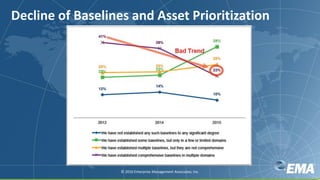
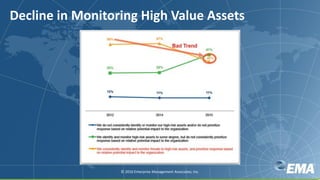
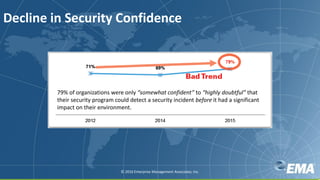
The document discusses key insights on avoiding data breaches in 2016, highlighting that 97% of executives expect an increase in data breach attempts and that 99% plan to invest more in security. It emphasizes the importance of addressing known vulnerabilities, as over 80% of attacks target them, and offers a three-pronged strategy for organizations to enhance security through people, processes, and technology. Additionally, it notes significant staffing challenges and the need for integration and automation in security operations.