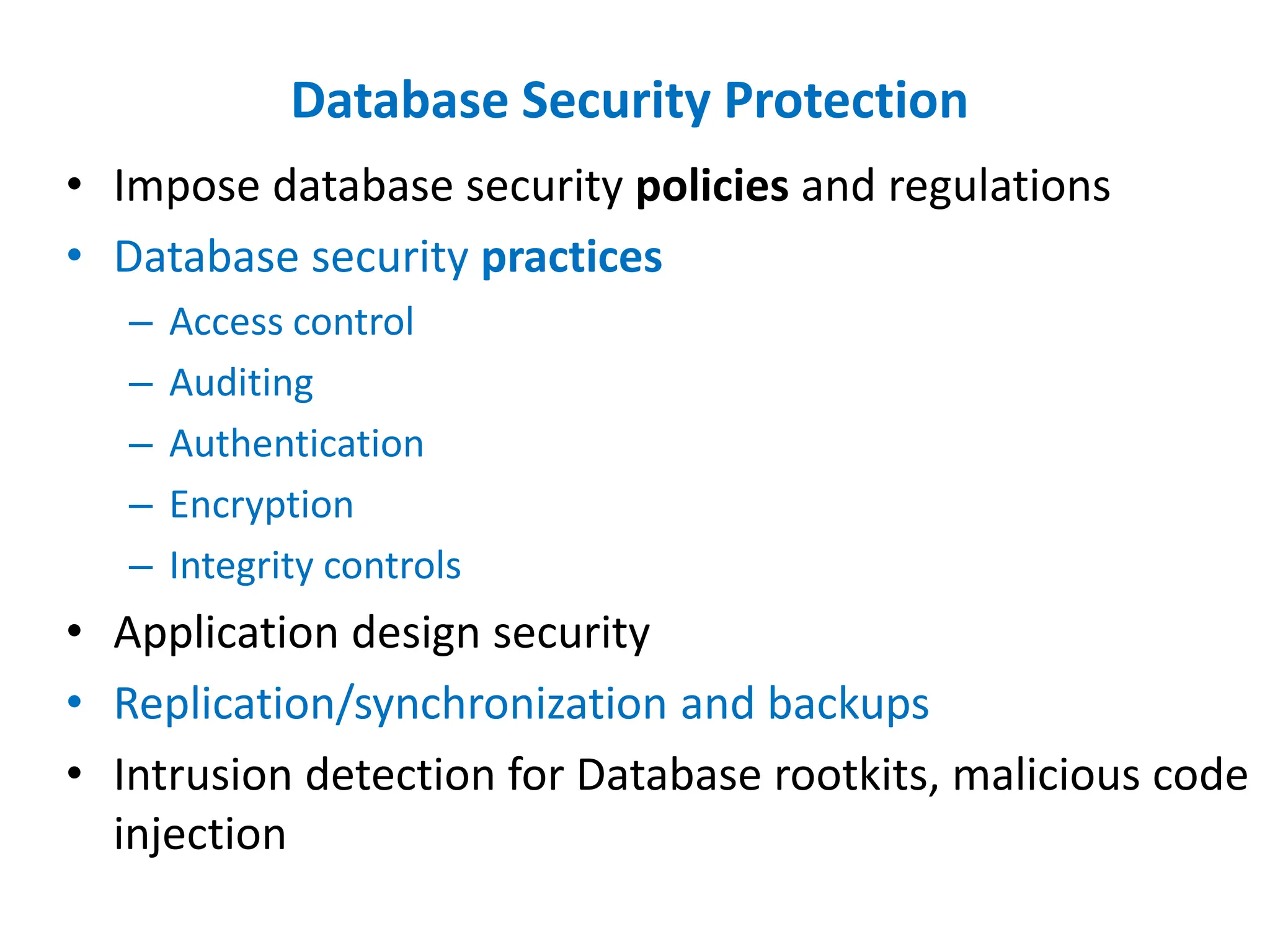
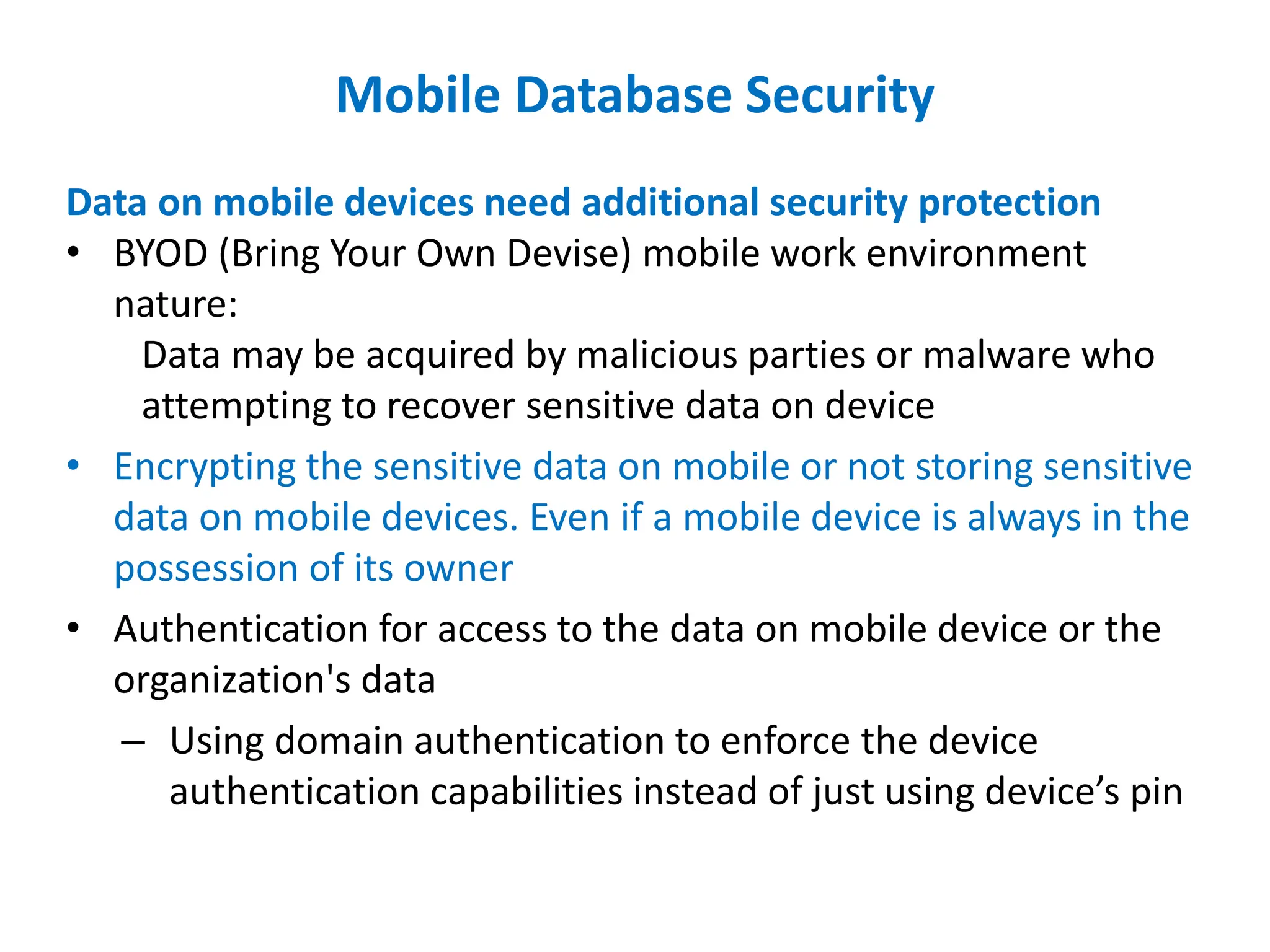
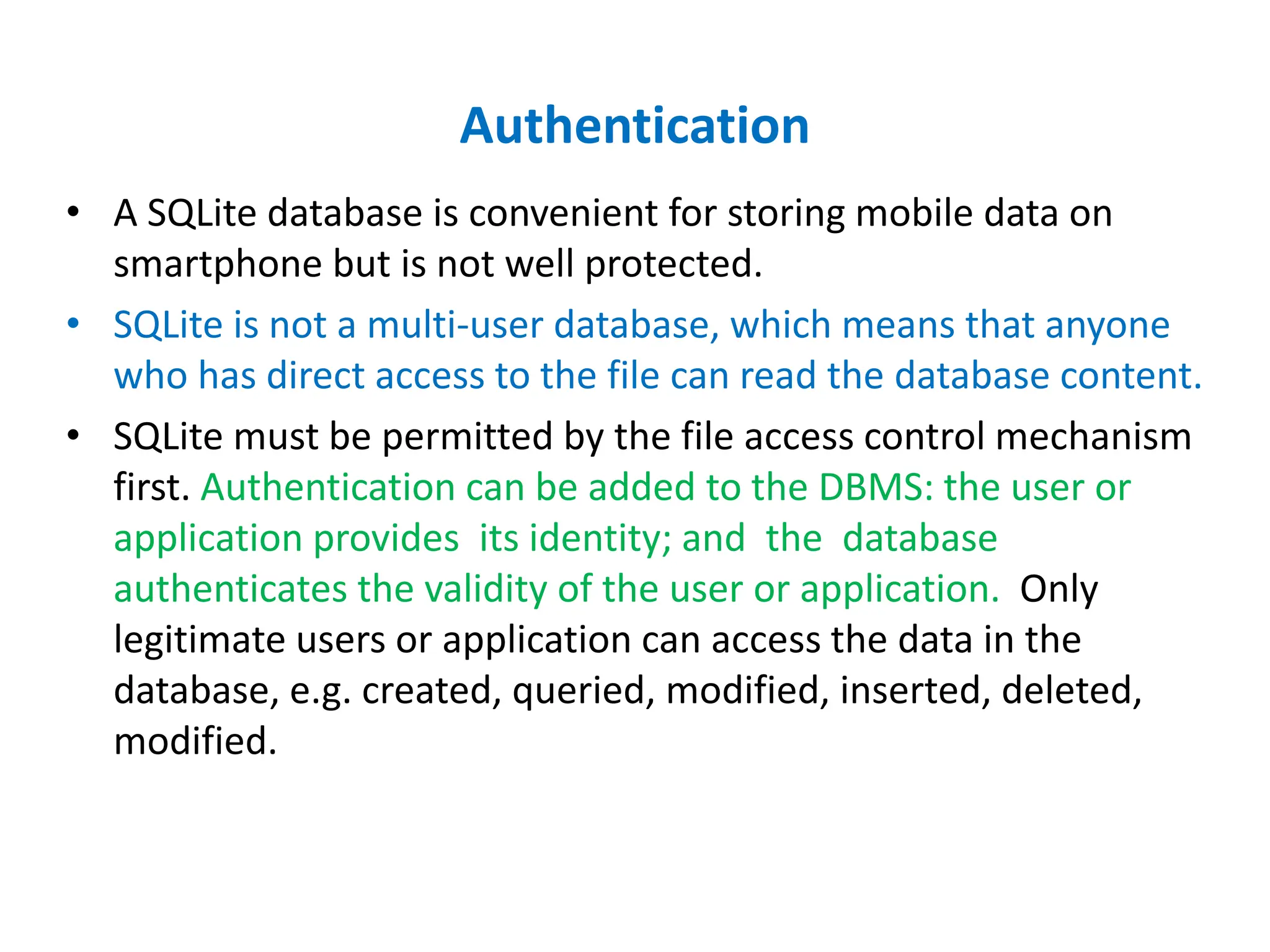
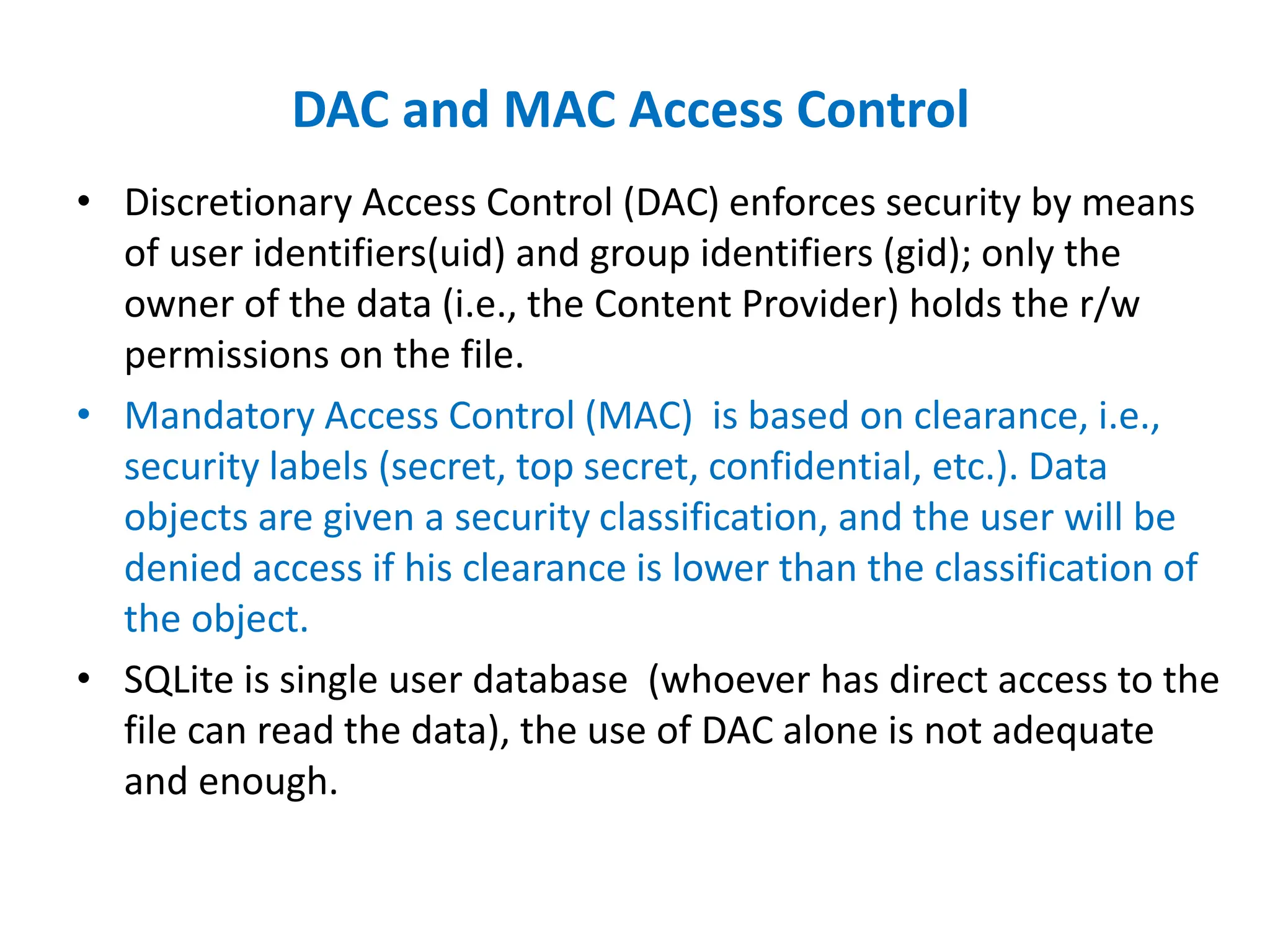
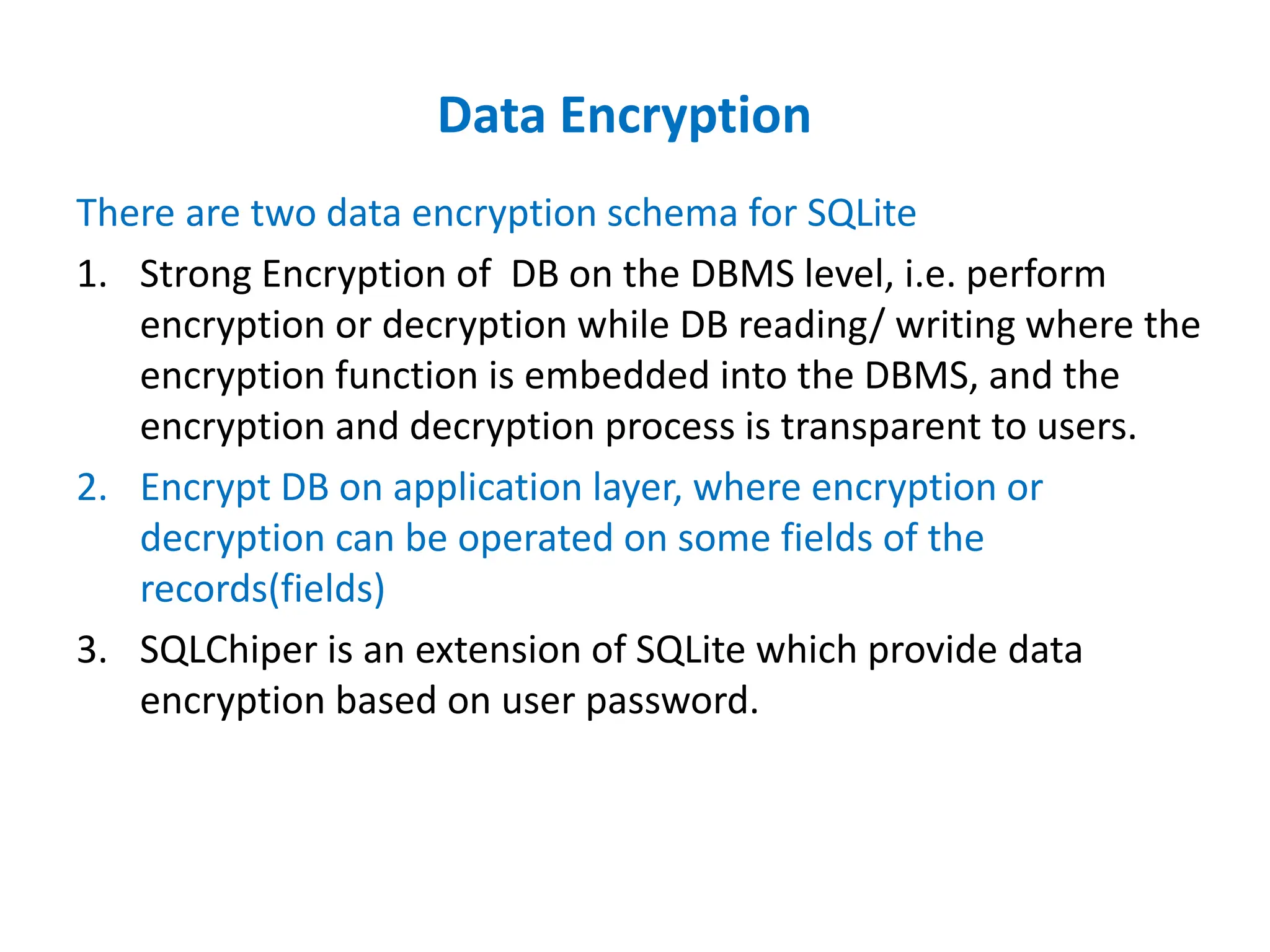
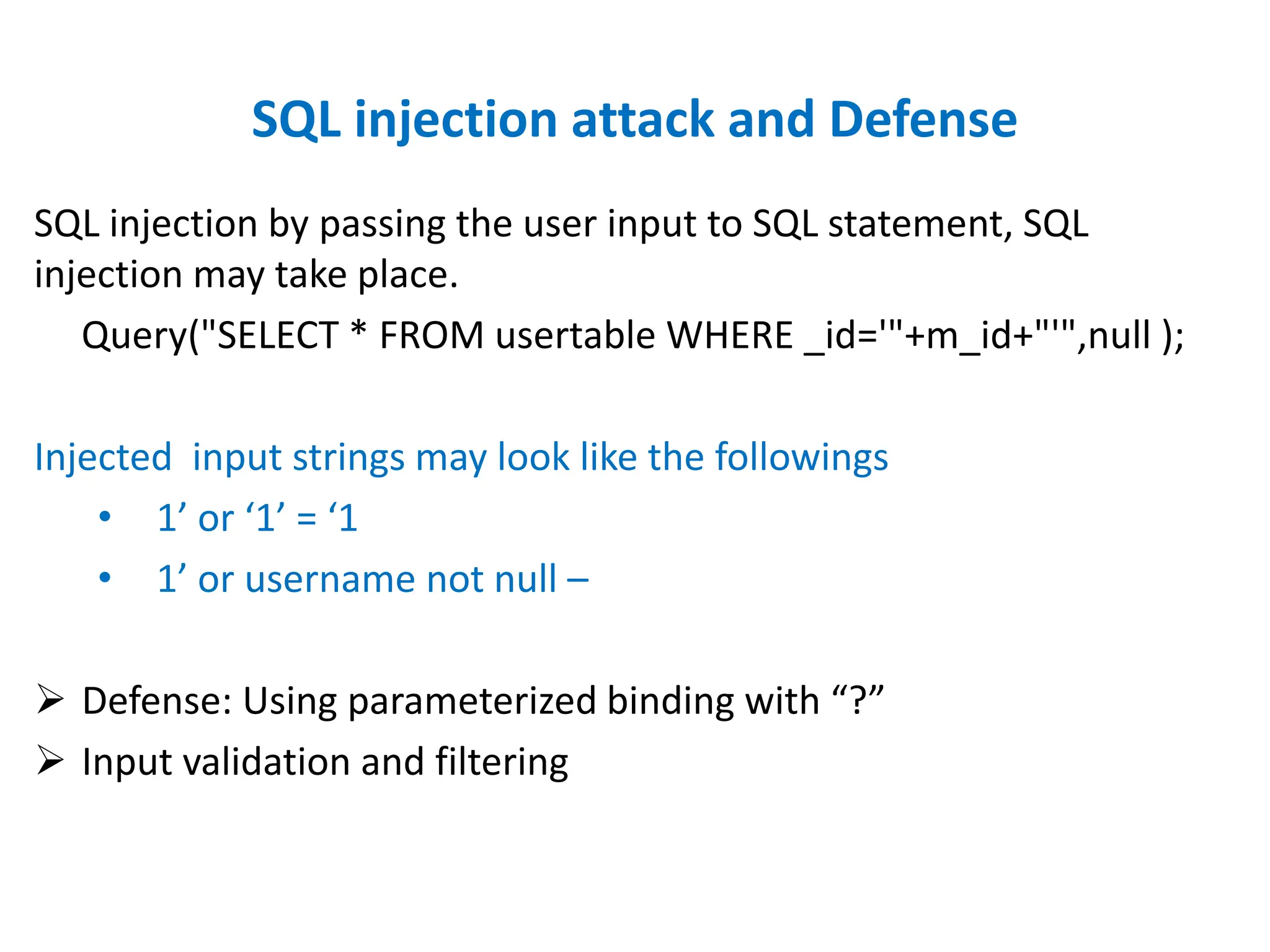
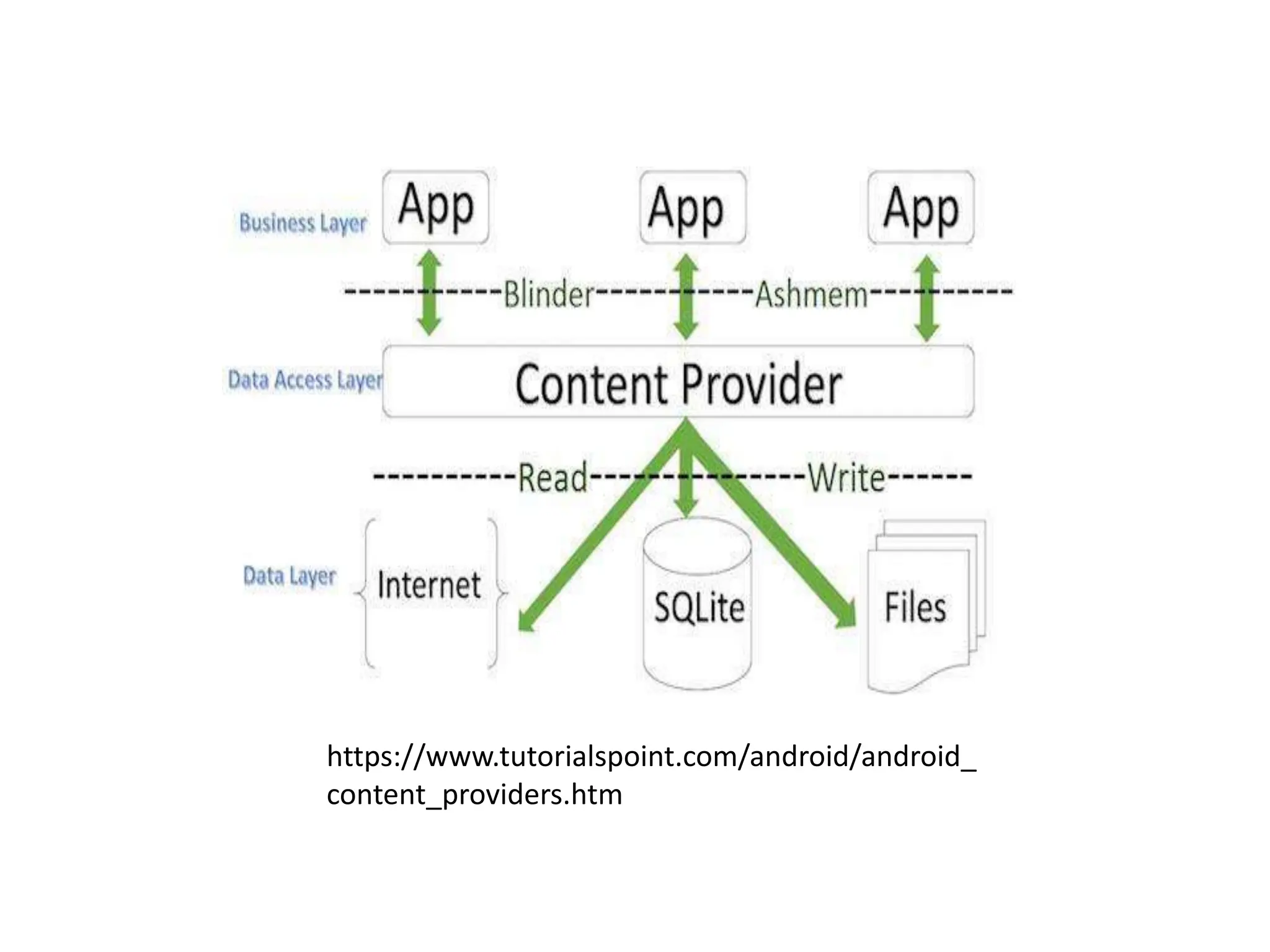
Dr. Wei Chen discusses database security. The three components of database security are confidentiality, integrity, and availability (CIA). Confidentiality involves protecting data from unauthorized disclosure through encryption and access controls. Integrity ensures data is not tampered with using hashing and signing. Availability ensures authorized users can access data when needed through backups and DDoS protection. Mobile database security poses additional challenges due to devices leaving secure networks. Encrypting sensitive data and using device authentication can help. Content providers allow sharing data between apps if necessary but increase security risks. Auditing, access controls, and input validation are important defenses against threats like SQL injection.