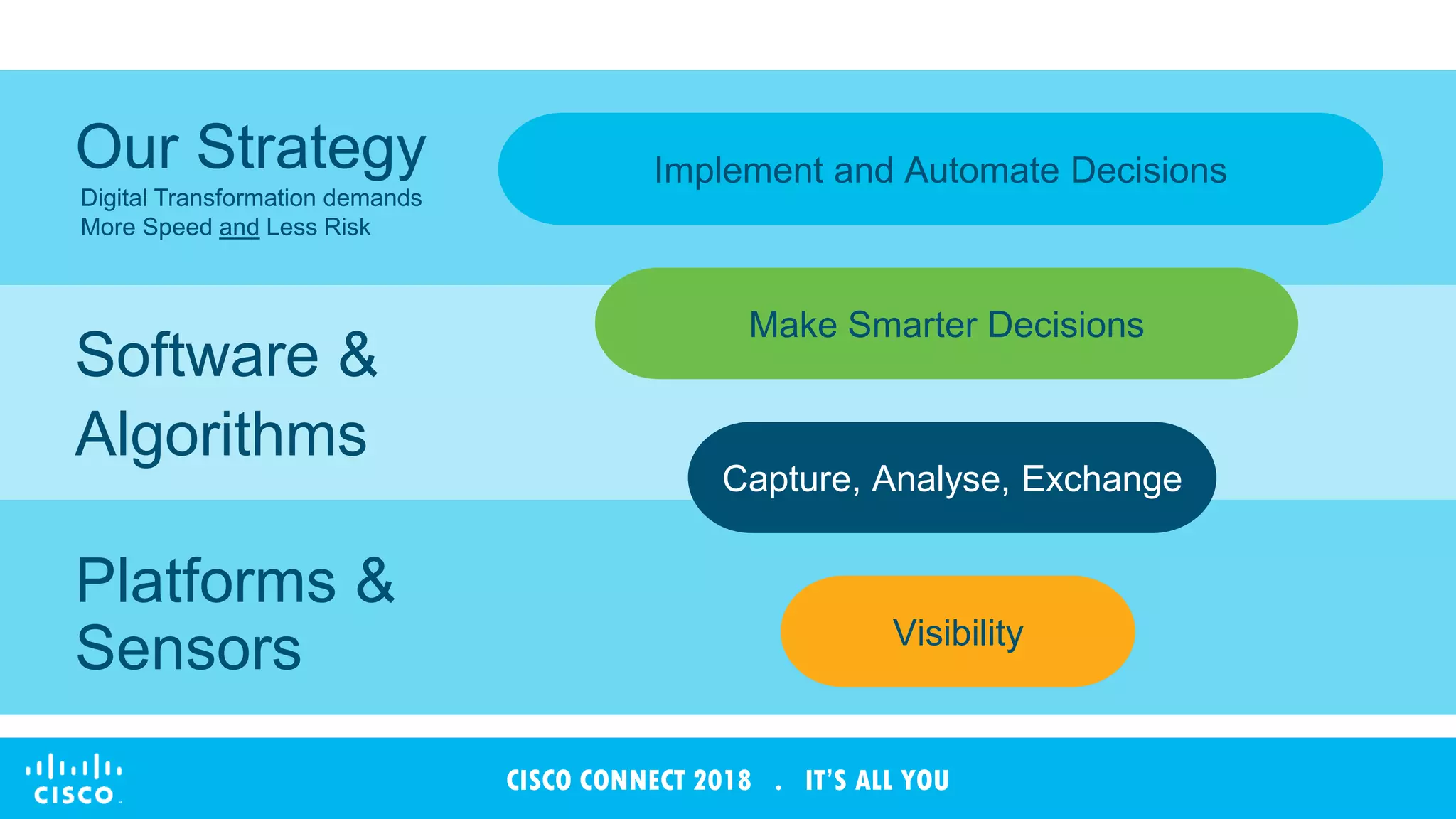
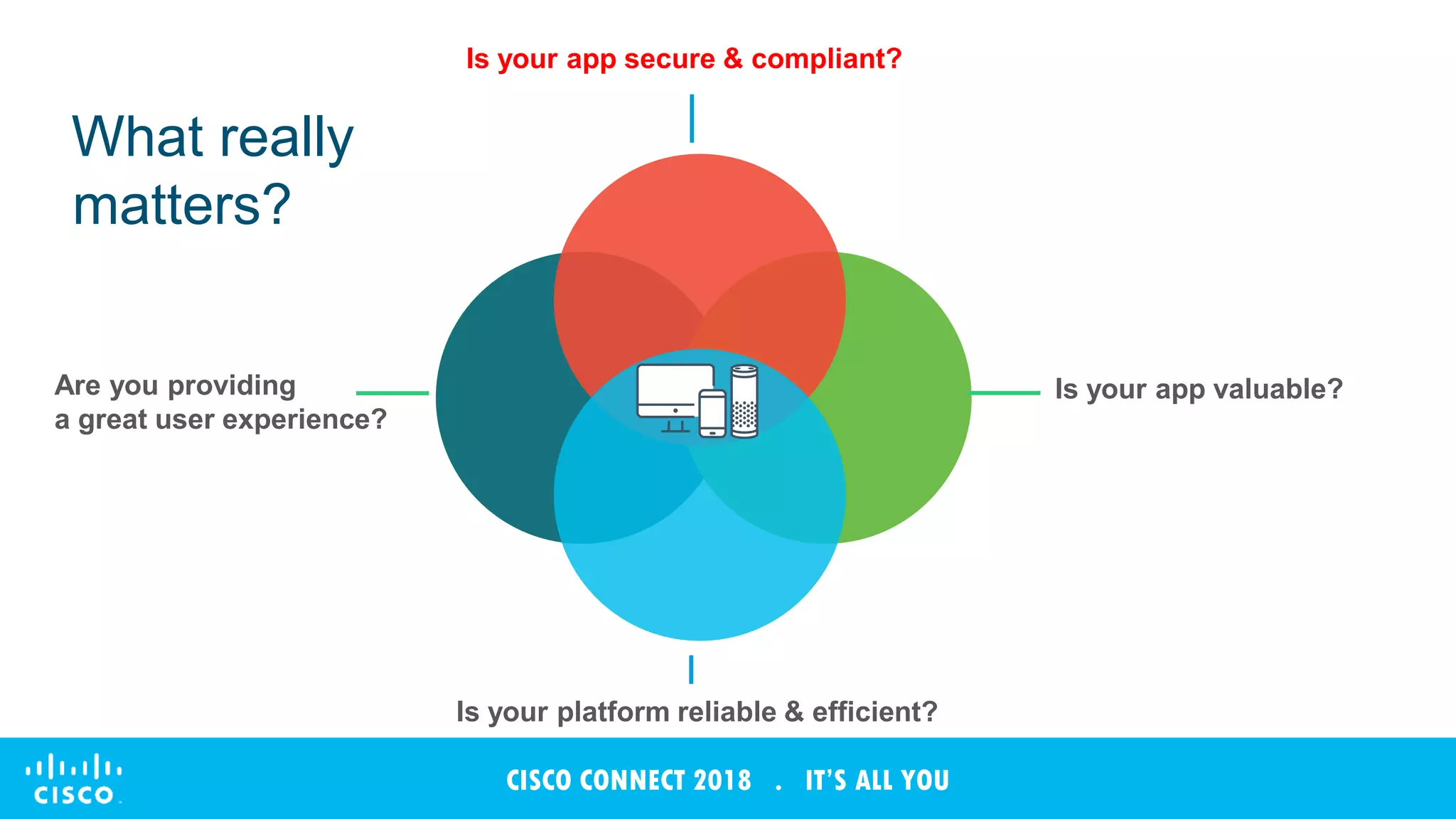
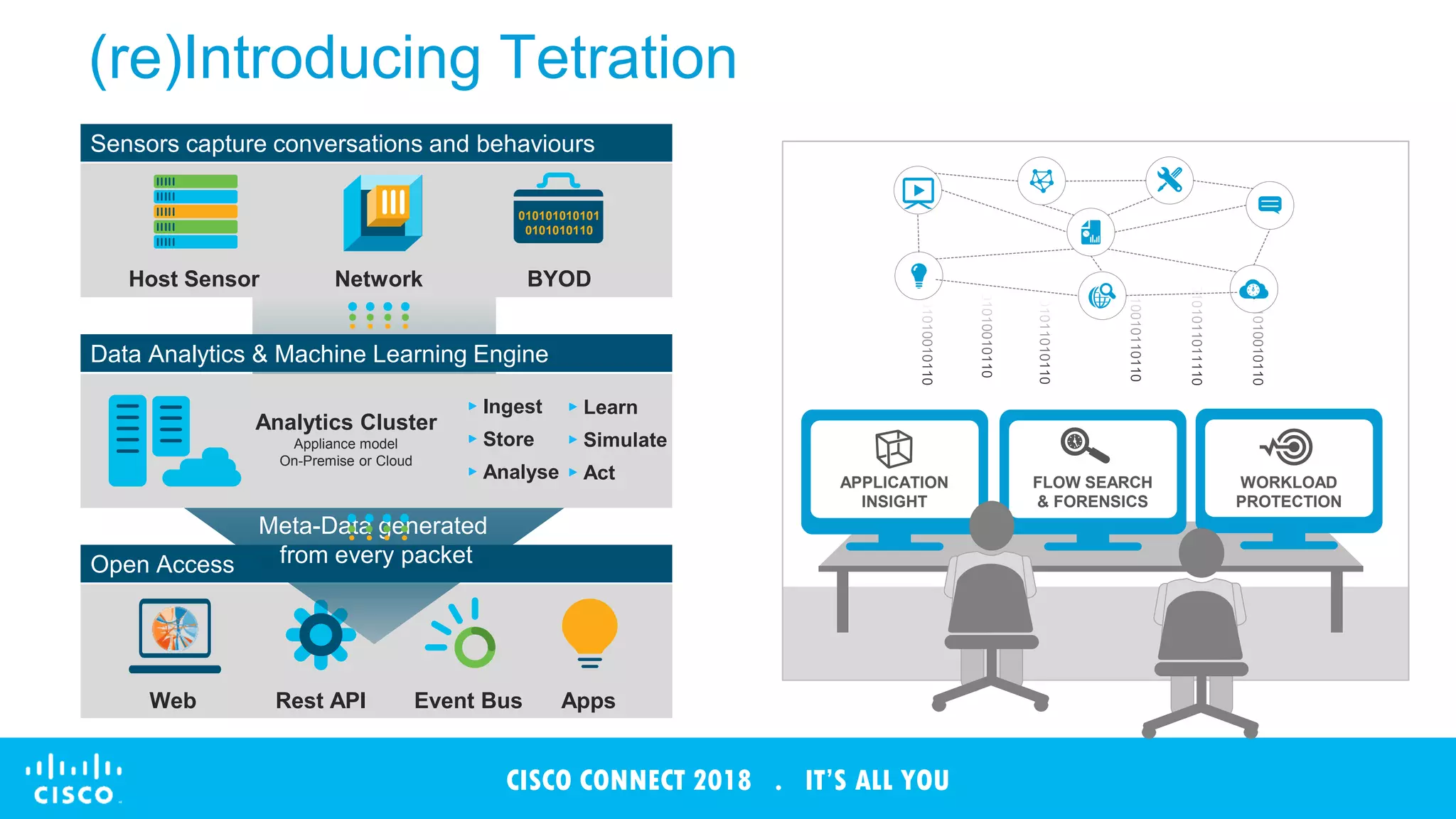
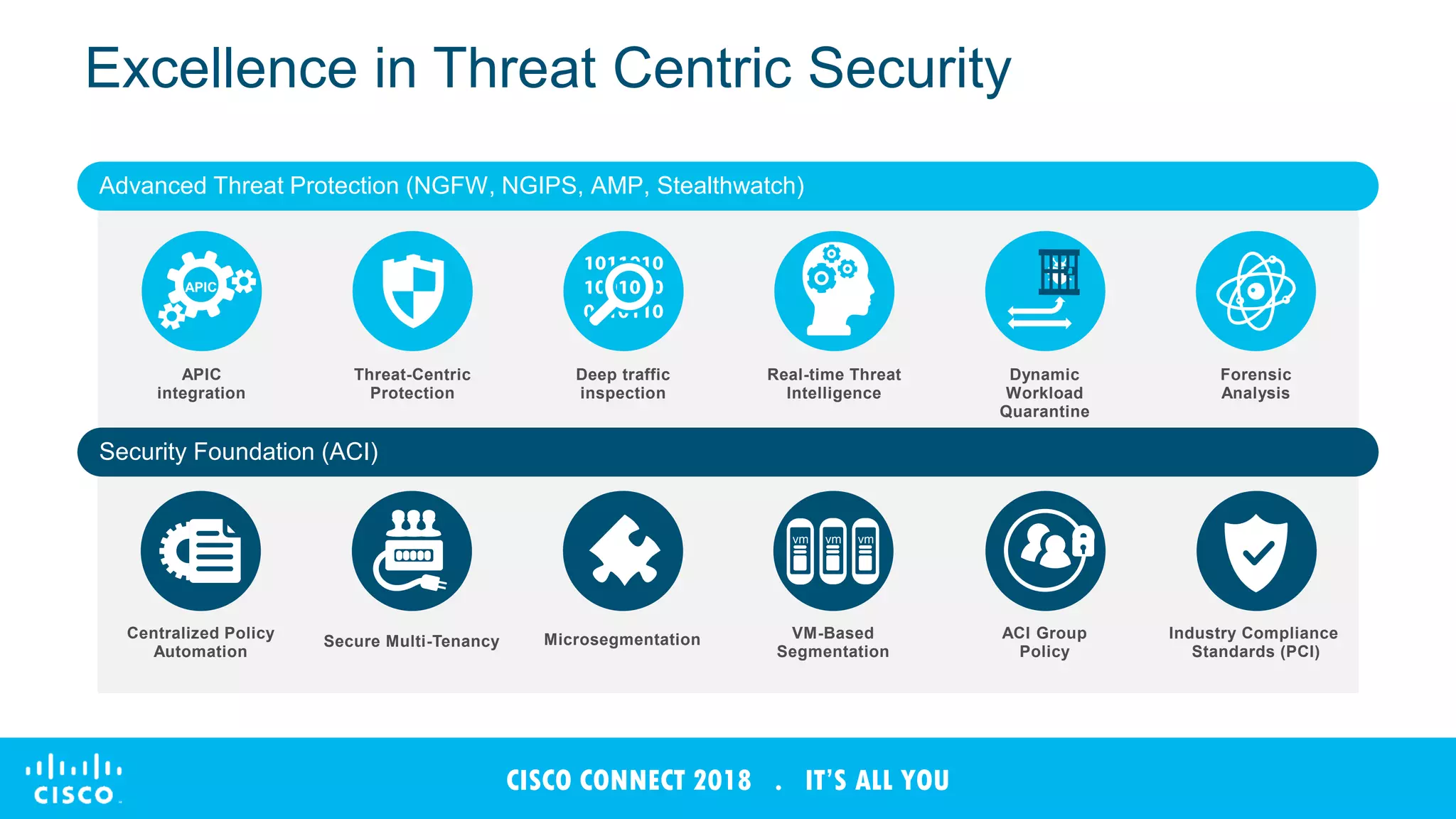
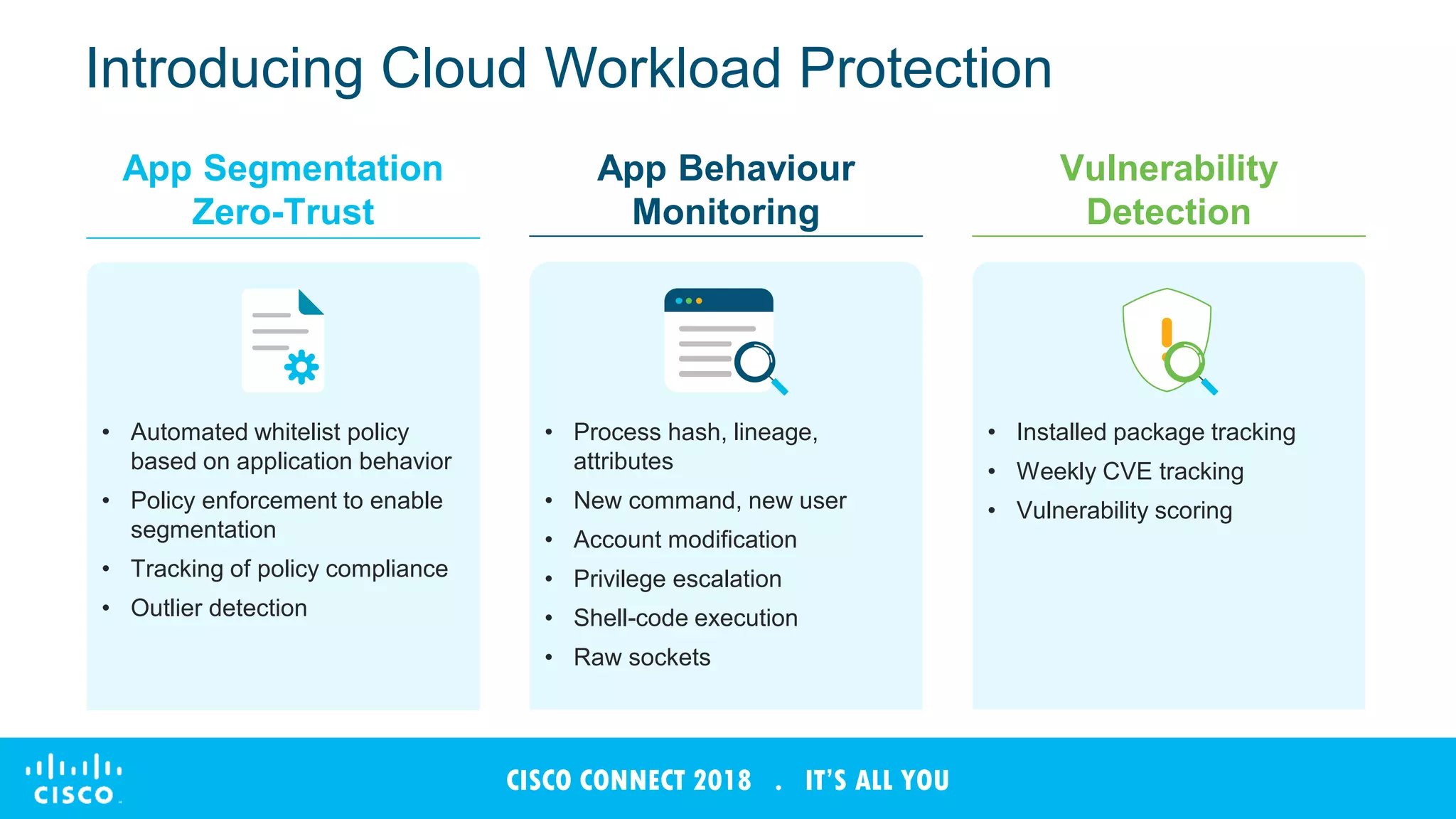
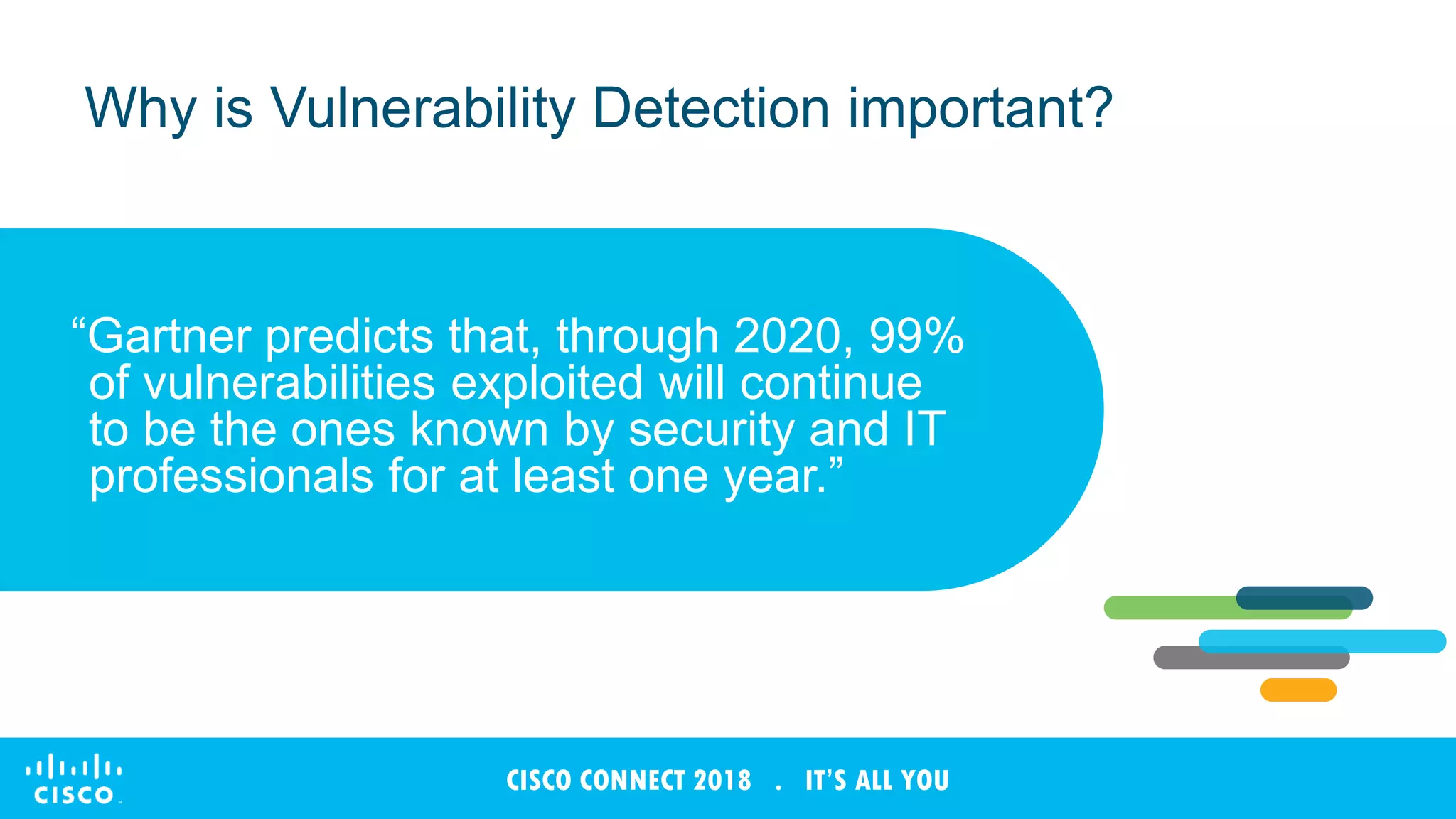
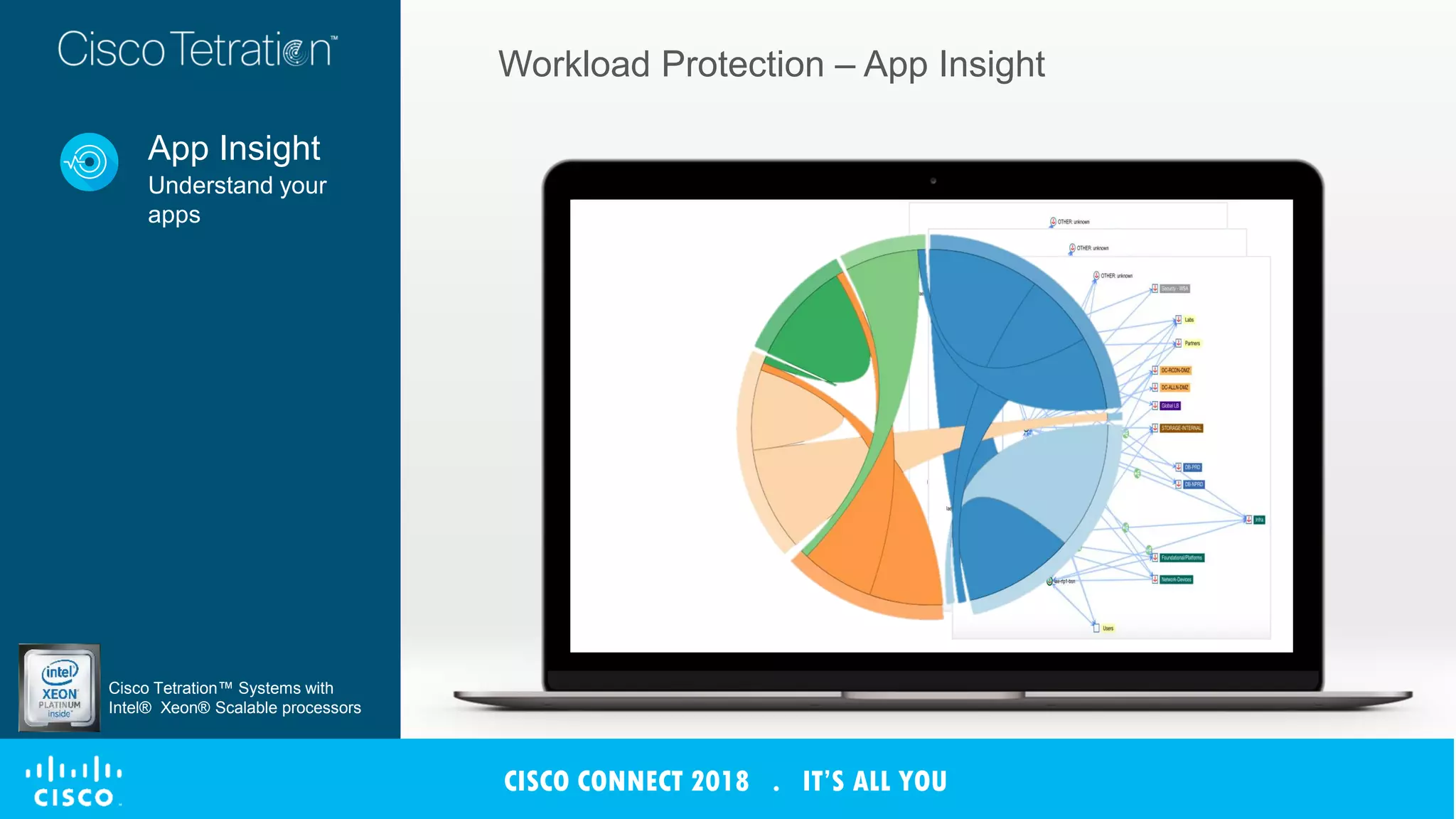
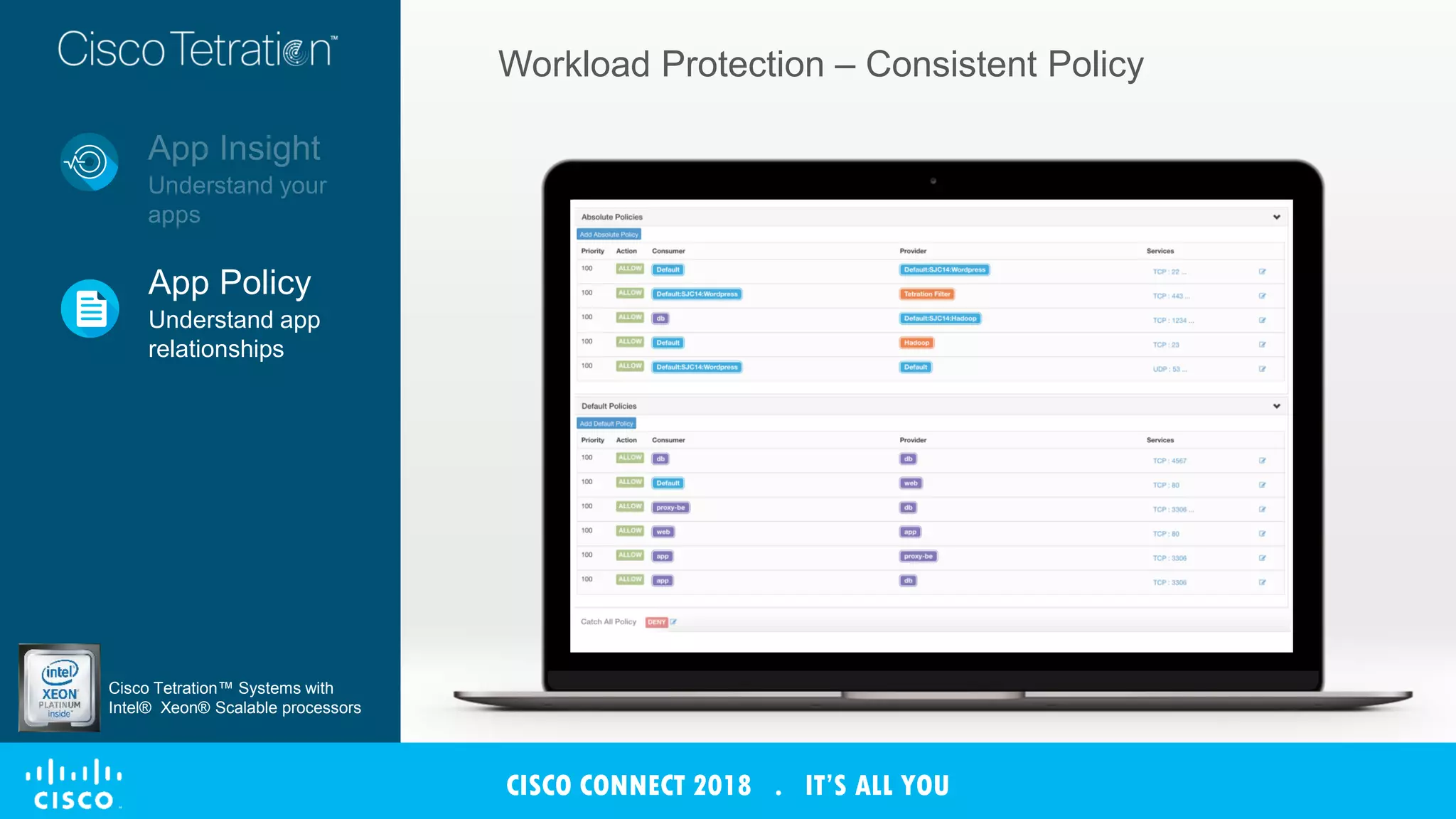
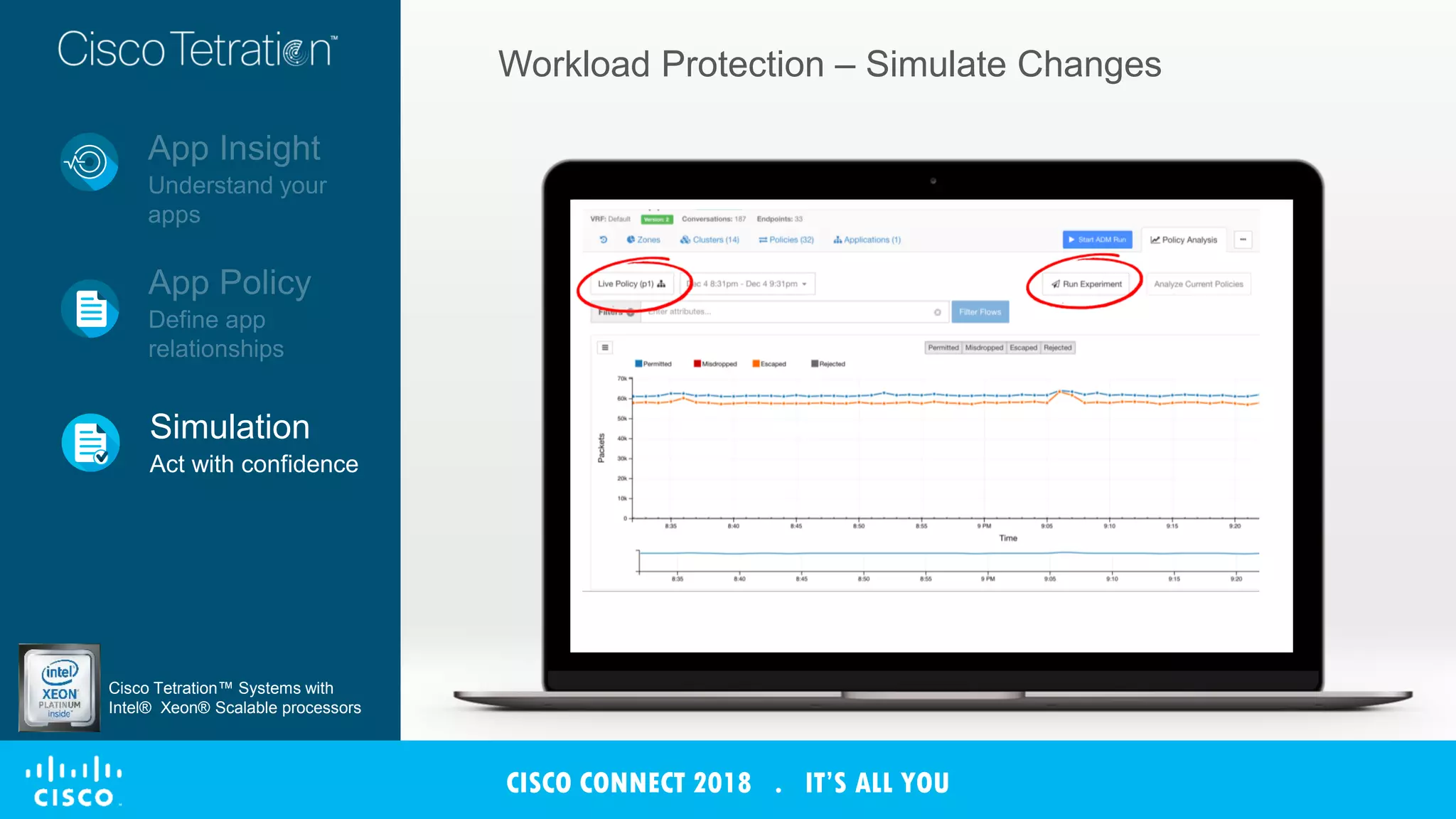
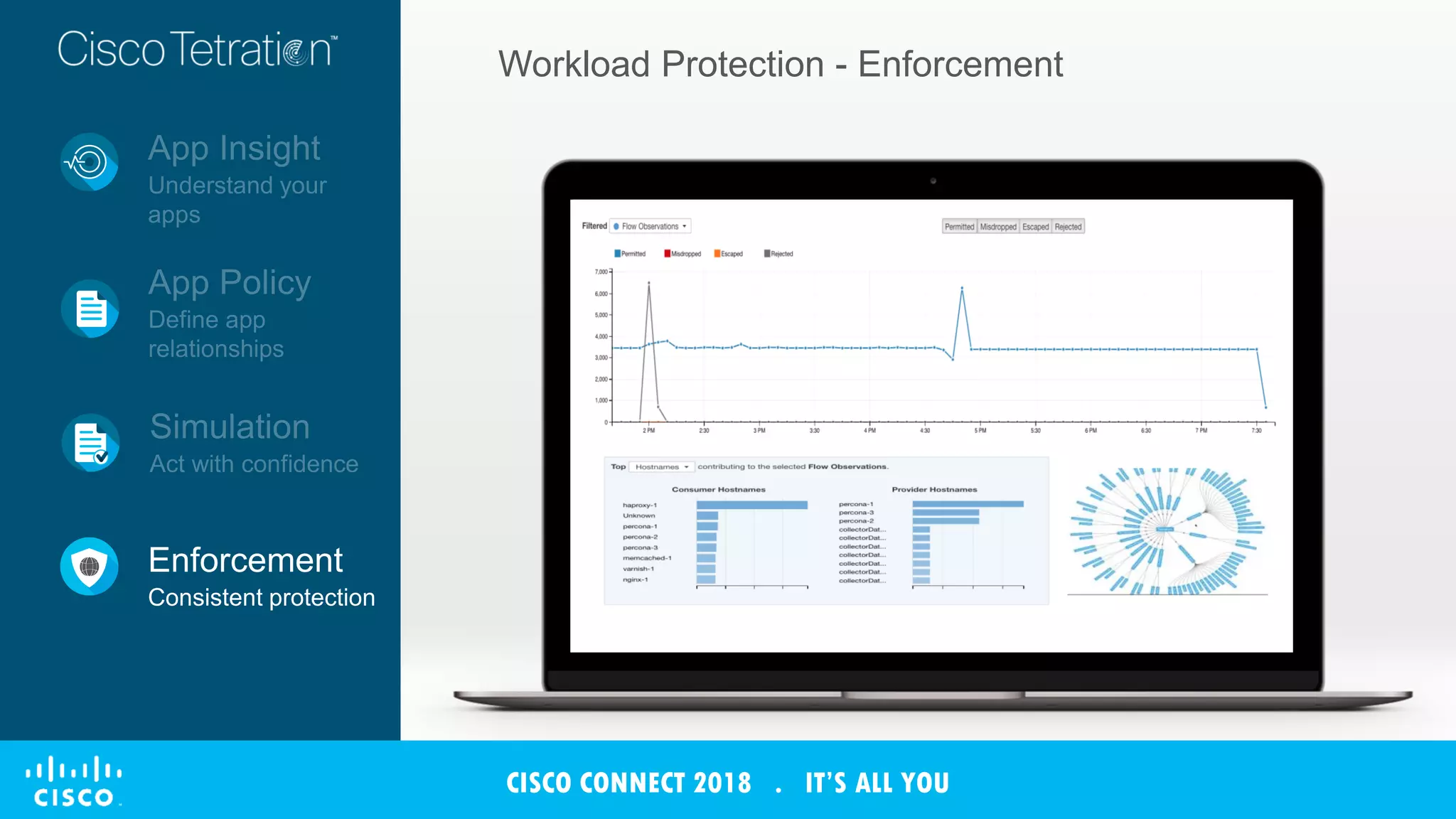
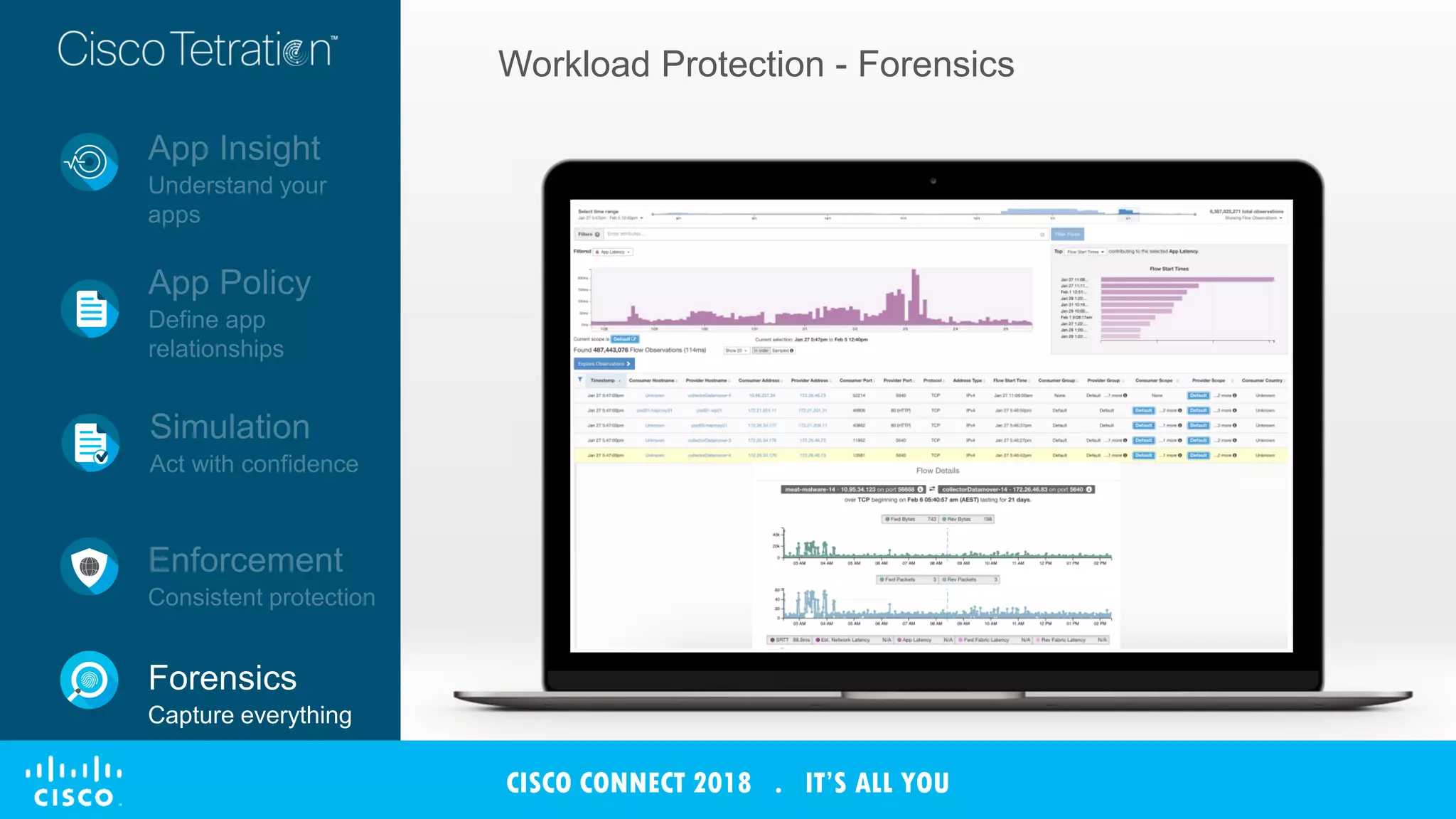
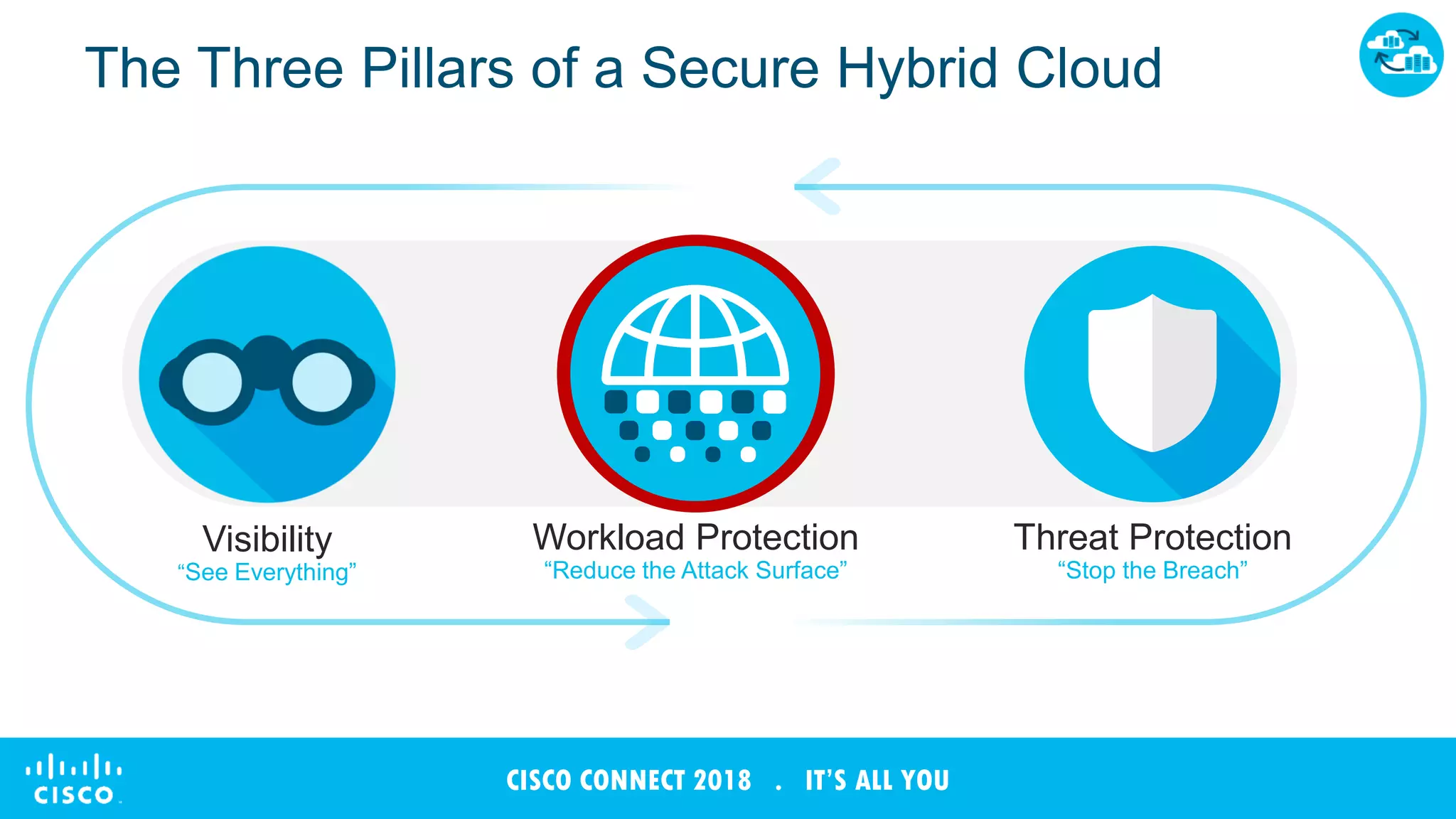
The document discusses Cisco's Tetration analytics platform for building a secure data center. Tetration provides visibility into application dependencies and network traffic, workload protection through microsegmentation and policy enforcement, and forensic capabilities for investigating security incidents. It captures metadata from all network traffic using sensors and analyzes the data with machine learning to provide insights into applications, detect anomalies, and automatically generate microsegmentation policies for increased security.